Using a GRE Tunnel to route VMs network and IP to external network.
-
Ok, so what's the 1:1 NAT rule at the remote side? It looks like it's not catching the traffic there on the way out and it's using the auto outbound rule instead.
Also the 1:1 NAT rule would not change the source port (icmp ID here) like is shown there.However it does look to be working as expected apart from that. There is two way traffic shown on all 4 interfaces involved. But the ping fails?
Steve
-
@stephenw10 The NAT rules on the remote site are like this:
1:1
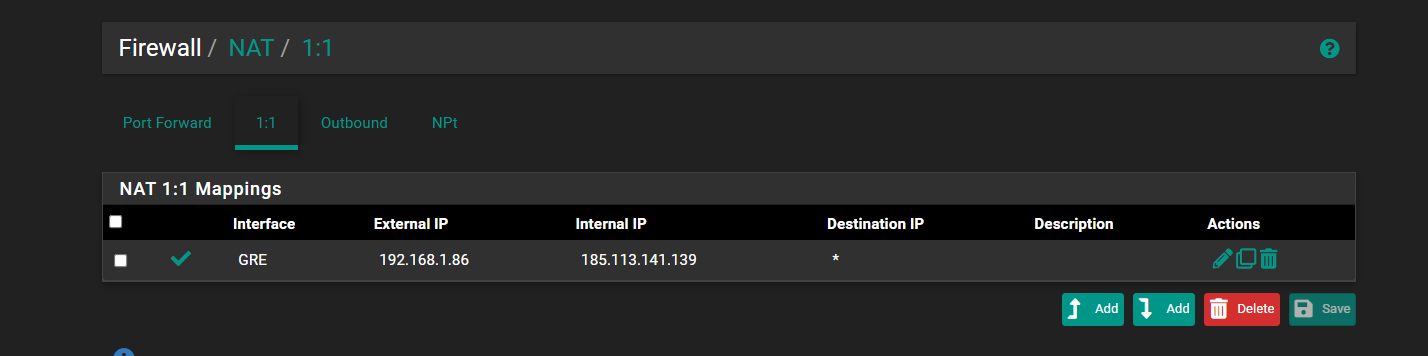
Outbound

Yeah, basically it just doesn't have internet access, nor even access to the pfsense or tunnel ping.. I can't ping the tunnel through the VM even tho the ping arrives there.
-
Ok the 1:1 NAT rule should be on WAN with the external IP being the public IP VIP and the internal IP being the private IP of the server.
-
@stephenw10 So, like this?
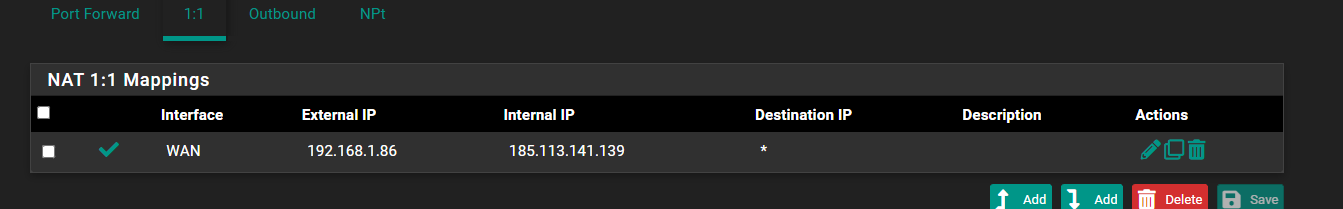
And on the VM, like this?

-
No the external IP should be the public IP. The internal IP should be the server IP in 192.168.1.0/24.
The VM gateway needs to be in the subnet so it should be the local pfSense VLAN interface IP. Probably 192.168.1.1
-
@stephenw10 So, my networks on local pfsense are like this:
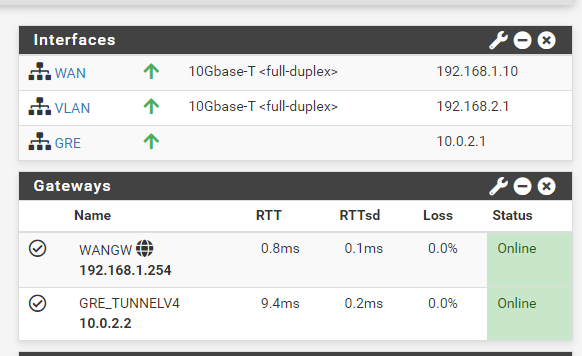
My WAN is the 192.168.1.10 which is on the main gateway of the router 192.168.1.254
I use the VLAN as a bridge for the VMs, but should I use something else both on pfsense or on the VMs?
-
Hmm, where is the VM at 192.168.1.86 then?
I expect all the VMs to be in the VLAN subnet and all the routing the NAT setup to be to and from the VLAN subnet.
Steve
-
I also did a pcap on both the GRE and VLAN of the local pfsense
GRE:

VLAN:

So, as I understood it is sending the ping to the 1.1.1.1 but it is not receiving any traffic..
-
Right, well it won't if traffic from 192.168.1.86 is coming in on the wrong interface!
If you run a pcap on WAN you will see all the replies going back that way because that's where the 192.168.1.0/24 subnet is.
How exactly is the VM connected?
-
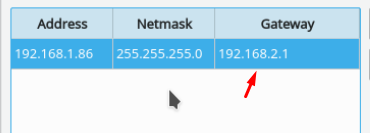
@stephenw10 The VM is in the proxmox with the IP on 192.168.1.86 and gateway 192.168.2.1 like I showed above
The VM is with the bridge of the VLAN (192.168.2.1) which is the Linux Bridge 1 on proxmox (vmbr1) that will (supposedly) be attached to all VMs so it can tunnel the traffic to the remote pfsense
-
This is the only 1.1.1.1 ping I have on the WAN of the local pfsense
-
There is an ARP request for 192.168.1.86 though because it's trying to find it on the WAN. And failing.
The VMs should be in the VLAN subnet, 192.168.2.0/24.
The static route at the remote end should be for that subnet.
The 1:1 NAT rules at the remote side should also be for host in that subnet.
Steve
-
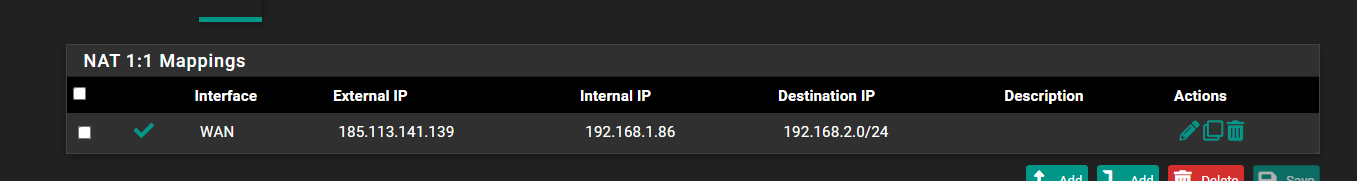
@stephenw10 So, like this?

-
Ok, so It looks like I was using a 192.168.1.86 on a .2 subnet, I changed it to 192.168.2.86 and it now pings 1.1.1.1 and 8.8.8.8 and the tunnel, but doesn't have internet access to like ifconfig.me or google.com. I'll do a bit more testing, but it's closer than never to work out.
-
Yeah you need to be using 192.168.2.X everywhere.
You are probably seeing pings work but no other traffic because there is some asymmetry somewhere. Once all the rules and routes are changed to the VLAN subnet it should work.
-
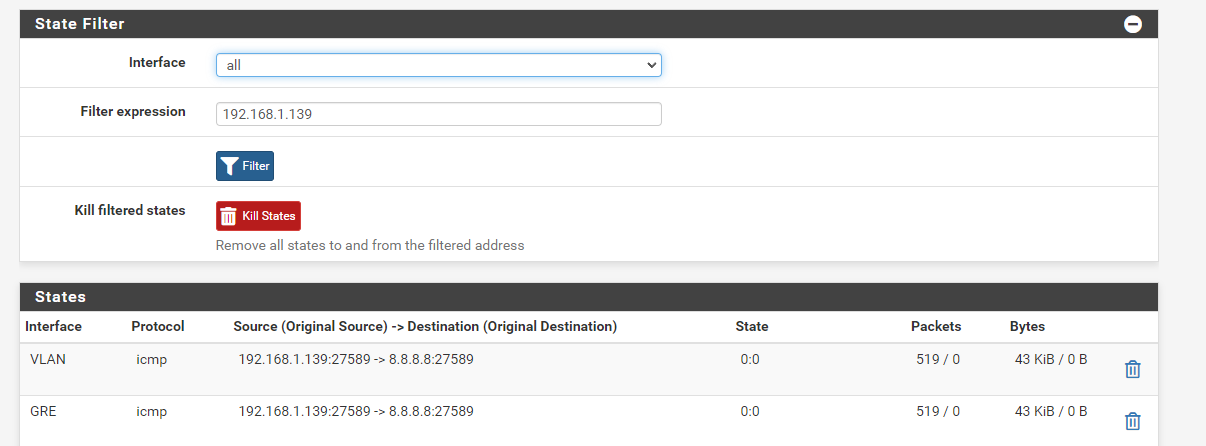
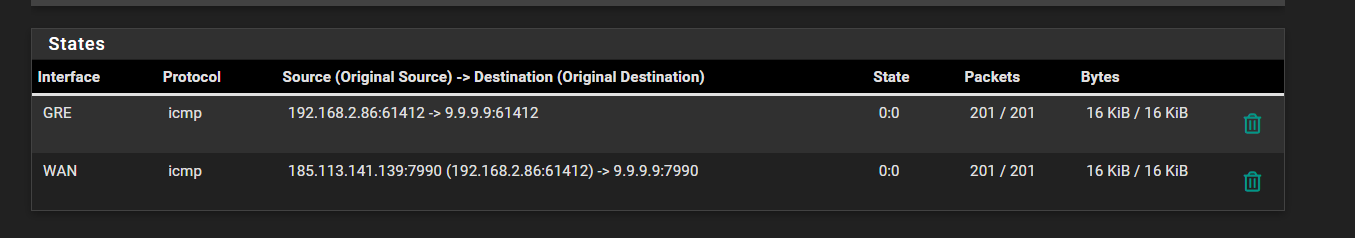
@stephenw10 Ok, it is pinging now. I can ping everything on IP addresses, except domains. Like, If I ping my Home Public IP address, I get a ping of 20ms or something, when the tunnel's ping is about 9ms.
But is it normal the ping state is 0:0 on both ends?
Local:

Remote:
Also the only NAT rules I have are on the remote pfsense, which are:

On the local pfsense I have the NAT disabled.
What rules should I change/add?
-
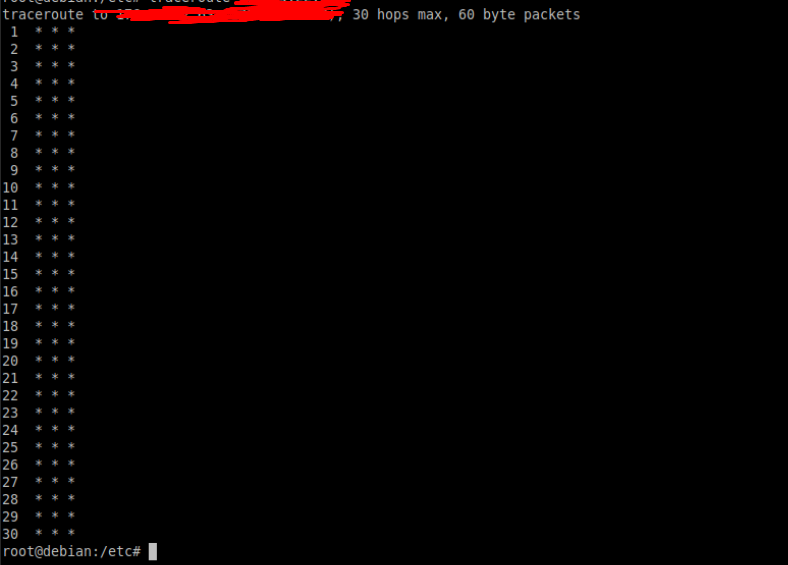
Also, traceroutes only give * * * * back:
-
@xuap said in Using a GRE Tunnel to route VMs network and IP to external network.:
But is it normal the ping state is 0:0 on both ends?
Yes. icmpv4 doesn't have a state.
You should still have 1:1 NAT rules on the remote pfSense. With that you wouldn't need the outbound NAT rule, the 1:1 does that already.
And you need the 1:1 rule if you want inbound connections the VM to work. Or add port forwards for each connection you need but 1:1 does it all.Steve
-
@stephenw10 So, I can remove the NAT Rules and set NAT as automatic because 1:1 Mapping does all those rules already?
Also, I want to use inbound connections too, for that, I do need that rule mentioned above, or what should I do?
-
Yes, if you have the 1:1 NAT rule in place it NAT's all traffic inbound and outbound between those IPs, 1:1.
So you can remove/disable the outbound NAT rule. No harm in leaving it in hybrid mode though.For inbound traffic you still need firewall rules to allow that on the remote side WAN. And they re applied after NAT so the destination will be the internal private IPs of the VMs.