WPA_Supplicant
-
Ah OK. So you're using the version from that attachment I assume.
Those posts are all from right around the time 2.7 was released. You might try just using the included wpa_supplicant version.That has those patches:
https://github.com/pfsense/FreeBSD-src/tree/RELENG_2_7_0/contrib/wpa/src/l2_packet -
@AiC0315 There was talk on the discord channel about changes in the new openssl breaking wpa_supplicant/att 802.1x use.
I don't recall off the top of my in which versionof pf openssl was updated (2.7/23.01 or 23.05.x, or 23.09).
In any event, the fix was to allow reverting back to a less secure usage (tls1) for environment in which wpa_supplicant is executed.
I've pasted the relevant lines to pastebin from the chat.
https://pastebin.com/bxg7qda4
This is a quote of https://discord.com/channels/886329492438671420/927008236584984587/1162122299445616650 from user "D" in the #pfsense channel.
Note you still need to be using the wpa_supplicant binary with the vlan0 patch.
Note2: The whole mac cloning is a non issue. You DON'T have to clone it. But what is important is the mac in the wpa_supplicant.conf file match the mac of the wan interface. So long as the two are the same, you will have connectivity. If they don't match, 802.1x auth will take place but you'll never get a dhcp ip.
-
@GPz1100 said in WPA_Supplicant:
https://pastebin.com/bxg7qda4
Mmm, that looks like it's only for the change to OpenSSL 3, which isn't in 2.7 (yet). Or in 23.05.1.

-
@stephenw10 ^^I believe it was 23.09 that introduced the new openssl.
It's unclear why the OP was unsuccessful with 2.70, given it does include the vlan0 patched wpa_supplicant with the same wpa_supplicant.conf
@AiC0315 said in WPA_Supplicant:
Failed to connect to non-global ctrl_ifname: (nil) error: No such file or directory
This error suggests a missing conf parameter in wpa_supplicant.conf, specifically
ctrl_interface=DIR=/var/run/wpa_supplicantThis goes ABOVE the "network={" array.
-
I'll add that parameter when i have time and see what happens.
Thank you both for helping me try to figure this out
-
@GPz1100
Had time to mess with this last night. using this config.ctrl_interface=DIR=/var/run/wpa_supplicant
eapol_version=1
ap_scan=0
fast_reauth=1
network={
ca_cert="/root/WPA/Certs/CA.pem"
client_cert="/root/WPA/Certs/Client.pem"
eap=TLS..
eapol_flags=0
identity="XX:XX:XX:XX:XX:XX" # Internet (ONT) interface MAC address must match this value
key_mgmt=IEEE8021X
phase1="allow_canned_success=1"
private_key="/root/WPA/Certs/PrivateKey.pem"
}
Works perfectly on 23.05.1 but does not get an IP on 2.7.0. Im using the wpa_supplicant posted on the dslforum link.
At this point I'm about to give up. Now I just have to dercide if I want to pay for plus from here on out -
You tried using the included wpa_supplicant? 2.7 should have the patch to accept vlan0 by default.
-
@AiC0315 Where/when are you initializing wpa_supplicant?
-
@stephenw10
Yes, I used the wpa_supplicant file posted in the dslreports post -
@GPz1100
/sbin/ifconfig igb0 ether "XX:XX:XX:XX:XX:XX" && /root/WPA/wpa_supplicant -B -Dwired -i igb0 -c /root/WPA/wpa_supplicant.conf -P/var/run/wpa_supplicant.pid && sleep 10 && /usr/sbin/wpa_cli logon. (early shellcmd)wpa_cli logoff && sleep 10 && wpa_cli logon (shellcmd)
-
-
@GPz1100
Thanks,
I will take a look when I am able to install 2.7.0 back on my machine. -
@AiC0315 said in WPA_Supplicant:
Yes, I used the wpa_supplicant file posted in the dslreports post
Yes I meant did you try the default wpa_supplicant version that's included in 2.7?
-
@GPz1100 said in WPA_Supplicant:
@stephenw10 ^^I believe it was 23.09 that introduced the new openssl.
It's unclear why the OP was unsuccessful with 2.70, given it does include the vlan0 patched wpa_supplicant with the same wpa_supplicant.conf
@AiC0315 said in WPA_Supplicant:
Failed to connect to non-global ctrl_ifname: (nil) error: No such file or directory
This error suggests a missing conf parameter in wpa_supplicant.conf, specifically
ctrl_interface=DIR=/var/run/wpa_supplicantThis goes ABOVE the "network={" array.
What about
Failed to connect to non-global ctrl-ifname: (nil) error: Success
-
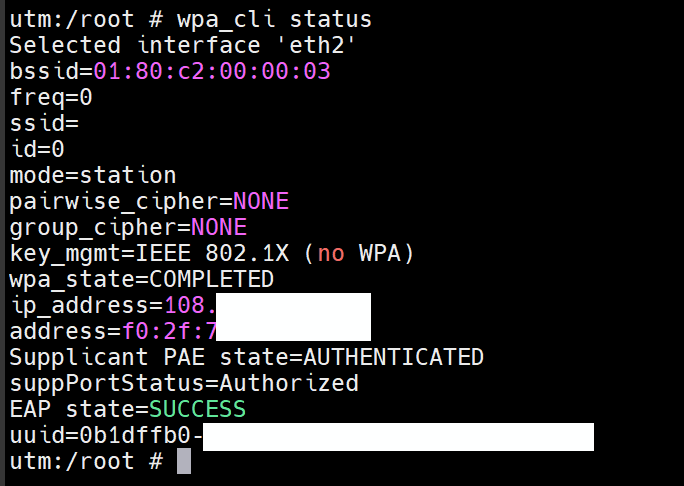
Here is the output of wpa_cli status:
Selected interface 'igb0' bssid=01:80:c2:00:00:03 freq=0 ssid= id=0 mode=station pairwise_cipher=NONE group_cipher=NONE key_mgmt=IEEE 802.1X (no WPA) wpa_state=ASSOCIATED address= Supplicant PAE state=HELD suppPortStatus=Unauthorized EAP state=FAILURE uuid=59fbef4f-this was using the wpa_supplicant in 2.7.0.
-
Sorry for reopen such an old thread.
I'm running 24.03 but my eap tls authentication always failed.My wpa_supplicant.conf is the same as the op (except the mac address)
I'm using the system build-in wpa_supplicant. -
I also tried 23.09.1 and got the same result.
wpa_cli status shows
wpa_state=associated
supplicant pae state=held
suppPortStatus=Unauthorized
EAP state=FAILURESame certificate set works on Mikrotik.
I've checked the identity mac address which are the same.Please help, it really drives me crazy
-
You are also trying to connect to AT&T?
-
@stephenw10 Yes, AT&T U-verse fiber. I confirm it's gpon not xgspon.
I also notice that the system has two wpa_supplicant. one is under /usr/sbin, the other under /usr/local/sbin. Both are version 2.10 and both failed the 1x authentication.
The system was originally running CE 2.7.2 and then upgrade to 23.09.1/24.03.
-
@henryzhou https://www.reddit.com/r/PFSENSE/comments/18jz0uc/installing_att_bypass_on_a_clean_install_of/
Follow the guide above. Additional settings are needed as pfsense 24.03 (and possibly earlier) uses openssl 3.0. Att's certs do not meet the minimum security standards so weaker ciphers must be allowed.