Is it possible for one to "slip through"?
-
@gertjan said in Is it possible for one to "slip through"?:
Another way : a state already existed.
But was a connection actually made? Or is that what he showing just a connection attempt by the client? Doesn't seem like the session was actually done. There are no frames, there is no time listed for the session, etc. Looks like some sort of connection attempt?
But sure I would look in the pfsense state table
-
If that IP list is being applies as a block to inbound connections that would otherwise reach that server then no, the connection would not 'slip through'.
So either it's not being applied like that or there is another rule passing it. Or, yes, there was an existing state before the block was added.Steve
-
@gertjan I meant to label everything, but did not. What you are looking at is the custom ipv4 block list in pfBlockerNG. With that in the list, nothing in that range should have gotten past the firewall, yet an ip address from that range came through to my Blue Iris server.
-
@johnpoz said in Is it possible for one to "slip through"?:
@gertjan said in Is it possible for one to "slip through"?:
Another way : a state already existed.
But was a connection actually made? Or is that what he showing just a connection attempt by the client? Doesn't seem like the session was actually done. There are no frames, there is no time listed for the session, etc. Looks like some sort of connection attempt?
But sure I would look in the pfsense state table
No connection was actually made. However, that ip address shouldn't even be able to get that far the way it is set up. Also, I have to look into this "state already existed" everyone is talking about.
-
@obxjeepguy said in Is it possible for one to "slip through"?:
that ip address shouldn't even be able to get that far the way it is set up.
But from what you posted I can not really tell if that is outbound connection attempt from inside your network, or a connection attempt from outside pfsense that is forwarded in?
-
Yes, more info needed.
I had assumed that you are forwarding traffic to the BlueIris server and have pfBlocker adding rules to filter that?
If you are using pfBlocker to automatically add rules make sure it's adding rules where you expect and in the right order.
Make sure the alias pfBlocker creates actually contains that subnet.Steve
-
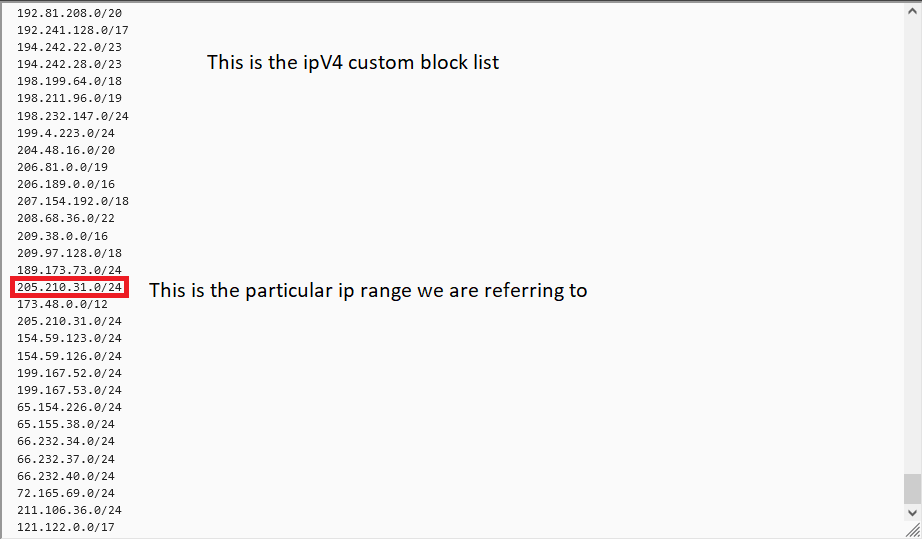
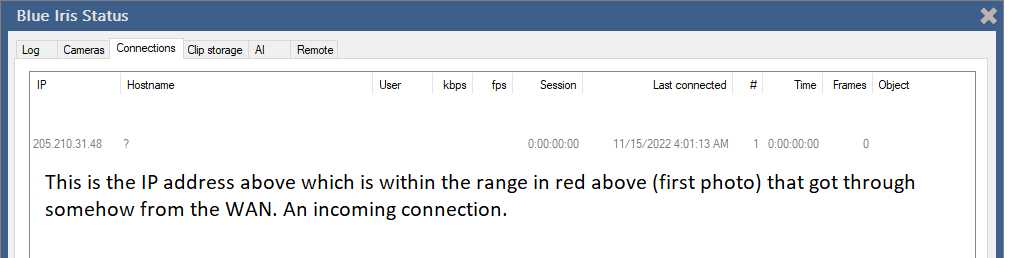
Okay, hopefully this explains it better. I have been running this firewall for about a year now with great success. Once I block a range, I never see another attempt. This particular one is the first time I have seen something like this happen.
-
But how are you applying that block? What is it blocking, traffic from a port forward to the server?
-
@stephenw10 I am blocking that IP range from anything on my LAN.
-
@obxjeepguy where is the rule?? On your lan? In floating, on your Wan?
What are the order of the rules? etc.. For all we know that was the device your showing the 205.x address in trying to make a connection and it didn't work, etc..
-
From connecting to anything on your LAN?
Yeah, we need to see the rule and where it's applied really. There are many ways to apply that incorrectly.

-
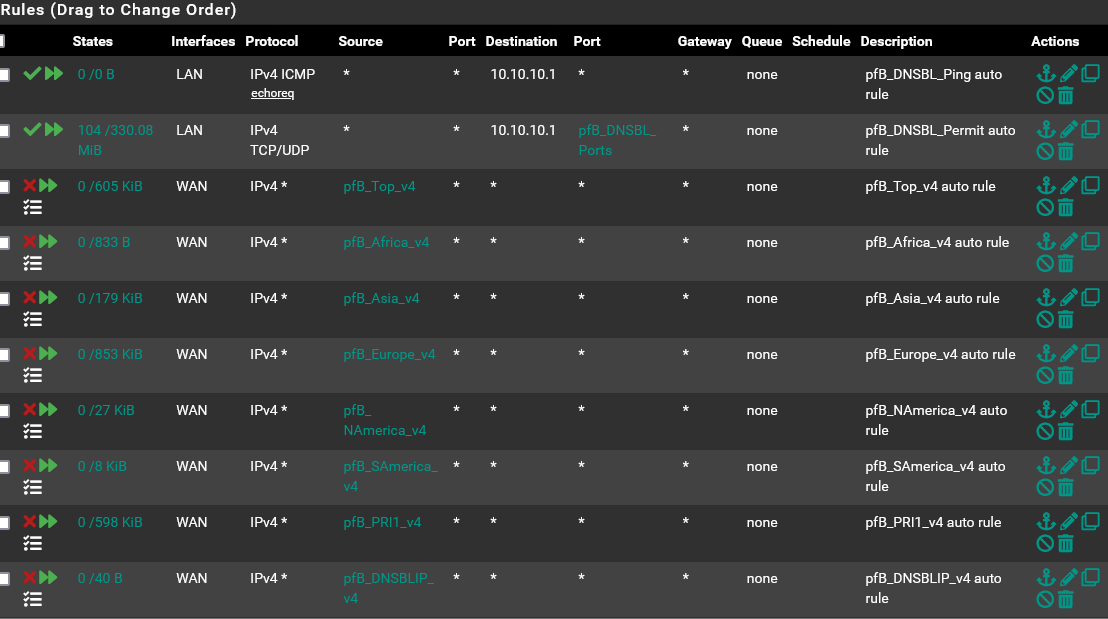
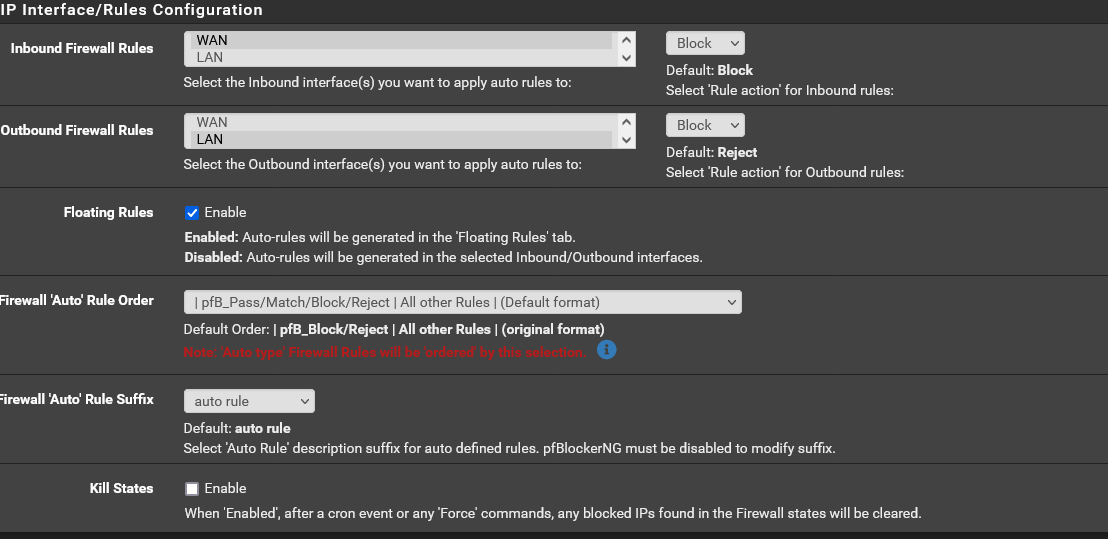
I am guessing this is what you are looking for.
-
Those all look like the included list names. Is your custom block list added to one of those?
Or, what 'list action' do you have set on your custom list?
-
@stephenw10 The custom block list is within pfB_PRI1_v4.
-
Ok, so that would block connections from that subnet inbound on WAN. And since it's a floating rule it would do so before and pass rules you might have on the WAN tab. You haven't explicitly confirmed it but I assume you have a port forward to the server on WAN with linked firewall rules there?
-
@stephenw10 said in Is it possible for one to "slip through"?:
Ok, so that would block connections from that subnet inbound on WAN. And since it's a floating rule it would do so before and pass rules you might have on the WAN tab. You haven't explicitly confirmed it but I assume you have a port forward to the server on WAN with linked firewall rules there?
Yes, I do have a port forward going to the server. I should have included that. I’ll post an image as soon as I get back to a PC.
-
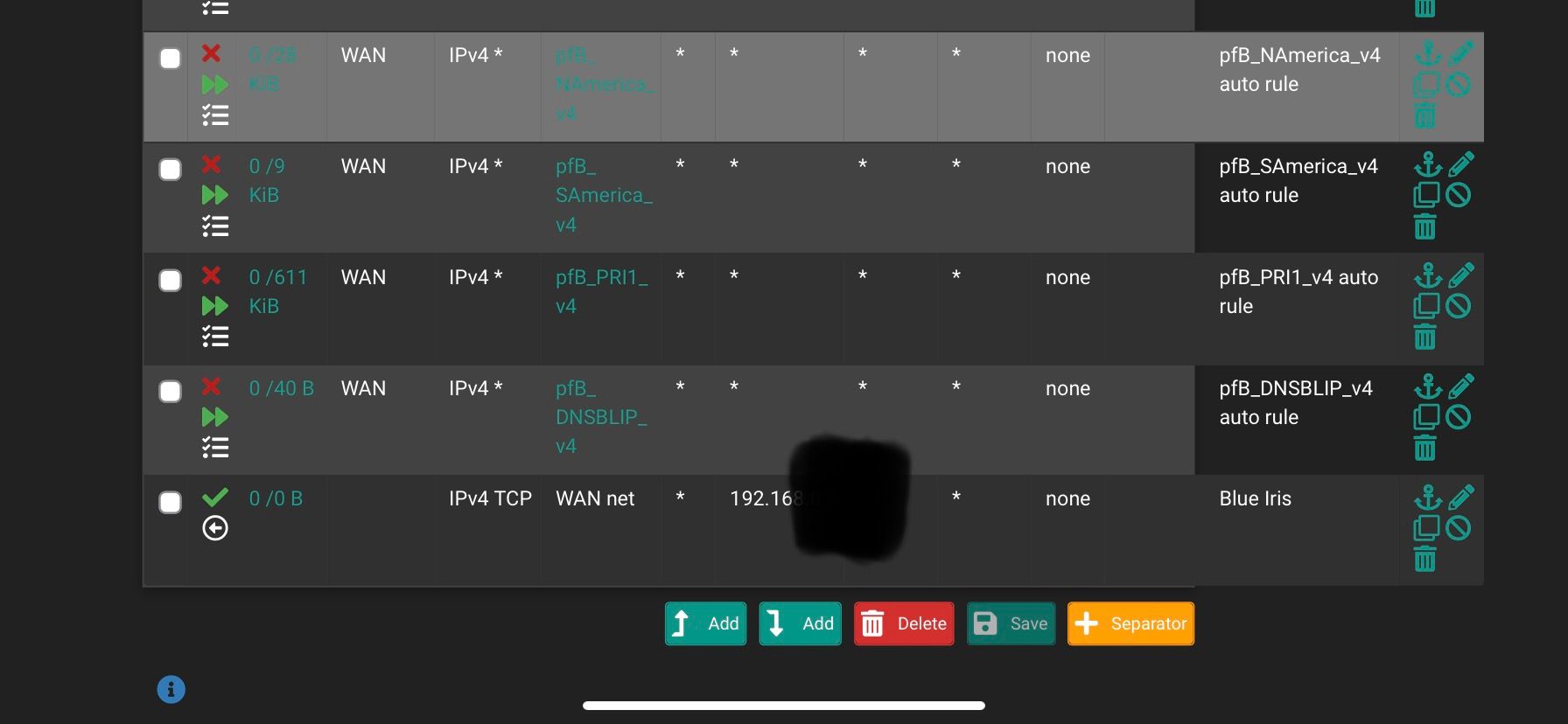
Okay. There it is. Been quite busy at work.
-
@stephenw10 Now that I look at it, something seems off. I'm not quite sure.
-
@obxjeepguy yeah that is not a port forward, that is a allow rule outbound to some 192.168 address, why would you think you need to hide a rfc1918 address.
-
Yes, very unlikely that rule would ever match anything. You can see no states have been opened by it. I would just disable that.
You can see the port forward in Firewall > NAT > Port Forwards.
The associated firewall rule will be on the WAN tab.
Steve