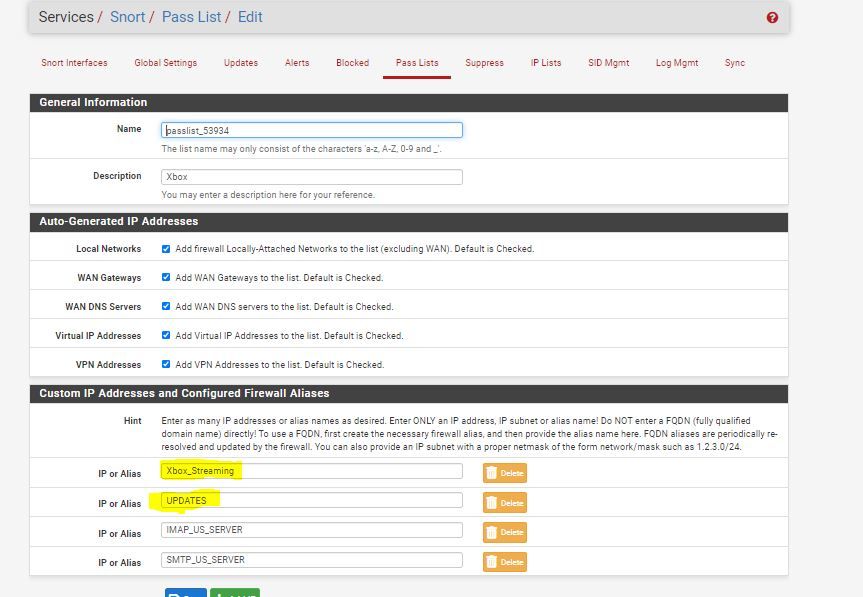
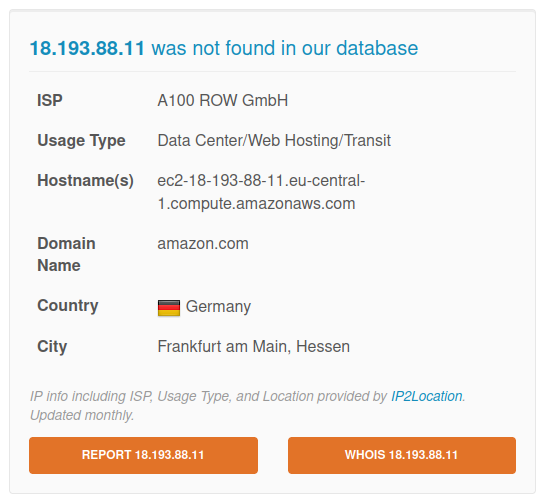
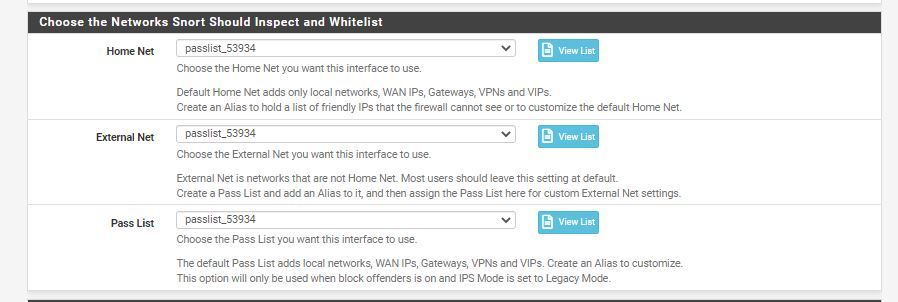
-
0 Votes8 Posts2k Views
-
0 Votes2 Posts309 Views
-
0 Votes4 Posts2k Views
-
0 Votes5 Posts1k Views
-
0 Votes2 Posts382 Views
-
0 Votes12 Posts2k Views
-
0 Votes2 Posts1k Views
-
0 Votes2 Posts347 Views
-
0 Votes2 Posts506 Views
-
0 Votes2 Posts1k Views
-
2 Votes8 Posts1k Views
-
0 Votes3 Posts629 Views
-
0 Votes15 Posts2k Views
-
1 Votes4 Posts1k Views
-
0 Votes4 Posts1k Views
-
0 Votes6 Posts1k Views
-
0 Votes3 Posts749 Views
-
0 Votes5 Posts1k Views
-
0 Votes8 Posts3k Views
-
0 Votes6 Posts2k Views
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.