22.05-RELEASE (amd64) Unable to check for updates?
-
@stephenw10 It was, unchecking made no difference.
-
Hmm. Just to be clear is that failing to resolve any host? Even when resolving directly?
That sounds like it must be something blocking DNS requests from the firewall. But I expect anything doing that to apply to NAT'd traffic from clients behind it also.

-
@stephenw10 I'm sorry but I don't understand your question. Is there a screenshot you'd like to see or some setting I can change that might solve this issue.
BTW I ran the dig command from a Raspberry Pi on my network:
crites@raspberrypi:~ $ dig +short @9.9.9.9 firmware.netgate.com
208.123.73.207
208.123.73.209crites@raspberrypi:~ $ dig +short @9.9.9.9 acb.netgate.com
208.123.73.212I have a basic homelab setup with some desktop computer, TrueNAS server running Plex, and some IOT stuff.
-
@TAC57 You’ve posted DNS to third party servers works from devices on LAN but not pfSense. Which implies something is blocking it. Can you post your LAN rules and any floating rules, and routes (diagnostics menu)?
-
I meant does Diag > DNS Lookup fail for any host or just firmware.netgate.com?
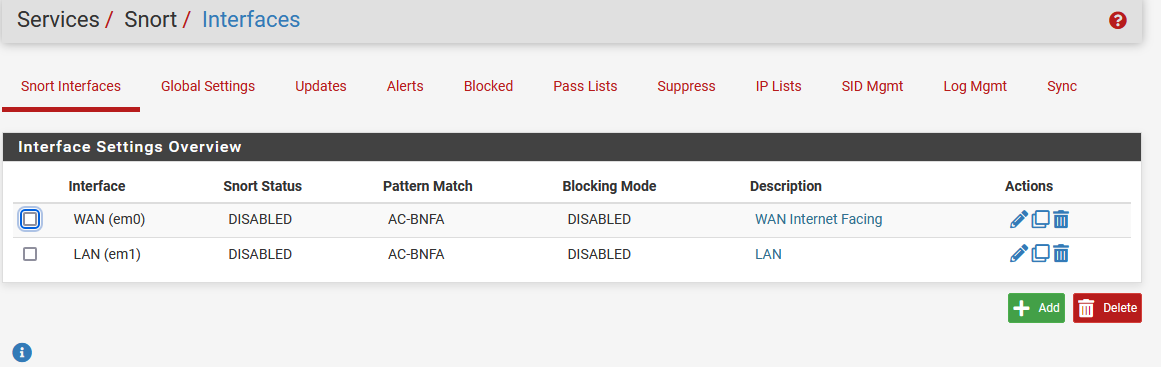
Are you running Snort or Suricata?
-
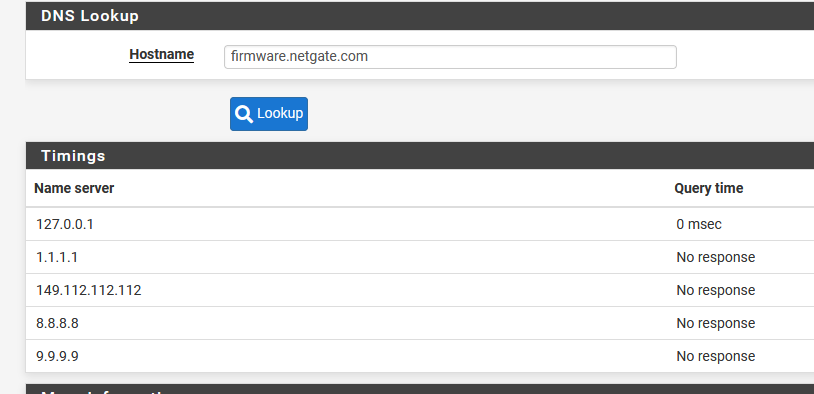
@stephenw10 Before rebooting I'd get the Unable to check for updates and DNS Lookup would not report anything from any host. On rebooting pfsense it now reports on the latest version. And DNS Lookup does report back (see below) and it reports back from google.com
I am running Snort.
-
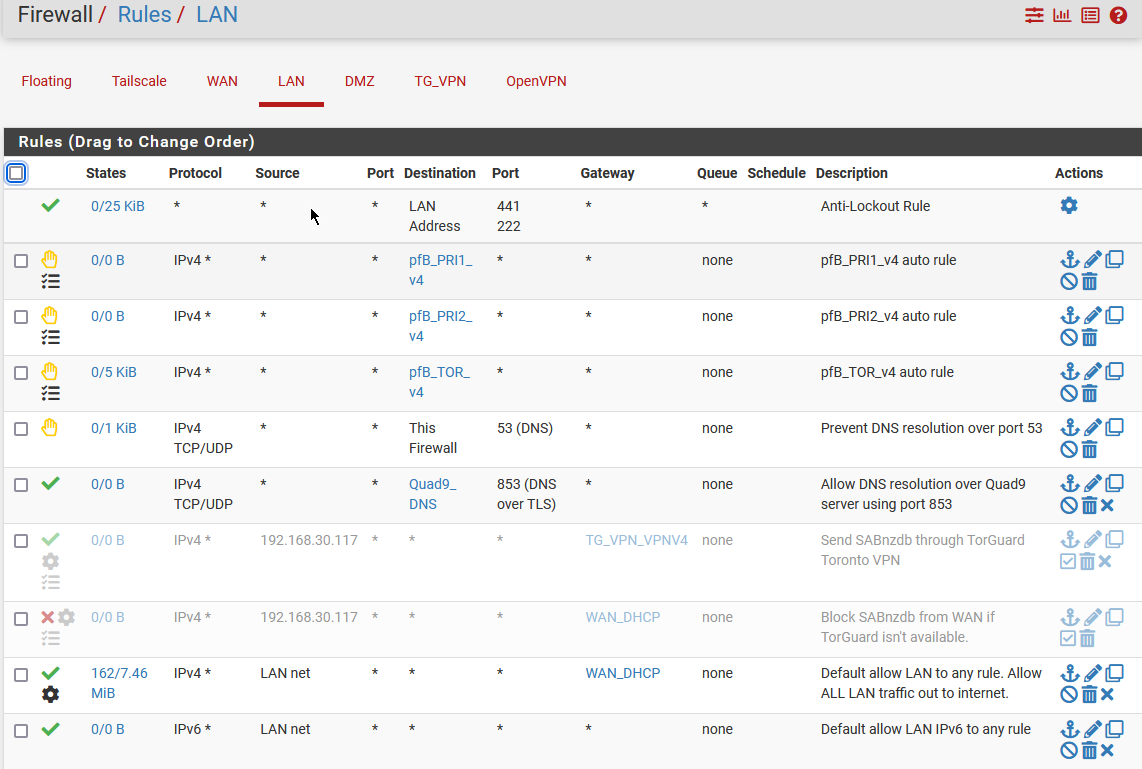
@SteveITS I'm not running any floating rules. Can DM you my routes?
LAN rules:
-
@TAC57 and were those DNS IPs on the Snort alert page? That’s why I asked about Snort above. Reading back it sounds like a restart fixed it in January also. Restarting would empty the Snort block table.
-
Yup, disable Snort. Reboot. Retest.
-
@SteveITS
I've been running Snort forever. I'll disable it and see what happens.
I'll disable it and see what happens.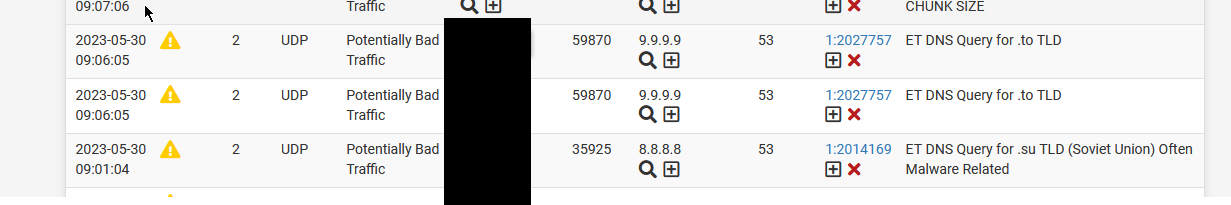
-
@stephenw10 I disabled Snort, rebooted and still unable to check for updates. Also, DNS Look up doesn't return any IPs.
-
Make sure the Snort block table is actually cleared, assuming you had Snort in blocking mode. Check Diag > Tables > Snort2c.
Snort pulls new signatures automatically. It can start alerting/blocking things that were previously fine without warning!
-
@stephenw10 Snort2c table is empty.
I've disabled Snort and have rebooted pfsense.
pfsense is still reporting 'Unable to check for updates'.
Diag / DNS Lookup times out with firmware.netgate.com, google.com, 8.8.8.8. It took about 3 minutes to get the message 'Host "firmware.netgarte.com" cound not be resolved.'
I can ping any of these host from a Raspberry Pi and replys.
To switch from the Status / Dashboard screen to the System / Update screen takes 1.5 minutes and then about another 30 seconds to report that it's Unable to check for updates.
I'm also still getting the notice "An error occurred while uploading the encrypted Netgate pfSense Plus configuration to https://acb.netgate.com/save ( Unable to resolve acb.netgate.com ) @ 2023-05-30 16:53:11"
I'm running pfsense on a Zima SBC:
Intel(R) Celeron(R) CPU N3450 @ 1.10GHz
4 CPUs : 1 package(s) x 4 core(s)
AES-NI CPU Crypto: Yes (active)
IPsec-MB Crypto: Yes (inactive)
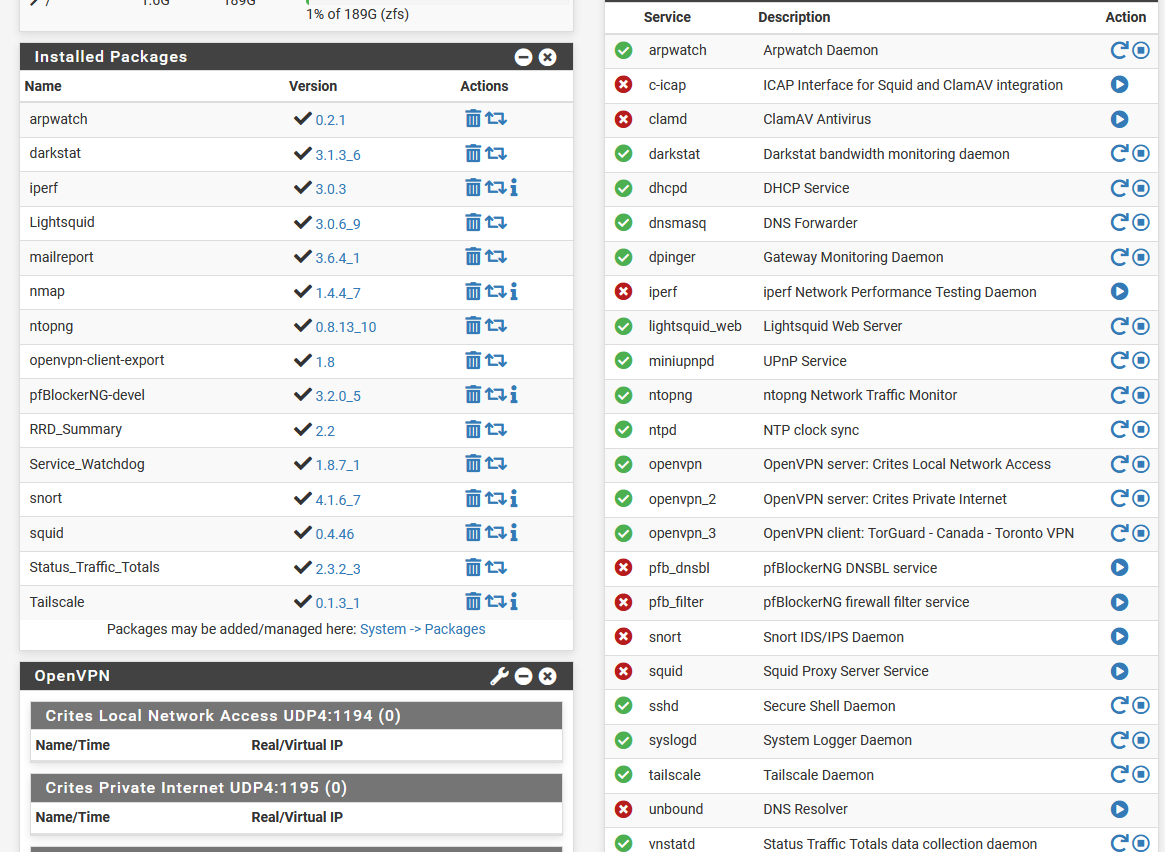
QAT Crypto: NoThese are my installed packages / Services:
-
Oh you're not using the resolver (Unbound) at all. You're using the forwarder (DNSMasq).
In that as a test I would try disabling DNSMasq and enabling Unbound and see if that makes any difference. With that it should resolve directly.
-
@stephenw10 Plus he’s running practically running every pfSense package!
-
@DefenderLLC If running a homelab with a TrueNAS Plex server, a few computers, and some IOT devices, what packages do you recommend to balance security, performance, and ease of use?
I must admit I've implemented (or attempted) most of these packages after reading about, or seeing a video on, some cool package that I think I need or was interested in learning about. Most of these I've setup with videos from https://forums.lawrencesystems.com/.
-
@TAC57 judging by your screenshots, your CPU is not very powerful to be running all of those packages at the same time. Just wait until you actually start doing IPS blocking or turn on a bunch of rules with pfBlockerNG. How much memory do you have allocated to this box?
-
@DefenderLLC I'm running pfsense on a Zima SBC:
Intel(R) Celeron(R) CPU N3450 @ 1.10GHz, 4GB RAM
4 CPUs : 1 package(s) x 4 core(s)
AES-NI CPU Crypto: Yes (active) -
@TAC57 That's not nearly enough horsepower to be running all of those packages. I would probably stick with pfBlockerNG and Snort only with not too many rules applied. They both require a lot of RAM if you enable too many rulesets.
-
I still wouldn't expect it to be blocking all outgoing DNS queries though.
Did you test switching to the resolver directly?