@digidax said in snort: restarting needed if IP list edited?:
@bmeeks
OK, will take a look into the logs to see, if the updates of the list are imported successful.
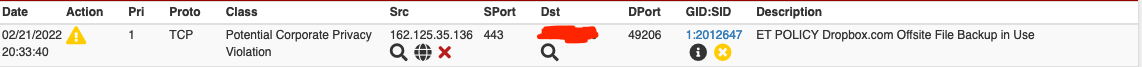
OT Question: in the blocked tab, I see the "Last 500 Hosts Blocked by Snort ". In the browser, I can use CTRL+f to search for an IP.
a) is it possible, as a future feature, to get a search filed for an IP when the list is larger, > 2000 entries?
I don't really understand why you would want the block list to grow like that. The suggested setup is to enable the automatic cron task (on the GENERAL SETTINGS tab) that clears blocked hosts who have seen no traffic for the interval specified in the parameter on that tab. For example, if you choose 1 hour, then any IP in the block list that has seen no traffic for the last hour will be automatically removed from the block list after the interval has expired.
There is really no point in maintaining huge block lists. If the same host attacks again, then Snort will detect and block it again. It is usually sufficient to block a host for 15 minutes to an hour. If you have not already, I strongly recommend you enable that setting and configure it for either 30 minutes or 1 hour max.
Snort blocks by making a pfSense system call and inserting the offending IP into a pf table called snort2c. That table is created by pfSense during bootup, and it is a RAM construct. So when the firewall is restarted, that table is recreated from scratch.
b) can I use a command line command to search for a blocked IP and remove it from snort's blocklist?
You can manage the pf firewall engine using the pfctl utility. Here is a link to its documentation: https://www.freebsd.org/cgi/man.cgi?query=pfctl&sektion=8.
Thanks, Frank