Which kind of VIP to use? (5 statics)
-
I've got 4 ISP connections which I have interfaces for however my primary backup ISP gives me 5 statics.
So I would like to use one interface for this ISP (one interface for the 5 statics).
Which kind of VIP do I use for these? I understand that it should be easy and straightforward - simply create the VIP's & assign each a static…
Currently I have one cat 6 cable from the modem to an interface... I have one of the statics assigned "normally". Do I just create 4 VIP's??
Which kind?
Thx!
-
For this setup, I think I would use either Proxy ARP or IP Alias. I would probably prefer IP Alias since I think you can do more with it than with ProxyARP.
-
And then just NAT them to an individual LAN IP?
There is one of the statics that I would like to be on it's own subnet & DHCP on it's own. Essentially the main one runs most of the machines & internet and then the rest go to individual servers - all but one which goes to a few VM's that I let a friend remote into from europe. I want to keep his stuff on his own static & LAN subnet if possible.
Thank you very much for the reply!!
-
Yes, it sounds like you are going to want to use port forward natting and manual outbound nat.
-
I can ping all five public IP's from the LAN. I can ping static #1 from WAN but the rest time out???
I can not figure out how to assign two of the statics their own LAN subnets or how to assign individual servers each to each of the other statics. I was planning on using VLANs for the statics so that I can keep using only one switch and two interfaces (LAN & WAN). I'm still confused how to assign a public static IP to amachine that is currently on IP#1's LAN.
Does that make sense?
-
OK i'm really at a loss here. I have 5 static IP's. #1 is working fine (business is currently running off of static #1 right now.)
I have 6 interfaces - a quad card and a dual card. I have Static #1 and LAN working fine on the dual NIC. I would like to add four (4) VIP's so that each of the 4 remaining statics go to the VIP's. From there (to keep things simple) I would like to assign each if the unused 4 NIC interfaces each as a LAN interface for their respective remaining statics.
So 6 interfaces - one WAN and 5 LAN's.
I would like each of the LAN's to each be on it's own subnet. Can be as simple as 10.10.99.1, 10.10.99.2, 10.10.99.3, 10.10.99.4 & 10.10.99.5.
Not trying to complicate things however I am running PfSense as a VM so the reason I want each of the ststic IP's to DHCP and be on their own subnets is that they are different machines and the interface may/may not ever plug into a switch and then a machine - the static may just be forwarded to the VM's within the host.
So, I set up 4 VIP's with the following:
**Type: IP Alias
**Interface: WAN
**IP Address(es): xx.xx.xx.5 /29 (/29 because it says "this must be the network's subnet mask, It does not specify CIDR) and I was given a subnet mask of 255.255.255.248 from my ISP
**VIPassword: Grayed out/blank
**VHID Group: "1" (Grayed out at #1)
**Advertising Frequency: Base 1 Skew 0 both grayed out at those #'s
**Description: Whatever I want to writeCurrently the machine is running and configured as if I have a single static IP address - the WAN goes to the WAN and the LAN goes to the LAN. Everything else has not worked so I reverted back to my initial config before I started screwing with stuff.
EDIT: it's an Optimum cable modem. Cisco DPQ3925. There are four interfaces on the back of the modem - when I pluh my laptop into any spare interface and configure it for the available static IP it works fine - I don't think this modem is offered to dynamic IP clients so it should be PfSense issues only (pf is fine :) pf user is obviously not)
I followed these instructions but can't ping a thing or connect to anything.
http://www.youtube.com/watch?v=zrBr0N0WrTY -
Can anyone simply answer whether I should want to use IP Alias or Proxy ARP?
The Docs dont describe either of these well and my ISP is very picky about hypervisors.
-
YOu can use either in this case, but I would suggest IP Alias as you can do more with it.
Since you want to have more LANs, each NIC is going to have to be in a separate subnet not its own IP address. So it would be something like 10.10.91.1/24. 10.10.92.1/24 … and so on. Then you are going to have to switch to Advanced outbound NAT so that you can direct traffic from each subnet out different IP Aliases.
You will also have to create the default rule for each NIC/subnet. Once that is complete, then you can assign your VM to each of the different port groups and/or have multiple switches for system that are external to the VMs. -
YOu can use either in this case, but I would suggest IP Alias as you can do more with it.
Since you want to have more LANs, each NIC is going to have to be in a separate subnet not its own IP address. So it would be something like 10.10.91.1/24. 10.10.92.1/24 … and so on. Then you are going to have to switch to Advanced outbound NAT so that you can direct traffic from each subnet out different IP Aliases.
You will also have to create the default rule for each NIC/subnet. Once that is complete, then you can assign your VM to each of the different port groups and/or have multiple switches for system that are external to the VMs.Thank you so much for your reply. I chose IP Alias but since it wasn't working I was unsure of myself.
I have set up each individual interface as you described, 10.10.22.1/24, 10.10.33.1/24, 10.10.44.1/24 and 10.10.55.1/24. I can connect a machine to each NIC port externally and it DHCP's as well as able to connect a VM internally and that works as well. The interfaces and four extra internal subnets are fine.
I think that setting up the VIP's is also fine except that I can't ping them from anything and I can't get the NAT rules to work.
-
For ping to work, you have to create a rule to allow it. It is denied by default.
If you could, screen shot the Outbound NAT table and we can help see if it looks right. -
For ping to work, you have to create a rule to allow it. It is denied by default.
If you could, screen shot the Outbound NAT table and we can help see if it looks right.So I have all five subnets working however I still cant reach the internet from the VIP's and I also can't ping them (knowing that I may not yet have set up the proper ICMP alow rule for each VIP). My ISP can only see the #1 static working, not the four VIP's.
Here are the rules I have. I simply copies what the machine did when it switched over from auto to manual and auto populated the rules.
If there is anything else I can paste up please ask for it and I'll be happy to share. I am unable to hit the internet like this so something isnt configured properly either on the VIP side or on the NAT'ing side… I have not built any rules for any of the subnets - is that the simple item I overlooked? Thx.
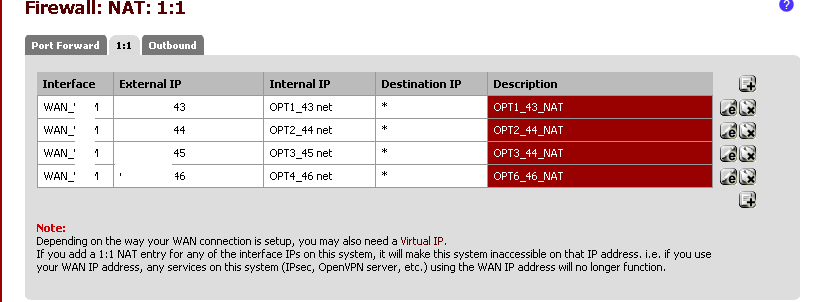
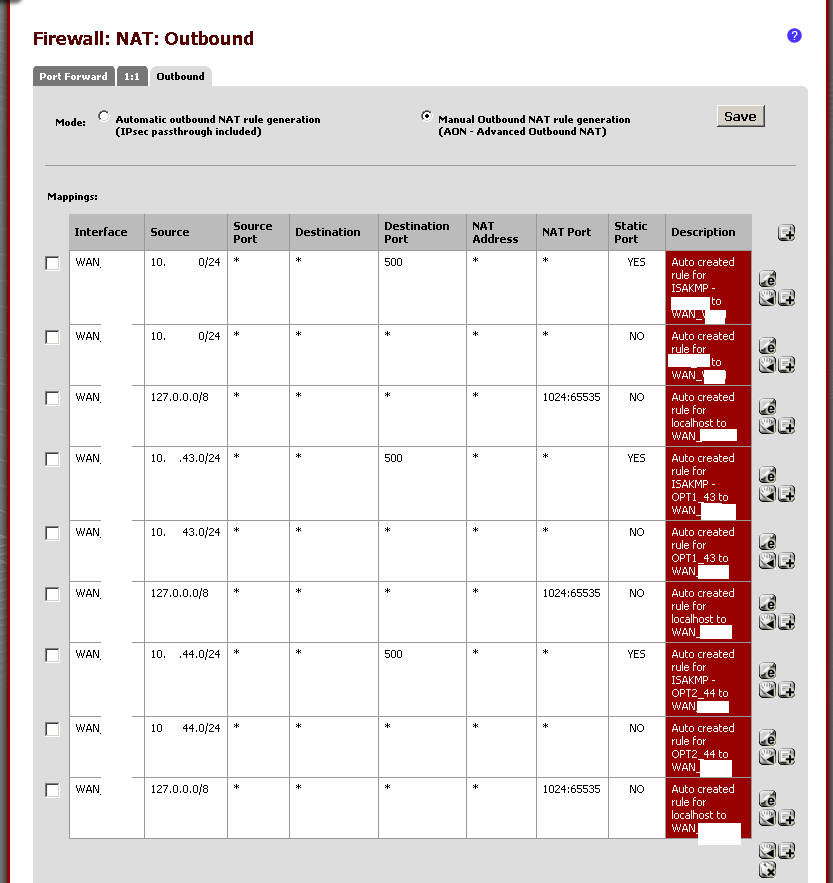
-
If you have not created the rules in each of the interface tabs in the firewall, you are going to by default block all access. Also, you do not need the 1:1 NATs, please remove them. Use only port forwards for the inbound services you absolutely need.
-
If you have not created the rules in each of the interface tabs in the firewall, you are going to by default block all access. Also, you do not need the 1:1 NATs, please remove them. Use only port forwards for the inbound services you absolutely need.
This is what I have for the rules tabs:
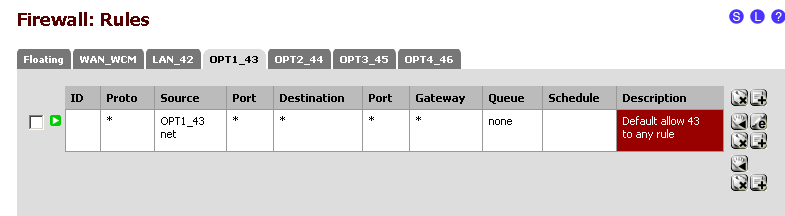
I am confused why you say to delete the 1:1 NAT in favor of port forwarding. These are remote desktop sessions behind the other static IP's not web servers so depending in what they are running it could require many many port forwarding mappings.
Do I need a rule under the WAN tab to allow from WAN to each interface or is that automatic with the VIP's? As of now there are only rules on the WAN tab regarding the static #1 not the other statics or other subnets.
Thx so much for your help.
EDIT: I can ping each static IP from it's respective subnet but still I can not reach the internet even with the rule to allow as I posted just above.
EDIT #2 - when I did nothing else but delete the 1:1 NAT's now I can get to the internet from each subnet but for some reason the traffic is only going through the primary IP, not the VIP's (when I go to ip chicken it gives me the primary IP) Should I put the 1:1 NATs back?
-
With the above setup/rules the VIP's are still dead to the outside world.
My ISP can only see that one of my 5 IP's are "configured" as they say.
I can ping them and see them from the LANs though.
-
The 1:1 NAT is for using and external IP for an internal IP. Remove them. Your systems are not servers so they only need outbound rules not inbound. Port Forwards and 1:1 are for servers behind a firewall and not systems. In the manual outbound NAT you MUST specify which VIP you want each subnet to use. The way you have it posted, you are going to use the WAN interface address.
-
I can't thank you enough!!! That worked!
Thanks - I will try and document this for others but at a minimum I will help others.
-
Now I have one final question - I kept it here but it may be a routing question??
Now that I have started to move over a few test machines to the static IP's I am realizing that I can't re-connect to them. Is the process for setting up ports, remote desktop and VNC pass through the same with VIP's or is that also more complicated.
Thx.
-
If you are trying to connect to them from the internet, the process is the same. If you are looking for inter-LAN communication, you should be able to access them via their internal IP address in the new subnet. The allow all rule you have on each LAN should pass all the communications.
If you want to restrict that, you are going to have to create a series of aliases and change the default rule.
If you are using DNS names, then I would use the DNS forwarder's override to create a split-brained DNS. This way if you are internal and you are using the pfSense firewall for DNS services, then when someone from the inside requests the DNS name they will get the internal address. But if you are on the internet, you get the VIP address.
I am sure there are more options as well depending on what exactly you are doing.
-
If you are trying to connect to them from the internet, the process is the same. If you are looking for inter-LAN communication, you should be able to access them via their internal IP address in the new subnet. The allow all rule you have on each LAN should pass all the communications.
If you want to restrict that, you are going to have to create a series of aliases and change the default rule.
If you are using DNS names, then I would use the DNS forwarder's override to create a split-brained DNS. This way if you are internal and you are using the pfSense firewall for DNS services, then when someone from the inside requests the DNS name they will get the internal address. But if you are on the internet, you get the VIP address.
I am sure there are more options as well depending on what exactly you are doing.
I got it sorted and I want to thank you publicly (not just by PM). I learned a lot during the process and I will make an effort to check the forum to try and help others.
Thanks again!! I appreciate the help.