Ubiquiti USG-3P to PFSense
-
@nightlyshark said in Ubiquiti USG-3P to PFSense:
@macusers You need to be able to PPPoE from your USG to your ISP (Internet Provider) through your CPE (customer premises equipment, the cheep modem, router or both in one your ISP gives you), in order to have a true public IPv4. The ability to connect your own router (USG) through your CPE modem hinges on either have your CPE not block layer 2 direct PPPoE connections from other devices through it's modem (layer 2) stream (what is called PPPoE passthrough and is usually only enabled by calling your ISPs support and specifically request it) or have the CPE modem not connect to your ISP at all (bridge mode, again, consult your ISP for details). You then configure USG with PPPoE.
PPPoE is a Layer 2 protocol, meaning its packets are not routable, eg are not sent to an IP from USG, but rather, the USG must be able to connect with your ISP on a "switch" (Data Link Layer) level, to put it simply, with MAC addresses. That is why the modem needs to allow PPPoE, because it bypasses it entirely. I hope I did not confuse the issue, some things may be lost in translation (english is my second language, not my native)
I'm very confused here - perhaps the lack of my understandimg but very confused. I do get the real Public IPv4 from ISP, which is assigned to me as Static.
This is tghe WAN setup on USG:
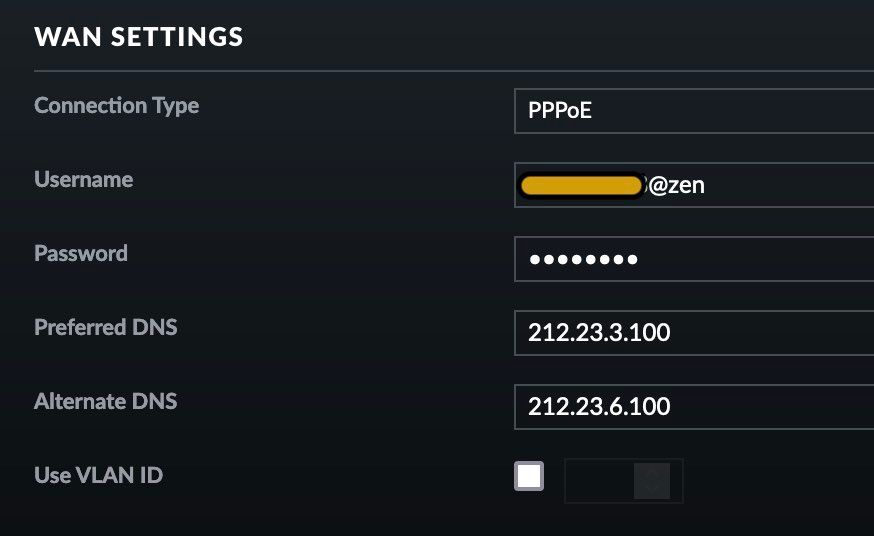
And this WAN in pfSense:
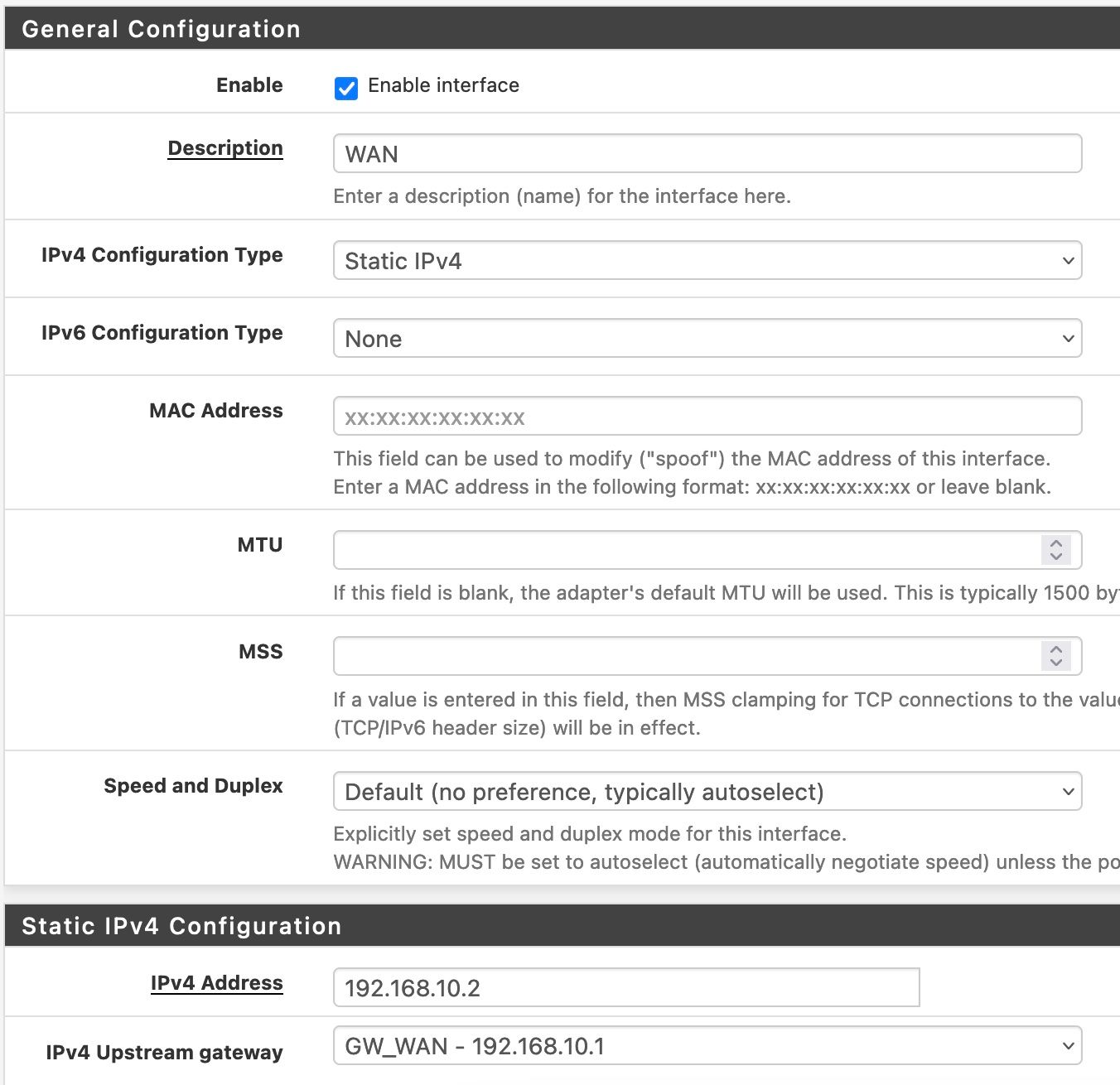
What am I missing?
My another issue is: as USG cannot connect the CK (hence cannot adopt), cannot do much in terms of configuration on USG apart from those settings only. -
@macusers To clarify:
You want to have a topology of:
---INTERNET---
---ISP PPPoE endpoint---
---ISP CPE Modem with PPPoE passthrough enabled---
---USG PPPoE configuration of WAN interface---
---USG NAT---
---PfSense FW---
---Clients---or
---INTERNET---
---ISP PPPoE endpoint---
---ISP CPE Modem with PPPoE passthrough enabled---
---PfSense PPPoE configuration of WAN interface---
---PfSense NAT---
---USG and other Clients---
? -
@macusers For example, my config is:
---INTERNET---
---ISP PPPoE endpoint---
---ISP CPE Modem with PPPoE passthrough enabled---
---PfSense:
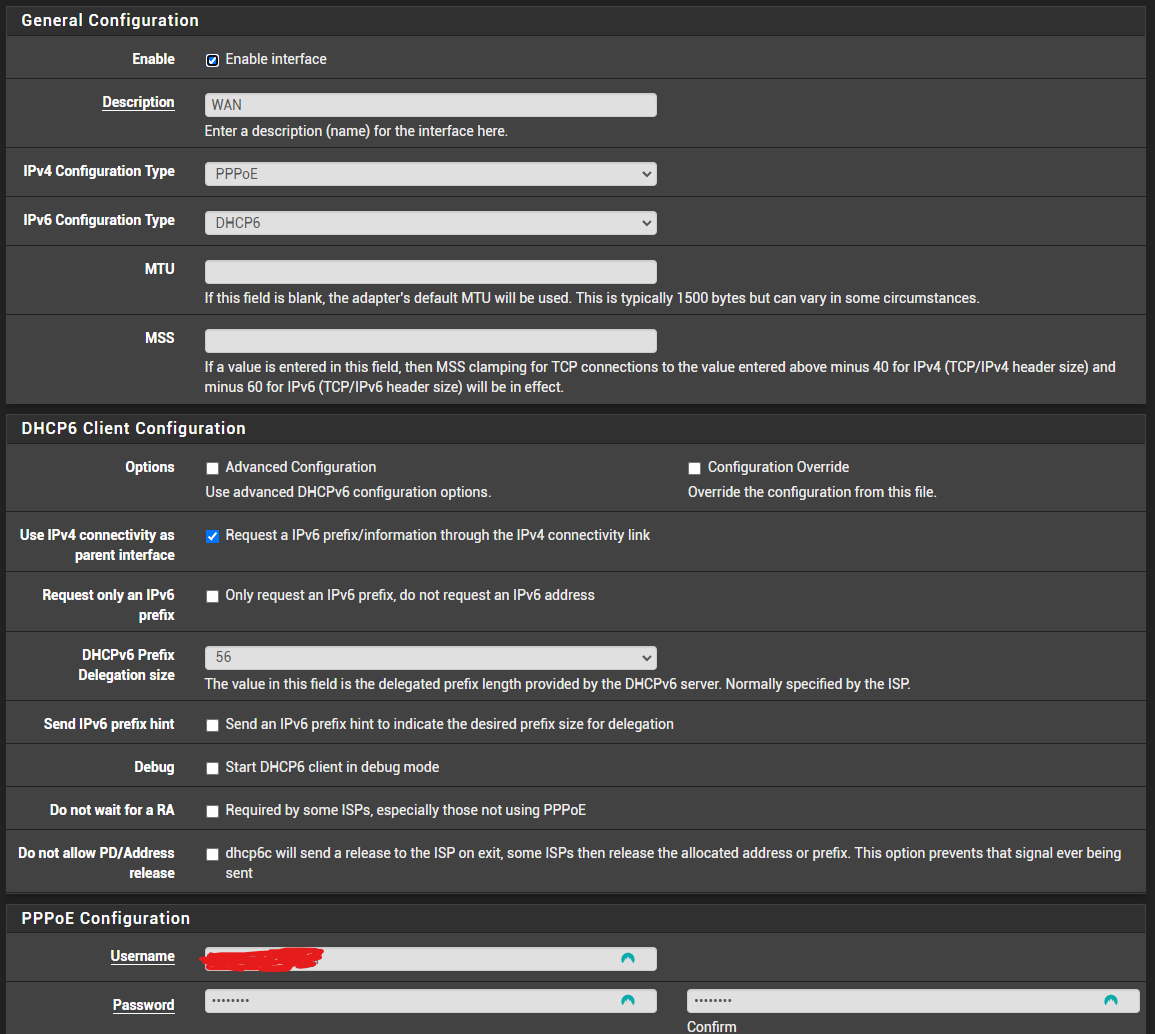
---PfSense NAT---
---Clients--- -
@macusers USG and controller need to be in the same broadcast domain (same "switch", same VLAN, same IPv4 subnet, eg 192.168.1.2 for USG and 192.168.1.200 for the controller) in order to adopt devices. I am not trying to nag you, but this in particular is a UI community issue...
-
@macusers I edited the posts because I forgot the CPE modem...

-
You can adopt devices between different subnets but you need to use a different method. Like at the CLI of the switch/ap etc.
-
@nightlyshark said in Ubiquiti USG-3P to PFSense:
@macusers USG and controller need to be in the same broadcast domain (same "switch", same VLAN, same IPv4 subnet, eg 192.168.1.2 for USG and 192.168.1.200 for the controller) in order to adopt devices. I am not trying to nag you, but this in particular is a UI community issue...
I'm not sure about if it's the special case for USG only but that's not true for Unifi switchs or APs. My controller is always on a seperate network and 12 other devices are happily adopted. As long long the device in question can ping the controller IP, it can be adopted. I think my issue is: USG doesn't know how to get to the 10.0.20.1/28 subnet from it's 192.168.10.1 address.
-
Hmm, the routing table implies it does.
Can it not ping to it?
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
You can adopt devices between different subnets but you need to use a different method. Like at the CLI of the switch/ap etc.
yeah, I tried from the CLI, but main issue is USG cannot reach to controller to send the adoption request - that was my 2nd issue in my original post. form
CKtoUSGping is fine but not the other way around. -
Then check the firewall rules on the pfSense WAN
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
Then check the firewall rules on the pfSense WAN
I have this rule on WAN interface:
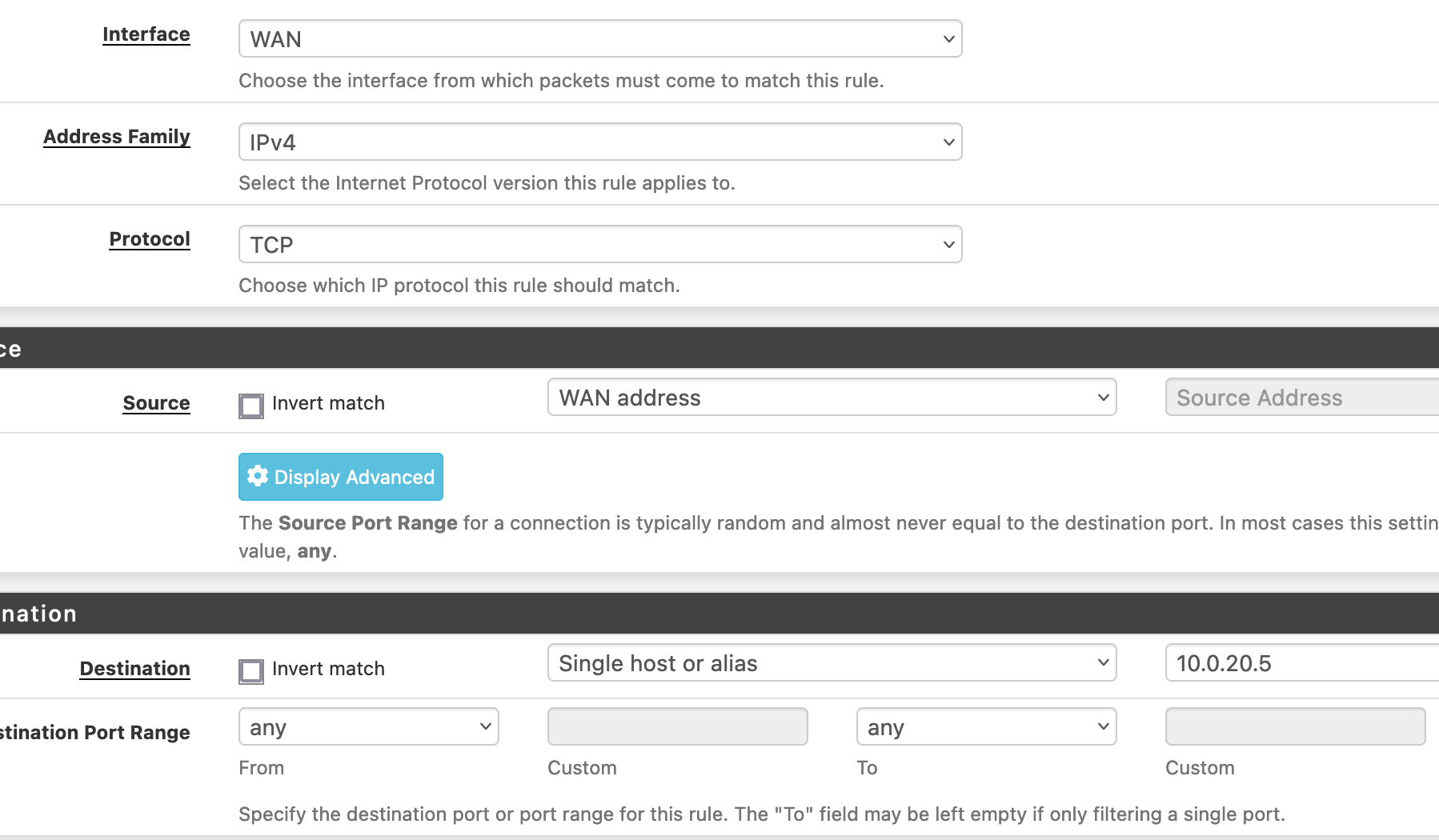
Source is wrong?
-
Should be 'WAN net'. That will include the USG's interfacein the WAN subnet.
And you might want to allow icmp also if you're testing with ping.
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
And you might want to allow icmp also if you're testing with ping.
yeeppp!!!!
that was the issue - it needed ICMP enabled. the moment I did that I could adopt the USG in the controller.Now, to fix the first issue - in coming VPN connection
-
@stephenw10, any idea what's might be the issue with VPN connection - double natting? Or need to setup some sort of port forwarding on USG?
-S
-
What sort of VPN is it? How are you testing?
If it's incoming to pfSense then you will need to port forward that traffic in the USG.
-
@stephenw10
it's OpenVPN. port forward teh traffic to VPN subnet or pfSense WAN IP?
Normally I connect though mobile phone (to get out of home network) and VPN back to see if it's connecting. -
Forward the encrypted OpenVPN traffic to the pfSense WAN in the USG. So by default that would be UDP port 1194 but it could be whatever you configured it as.
Steve
-
VPN worked

-
@stephenw10
Is it possible setup a static route (from WAN to LAN) on and disable NAT'ing on USG? IS it better? Or will it even work?-S
-
You must have NAT somewhere between your public IP and the private internal subnets in order for clients to be able to connect out and replies to know where to come back to.
By default both the USG and pfSense will apply outbound NAT only one of them needs to. The USG needs to do it in your setup because it has the public IP to NAT to.
You can disable outbound NAT on the USG as long as it has static routes to the subnets behind pfSense.
Steve