Ubiquiti USG-3P to PFSense
-
Hmm, the routing table implies it does.
Can it not ping to it?
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
You can adopt devices between different subnets but you need to use a different method. Like at the CLI of the switch/ap etc.
yeah, I tried from the CLI, but main issue is USG cannot reach to controller to send the adoption request - that was my 2nd issue in my original post. form
CKtoUSGping is fine but not the other way around. -
Then check the firewall rules on the pfSense WAN
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
Then check the firewall rules on the pfSense WAN
I have this rule on WAN interface:
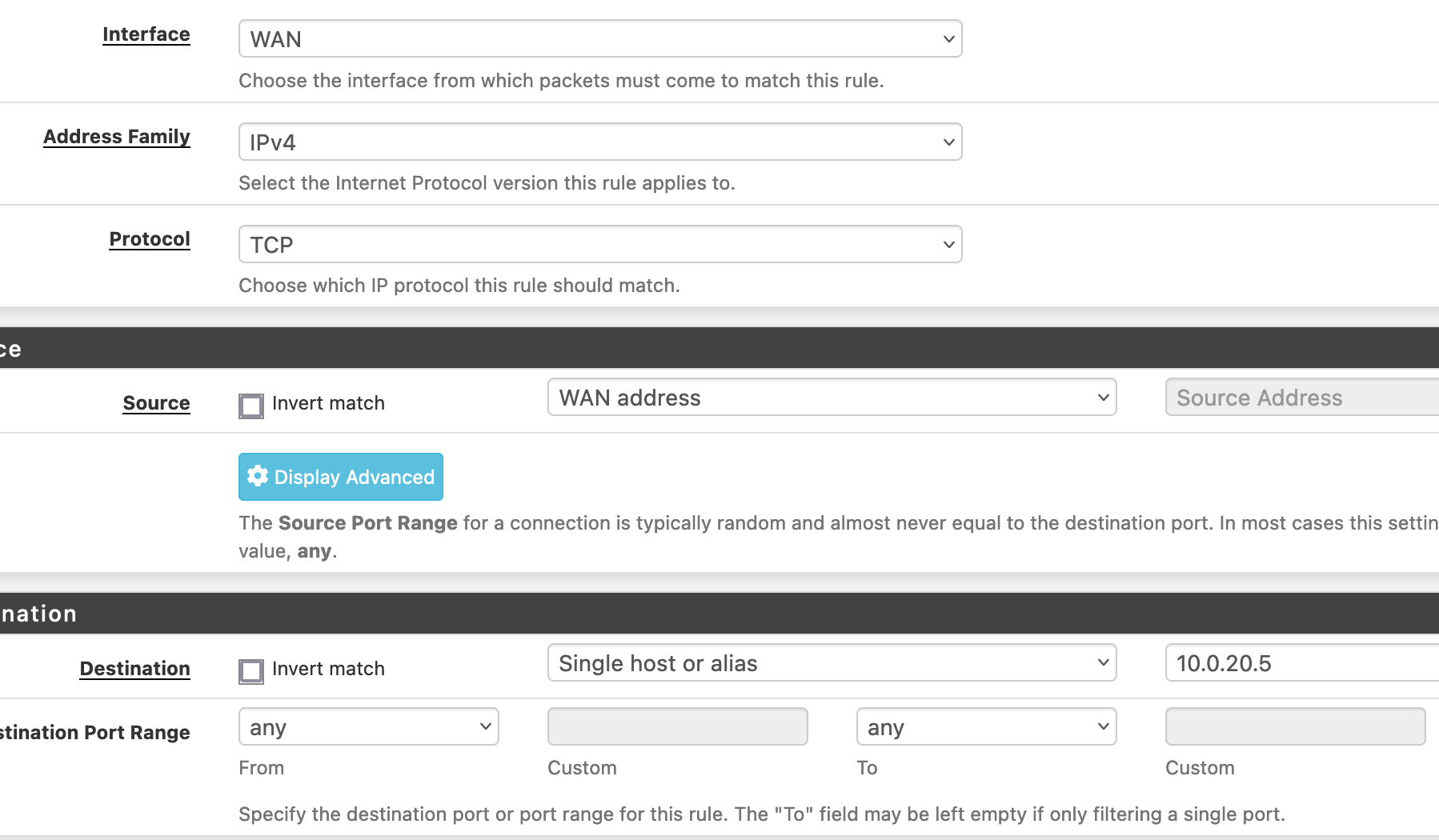
Source is wrong?
-
Should be 'WAN net'. That will include the USG's interfacein the WAN subnet.
And you might want to allow icmp also if you're testing with ping.
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
And you might want to allow icmp also if you're testing with ping.
yeeppp!!!!
that was the issue - it needed ICMP enabled. the moment I did that I could adopt the USG in the controller.Now, to fix the first issue - in coming VPN connection
-
@stephenw10, any idea what's might be the issue with VPN connection - double natting? Or need to setup some sort of port forwarding on USG?
-S
-
What sort of VPN is it? How are you testing?
If it's incoming to pfSense then you will need to port forward that traffic in the USG.
-
@stephenw10
it's OpenVPN. port forward teh traffic to VPN subnet or pfSense WAN IP?
Normally I connect though mobile phone (to get out of home network) and VPN back to see if it's connecting. -
Forward the encrypted OpenVPN traffic to the pfSense WAN in the USG. So by default that would be UDP port 1194 but it could be whatever you configured it as.
Steve
-
VPN worked

-
@stephenw10
Is it possible setup a static route (from WAN to LAN) on and disable NAT'ing on USG? IS it better? Or will it even work?-S
-
You must have NAT somewhere between your public IP and the private internal subnets in order for clients to be able to connect out and replies to know where to come back to.
By default both the USG and pfSense will apply outbound NAT only one of them needs to. The USG needs to do it in your setup because it has the public IP to NAT to.
You can disable outbound NAT on the USG as long as it has static routes to the subnets behind pfSense.
Steve
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
You must have NAT somewhere between your public IP and the private internal subnets in order for clients to be able to connect out and replies to know where to come back to.
yeah, of course!!
I meant to ask: is it better to do the natting on pfSense and disable on USG or otherway round. As thenattingis enabled on USG, is it safe to completely disable on pfSense? do I need to anything else as well, if NAT is disabled on pfSense?-S
-
You have to have NAT enabled on the USG because it has the public IP.
You can disable NAT on pfSense as long as the USG has static routes to the subnets behind pfSense and is setup to NAT those.
-
@macusers For most small scale (under 20 users) intents and purposes, you actually don't need both devices, they complicate setup, add latencies and cause headaches. PfSense can do everything USG does, a lot faster (depending on the hardware) and a lot more reliably.
But, all that is always, just my opinion.
-
@nightlyshark said in Ubiquiti USG-3P to PFSense:
@macusers For most small scale (under 20 users) intents and purposes, you actually don't need both devices, they complicate setup, add latencies and cause headaches. PfSense can do everything USG does, a lot faster (depending on the hardware) and a lot more reliably.
But, all that is always, just my opinion.
Your are absolutely correct! that USG was sitting duck and as my rst of the equipements are all UniFi, I thought it would be nice to fiil the empty space on the Controller dashboard.
On a seperate note, what can I do for the DPI (and possiblly IDS) on pfSense?
-S
-
Use Snort or Suricata. https://docs.netgate.com/pfsense/en/latest/packages/snort/index.html
-
@stephenw10 Is there a free (and functional) Snort licence (I think Snort is Cisco, right?)?
-
@nightlyshark said in Ubiquiti USG-3P to PFSense:
@stephenw10 Is there a free (and functional) Snort licence (I think Snort is Cisco, right?)?
If you mean the Snort Subscriber Rules, then there are two options. There is a free version that you can get by simply registering an email address. That will give you an Oinkcode which is the license key you need to input into the Snort GUI. There is also a paid version of the rules and associated Oinkcode. That license is $29.99 USD annually for individual home use, or around $300 USD annually (if I recall) for commercial or business use. The difference in those two rule packages is that the free license version only gets new rules added after those rules have been in the paid version for 30 days. Or stated differently, new rules are added to the free license version 30 days or more AFTER they were added to the paid version. So, the free version will NOT have detection for the newest zero-day and similar exploits once discovered.
A third free option, but not nearly so useful, is the Snort GPLv2 Community Rules. Those are 100% free and require no registration. But that package only contains rules the Snort Vulnerability Research Team (VRT) has released into public domain. That means those rules are usually quite old.
When choosing Rules to enable on the GLOBAL SETTINGS tab in Snort, if you have a paid Subscriber Rules Oinkcode, then you do NOT need to use the GPLv2 Community Rules. They are included as part of the rules package that downloads using your paid subscriber Oinkcode.