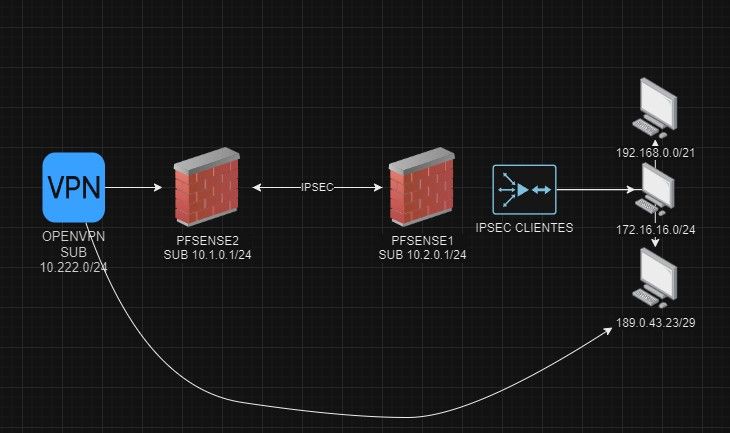
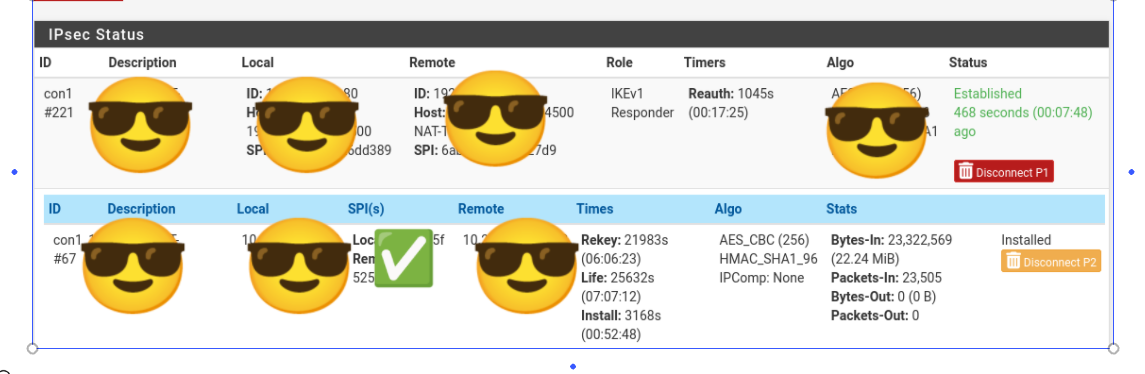
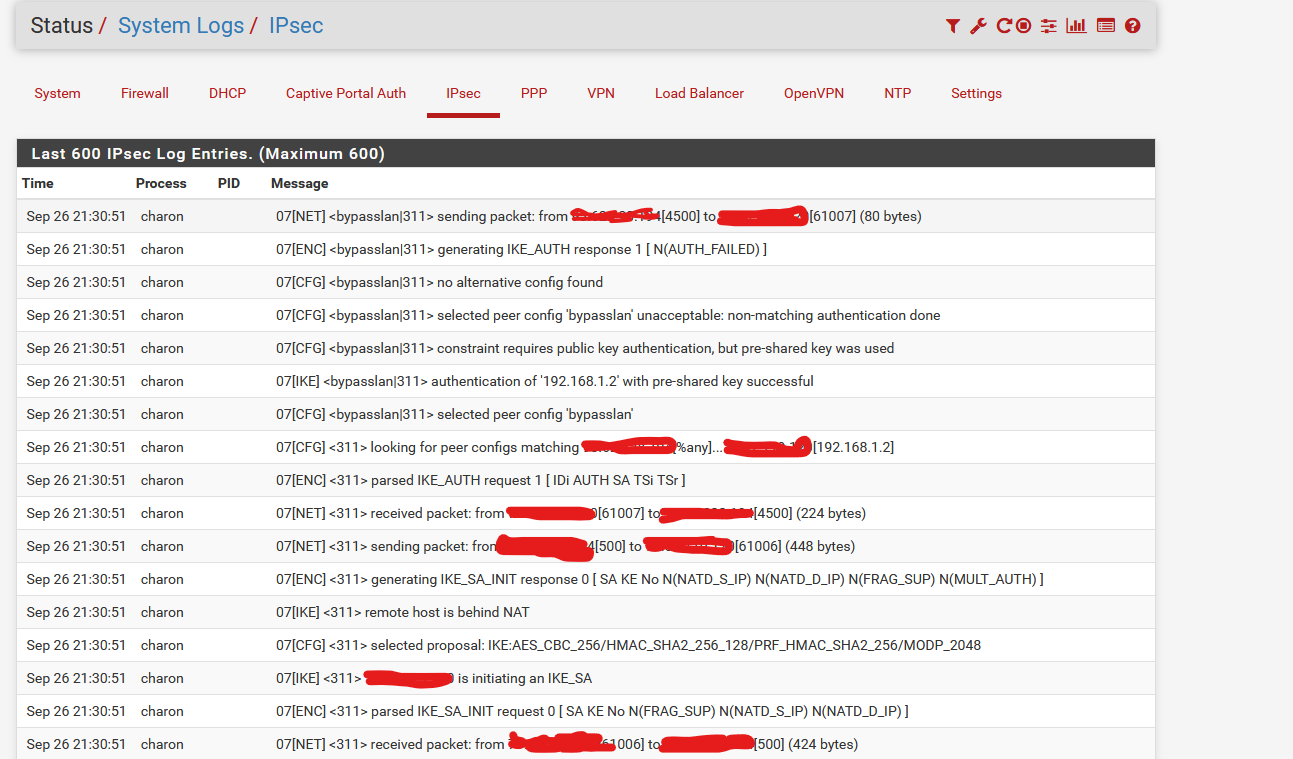
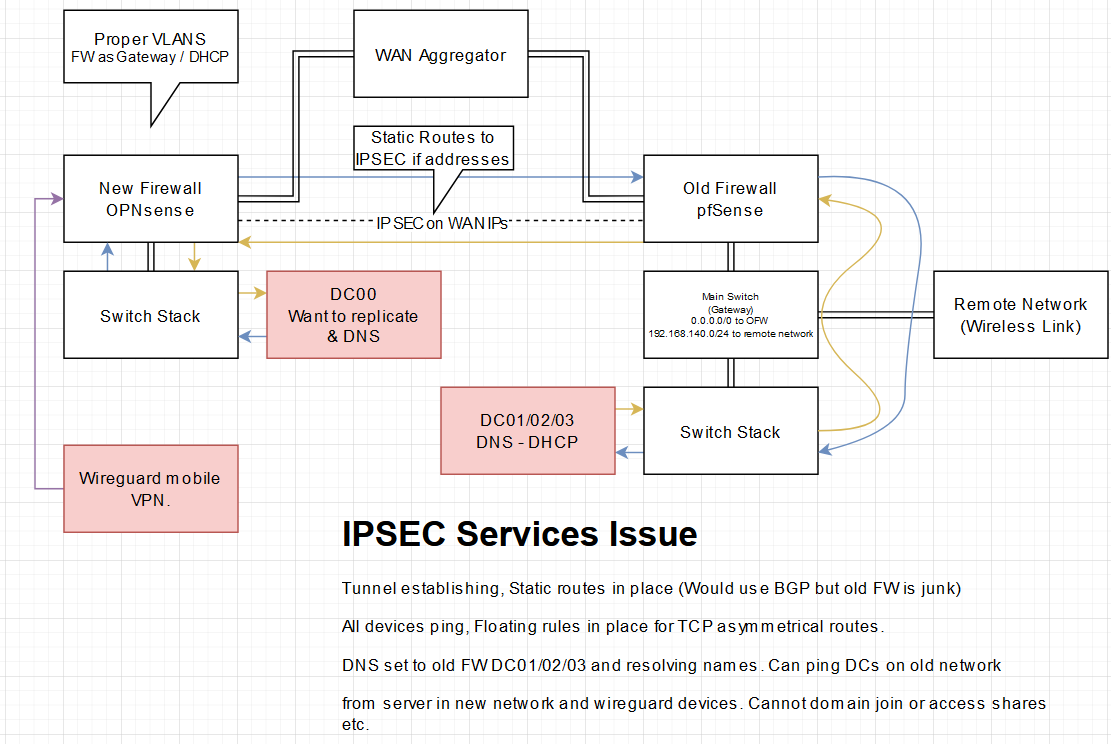
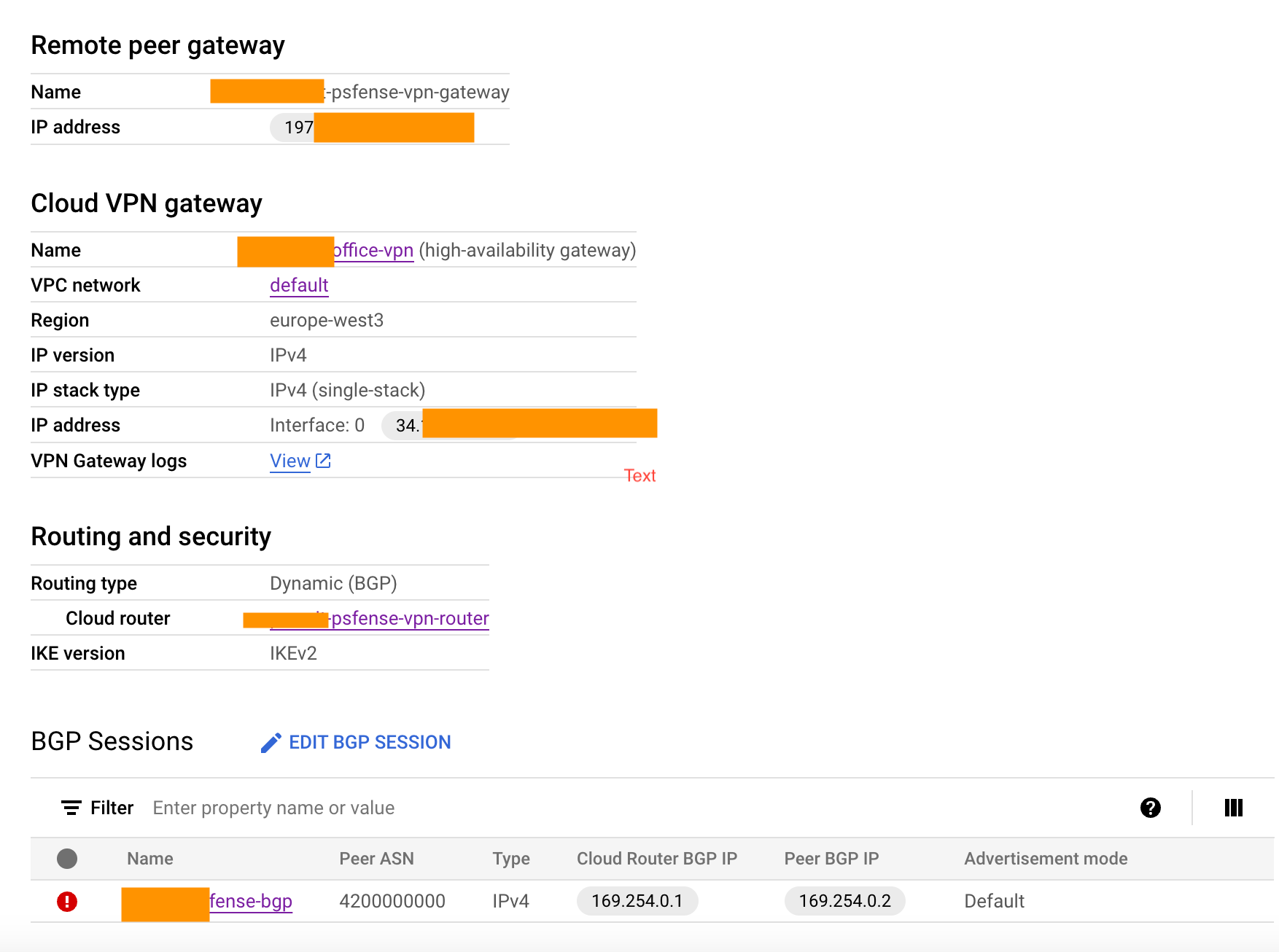
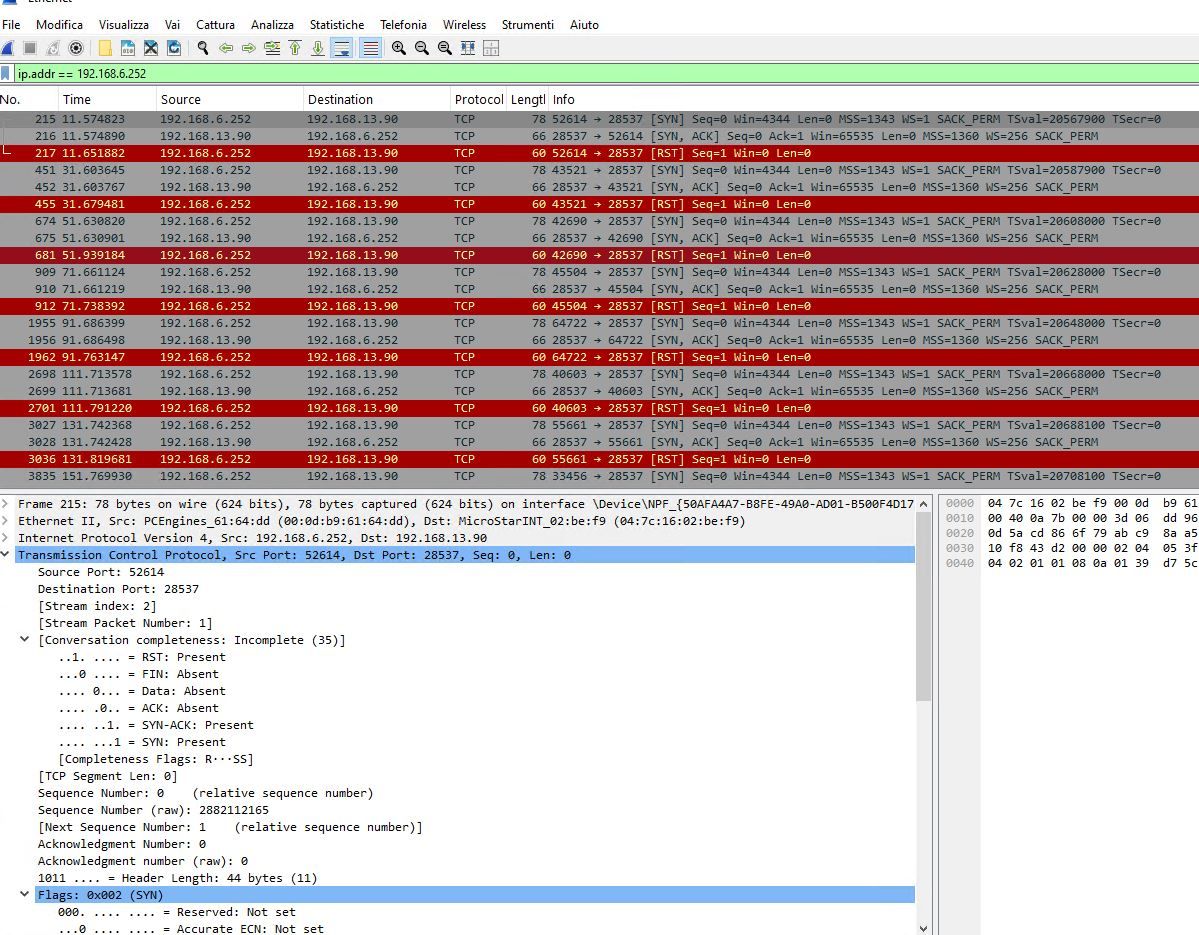
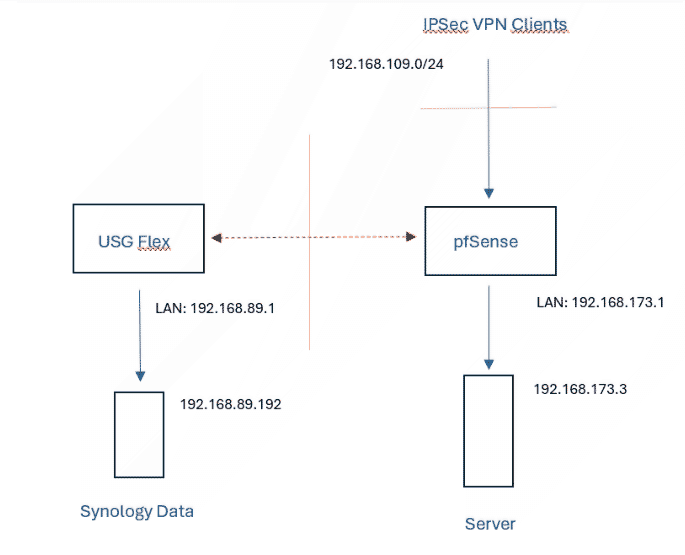
Here is the log informatin I get when trying to ping from one of hte remote sites:
Oct 4 08:53:19 charon 80307 12[KNL] <con3|370> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:19 charon 80307 12[KNL] <con3|370> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:19 charon 80307 12[IKE] <con3|370> sending DPD request
Oct 4 08:53:19 charon 80307 12[IKE] <con3|370> queueing IKE_DPD task
Oct 4 08:53:19 charon 80307 12[IKE] <con3|370> activating new tasks
Oct 4 08:53:19 charon 80307 12[IKE] <con3|370> activating IKE_DPD task
Oct 4 08:53:19 charon 80307 12[ENC] <con3|370> generating INFORMATIONAL request 2250 [ ]
Oct 4 08:53:19 charon 80307 12[NET] <con3|370> sending packet: from 50.169.69.234[500] to 50.169.69.203[500] (80 bytes)
Oct 4 08:53:19 charon 80307 12[NET] <con3|370> received packet: from 50.169.69.203[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:19 charon 80307 12[ENC] <con3|370> parsed INFORMATIONAL response 2250 [ ]
Oct 4 08:53:19 charon 80307 12[IKE] <con3|370> activating new tasks
Oct 4 08:53:19 charon 80307 12[IKE] <con3|370> nothing to initiate
Oct 4 08:53:22 charon 80307 12[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:22 charon 80307 12[ENC] <con1|366> parsed INFORMATIONAL request 12680 [ ]
Oct 4 08:53:22 charon 80307 12[ENC] <con1|366> generating INFORMATIONAL response 12680 [ ]
Oct 4 08:53:22 charon 80307 12[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:22 charon 80307 12[KNL] <con2|371> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:22 charon 80307 12[KNL] <con2|371> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:22 charon 80307 12[IKE] <con2|371> sending DPD request
Oct 4 08:53:22 charon 80307 12[IKE] <con2|371> queueing IKE_DPD task
Oct 4 08:53:22 charon 80307 12[IKE] <con2|371> activating new tasks
Oct 4 08:53:22 charon 80307 12[IKE] <con2|371> activating IKE_DPD task
Oct 4 08:53:22 charon 80307 12[ENC] <con2|371> generating INFORMATIONAL request 1086 [ ]
Oct 4 08:53:22 charon 80307 12[NET] <con2|371> sending packet: from 50.169.69.234[500] to 50.169.69.219[500] (80 bytes)
Oct 4 08:53:22 charon 80307 12[NET] <con2|371> received packet: from 50.169.69.219[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:22 charon 80307 12[ENC] <con2|371> parsed INFORMATIONAL response 1086 [ ]
Oct 4 08:53:22 charon 80307 12[IKE] <con2|371> activating new tasks
Oct 4 08:53:22 charon 80307 12[IKE] <con2|371> nothing to initiate
Oct 4 08:53:27 charon 80307 11[IKE] <con4|372> sending DPD request
Oct 4 08:53:27 charon 80307 11[IKE] <con4|372> queueing IKE_DPD task
Oct 4 08:53:27 charon 80307 11[IKE] <con4|372> activating new tasks
Oct 4 08:53:27 charon 80307 11[IKE] <con4|372> activating IKE_DPD task
Oct 4 08:53:27 charon 80307 11[ENC] <con4|372> generating INFORMATIONAL request 93 [ ]
Oct 4 08:53:27 charon 80307 11[NET] <con4|372> sending packet: from 50.169.69.234[500] to 192.158.19.11[500] (80 bytes)
Oct 4 08:53:27 charon 80307 11[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:27 charon 80307 11[ENC] <con1|366> parsed INFORMATIONAL request 12681 [ ]
Oct 4 08:53:27 charon 80307 11[ENC] <con1|366> generating INFORMATIONAL response 12681 [ ]
Oct 4 08:53:27 charon 80307 11[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:27 charon 80307 11[NET] <con4|372> received packet: from 192.158.19.11[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:27 charon 80307 11[ENC] <con4|372> parsed INFORMATIONAL response 93 [ ]
Oct 4 08:53:27 charon 80307 11[IKE] <con4|372> activating new tasks
Oct 4 08:53:27 charon 80307 11[IKE] <con4|372> nothing to initiate
Oct 4 08:53:29 charon 80307 11[KNL] <con3|370> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:29 charon 80307 11[KNL] <con3|370> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:29 charon 80307 11[IKE] <con3|370> sending DPD request
Oct 4 08:53:29 charon 80307 11[IKE] <con3|370> queueing IKE_DPD task
Oct 4 08:53:29 charon 80307 11[IKE] <con3|370> activating new tasks
Oct 4 08:53:29 charon 80307 11[IKE] <con3|370> activating IKE_DPD task
Oct 4 08:53:29 charon 80307 11[ENC] <con3|370> generating INFORMATIONAL request 2251 [ ]
Oct 4 08:53:29 charon 80307 11[NET] <con3|370> sending packet: from 50.169.69.234[500] to 50.169.69.203[500] (80 bytes)
Oct 4 08:53:29 charon 80307 11[NET] <con3|370> received packet: from 50.169.69.203[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:29 charon 80307 11[ENC] <con3|370> parsed INFORMATIONAL response 2251 [ ]
Oct 4 08:53:29 charon 80307 11[IKE] <con3|370> activating new tasks
Oct 4 08:53:29 charon 80307 11[IKE] <con3|370> nothing to initiate
Oct 4 08:53:32 charon 80307 11[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:32 charon 80307 11[ENC] <con1|366> parsed INFORMATIONAL request 12682 [ ]
Oct 4 08:53:32 charon 80307 11[ENC] <con1|366> generating INFORMATIONAL response 12682 [ ]
Oct 4 08:53:32 charon 80307 11[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:32 charon 80307 11[KNL] <con2|371> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:32 charon 80307 11[KNL] <con2|371> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:32 charon 80307 11[IKE] <con2|371> sending DPD request
Oct 4 08:53:32 charon 80307 11[IKE] <con2|371> queueing IKE_DPD task
Oct 4 08:53:32 charon 80307 11[IKE] <con2|371> activating new tasks
Oct 4 08:53:32 charon 80307 11[IKE] <con2|371> activating IKE_DPD task
Oct 4 08:53:32 charon 80307 11[ENC] <con2|371> generating INFORMATIONAL request 1087 [ ]
Oct 4 08:53:32 charon 80307 11[NET] <con2|371> sending packet: from 50.169.69.234[500] to 50.169.69.219[500] (80 bytes)
Oct 4 08:53:32 charon 80307 11[NET] <con2|371> received packet: from 50.169.69.219[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:32 charon 80307 11[ENC] <con2|371> parsed INFORMATIONAL response 1087 [ ]
Oct 4 08:53:32 charon 80307 11[IKE] <con2|371> activating new tasks
Oct 4 08:53:32 charon 80307 11[IKE] <con2|371> nothing to initiate
Oct 4 08:53:37 charon 80307 11[IKE] <con4|372> sending DPD request
Oct 4 08:53:37 charon 80307 11[IKE] <con4|372> queueing IKE_DPD task
Oct 4 08:53:37 charon 80307 11[IKE] <con4|372> activating new tasks
Oct 4 08:53:37 charon 80307 11[IKE] <con4|372> activating IKE_DPD task
Oct 4 08:53:37 charon 80307 11[ENC] <con4|372> generating INFORMATIONAL request 94 [ ]
Oct 4 08:53:37 charon 80307 11[NET] <con4|372> sending packet: from 50.169.69.234[500] to 192.158.19.11[500] (80 bytes)
Oct 4 08:53:37 charon 80307 09[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:37 charon 80307 09[ENC] <con1|366> parsed INFORMATIONAL request 12683 [ ]
Oct 4 08:53:37 charon 80307 09[ENC] <con1|366> generating INFORMATIONAL response 12683 [ ]
Oct 4 08:53:37 charon 80307 09[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:37 charon 80307 09[NET] <con4|372> received packet: from 192.158.19.11[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:37 charon 80307 09[ENC] <con4|372> parsed INFORMATIONAL response 94 [ ]
Oct 4 08:53:37 charon 80307 09[IKE] <con4|372> activating new tasks
Oct 4 08:53:37 charon 80307 09[IKE] <con4|372> nothing to initiate
Oct 4 08:53:39 charon 80307 09[KNL] <con3|370> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:39 charon 80307 09[KNL] <con3|370> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:39 charon 80307 09[IKE] <con3|370> sending DPD request
Oct 4 08:53:39 charon 80307 09[IKE] <con3|370> queueing IKE_DPD task
Oct 4 08:53:39 charon 80307 09[IKE] <con3|370> activating new tasks
Oct 4 08:53:39 charon 80307 09[IKE] <con3|370> activating IKE_DPD task
Oct 4 08:53:39 charon 80307 09[ENC] <con3|370> generating INFORMATIONAL request 2252 [ ]
Oct 4 08:53:39 charon 80307 09[NET] <con3|370> sending packet: from 50.169.69.234[500] to 50.169.69.203[500] (80 bytes)
Oct 4 08:53:39 charon 80307 09[NET] <con3|370> received packet: from 50.169.69.203[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:39 charon 80307 09[ENC] <con3|370> parsed INFORMATIONAL response 2252 [ ]
Oct 4 08:53:39 charon 80307 09[IKE] <con3|370> activating new tasks
Oct 4 08:53:39 charon 80307 09[IKE] <con3|370> nothing to initiate
Oct 4 08:53:42 charon 80307 09[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:42 charon 80307 09[ENC] <con1|366> parsed INFORMATIONAL request 12684 [ ]
Oct 4 08:53:42 charon 80307 09[ENC] <con1|366> generating INFORMATIONAL response 12684 [ ]
Oct 4 08:53:42 charon 80307 09[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:42 charon 80307 09[KNL] <con2|371> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:42 charon 80307 09[KNL] <con2|371> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:42 charon 80307 09[IKE] <con2|371> sending DPD request
Oct 4 08:53:42 charon 80307 09[IKE] <con2|371> queueing IKE_DPD task
Oct 4 08:53:42 charon 80307 09[IKE] <con2|371> activating new tasks
Oct 4 08:53:42 charon 80307 09[IKE] <con2|371> activating IKE_DPD task
Oct 4 08:53:42 charon 80307 09[ENC] <con2|371> generating INFORMATIONAL request 1088 [ ]
Oct 4 08:53:42 charon 80307 09[NET] <con2|371> sending packet: from 50.169.69.234[500] to 50.169.69.219[500] (80 bytes)
Oct 4 08:53:42 charon 80307 09[NET] <con2|371> received packet: from 50.169.69.219[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:42 charon 80307 09[ENC] <con2|371> parsed INFORMATIONAL response 1088 [ ]
Oct 4 08:53:42 charon 80307 09[IKE] <con2|371> activating new tasks
Oct 4 08:53:42 charon 80307 09[IKE] <con2|371> nothing to initiate
Oct 4 08:53:47 charon 80307 09[IKE] <con4|372> sending DPD request
Oct 4 08:53:47 charon 80307 09[IKE] <con4|372> queueing IKE_DPD task
Oct 4 08:53:47 charon 80307 09[IKE] <con4|372> activating new tasks
Oct 4 08:53:47 charon 80307 09[IKE] <con4|372> activating IKE_DPD task
Oct 4 08:53:47 charon 80307 09[ENC] <con4|372> generating INFORMATIONAL request 95 [ ]
Oct 4 08:53:47 charon 80307 09[NET] <con4|372> sending packet: from 50.169.69.234[500] to 192.158.19.11[500] (80 bytes)
Oct 4 08:53:47 charon 80307 09[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:47 charon 80307 09[ENC] <con1|366> parsed INFORMATIONAL request 12685 [ ]
Oct 4 08:53:47 charon 80307 09[ENC] <con1|366> generating INFORMATIONAL response 12685 [ ]
Oct 4 08:53:47 charon 80307 09[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:47 charon 80307 09[NET] <con4|372> received packet: from 192.158.19.11[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:47 charon 80307 09[ENC] <con4|372> parsed INFORMATIONAL response 95 [ ]
Oct 4 08:53:47 charon 80307 09[IKE] <con4|372> activating new tasks
Oct 4 08:53:47 charon 80307 09[IKE] <con4|372> nothing to initiate
Oct 4 08:53:49 charon 80307 09[KNL] <con3|370> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:49 charon 80307 09[KNL] <con3|370> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:49 charon 80307 09[IKE] <con3|370> sending DPD request
Oct 4 08:53:49 charon 80307 09[IKE] <con3|370> queueing IKE_DPD task
Oct 4 08:53:49 charon 80307 09[IKE] <con3|370> activating new tasks
Oct 4 08:53:49 charon 80307 09[IKE] <con3|370> activating IKE_DPD task
Oct 4 08:53:49 charon 80307 09[ENC] <con3|370> generating INFORMATIONAL request 2253 [ ]
Oct 4 08:53:49 charon 80307 09[NET] <con3|370> sending packet: from 50.169.69.234[500] to 50.169.69.203[500] (80 bytes)
Oct 4 08:53:49 charon 80307 10[NET] <con3|370> received packet: from 50.169.69.203[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:49 charon 80307 10[ENC] <con3|370> parsed INFORMATIONAL response 2253 [ ]
Oct 4 08:53:49 charon 80307 10[IKE] <con3|370> activating new tasks
Oct 4 08:53:49 charon 80307 10[IKE] <con3|370> nothing to initiate
Oct 4 08:53:52 charon 80307 10[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:52 charon 80307 10[ENC] <con1|366> parsed INFORMATIONAL request 12686 [ ]
Oct 4 08:53:52 charon 80307 10[ENC] <con1|366> generating INFORMATIONAL response 12686 [ ]
Oct 4 08:53:52 charon 80307 10[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:52 charon 80307 10[KNL] <con2|371> querying policy 0.0.0.0/0|/0 === 0.0.0.0/0|/0 in failed, not found
Oct 4 08:53:52 charon 80307 10[KNL] <con2|371> querying policy ::/0|/0 === ::/0|/0 in failed, not found
Oct 4 08:53:52 charon 80307 10[IKE] <con2|371> sending DPD request
Oct 4 08:53:52 charon 80307 10[IKE] <con2|371> queueing IKE_DPD task
Oct 4 08:53:52 charon 80307 10[IKE] <con2|371> activating new tasks
Oct 4 08:53:52 charon 80307 10[IKE] <con2|371> activating IKE_DPD task
Oct 4 08:53:52 charon 80307 10[ENC] <con2|371> generating INFORMATIONAL request 1089 [ ]
Oct 4 08:53:52 charon 80307 10[NET] <con2|371> sending packet: from 50.169.69.234[500] to 50.169.69.219[500] (80 bytes)
Oct 4 08:53:52 charon 80307 10[NET] <con2|371> received packet: from 50.169.69.219[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:52 charon 80307 10[ENC] <con2|371> parsed INFORMATIONAL response 1089 [ ]
Oct 4 08:53:52 charon 80307 10[IKE] <con2|371> activating new tasks
Oct 4 08:53:52 charon 80307 10[IKE] <con2|371> nothing to initiate
Oct 4 08:53:57 charon 80307 10[IKE] <con4|372> sending DPD request
Oct 4 08:53:57 charon 80307 10[IKE] <con4|372> queueing IKE_DPD task
Oct 4 08:53:57 charon 80307 10[IKE] <con4|372> activating new tasks
Oct 4 08:53:57 charon 80307 10[IKE] <con4|372> activating IKE_DPD task
Oct 4 08:53:57 charon 80307 10[ENC] <con4|372> generating INFORMATIONAL request 96 [ ]
Oct 4 08:53:57 charon 80307 10[NET] <con4|372> sending packet: from 50.169.69.234[500] to 192.158.19.11[500] (80 bytes)
Oct 4 08:53:57 charon 80307 10[NET] <con1|366> received packet: from 66.207.143.1[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:57 charon 80307 10[ENC] <con1|366> parsed INFORMATIONAL request 12687 [ ]
Oct 4 08:53:57 charon 80307 10[ENC] <con1|366> generating INFORMATIONAL response 12687 [ ]
Oct 4 08:53:57 charon 80307 10[NET] <con1|366> sending packet: from 50.169.69.234[500] to 66.207.143.1[500] (80 bytes)
Oct 4 08:53:57 charon 80307 10[NET] <con4|372> received packet: from 192.158.19.11[500] to 50.169.69.234[500] (80 bytes)
Oct 4 08:53:57 charon 80307 10[ENC] <con4|372> parsed INFORMATIONAL response 96 [ ]
Oct 4 08:53:57 charon 80307 10[IKE] <con4|372> activating new tasks
Oct 4 08:53:57 charon 80307 10[IKE] <con4|372> nothing to initiate