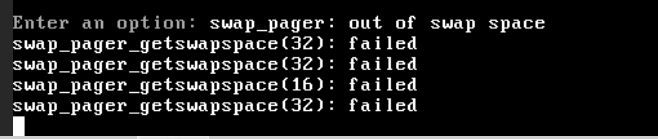
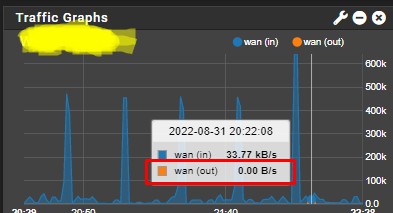
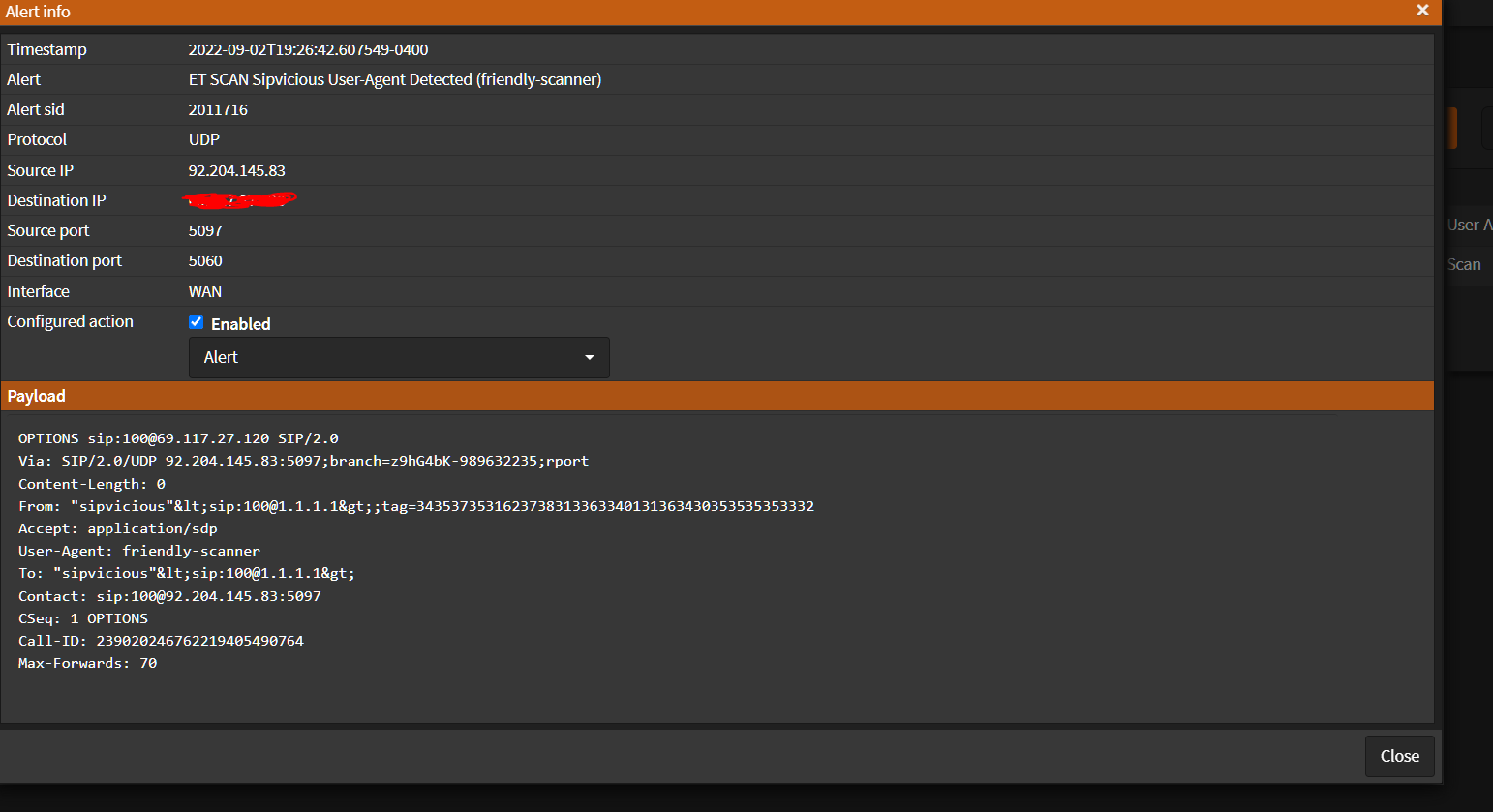
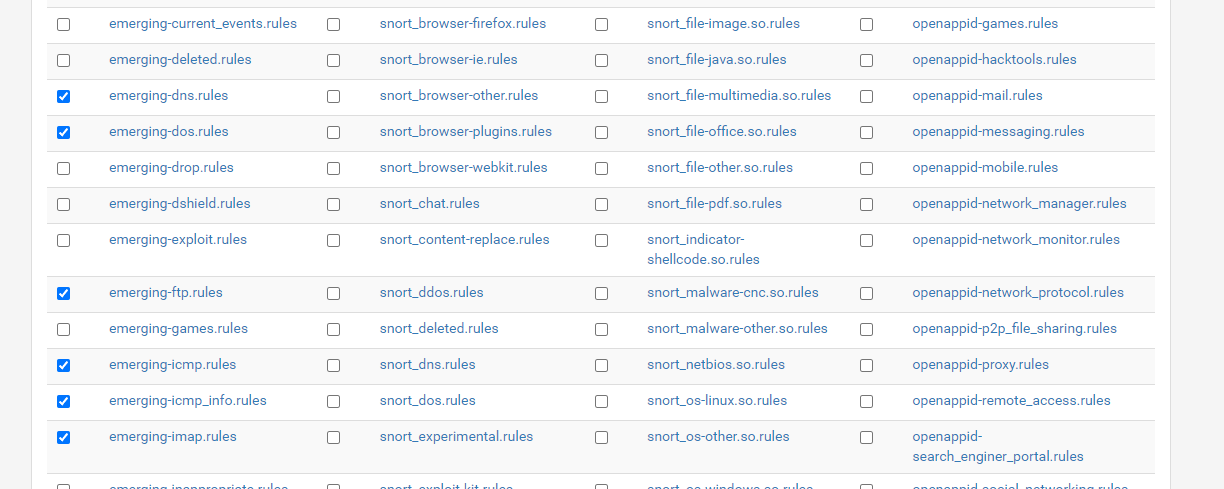
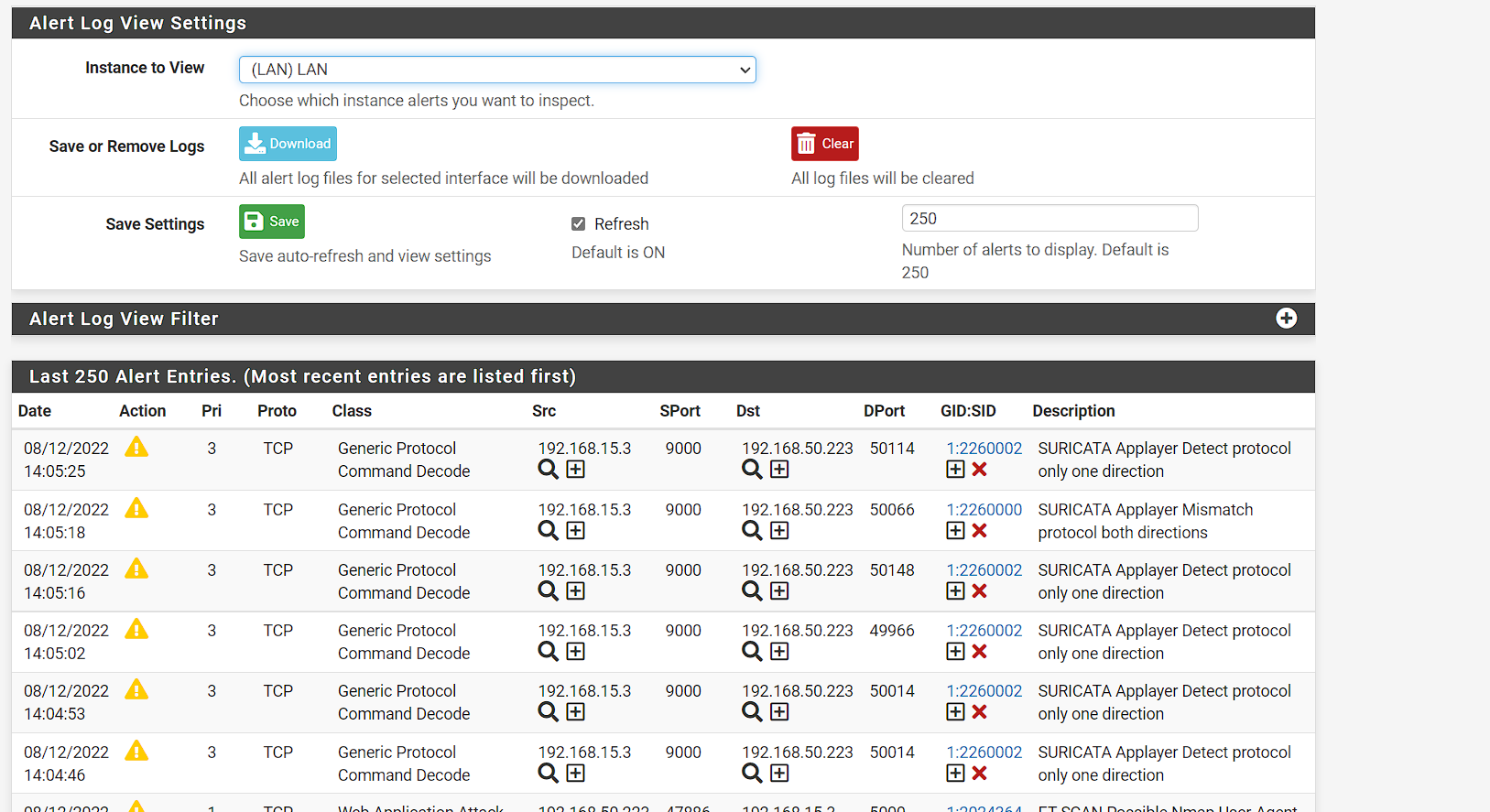
For home usage you should split services;
SquidGuard with Blacklists
Blocks much more then I was expecting
Snort with an Oink Code free
Several books from Amazon are available to get in closer touch with it.
pfBlocker-NG with I-Blocklist for ~10 € a year
You might be really good sorted with many of them
In short if you sort the things to do over more then one pfSense packet, often you will be getting a better service
out for you or your company it self's! If you where reading
something about IDS/IPS it makes more sense to come back and ask this or that function, about a problem and
more points.
You may think it is not really that books are outdated, old
and whatever, but for getting an overview how it works
and more makes you then also install only one rules, edit
it and see for three month how many false positives you got and then you will starting the second rule once more
for let us say three month and so on. What is the right mode for you, what is the most attacks you may be confronted with, what you want to secure and why.
You may be also setting up Squid & SquidGuard as caching proxy in front of your LAN and lightSquid as an
reserve proxy in front of your DMZ with the servers to get
a better "not in contact directly with the internet" state of
your network. Setting up public IPs directly on pfsense is one more point. Security is not one point and all is fine for you and IDS/IPS is not a set it up and forget it service.
Book: (Amazon)
IDS: Intrusion Detection (Trace search in the net) ~5 €
Install TCPDump or WireShark and collect data and packets from your network, learn what is written in this
packets, what are the meaning of the numbers and and and .......
Books: (Amazon)
Network Intrusion Detection
Snort 2.0 Intrusion Detection
Snort Primer: A FAQ Based Introduction
Managing Security with Snort and IDS Tools
Then after you know this you will be setting up ids/ips and you only insert one rule after one rule and editing them that they match to you network and your situation.
After you got a problem, @bmeeks might be better able to help you, without making an ids/ips basic course with you.