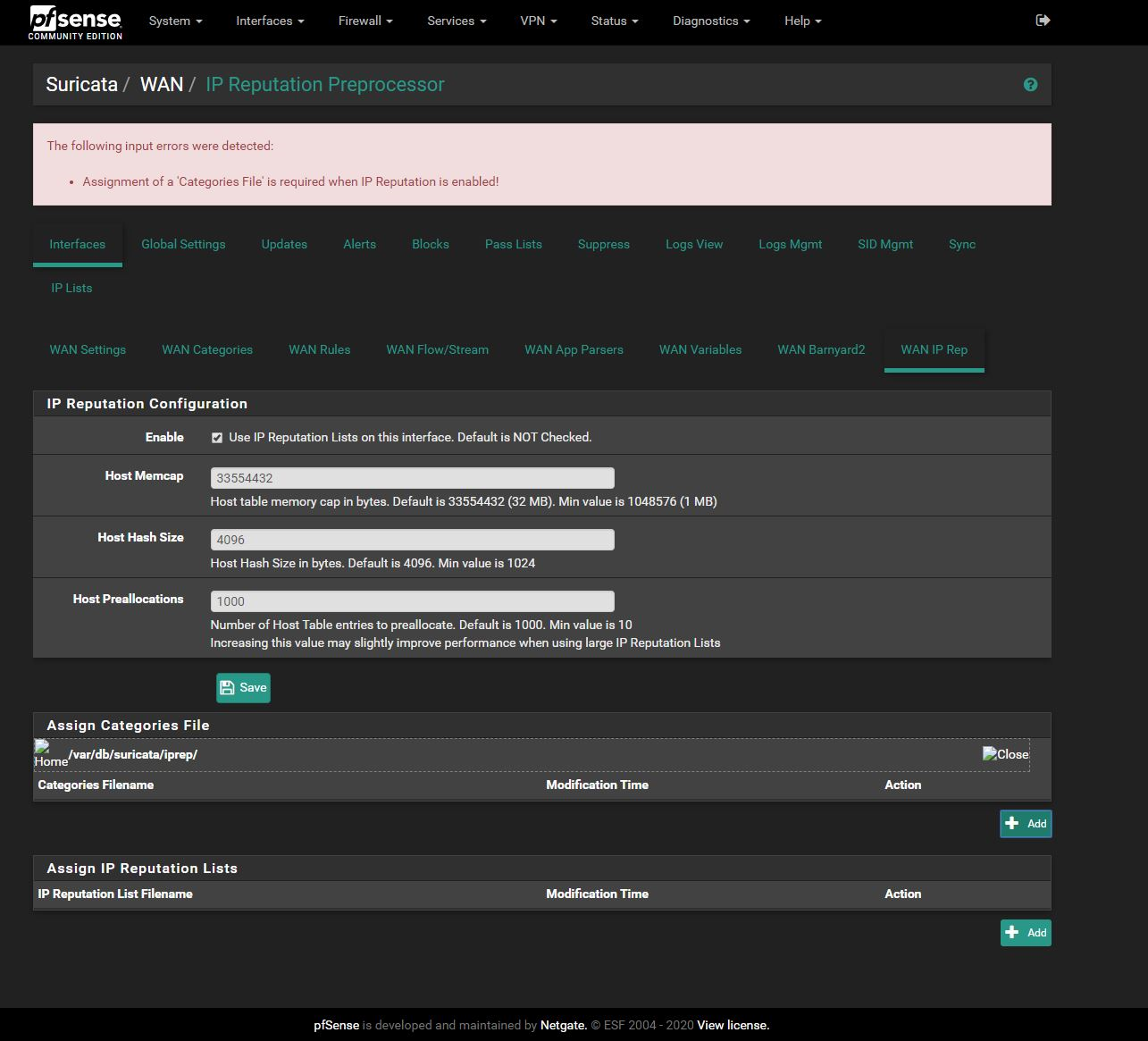
-
0 Votes5 Posts1k Views
-
0 Votes6 Posts976 Views
-
0 Votes2 Posts374 Views
-
0 Votes30 Posts11k Views
-
0 Votes5 Posts2k Views
-
0 Votes2 Posts244 Views
-
0 Votes2 Posts348 Views
-
0 Votes2 Posts463 Views
-
0 Votes10 Posts508 Views
-
0 Votes4 Posts356 Views
-
0 Votes4 Posts2k Views
-
0 Votes14 Posts1k Views
-
0 Votes8 Posts912 Views
-
0 Votes2 Posts993 Views
-
0 Votes2 Posts332 Views
-
0 Votes2 Posts855 Views
-
0 Votes3 Posts689 Views
-
0 Votes5 Posts2k Views
-
3 Votes1 Posts303 Views
-
0 Votes4 Posts2k Views
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.