How to block internet access for client operating system's DNS over HTTPS
-
Not a solution, but a couple things that may help. The free DNSBL list in PF blocker are only updated once a month at the most. I would go back through and change all of your update settings to weekly. An example is is the UT1 list that you have enabled. A quick check told me the last time that list was updated was eight months ago. Personally, I would not run that list yet. It’s a big list and if you don’t have the CPU horsepower or RAM it’s just going to bog your system down. Plus trying to block porn is like trying to control the weather. I would start with your Steven black list, get things running how you want. Then add just one list at a time and see how the system handles it.
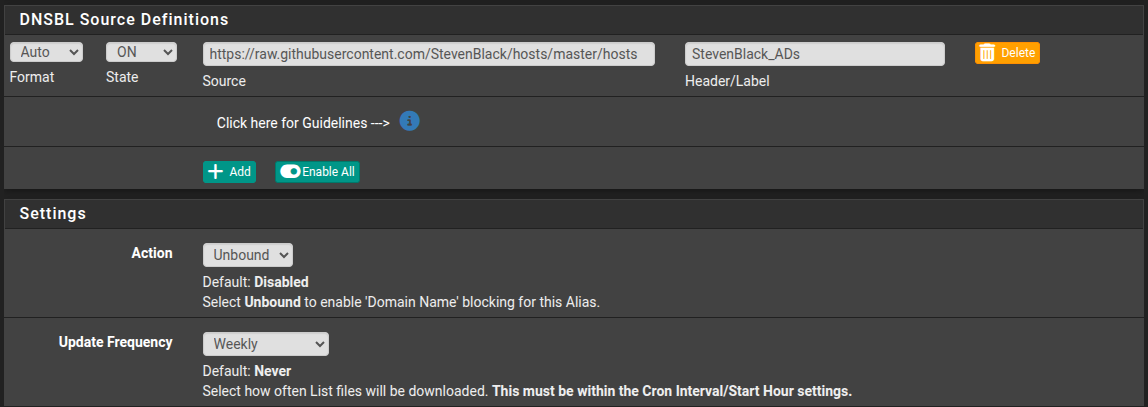
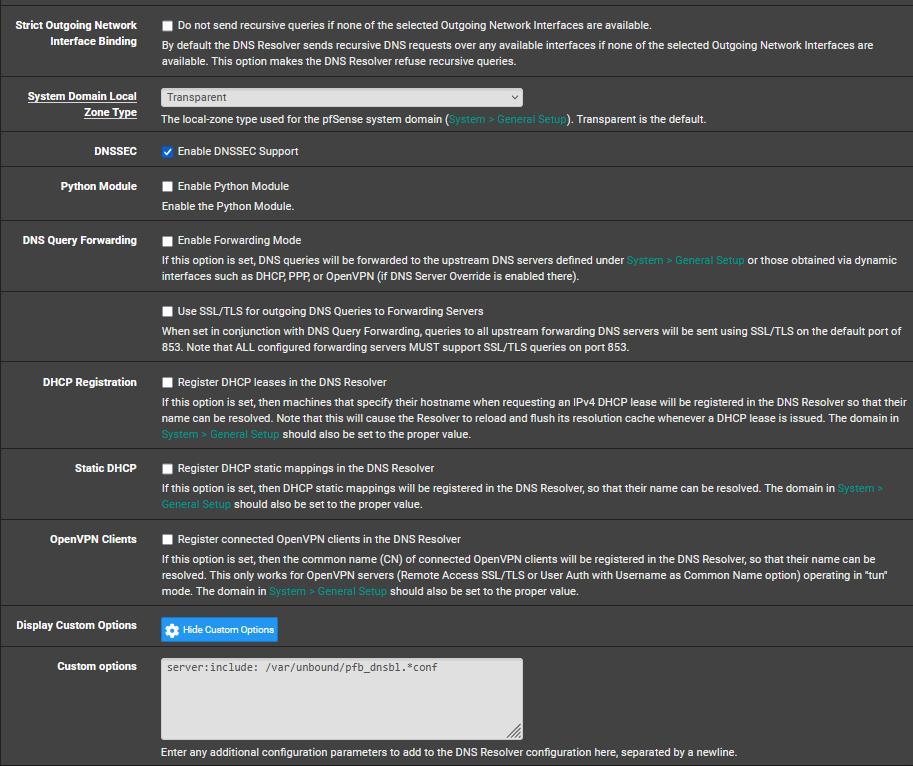
I would also disable DNSBL IP, put it back to stock settings. I dont understand what function it preforms exactly. Im just thinking it could be one of the sources of your problems.
-
@richardsago said in How to block internet access for client operating system's DNS over HTTPS:
How do I block internet access of users who enabled their operating system's DNS over HTTPS
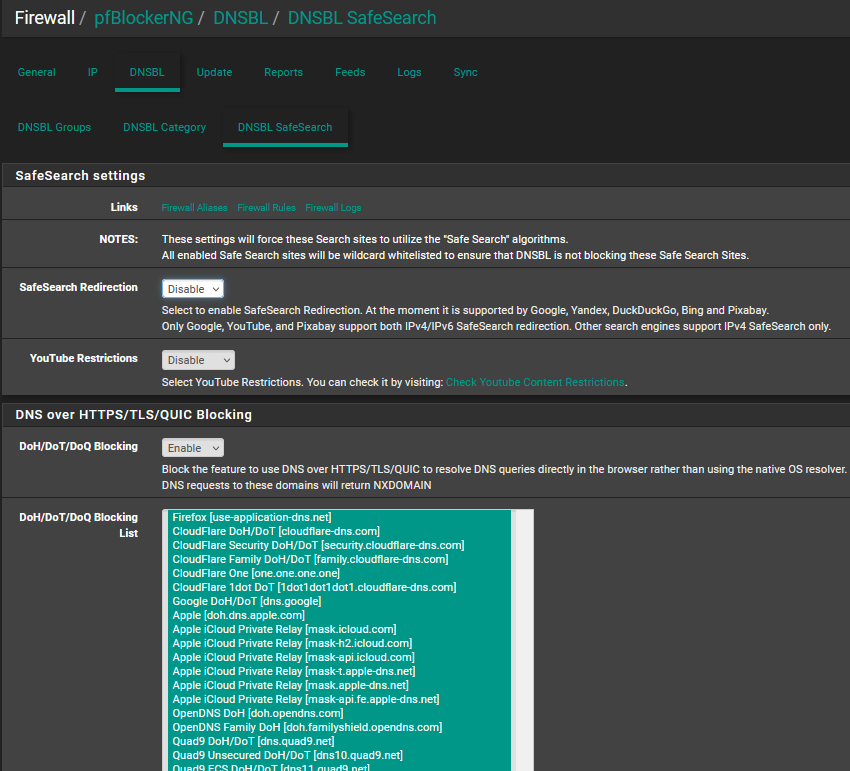
Enable DNSBL, and this, and then select all entries in the list:
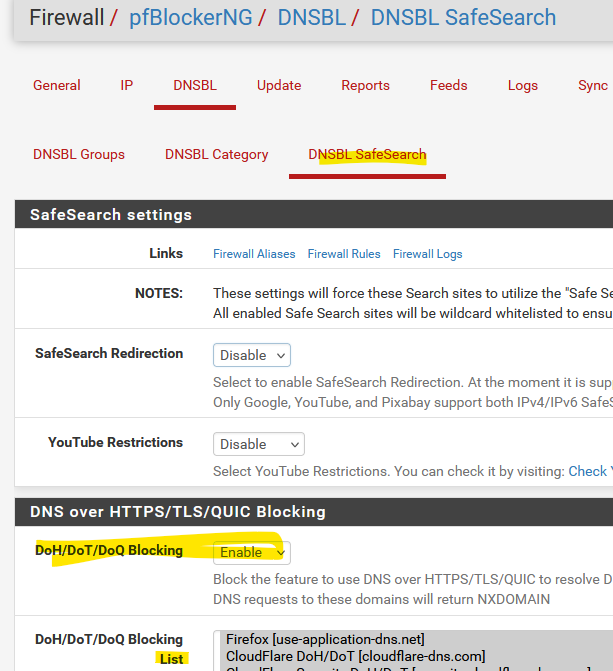
-
and in general block https://docs.netgate.com/pfsense/en/latest/recipes/dns-block-external.html#dns-over-tls
-
Thank you @Uglybrian for the suggestion. The UT1 DNSBL update frequency was already once a day but internet browsing is still possible when client's OS uses DNS over HTTPS.
Thank you @SteveITS for the suggestions. The "DoH/DoT/DoQ Blocking" was already enabled and all its entries were already selected, and the DNS over TLS entry is now added in the firewall rules but internet browsing is still possible when client's OS uses DNS over HTTPS.
I tried applying the "DNS over HTTPS" topic in the link (https://docs.netgate.com/pfsense/en/latest/recipes/dns-block-external.html#dns-over-tls) you gave and it can successfully block internet browsing if client's OS uses DoH, but it requires manually adding the IP Addresses of the DoH servers. Below are what I did and please let me know if you have other DoH Servers so I can add them to my list. Thank you in advance.
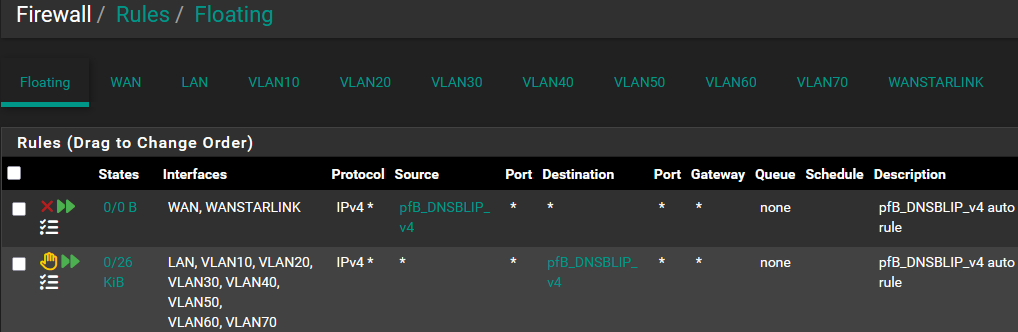
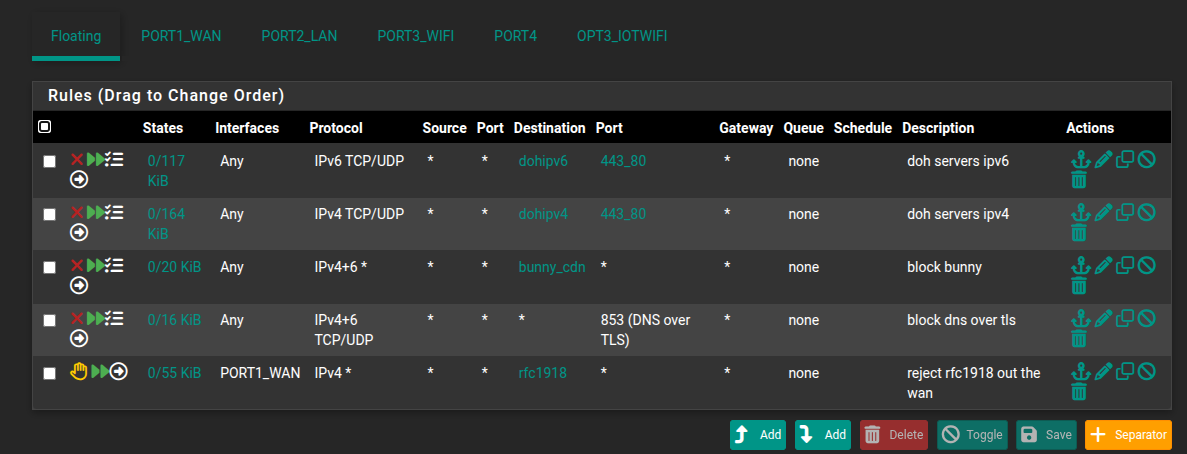
Added this firewall rule:
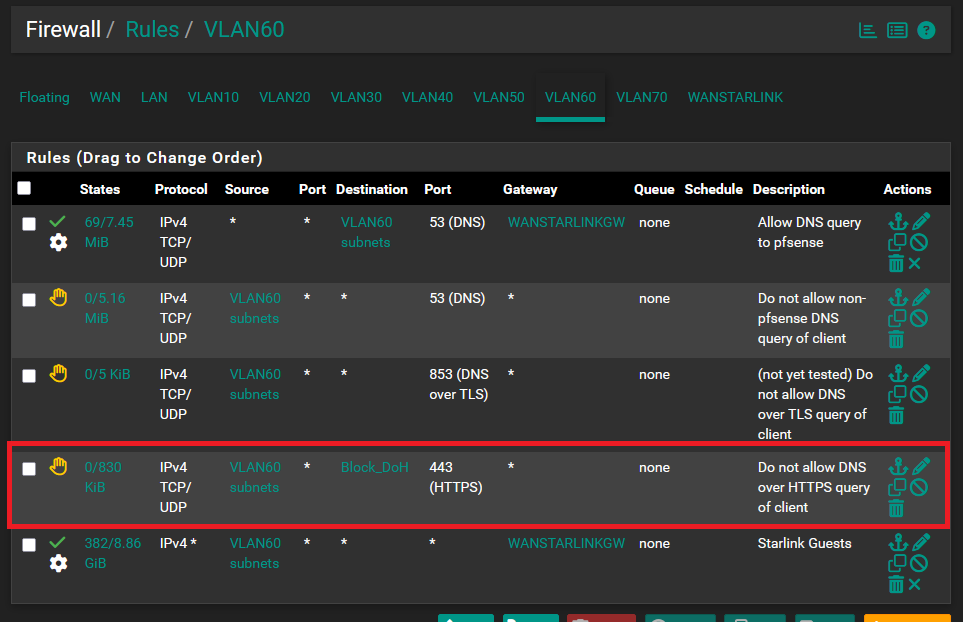
Created this alias:
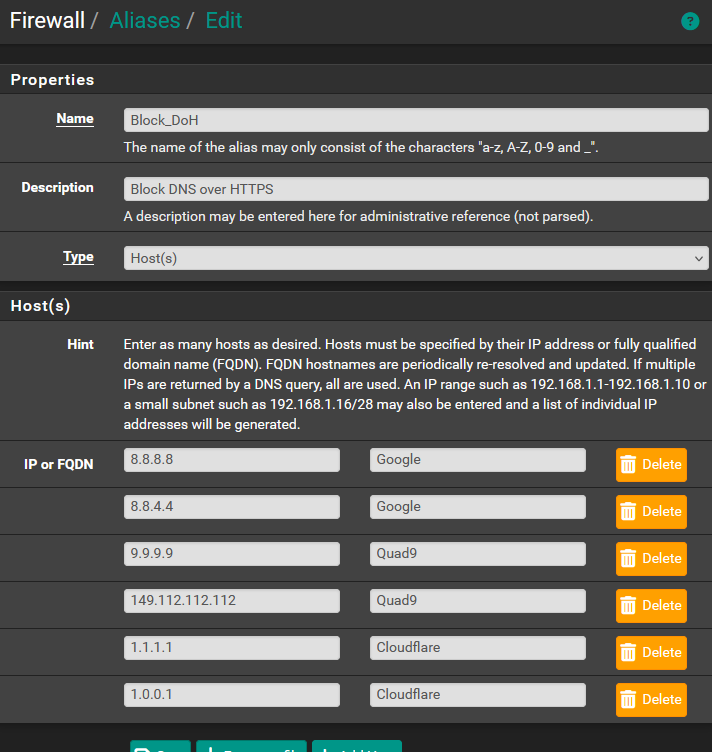
-
@richardsago said in How to block internet access for client operating system's DNS over HTTPS:
let me know if you have other DoH Servers
He showed you all the known DoH/Dot/DoQ server - see the list in pfBlockerng

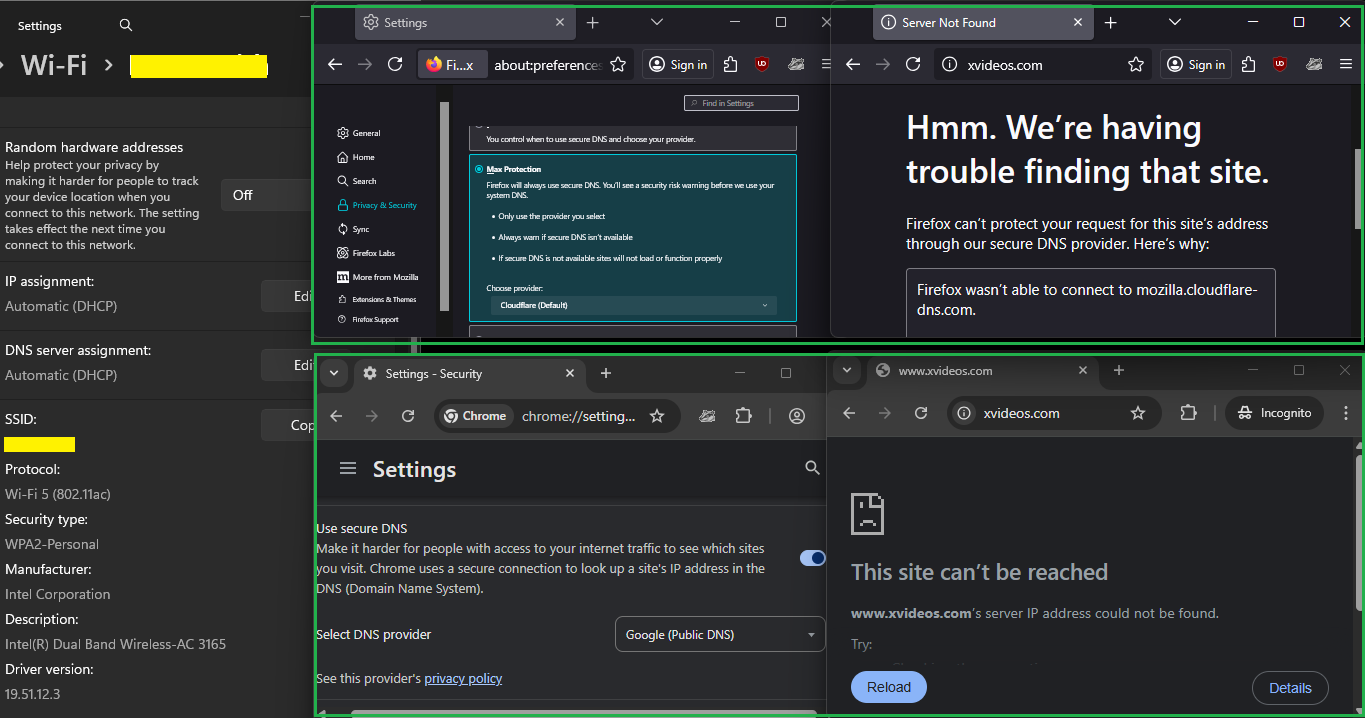
Example : when I switch from "Off" to the maximum protection mode in my browser :
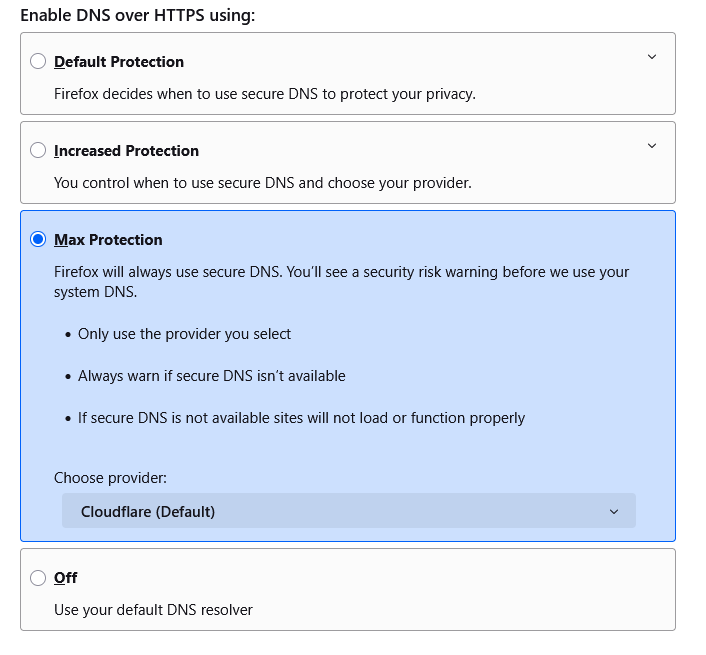
I couldn't visit nothing anymore : the browser showed :
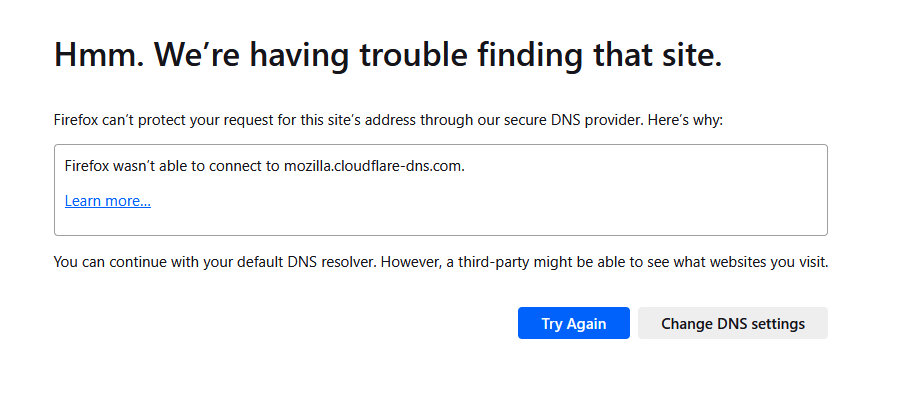
(Firefox uses mozilla.cloudflare-dns.com which was blocked)
That's what pfBlockerng does for me, I enbaled :
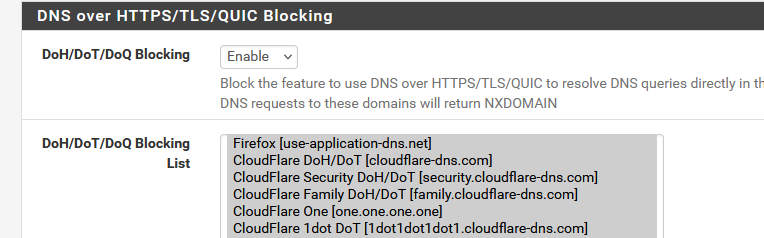
and done.
No need to maintain a list by myself. -
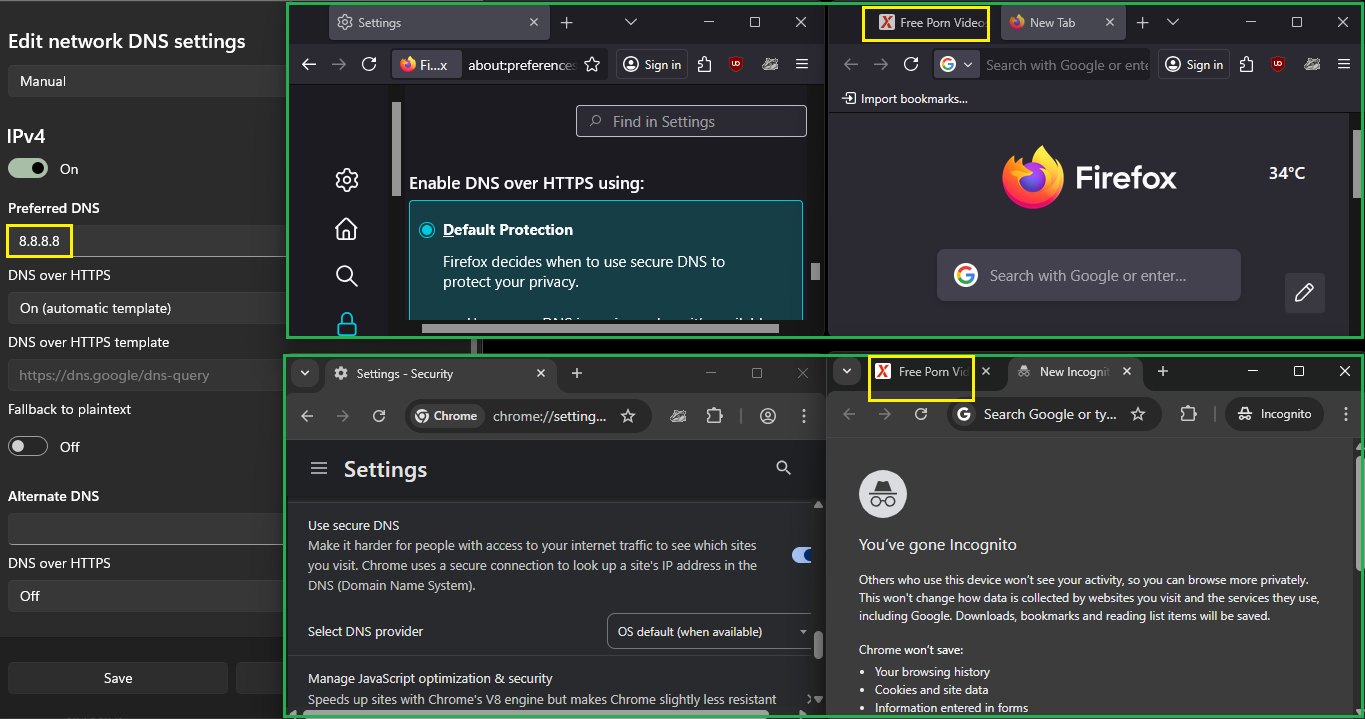
Thank you @Gertjan for the reply. The problem I wanted to solve was that users can bypass pfBlockerNG by activating DNS over HTTPS in the operating system. These are the steps to activate DoH in Windows 11 that will bypass pfBlockerNG if I will not use the firewall rule and alias in my last post:
-
Under Windows Settings go to the network settings and click the "DNS server assignment" button
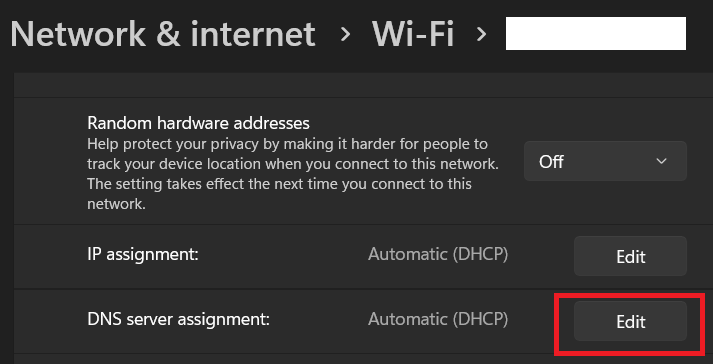
-
Click "Automatic (DHCP)"
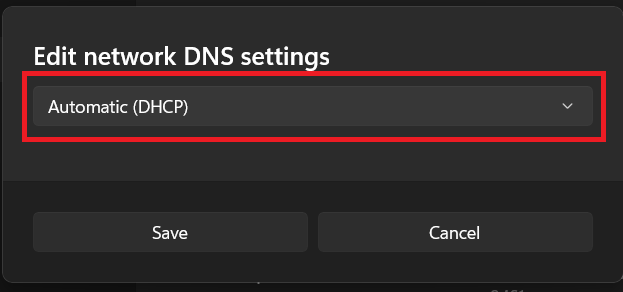
-
Choose "Manual"
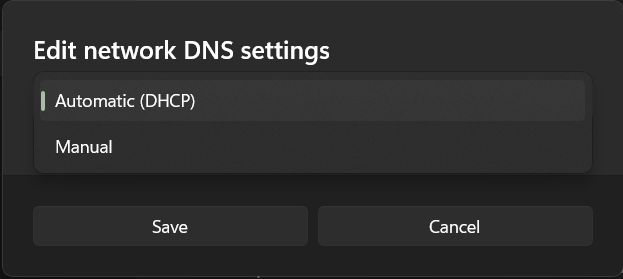
-
Click the IPv4 button to set it to ON value
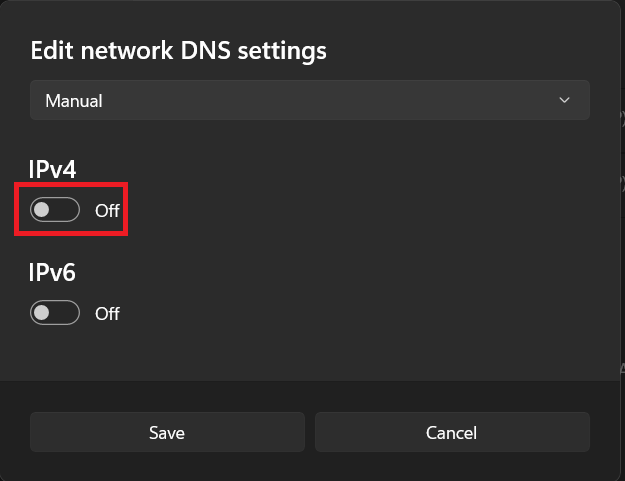
-
Set the "Preferred DNS" to 8.8.8.8, set "DNS over HTTPS" to "On (automatic template)", and the "DNS over HTTPS template" should automatically change to "https://dns.google/dns-query" value. Click the Save button
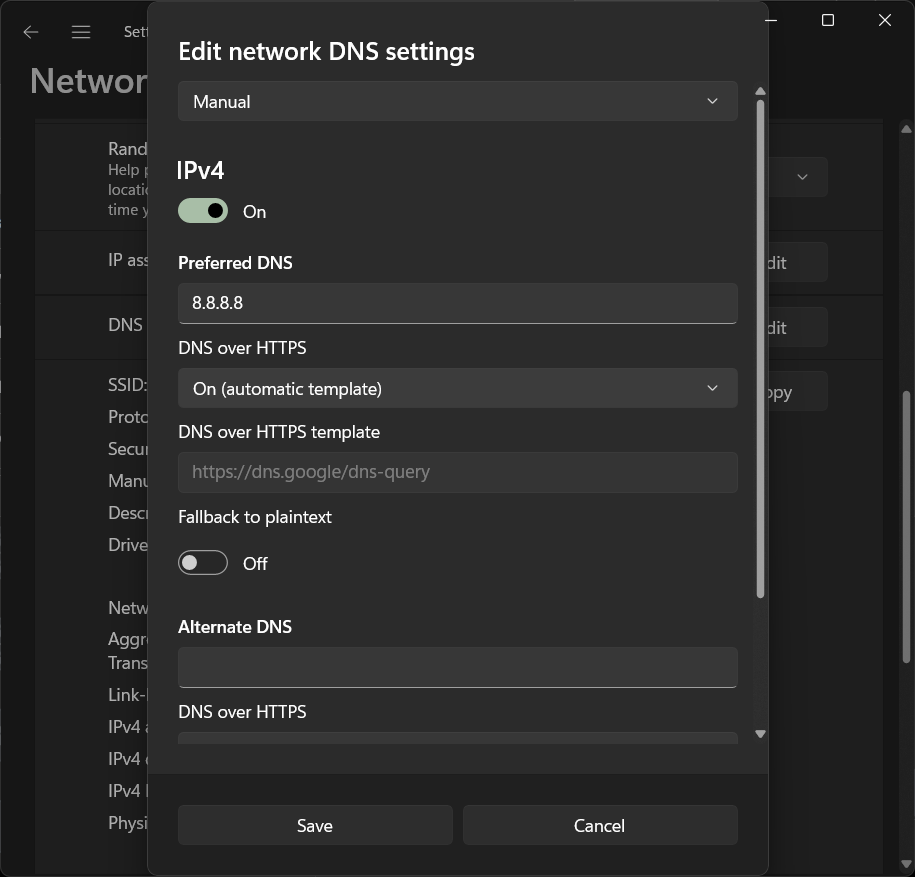
-
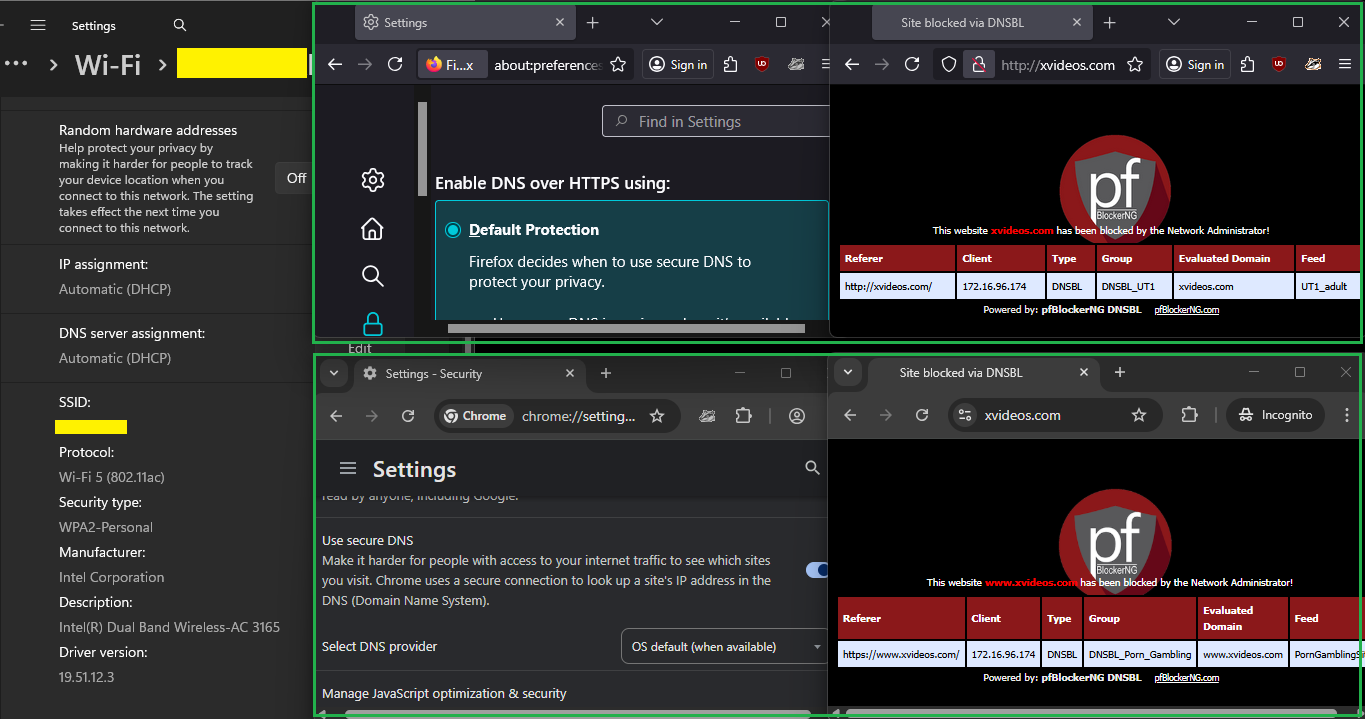
I open a website that's listed in the StevenBlack and it will successfully open and not blocked by pfBlockerNG. Please let me know if this is also the behavior in your system, because maybe there's a misconfiguration in my system. Thank you in advance.
-
-
@richardsago said in How to block internet access for client operating system's DNS over HTTPS:
These are the steps to activate DoH in Windows 11
Ok, I see.
The thing is, I can't test that right now.
Some one (== me, in the past) was using regedit or the policy editor to telle 'Windows' that it shouldn't use DoH or DoT.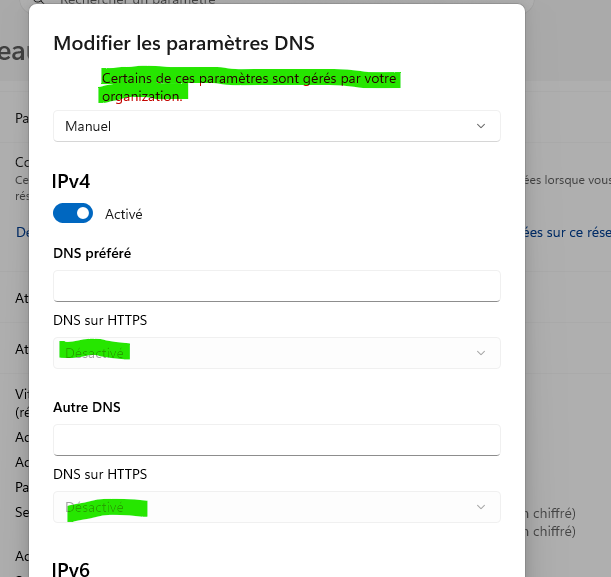
I have to undo these setting first ^^
That is : find how to undo them.But : whatever happens, my Windows device can not 'bypass' pfSense.
So, if it uses an IP that belongs to this list :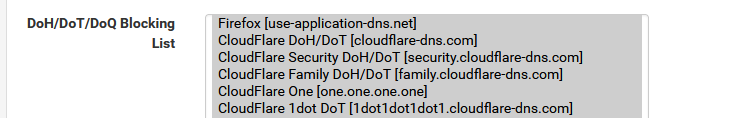
it will get blocked.
Btw : this list shows host names like "use-application-dns.net", so, first, the classic DNS has to be used, like asking pfSense IP (!) or 8.8.8.8 (IP !) or whatever your windows device is using as a 'classic' DNS, so it can / has to resolve "use-application-dns.net" first !
Then when it gets the IP of "use-application-dns.net", it will use this IP to do a DoT/DoH.
pfBlocker will block requests from your PC to resolve "use-application-dns.net", but if your Windows PC was using 8.8.8.8 (== bypassing the pfSense normal resolver DNS), then pfSense has to block all outgoing port 53 (== DNS requests) first.So requests going to the classic 8.8.8.8, 1.1.1.1 etc etc will have to be blocked also.
Makes sense as if you want to block Dot/Doh, start by blocking the normal outgoing (= not to pfSense) DNS requests.
This forces the (windows) device to use the pfSense LAN IP as its DNS. And there, requests for "use-application-dns.net" will get blocked, so DoH/DoT isn't possible anymore. -
@richardsago Are you flushing DNS on the Windows PC when testing? If it’s blocked in pfBlocker seems like your task is figuring out how dns.google resolves on it. The PC is only using pfSense for DNS?
-
I think you are on the right track with your With your DoH list on your firewall.
Here are two list i use.https://raw.githubusercontent.com/crypt0rr/public-doh-servers/refs/heads/main/ipv4.list
https://raw.githubusercontent.com/crypt0rr/public-doh-servers/refs/heads/main/ipv6.list
Here is how i have mine set up. go to firewall/aliases/ URLs click add. In properties change the URL type to tables. Add your list.
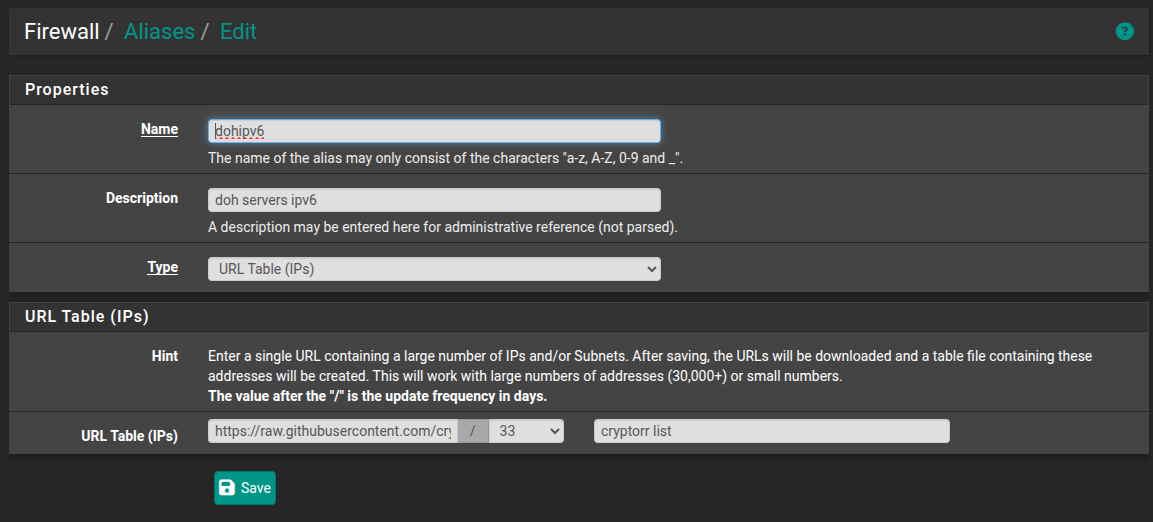
your update frequency will be stock at 128 days i set mine to 33. Save and then make your firewall rule.
There are more DoH list on github that are more aggressive.
-
Thank you @Gertjan for the reply. I will next try to solve the "Unbound python mode" for the next school break.
Thank you @SteveITS for the reply. I was not sure about dns flushing and browser cache issues so what I did was to restart the client PC each time I tested a DoH setting change in the operating system, and pressing shift + [refresh] multiple times on the browser when I typed a URL. The client computer is using pfSense for DNS, DHCP, and internet connection. In case I misunderstood the question this is the services status on the pfSense dashboard:
Thank you @Uglybrian for the suggestion. I have replaced my manual list with your auto-populated list.