Are you using Inline IPS Mode or Legacy Blocking Mode?
With Inline IPS Mode there is no blocking of all traffic for an IP address. Only individual packets trigger a rule will be dropped, but other traffic that does not trigger a rule is passed.
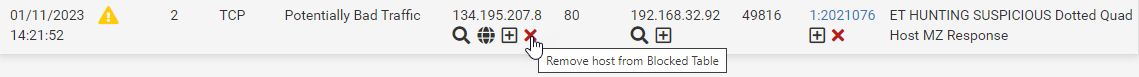
With Legacy Blocking Mode, any alerting rule will potentially result in the IP address(es) from the packet that triggered the rule being added to a built-in pfSense packet filter table called snort2c. Once an IP is placed in that table, hidden built-in firewall rules within pfSense will block all traffic to/from that IP address.
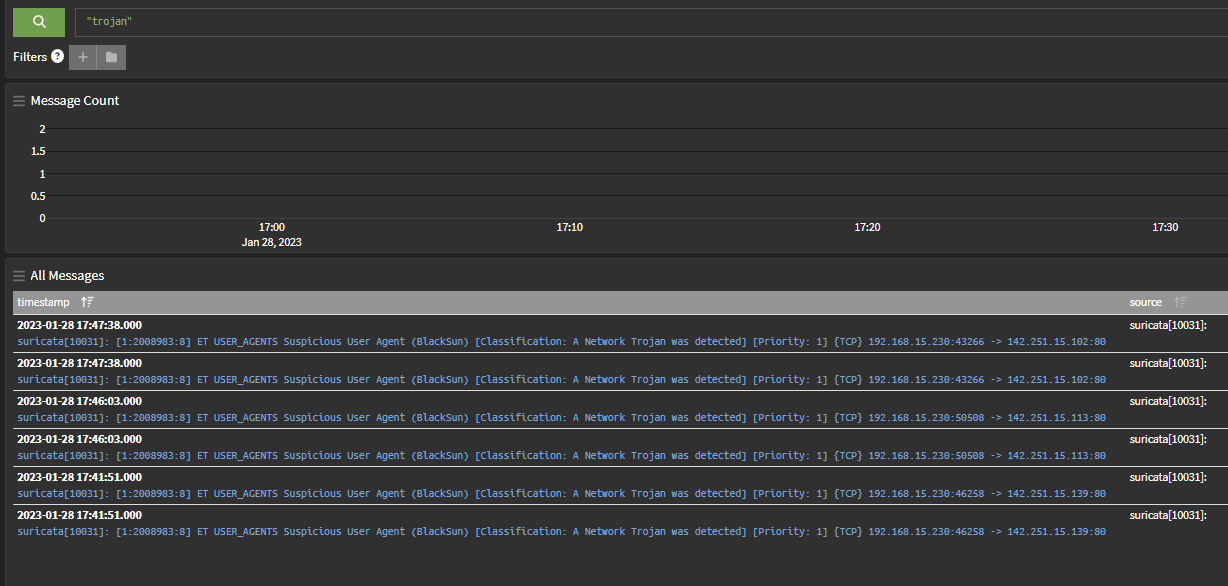
Inline IPS Mode does not place an IP address in the snort2c table, therefore it won't show up on the BLOCKS tab as that tab simply shows the current contents of the snort2c table. To find alerts that resulted in dropped packets when using Inline IPS Mode, look on the ALERTS tab for entries printed in red.
Pass Lists are how you "whitelist" an IP with Legacy Blocking Mode, but there are several steps that must be performed in the correct sequence. First, create the Pass List and make sure the address or network is added to it. Save the list. Next, go to the INTERFACE SETTINGS tab and select the correct Pass List in the Pass List drop-down selector and then save that change. Finally, you must restart Snort on the affected interface in order for the running daemon binary to pick up the Pass List assignment.
This part of your message is confusing:
This website got blocked by snort and we added it to the pass list and it seems like snort is ignoring it's entry on the pass list. The website does not appear to be in the blocklist either.
With Legacy Mode Blocking, Snort cannot block anything without putting the IP in the snort2c table. And any IP in that table will show up when you view the BLOCKS tab. It may very well be that Snort is not the cause of your problem if the website's IP is not showing on the BLOCKS tab -- either that or you are not looking for the correct IP. Be aware that many websites are behind CDNs and thus may be using a large number of IP addresses that can change every few minutes. Some CDNs have TTL values in DNS set to as low as 2 minutes, and many others have it set to 5 minutes. That means a given IP might only be valid on your box for 5 minutes or less before it changes again with the next client that performs a DNS lookup.
 1
0 Votes41 Posts5k Views
1
0 Votes41 Posts5k Views