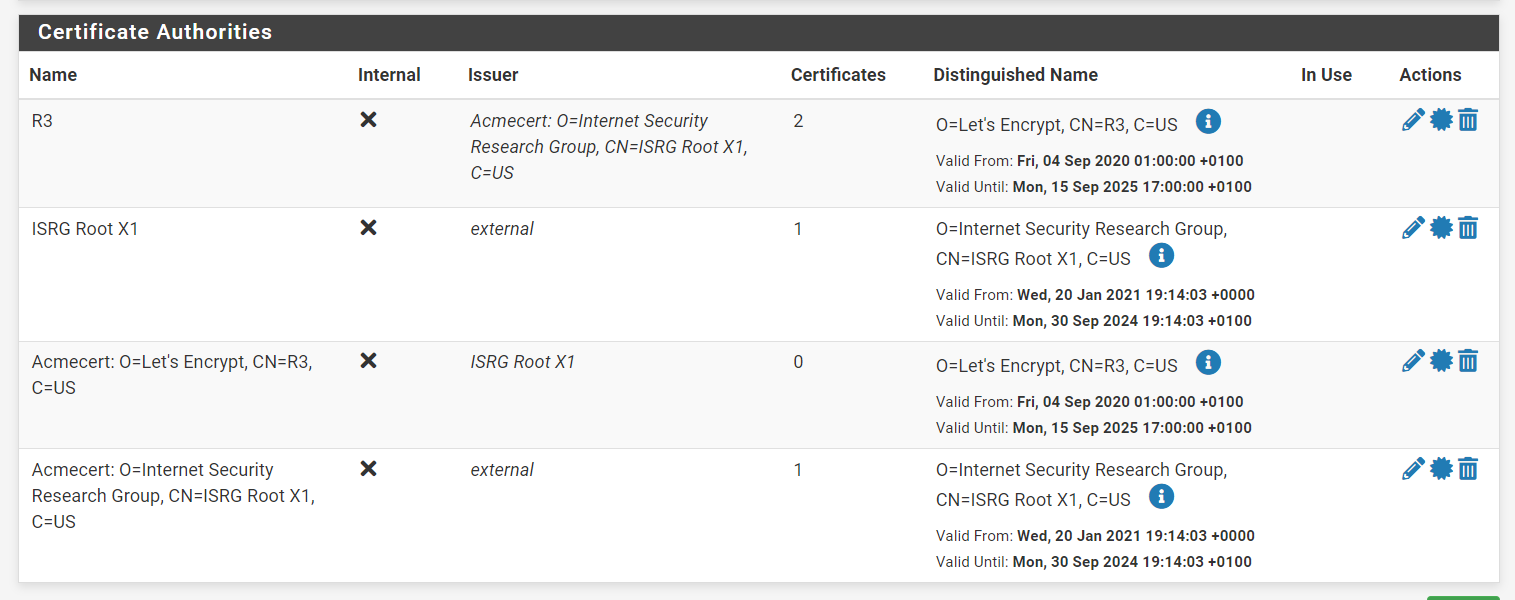
@decidable3195 said in ACME Verify error: 404:
Please check log file for more details: /tmp/acme/Webserver/acme_issuecert.log
The last line shows you where more info can be found :
/tmp/acme/Webserver/acme_issuecert.log
although, even if you don't spot the error, at least you will know now how deep the pool is ;)
Important info is also :
http://www.xxx.com/.well-known/acme-challenge/wCSyAsP9hDHGn7CPmLyEXZd7uuAUlnBgpBrcKZux39M: 404
This means that if Letsencrypt, or me, or you, or who ever, visits this file :
http://www.xxx.com/.well-known/acme-challenge/wCSyAsP9hDHGn7CPmLyEXZd7uuAUlnBgpBrcKZux39M
you ( and I, and everybody, and also LE) should see the secret temporary 'key' (some random asci codes, you can see it in the acme log) that acme.sh put there.
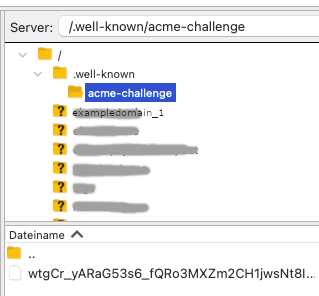
So, http://www.xxx.com/.well-known/acme-challenge/ must be publicly accessible.
So, the question is : is the file there ?
And if so, is the content ok ? Often, if the file was created, the content is also fine.
You already run your own web server on a server, so you know where the web server root folder is.
In that root folder, there must be a sub folder with the name ".well-known/" that contains a subsequent folder called "acme-challenge/".
Is that so ?
Now, create a file called 'hello' and put something in it like "hello again".
Now : test, like me and LE : from the outside ( !! ), use your phone with the wifi de activated , and visit http://www.xxx.com/.well-known/acme-challenge/hello
Does it show "hello again" ?
It should.
If you can't, LE can't do it neither => fail !
Remember : LE told the acme.sh script the file name : in your case, it was "wCSyAsP9hDHGn7CPmLyEXZd7uuAUlnBgpBrcKZux39M" and it also gave a content like "hjgjhghjgqgqjhdqsgqsgd".
That was the "Getting domain auth token for each domain" part.
Then, all acme.sh has to do, using a helper DNS-script like 'webroot' is accessing your web root, create the sub folders and the file with the content.
This must work.
This is the :
Getting webroot for domain='www.xxx.com'
Getting webroot for domain='service.xxx.com'
part.
Btw : if all works well, and the LE check passes, the acme.sh helper script will also remove the wCSyAsP9hDHGn7CPmLyEXZd7uuAUlnBgpBrcKZux39M file.
You use the standalone mode. That's a no-automation-mode.
Read the manual : https://github.com/acmesh-official/acme.sh/wiki/How-to-issue-a-cert
That's strange because you have (you should) access to your web server's root folder.
There is the webrootftp helper mode. You have FTP access, right ?? (ok, 'FTP' was abandoned and shot in the forest last century, but you can still use it locally)
Or far better, as you have a domain name (that you rent annually) : most (the ones that don't are all broke by now) registrars have an API access : use the API access credentials, pick the right helper access, and use one of the DNS helper modes
General comments :
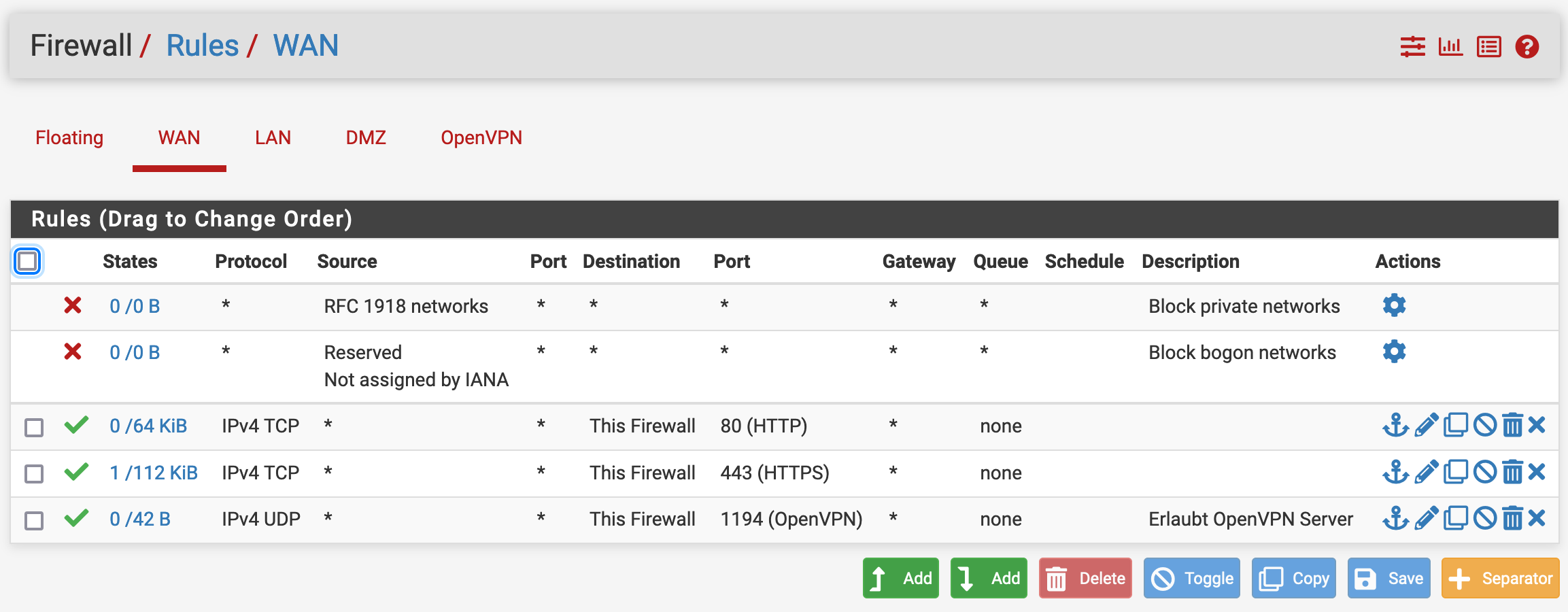
Opening port 80 and or 443 (the webgui) on WAN ?
Your pool is 1 mm deep, and you dive head first in it. We all know what will happen.
You are using floating rules.
Take this advise : don't do that. Live is already hard enough without that "floating" thing.