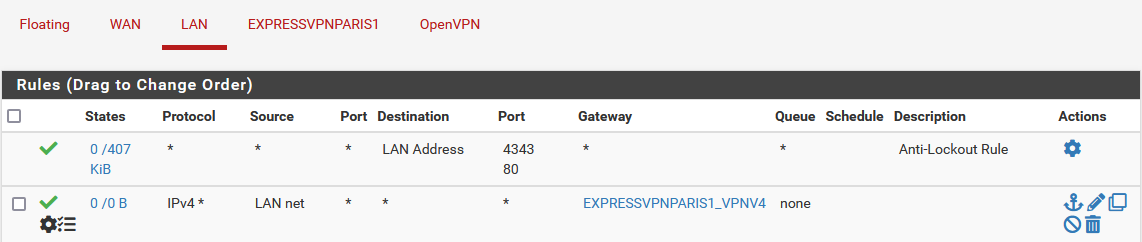
@lolipoplo
00:00:39.893213 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 39453, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 123.139.94.40.16379: [udp sum ok] UDP, length 104
00:11:15.697052 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 41593, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 123.139.94.40.16379: [udp sum ok] UDP, length 104
01:27:00.579015 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 24615, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62214: [udp sum ok] UDP, length 104
00:00:00.296683 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 24616, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62224: [udp sum ok] UDP, length 104
00:14:59.783329 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 63138, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62214: [udp sum ok] UDP, length 104
00:04:14.623627 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 63139, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.52601: [udp sum ok] UDP, length 104
00:10:46.028208 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 21564, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.1: [udp sum ok] UDP, length 104
00:00:00.290588 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 21565, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62224: [udp sum ok] UDP, length 104
00:00:01.600105 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 21566, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62224: [udp sum ok] UDP, length 104
00:14:58.004355 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 6150, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.52601: [udp sum ok] UDP, length 104
00:00:00.162623 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 6151, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.1: [udp sum ok] UDP, length 104
00:00:00.154916 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 6152, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62386: [udp sum ok] UDP, length 104
00:00:01.225057 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 6153, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62320: [udp sum ok] UDP, length 104
00:14:58.611751 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 47222, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62320: [udp sum ok] UDP, length 104
00:00:01.804954 rule 51/0(match) [ridentifier 1000000119]: block in on em1: (tos 0x0, ttl 64, id 47223, offset 0, flags [none], proto UDP (17), length 132)
192.168.55.100.59372 > 45.190.158.201.62386: [udp sum ok] UDP, length 104
00:33:32.433578 rule 4/0(match) [ridentifier 1000000103]: block in on pppoe0: (tos 0x28, ttl 110, id 63739, offset 0, flags [none], proto TCP (6), length 52)
154.16.174.207.59372 > My-WAN-IP.54296: Flags [S], cksum 0x05da (correct), seq 3626588183, win 65142, options [mss 1287,nop,wscale 8,nop,nop,sackOK], length 0
00:00:01.010321 rule 4/0(match) [ridentifier 1000000103]: block in on pppoe0: (tos 0x28, ttl 110, id 63740, offset 0, flags [none], proto TCP (6), length 52)
154.16.174.207.59372 > My-WAN-IP.54296: Flags [S], cksum 0x05da (correct), seq 3626588183, win 65142, options [mss 1287,nop,wscale 8,nop,nop,sackOK], length 0
00:00:02.000693 rule 4/0(match) [ridentifier 1000000103]: block in on pppoe0: (tos 0x28, ttl 110, id 63741, offset 0, flags [none], proto TCP (6), length 52)
154.16.174.207.59372 > My-WAN-IP.54296: Flags [S], cksum 0x05da (correct), seq 3626588183, win 65142, options [mss 1287,nop,wscale 8,nop,nop,sackOK], length 0
00:07:20.160301 rule 4/0(match) [ridentifier 1000000103]: block in on pppoe0: (tos 0x2a,ECT(0), ttl 113, id 17567, offset 0, flags [none], proto TCP (6), length 52)
188.132.209.91.59372 > My-WAN-IP.38535: Flags [SEW], cksum 0x7a03 (correct), seq 4200447135, win 64240, options [mss 1400,nop,wscale 8,nop,nop,sackOK], length 0
00:00:06.000334 rule 4/0(match) [ridentifier 1000000103]: block in on pppoe0: (tos 0x28, ttl 113, id 17573, offset 0, flags [none], proto TCP (6), length 52)
188.132.209.91.59372 > My-WAN-IP.38535: Flags [S], cksum 0x7ac3 (correct), seq 4200447135, win 64240, options [mss 1400,nop,wscale 8,nop,nop,sackOK], length 0
This is after I left it for a whole night to run.