WPA_Supplicant
-
@GPz1100
Had time to mess with this last night. using this config.ctrl_interface=DIR=/var/run/wpa_supplicant
eapol_version=1
ap_scan=0
fast_reauth=1
network={
ca_cert="/root/WPA/Certs/CA.pem"
client_cert="/root/WPA/Certs/Client.pem"
eap=TLS..
eapol_flags=0
identity="XX:XX:XX:XX:XX:XX" # Internet (ONT) interface MAC address must match this value
key_mgmt=IEEE8021X
phase1="allow_canned_success=1"
private_key="/root/WPA/Certs/PrivateKey.pem"
}
Works perfectly on 23.05.1 but does not get an IP on 2.7.0. Im using the wpa_supplicant posted on the dslforum link.
At this point I'm about to give up. Now I just have to dercide if I want to pay for plus from here on out -
You tried using the included wpa_supplicant? 2.7 should have the patch to accept vlan0 by default.
-
@AiC0315 Where/when are you initializing wpa_supplicant?
-
@stephenw10
Yes, I used the wpa_supplicant file posted in the dslreports post -
@GPz1100
/sbin/ifconfig igb0 ether "XX:XX:XX:XX:XX:XX" && /root/WPA/wpa_supplicant -B -Dwired -i igb0 -c /root/WPA/wpa_supplicant.conf -P/var/run/wpa_supplicant.pid && sleep 10 && /usr/sbin/wpa_cli logon. (early shellcmd)wpa_cli logoff && sleep 10 && wpa_cli logon (shellcmd)
-
-
@GPz1100
Thanks,
I will take a look when I am able to install 2.7.0 back on my machine. -
@AiC0315 said in WPA_Supplicant:
Yes, I used the wpa_supplicant file posted in the dslreports post
Yes I meant did you try the default wpa_supplicant version that's included in 2.7?
-
@GPz1100 said in WPA_Supplicant:
@stephenw10 ^^I believe it was 23.09 that introduced the new openssl.
It's unclear why the OP was unsuccessful with 2.70, given it does include the vlan0 patched wpa_supplicant with the same wpa_supplicant.conf
@AiC0315 said in WPA_Supplicant:
Failed to connect to non-global ctrl_ifname: (nil) error: No such file or directory
This error suggests a missing conf parameter in wpa_supplicant.conf, specifically
ctrl_interface=DIR=/var/run/wpa_supplicantThis goes ABOVE the "network={" array.
What about
Failed to connect to non-global ctrl-ifname: (nil) error: Success
-
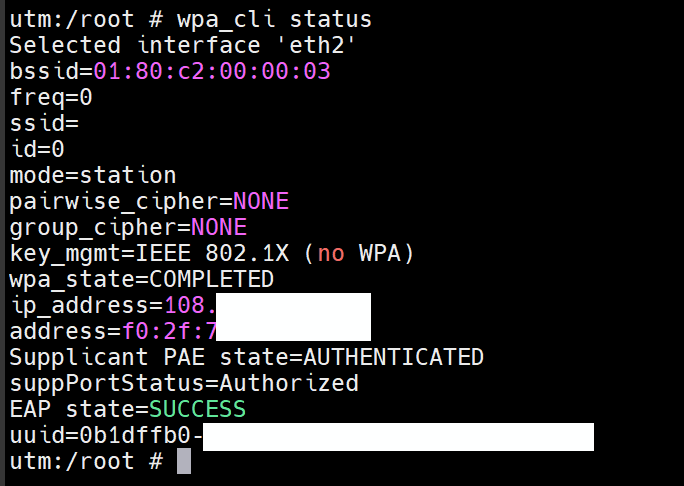
Here is the output of wpa_cli status:
Selected interface 'igb0' bssid=01:80:c2:00:00:03 freq=0 ssid= id=0 mode=station pairwise_cipher=NONE group_cipher=NONE key_mgmt=IEEE 802.1X (no WPA) wpa_state=ASSOCIATED address= Supplicant PAE state=HELD suppPortStatus=Unauthorized EAP state=FAILURE uuid=59fbef4f-this was using the wpa_supplicant in 2.7.0.
-
Sorry for reopen such an old thread.
I'm running 24.03 but my eap tls authentication always failed.My wpa_supplicant.conf is the same as the op (except the mac address)
I'm using the system build-in wpa_supplicant. -
I also tried 23.09.1 and got the same result.
wpa_cli status shows
wpa_state=associated
supplicant pae state=held
suppPortStatus=Unauthorized
EAP state=FAILURESame certificate set works on Mikrotik.
I've checked the identity mac address which are the same.Please help, it really drives me crazy
-
You are also trying to connect to AT&T?
-
@stephenw10 Yes, AT&T U-verse fiber. I confirm it's gpon not xgspon.
I also notice that the system has two wpa_supplicant. one is under /usr/sbin, the other under /usr/local/sbin. Both are version 2.10 and both failed the 1x authentication.
The system was originally running CE 2.7.2 and then upgrade to 23.09.1/24.03.
-
@henryzhou https://www.reddit.com/r/PFSENSE/comments/18jz0uc/installing_att_bypass_on_a_clean_install_of/
Follow the guide above. Additional settings are needed as pfsense 24.03 (and possibly earlier) uses openssl 3.0. Att's certs do not meet the minimum security standards so weaker ciphers must be allowed.
-
-
@GPz1100 Thank you so much.
After adding
openssl_ciphers=DEFAULT@SECLEVEL=0to my wpa_supplicant.conf and set OPENSSL_CONF to a customized config file it works.I do appreciate your help. All of you.
-
@stephenw10 said in WPA_Supplicant:
Nice!

Don't shoot the messenger :). Technically, these certs are for internal use. I suppose these could be updated via firmware, but like most things att, doing so will probably create more damage than it solves.
Eventually gpon/eapol may fade away in favor of xgs and newer technologies.
-
one more thing, does pfsense plus provide a better integration with wpa_supplicant (instead of shellcmd/earlyshellcmd)? I notice this doc https://docs.netgate.com/pfsense/en/latest/recipes/authbridge.html but it basically focuses on bridging the ATT router with pfsense.
-
@henryzhou Depends on your use case. Most of us want the att box out of the path entirely. The recipe does the equivalent mode of using netgraph in proxy mode.
Im making use of earlyshell/shell cmd as outlined in the reddit link. We experimented last June (2023) in the discord group with different variations and found that to work best. The info's a bit scattered; poster on reddit did a good job of organizing it all.
It's unclear if you're using an external ont or gone the full fiber--> sfp route. In either even the wpa portion remains the same, just the interfaces change slightly - depending on which stick you use. Some sticks (odi dfp-34x-2c2 or equiv) require passing of a specific vlan to the firewall, others handle all the vlan internally (fs.com/lantiq modules). The wpa part however remains bound to the parent interface, not the vlan.