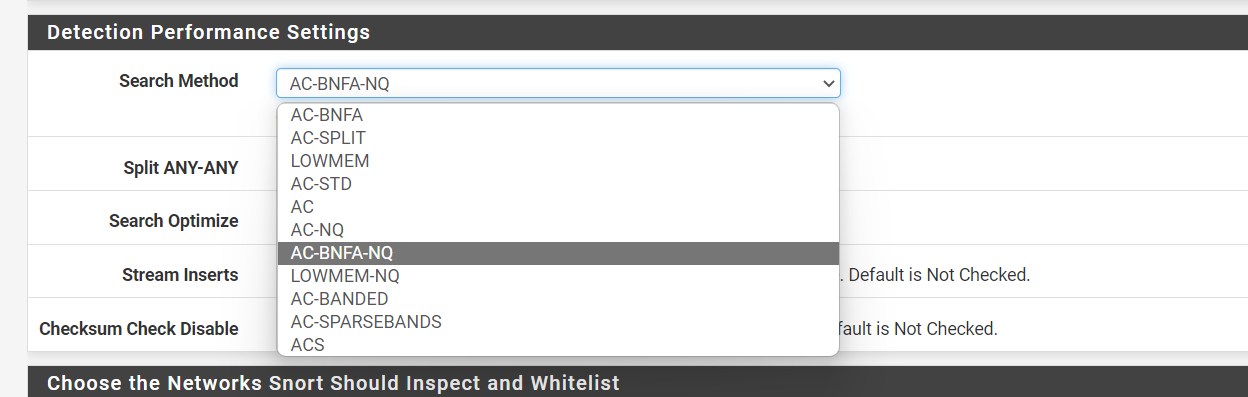
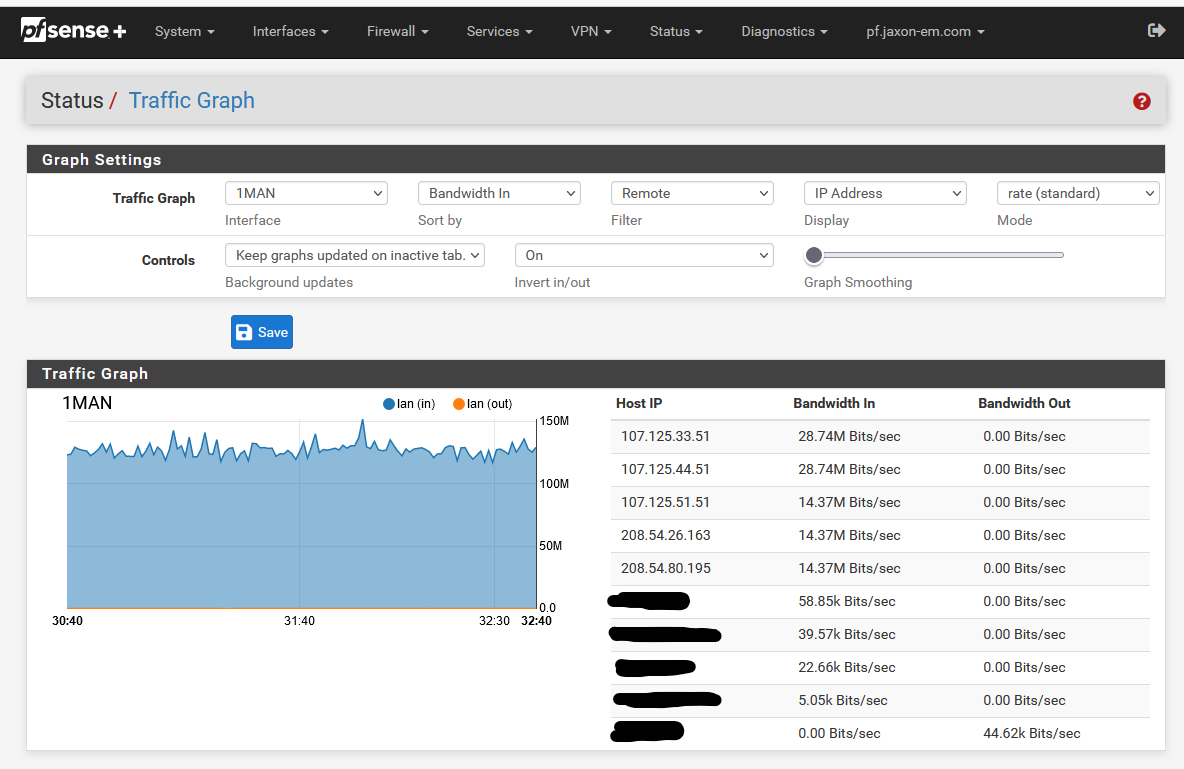
-
0 Votes3 Posts414 Views
-
0 Votes10 Posts5k Views
-
0 Votes2 Posts1k Views
-
0 Votes6 Posts629 Views
-
0 Votes5 Posts2k Views
-
0 Votes6 Posts851 Views
-
0 Votes5 Posts641 Views
-
0 Votes4 Posts2k Views
-
0 Votes6 Posts454 Views
-
0 Votes11 Posts1k Views
-
0 Votes17 Posts2k Views
-
0 Votes3 Posts763 Views
-
0 Votes1 Posts283 Views
-
0 Votes2 Posts3k Views
-
0 Votes34 Posts2k Views
-
0 Votes2 Posts500 Views
-
0 Votes2 Posts411 Views
-
0 Votes50 Posts10k Views
-
0 Votes4 Posts1k Views
-
0 Votes3 Posts747 Views
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.