Shared Firewall for Voip Service
-
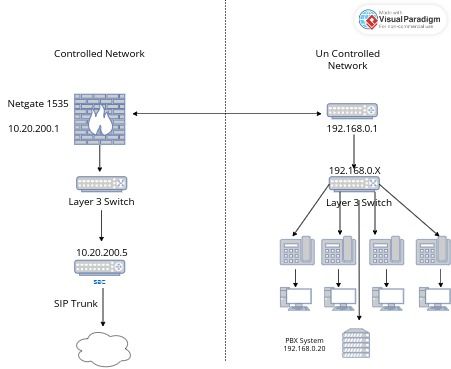
Im trying to figure the best way to Share my Session Border Controller for a sub tenant Phone System. Im trying to come up with a solution that wont require me to Touch there Network. I'll put a Diagram of what i have for a network. The PBX 192.168.0.20 needs to access the Session Border Controller (10.20.200.5) for its Sip Trunk. I have access to the PBX but thats it.
-
@halter_joel Im not all together following what the requirement. So the tenant is in the 192.168.0 network. You are in the 10.20.200 network.
You want the tenant to access 10.20.200.5?
Am i understanding it correctly? -
@michmoor
That is correct i only want the PBX 192.168.0.20 to access the SBC 10.20.200.5I thought i could create the 192.168.0.254 network on my Pfsense and plug the Ethernet cable into their Switch and allow only the 192.168.0.20 traffic thru. When i did that i can't get any traffic from pbx to hit the SBC.
-
@halter_joel Oh..
So create a firewall rule permitting the single host 192.168.0.20 to connect to single host 10.20.200.5. The port(s) you'll need can be defined in the rule as well.Does SBC know how to access your PBX? Is there routing in place?
-
When i Plug the Pfsense port associated to the new network i created 192.168.0.254, into the Customers Switch and create a rule that allows all traffic to and from i don't get any traffic. I plug my Laptop into the switch and ping 192.168.0.254 i get nothing. I have also tried to take the new network and have it try to dhcp and it wont pull an address from their network.
I'm assuming because when i plug a laptop into their network i pull a gateway of 192.168.0.1 and it has no idea that 192.168.0.254 exist. I thought that the pfsense would pull an IP from their network though. -
@halter_joel The link between the Netgate and 192.168.0.1.
Is that over a WAN or VPN? Is this within a building and directly connected? Whats the expectation of connectivity? How are you guys supposed to talk to each other? If you can explain that then we can move forward. Otherwise how are you expacting your network to talk to the Un Controlled network? -
@michmoor
The link is a Cat 5e Cable. Both companies are located in the same building.The goal here is to create a secure way for the PBX to get to the SBC for SIP and RTP. I feel like there should be an easy way to do this but for some reason its been difficult. I have Netgate 2100 that i could also use to put in place between the two but i feel like this method should work.
-
@halter_joel but you never answered how each network knows about each other. Do you have routes in place? If you’re able to ping each other then this is just a simple firewall rule.
-
These two networks aren't currently connected so they don't know anything about each other. That is what i am trying to accomplish. Both Networks are in the same building. If i had access to their Router i would put some static routes in and id be good to go. I am trying to come up with a solution without touching their network.
-
@halter_joel
Once you are connected physically, assign a /30 network to the link.
So for example you will be 10.1.1.1/30 and they will be 10.1.1.2/30Once you got that transit in place, create your static route. They will need one for you as well.
After that apply firewall rules on that new interface/transit link and thats it.