Share your pfSense stories!
-
Mine is an unusual situation. I have for years been using an ASA5550 I picked up used probably 8 years ago. I had access to the firmware for that platform and its what we used at work so I could sometimes try things out at home. The thing was a tank. It was good for 1Gbps from LAN->WAN but had to share backplane from LAN->GUEST or LAN->ISOLATION (my workbench equipment) but that was fine for my needs. The two built in remote access VPN connections were enough for my needs and naturally it was fine for building S-2-S IPSec VPNs. It ran non-stop for all those years unless the power was out. Just rock-stable and reliable gear.
But with each year after it went EOL/EOS it became harder to keep it up. The issues with Java and all the security settings with the old ASDM GUI and later with browsers making TLS 1.1 a major PITA it was getting very involved to get into the GUI anymore. Sure, it has a rocking CLI but I'm visual and prefer seeing related parts of config. It's also a major electrical load to run every day every hour on top of my two other managed switches. I decided it was time to part ways with her.
I looked into Cisco gear again and the FP1100 but the price is just astronomical plus the requirement to pay yearly for every feature you want. That was a solid "no". Fortinet, SonicWall, and Sophos were others I looked at too but all would be locking me into some level of subscription and they are pretty pricy still for real 1Gbps throughput on all the inspections. I decided to take another look at pfSense to see how it had come along since I last saw it a decade ago.
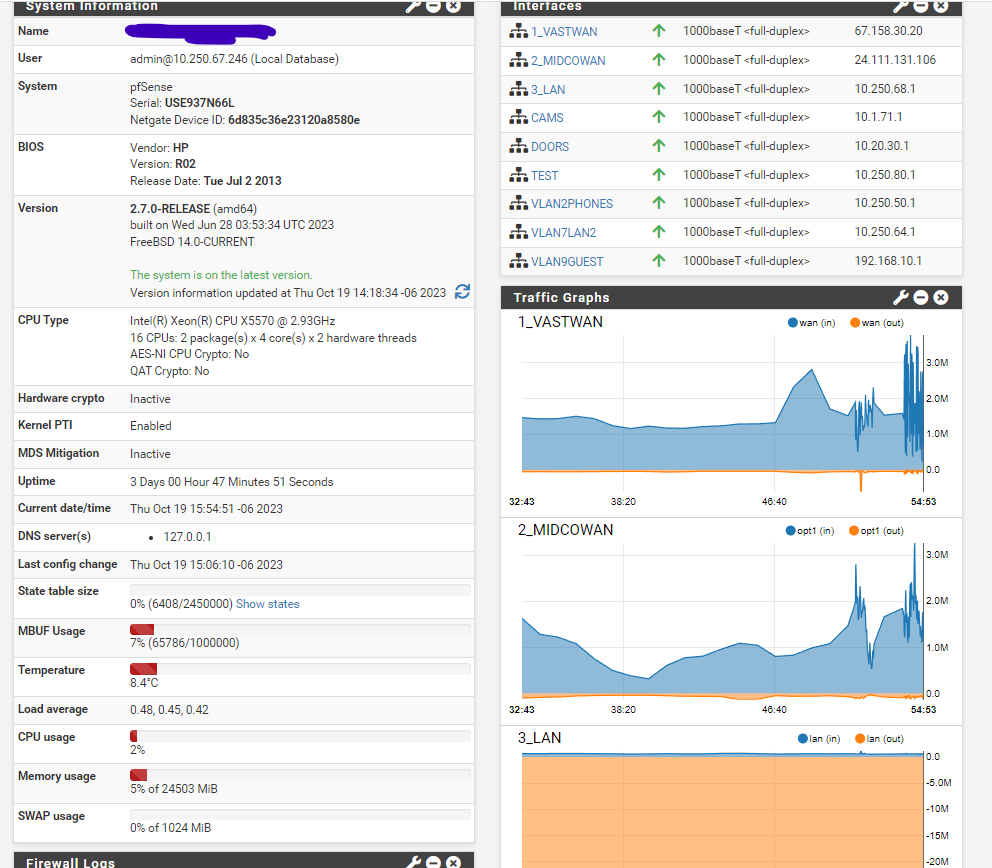
That brought me to the Netgate hardware and It didn't take long to decide. I settled on the 4100. The features needed were there, the interface was pretty nice and feature rich (vs the Unifi Dream Machine I was considering) and the specs looked really good. Everything I was doing on the ASA could be done here and in a smaller, quieter, lower power setup. I waffled between 6100 and 4100 but I think this is already overkill for my home network needs.
Watched a few videos to get up to speed after ordering and my equipment arrived in 2 days. It took me about 4 hours to get basic setup in place and get it put in parallel with the ASA. Worked immediately and with a few tests done I went ahead and swapped it into place on the internal network. Most of the family had no idea it even happened. Another 4 hours and I had most of my other networks grafted onto it.
Day two and I had incoming port forwards done. Certificate setup done. OpenVPN working, single-pipe traffic limiting on my guest network and per-ip traffic limiting on my internal network. I have a plan for setting up a site-2-site VPN with a friend in another city to allow remote backup to an off-site NAS. This I will probably use a Netgate 1100 to implement.
So far I am impressed with this platform and software. I think a little more documentation in the box would be nice and with an ASA background figuring out if I really want some of the "we did that for you" items can be a little bit hard but I really have no major negatives. There are aspects of the ASA, CLI, and ASDM GUI that I will miss but not many. This is FAR FAR more intuitive to setup and VPN is a complete snap by comparison. Over a decade and Cisco ASA VPN is still a nightmare to setup and admin. I was happy with how quickly I could each new feature bolted into place.
Impressive project and product. Nice to see an open source project go this long and mature this well AND not be arcane. Kudos and I feel I made a really solid choice if the hardware lasts and the updates are solid.
AT&T Fiber Internet
2 C3750-X 48 port full PoE switches w/routing (1 home, 1 outbuilding)
1 Netgate 4100
4 Main subnets (Internal, Guest, Shop, Isolation)
3 Wireless APs.
16 to 24 connected devices average.
Work from Home office in the Shop building. -
hello all. before all i want start saying my English is not very well, but the thins i can do with pfsense are really good and is thanks to this magnific software and a great community, i'm using pfsense from year 2007, i'm was coming from ASTARO community edition, now i manage ~12 pfsense servers, across network at my job, one the most challenger thing i done was scripting some bash and php jobs to copy the acme cert to some my internal pfsense with no internet access, for this reason i can validate the domain, i missing some removed additional package like mail relay.... i wold like something like a control center in pf-sense like astaro control center; yes, i remember i was manage all my appliances from a unique console, share alias and objects, build ipsec tunels bettwen some appliances and monitoring all from one location. i never have a security inccident on my net involving pfsense it is very very good, the recover on faillure are really fast, the web GUI are complete , and i wanna thanks to all people are making possible this
-
I want to build a raspberry pi statum 1 NTP server and use it with PfSense.
I just need this part..
Does anyone else use a statum one NTP server?
-
@JonathanLee said in Share your pfSense stories!:
Does anyone else use a statum one NTP server?
I use 3 of them, but they're public, not my own. This provides stratum 2 to my LAN.
-
I think my first pfSense install was on an AMD K6-233 homebuild that I had in a cool Cisco-green AT case, 3x 10Mb NICS. Had been running a floppy install of Smoothwall previously.
Second was an old Nokia ip530 Checkpoint box I was given by my old MIS boss around 2010. Still on shelf, runs v. 1.2.3. As I recall, it was around $16K new, p3-700/512MB which I upgraded to p3-1000 and a gig. Could boot both Nano from CF and Gmirror from HDD.
Documented here ip530Third was a retired Stonegate SSL appliance with a VIA 1000MHz proc and a gig of RAM plus 4 Realteks, and absolutely the SLOWEST 4GB SSD (2004 tech).
Fourth, I finally went VM on Server 2012R2, built when 32 bit was dropped after v. 2.3.5. Still kept as backup.
Fifth and current is a total overkill Adlink MXE-5401 with a Gen4 i7, 16GB, 64GB Industrial SSD and a 500GB laptop drive for logs. The MXE was a $2K box when new and I got it on Ebay for $65. Still only pulls 25w and runs 800MHz most of the time. and only had 4.5 years operating time according to the BIOS. Barring a lightning strike, it will likely last longer than I do.
-
After many years of owning garbage consumer grade routers that had horrible security, little customization, poor performance, and terrible stability, i began looking at OpenWRT and some other firmwares, then found an article about PFSENSE and it seemed like it would be worth a shot. I tried it initially on a very old Core 2 Quad board with an Intel NIC and after about a week i decided this was the gonna be my new router. So I did a little research and found an incredible deal on a Lenovo Think-Centre M700 Tiny with an i5-6500T and 8gb DDR4 for the low low price of $75 and all i needed to add was a SSD which i already had. I also removed the wifi card and replaced it with a Gigabit LAN adapter so it would have two gigabit ports. I then got it installed and its been great for the past year.
In fact, PFSENSE has been so good with zero crashes and great speed that i kinda just stopped checking in on it until yesterday and noticed there was a big update a while back and i will likely install it tonight later.
What also caught my attention was the uptime. If that isn't a great indicator of stability, i don't know what is.

-
@Andrew-LB said in Share your pfSense stories!:
What also caught my attention was the uptime. If that isn't a great indicator of stability, i don't know what is.
Once you get away from Windows, that's the norm. PfSense is built on FreeBSD, a Unix type system, just like Linux. Over the decades, there have been many stories about Netware or OS/2 servers that just keep on running. If pfSense fails, it's likely a hardware issue. That's certainly my experience, when the only time it failed for me was because the computer I was running it on died.
-
This guy takes the cake.
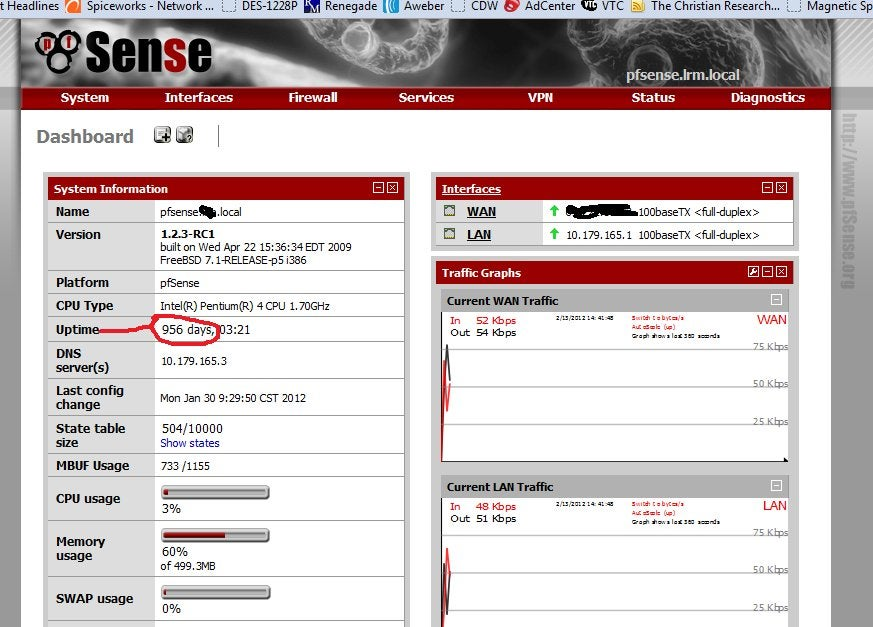
-
@nimrod said in Share your pfSense stories!:
This guy takes the cake.
I suspect it's about due for an update.

Several years ago, I heard about a Novell Netware server that nobody could find. It had been walled in and nobody noticed it, because it just kept on working. Windows got us into the expectation computers are supposed to have problems. I used to be an OS/2 product specialist at IBM Canada. I provided 3rd level OS/2 support, as well as some apps on OS/2, Windows 95 and NT. I was also on the team that built standard systems for IBM Canada employees. There were very few problems on OS/2, some on NT and lots on W95. Years before I started at IBM, I was a computer tech, working on Data General Eclipse computers, VAX 11/780s and others. Again, they were very reliable.
-
@nimrod I have 3 routers getting close... @ version 2.5.1.
-
@JKnott said in Share your pfSense stories!:
Data General Eclipse computers, VAX 11/780s and others. Again, they were very reliable.
Ditto, same experience. Unfortunately, technical superiority does not guarantee success. I miss VMS & VAXELN. I'm glad Dave Cutler tried to set MS on the right path with NT - too bad it went sideways for a while.
-
@MaxK-0 said in Share your pfSense stories!:
I miss VMS & VAXELN.
The problem is technology moves on. I recall reading an article that said the new Intel 80386 CPU was as powerful as a VAX 11/780. I then realized I was working in a dying industry. A typical personal computer is far more powerful than those VAX computers were.
-
@JKnott said in Share your pfSense stories!:
Over the decades, there have been many stories about Netware or OS/2 servers that just keep on running.
-
At my 1st IT job, I deployed 40+ pfSense installed on Protectli mini PC. It was my first adventure into firewalling and I was learning on the go along with many network concepts how to configure all of them. They are all around Virginia, Maryland, and Washington DC connected via MPLS over IPSec serving over 400+ employees in the Medical/Insurance field. I left the company over 3 years ago and don't do many firewalls anymore but keep my pfSense on my work desk to test various ideas.
-
@pfrickroll said in Share your pfSense stories!:
connected via MPLS over IPSec
Wouldn't that be IPSec over IP over MPLS? MPLS is layer 2.5 and usually provided by the carrier.
-
Mine may be typical, maybe not.....
Took over a large sennior living facility with a pretty robust it infrastructure spread between 4 IT rooms, 23 access points, 12-14 switches, and 200 internal devices and 200 guest/resident devices, all being run by a Sonicwall TZ350. I had been wanting to reallign everything network wise for some time but the TZ had 2 ports that were failing. I had worked with ClearOS from back in the ClarkConnect days and started searching for something similar. I found PfSense and it just fit what I wanted to do.
I tested it a bit on an old Athalon64x2 rig for proof of concept and had planned on installing on a mini pc or something, but I wanted 6 nics. Standing in my main IT room I looked down and in the bottom of the rack were 4 HP DL380s, 2 of which were decommissioned 2 years ago. It's such huge overkill for hardware that it's hard to explain, but who wouldn't want redundant power supplies, raid 60 with 25 drives and remote system monitoring through ILO? lolI spun one up and loaded PfSense and started tweaking. 2 weeks ago I switched over and have been working out gremlins since.. Overall it's gone well, just one snag that a couple members here have been very kind in helping me work out. Thank you to this page for all the help.