22.05-RELEASE (amd64) Unable to check for updates?
-
Hmm, 15mins is far longer than I'd expect for any package. Unless your WAN is very slow.
I would check the system logs if it's still doing it.
-
@stephenw10 I'm having this problem again. This DNS Lookout command times out after 2 minutes with Host "firmware.netgate.com" could not be resolved.
9.9.9.9 No response
149.112.112.112 No responseI'm also getting the Notice:
An error occurred while uploading the encrypted Netgate pfSense Plus configuration to https://acb.netgate.com/save ( Unable to resolve acb.netgate.com )I am running pfSense 23.05-RELEASE (amd64) on a Zima SBC (4GB RAM), 240GB SSD (zfs), Intel PRO/1000 PT dual port.
-
What if you query 9.9.9.9 directly like:
steve@steve-MacBookPro:~$ dig +short @9.9.9.9 firmware.netgate.com 208.123.73.209 208.123.73.207 -
@stephenw10 I entered this from the pfsense+ command line and got:
;; communications error to 9.9.9.9#53: timed out
;; communications error to 9.9.9.9#53: timed out
;; communications error to 9.9.9.9#53: timed out
;; no servers could be reached -
@TAC57 if you’re forwarding to Quad9 it sounds like that isn’t working…Snort block maybe? Try turning off forwarding or use a different DNS.
-
@SteveITS In System / General Setup / DNS Servers I changed 9.9.9.9 to 1.1.1.1 and ran the command above with @1.1.1.1 and got the following:
;; communications error to 1.1.1.1#53: timed out
;; communications error to 1.1.1.1#53: timed out
;; communications error to 1.1.1.1#53: timed out
;; no servers could be reached -
Can you query either of those from a host behind pfSense?
-
@stephenw10
This from my windows command prompt:
Microsoft Windows [Version 10.0.19045.3031]
(c) Microsoft Corporation. All rights reserved.C:\Users\Tom>ping 9.9.9.9
Pinging 9.9.9.9 with 32 bytes of data:
Reply from 9.9.9.9: bytes=32 time=266ms TTL=57
Reply from 9.9.9.9: bytes=32 time=15ms TTL=57
Reply from 9.9.9.9: bytes=32 time=15ms TTL=57
Reply from 9.9.9.9: bytes=32 time=16ms TTL=57Ping statistics for 9.9.9.9:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 15ms, Maximum = 266ms, Average = 78msC:\Users\Tom>ping 1.1.1.1
Pinging 1.1.1.1 with 32 bytes of data:
Reply from 1.1.1.1: bytes=32 time=267ms TTL=57
Reply from 1.1.1.1: bytes=32 time=16ms TTL=57
Reply from 1.1.1.1: bytes=32 time=15ms TTL=57
Reply from 1.1.1.1: bytes=32 time=15ms TTL=57Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 15ms, Maximum = 267ms, Average = 78msC:\Users\Tom>ping 8.8.8.8
Pinging 8.8.8.8 with 32 bytes of data:
Reply from 8.8.8.8: bytes=32 time=14ms TTL=115
Reply from 8.8.8.8: bytes=32 time=13ms TTL=115
Reply from 8.8.8.8: bytes=32 time=14ms TTL=115
Reply from 8.8.8.8: bytes=32 time=14ms TTL=115Ping statistics for 8.8.8.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 13ms, Maximum = 14ms, Average = 13msC:\Users\Tom>ping acb.netgate.com
Pinging acb.netgate.com [208.123.73.212] with 32 bytes of data:
Reply from 208.123.73.212: bytes=32 time=39ms TTL=51
Reply from 208.123.73.212: bytes=32 time=39ms TTL=51
Reply from 208.123.73.212: bytes=32 time=38ms TTL=51
Reply from 208.123.73.212: bytes=32 time=39ms TTL=51Ping statistics for 208.123.73.212:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 38ms, Maximum = 39ms, Average = 38ms -
@SteveITS I have DNS resolver enabled. What is the easiest way to turn all this off?
And this has to be related:
An error occurred while uploading the encrypted Netgate pfSense Plus configuration to https://acb.netgate.com/save ( Unable to resolve acb.netgate.com ) @ 2023-05-28 16:49:05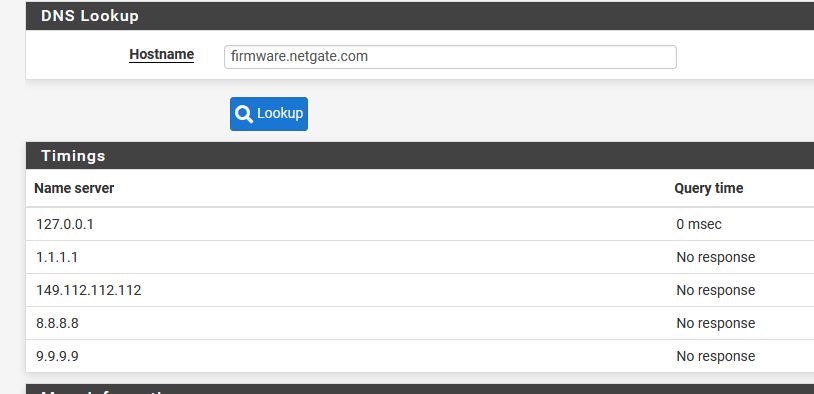
-
Do you have the DNS resolver set to forwarding mode though?
If you do try just unchecking that so it resolves directly.
-
@stephenw10 It was, unchecking made no difference.
-
Hmm. Just to be clear is that failing to resolve any host? Even when resolving directly?
That sounds like it must be something blocking DNS requests from the firewall. But I expect anything doing that to apply to NAT'd traffic from clients behind it also.

-
@stephenw10 I'm sorry but I don't understand your question. Is there a screenshot you'd like to see or some setting I can change that might solve this issue.
BTW I ran the dig command from a Raspberry Pi on my network:
crites@raspberrypi:~ $ dig +short @9.9.9.9 firmware.netgate.com
208.123.73.207
208.123.73.209crites@raspberrypi:~ $ dig +short @9.9.9.9 acb.netgate.com
208.123.73.212I have a basic homelab setup with some desktop computer, TrueNAS server running Plex, and some IOT stuff.
-
@TAC57 You’ve posted DNS to third party servers works from devices on LAN but not pfSense. Which implies something is blocking it. Can you post your LAN rules and any floating rules, and routes (diagnostics menu)?
-
I meant does Diag > DNS Lookup fail for any host or just firmware.netgate.com?
Are you running Snort or Suricata?
-
@stephenw10 Before rebooting I'd get the Unable to check for updates and DNS Lookup would not report anything from any host. On rebooting pfsense it now reports on the latest version. And DNS Lookup does report back (see below) and it reports back from google.com
I am running Snort.
-
@SteveITS I'm not running any floating rules. Can DM you my routes?
LAN rules:
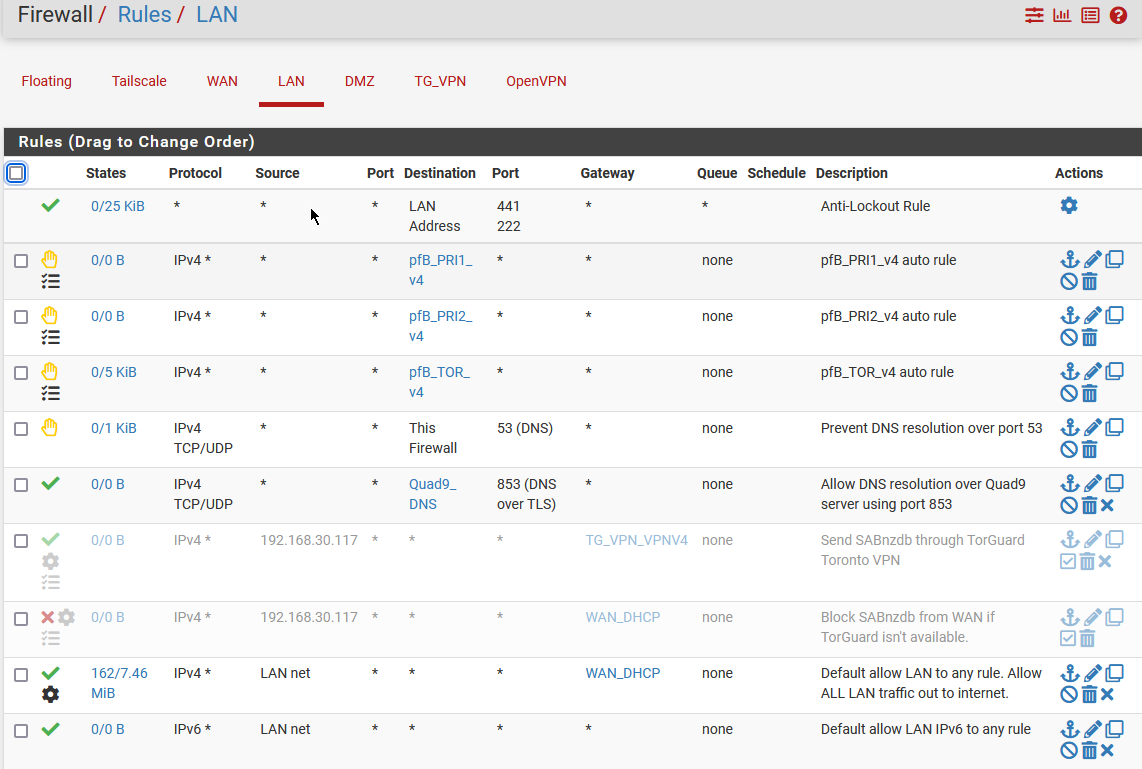
-
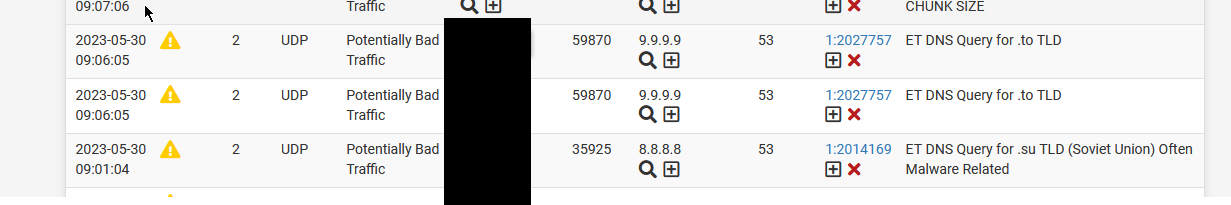
@TAC57 and were those DNS IPs on the Snort alert page? That’s why I asked about Snort above. Reading back it sounds like a restart fixed it in January also. Restarting would empty the Snort block table.
-
Yup, disable Snort. Reboot. Retest.
-
@SteveITS
I've been running Snort forever. I'll disable it and see what happens.
I'll disable it and see what happens.