how to block persistent and repeated http inboud connection
-
Hi!
I'm searching how to block source IP by number http inbound connections per second with pfSense+pfBlockerNG or Suricata. Is there any wayto do this?
Thanks, Alessandro
-
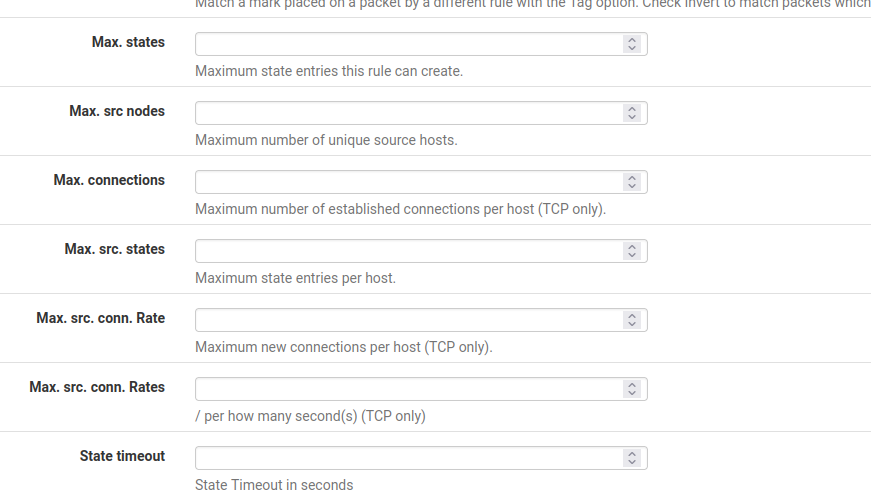
@alexferro32 I suppose that what you want is this?
If so, check advanced option in your inbound firewall rule.
-
@alexferro32 said in how to block persistent and repeated http inboud connection:
Hi!
I'm searching how to block source IP by number http inbound connections per second with pfSense+pfBlockerNG or Suricata. Is there any wayto do this?
Thanks, Alessandro
You can do this with either Snort or Suricata by using the rule alert threshold feature. This is an advanced feature not directly provided in the GUI, and it would require you either write your own custom rule, or copy an existing similar rule and then modify it accordingly. Once you have your custom rule created, you can add it by going to the RULES tab for the Snort interface, selecting Custom Rules in the drop-down, and then typing or pasting your new rule into the text box and saving it.
Here is the Snort documentation on the rule threshold parameter: http://manual-snort-org.s3-website-us-east-1.amazonaws.com/node35.html.
And here is the same documentation for Suricata: https://suricata.readthedocs.io/en/suricata-6.0.0/configuration/global-thresholds.html.
-
-
@johnpoz said in how to block persistent and repeated http inboud connection:
@bmeeks While sure could do this with IPS, wouldn't you just be able to do it via the advanced options that @mcury mentioned.
I have not had to play with such a rule.. But I would think in the advanced section you could limit rate of connections just in the firewall rule?
I have never played with that either. I suppose, from looking over the available parameters, it could work.
To tell the truth I was specifically only paying attention to the OP's question about the two IDS/IPS packages, so I answered from that angle. I did not mean to imply @mcury's method would not work.
-
@bmeeks no I didn't think you were ;)
And yeah everyone normally looks at a problem from their angle what they are most familiar with.. I was just kind of hoping maybe you had played with them before.. But guess not...
Should be something to play with, never had need before to test the rate limiting - but pretty sure their are some fun tools to generate traffic as different rates to see if the advanced options work ;) heheh
-
@bmeeks ive done something similar. Make sure you acquire a baseline first so you can set your threshold accordingly.