@bmeeks said in Suricata blocking IPs that are on the passlist:
@ELMcDonald said in Suricata blocking IPs that are on the passlist:
No they are not, also not listed in any of the log's
Then if the IP is not listed in an alert showing on the ALERTS tab, Suricata is not the cause. It is not possible for Suricata to block without showing the IP in an alert and on the BLOCKS tab. Just for info, blocked IPs are never shown anywhere in the pfSense system log nor in the suricata.log. So don't look for them there. Look on the ALERTS and BLOCKS tabs. IPs from triggered rules only show up on the ALERTS tab or the BLOCKS tab.
I understand what you are saying. I can't get to reddit while its running and i did check it is in legacy mode. As soon as it stops I can access the site and use the app.
One one odd thing, I can ping and tracert to the site with no problems.
These statements prove to me that Suricata is not your problem (if you are actually using Legacy Mode). Suricata blocks everything for an IP once it blocks. That includes all ports and all protocols. So nothing would work for a given IP if Suricata is actually doing the blocking, so the tracert and ping would fail. This is especially the case in Legacy Mode. It is impossible within the code for Suricata in Legacy Mode to block just one protocol for an IP.
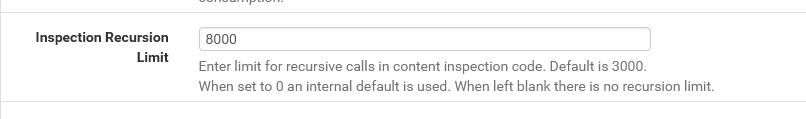
I don't mean to be rude, but your description of the issue leads to me to believe you need much more experience with an IDS before you put it in blocking mode. Go to the INTERFACE SETTINGS tab (for your WAN, since you said you are running Suricata on the WAN) and uncheck the box for Block Offenders. Save the change and restart Suricata. See how things work then. If everything works fine, then that indicates you have a lot of learning to do with regards to how to operate and utilize the Suricata package.
The things you have described as happening to you thus far do not follow logically based on other information you are giving to my questions. To be blunt, it can't be working exactly as you describe. The code just does not work that way. Perhaps you are not describing things correctly when answering my specific questions.
I admitted that I have no experience with IDS/IPS. Do you have any sites that would be good for a beginner?
I stumbled upon another address that my research didn't find the first time. Added that ip and did a test and all works. Turned blocking mode back off.
Thank you for you help.