So many config changes from WireGuard (and even more from pfBlocker if DNSBL is disabled)
-
@bmeeks said in So many config changes from WireGuard:
ot record a config backup unless some really important info was changed in the file.
Exactly - it doing an update of its current configuration list/alias, ie the entries is not a "configuration" change imho.. Now if I modified which lists its pulling from, or altered how often they are updated, sure ok yeah the "config" was altered.
But it going out every X hours to see if new IPs or an ASN or IPs have been added remove to a geo list is not a "config" change.. I am glad its not forcing an auto backup upload if that is the case, haven't looked into doing that.
I don't normally use the config restore feature, etc. but I was really just looking into it for some thread.. And I was like well thats pretty useless all that was listed was pfblocker changes.. So I updated the list to be much longer so I could go back a few days even if filled up with the pfblocker nonsense.
-
Yeah, I think my IDS/IPS package is recording the status (success or failure) of the last rules update and a timestamp. That is not worthy of a config backup. I used it to display that info on a PHP tab, but it does not warrant a config backup. Probably some other similar things in my two packages as well.
Now, if an admin changes things such as adds a new rule category, force disables or enables some particular rule or rules, or changes a parameter setting, then that is worthy of a full config backup.
I have created an internal tracker for me to address this in the next package update.
I can't speak for pfBlockerNG and other packages, but likely similar scenarios exist where some changes are not worth generating a config backup for.
-
@johnpoz said in So many config changes from WireGuard:
I don't normally use the config restore feature, etc. but I was really just looking into it for some thread.. And I was like well thats pretty useless all that was listed was pfblocker changes.. So I updated the list to be much longer so I could go back a few days even if filled up with the pfblocker nonsense.
That is not the list I was showing or is it? Because mine doesn't contain pfBlockerNG and I let that update itself every hour.
-
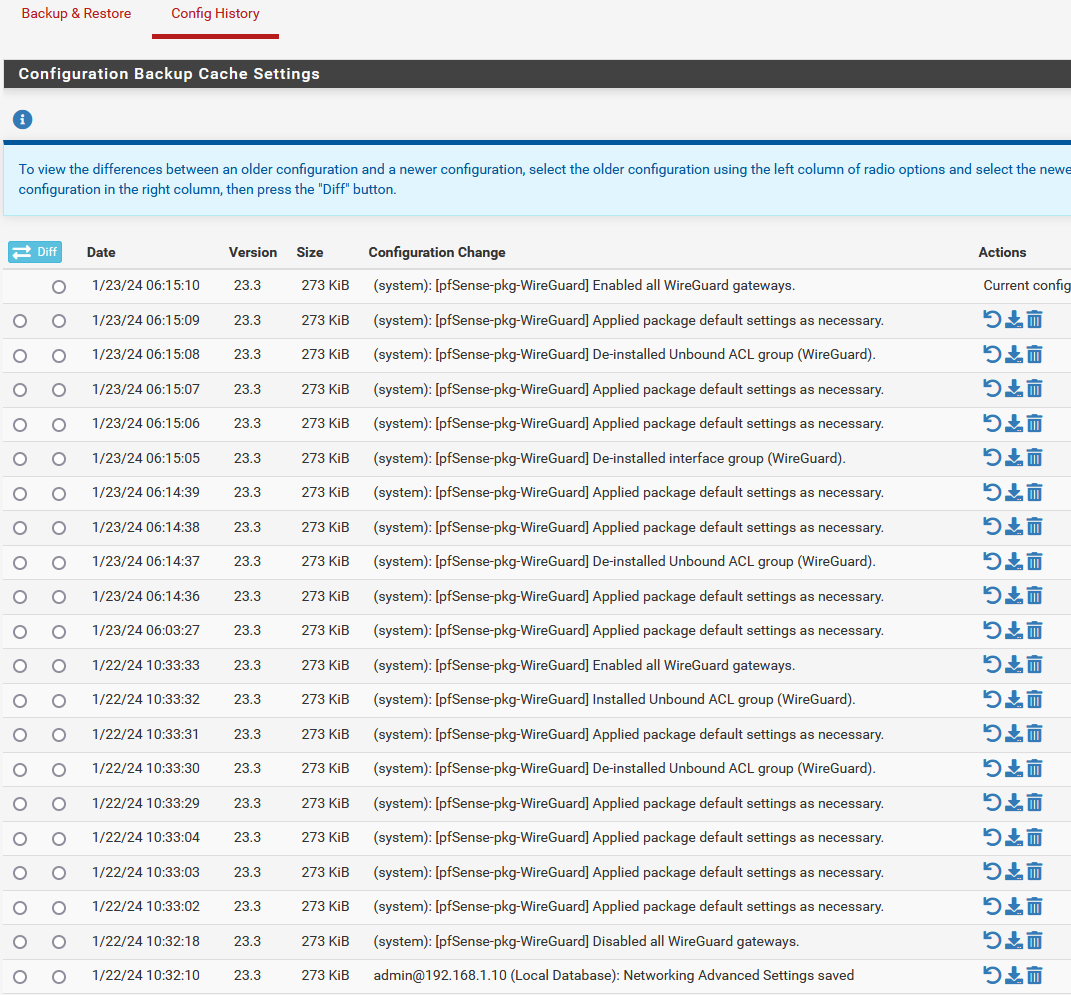
@Bob-Dig option 15 from the menu from console/ssh or config history in the menu..
I haven't touched pfblocker in days, but you can see its taking up a slot in the config history
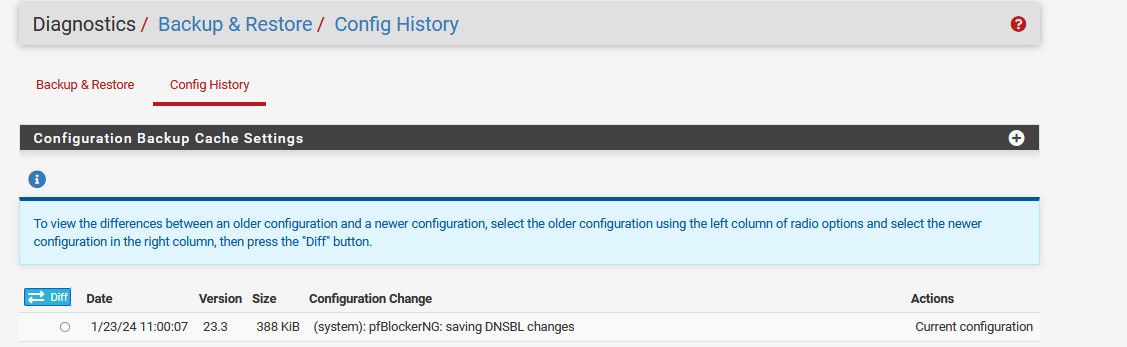
But its not listed in the ACB
-
@johnpoz said in So many config changes from WireGuard:
@Bob-Dig option 15 from the menu from console/ssh or config history in the menu..
It is not listed there for me either. I only see that problem with WireGuard.
-
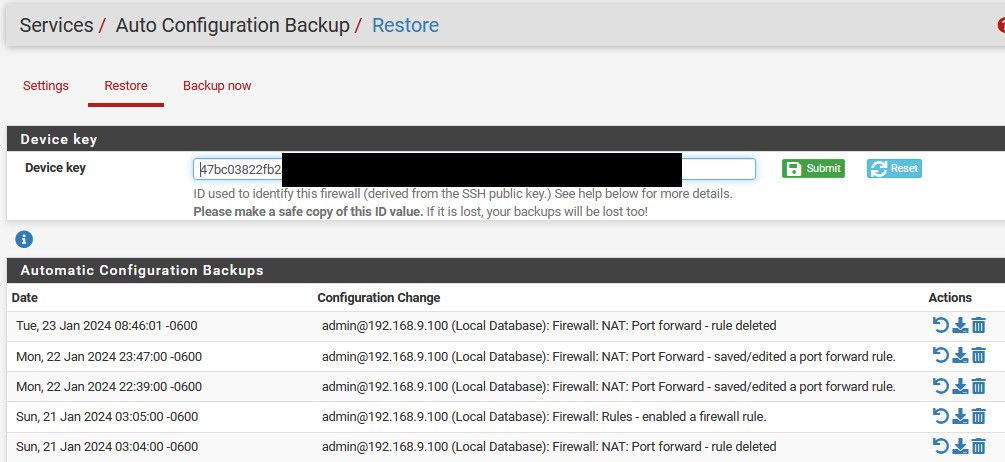
@Bob-Dig I would love to know how to stop it.. If you look at a diff, there isn't any listed other than the description
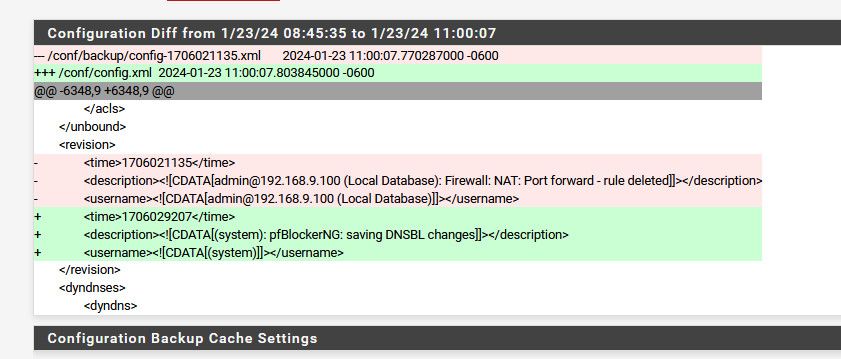
Are you on + or CE?
I don't have wireguard installed, I have tailscale installed.
Not meaning to hijack your thread, but seems related to me - stuff being added to config history, that really shouldn't be imho.
-
@johnpoz said in So many config changes from WireGuard:
@Bob-Dig I would love to know how to stop it..
I am on plus with this machine.
Do the settings play a role here under DiagnosticsBackup & Restore?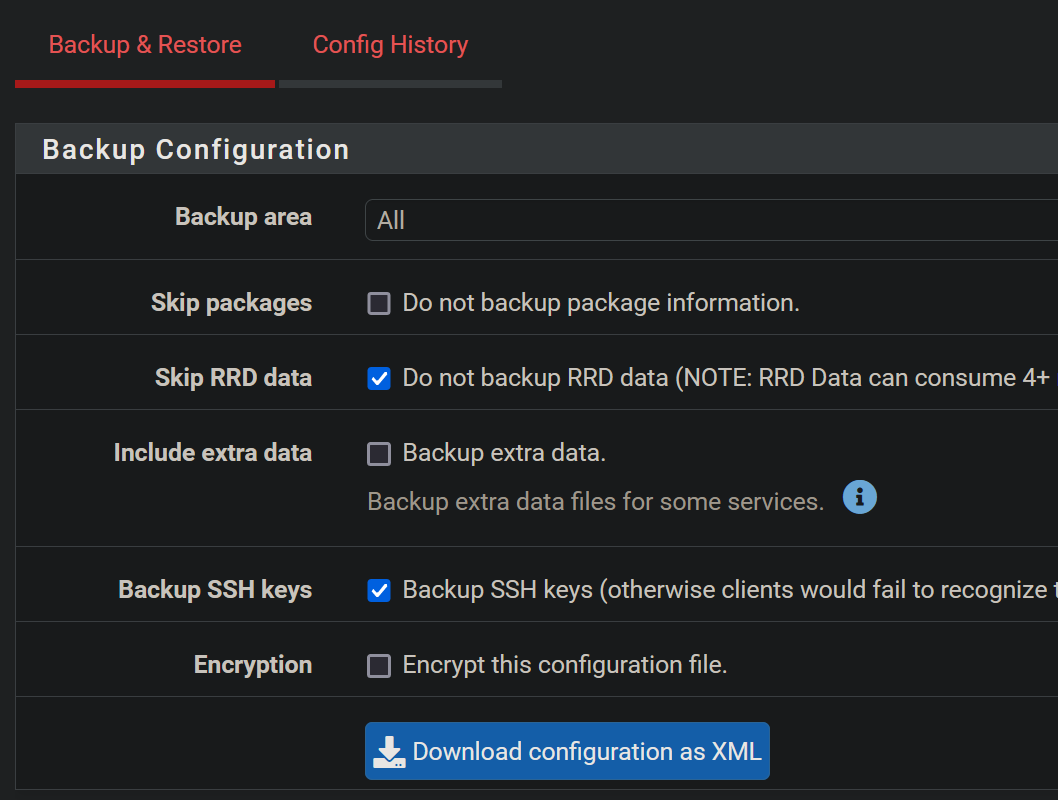
-
@johnpoz said in So many config changes from WireGuard:
I don't have wireguard installed, I have tailscale installed.
Becoming lazy, don't want to open a port?

-
@Bob-Dig while I have a port open for tailscale - I thought I was reading somewhere recently that someone has tailscale working without opening that port.. tailscale is not my go to vpn solution. I use openvpn for day to day remote access.. Which is way less than it use to be now that just full time work from home ;)
As to the backup/config settings - I don't see anything there that would have an effect on the pfblocker stuff
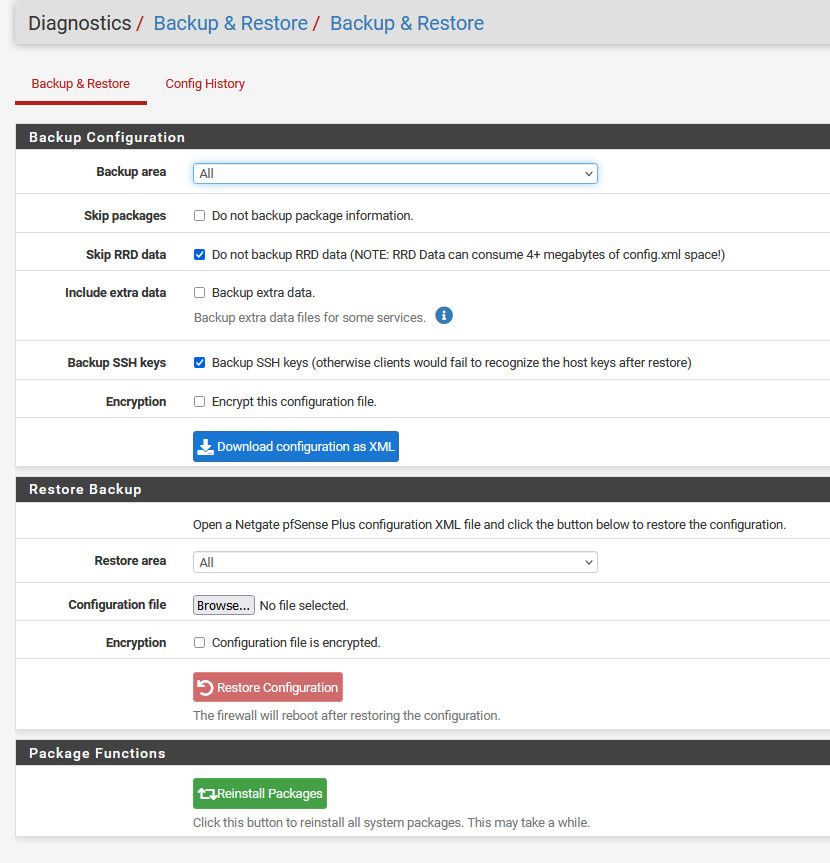
-
@johnpoz said in So many config changes from WireGuard:
I would love to know how to stop it.
Currently the only way would be to manually edit the PHP code of the pfBlockerNG GUI and add the additional arguments to calls to the
write_config()function that I copied in my earlier post. That would require knowledge of the code paths in the package or some study to figure them out. -
Do you actually have DNS-BL enabled?
Maybe: https://redmine.pfsense.org/issues/14409
I do have DNS-BL enabled and don't see config backups for it.
-
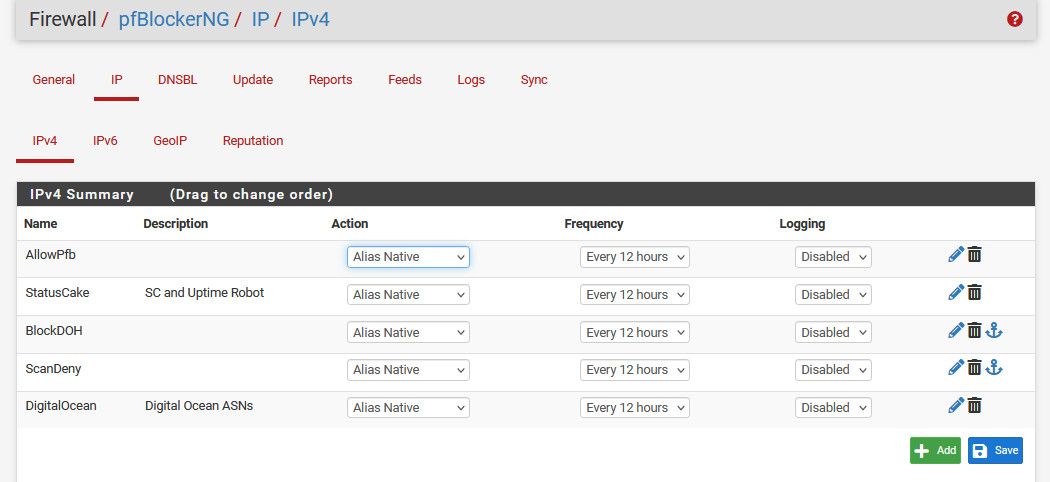
@stephenw10 no I do not actually have dns-bl enabled. I just use pfblocker to create native aliases that I use in my firewall rules.
here is what I am using pfblocker for
-
@johnpoz I use both.
-
@Bob-Dig I wonder if I just enabled dns-bl, without actually using it would get rid of the config entries?
-
@johnpoz said in So many config changes from WireGuard:
@Bob-Dig I wonder if I just enabled dns-bl, without actually using it would get rid of the config entries?
Sounds like a plan.
-
@Bob-Dig yup have it enabled now, just not doing anything.. So check back tmrw to see if those config entries are in there..
-
@johnpoz Do you have anything in DNSBL Groups enabled or the other tabs?
Still wouldn't make any sense. -
@Bob-Dig nope have never setup dns-bl, have no use for it. Have never had it enabled ever..
-
@johnpoz I think one ad list is included by installation there, maybe removing it does something; or not.

-
@Bob-Dig I looked I have nothing selected.. Ah, this is set by default for top 1M whitelist
Default: COM, NET, ORG, CA, CO, IO
But can not unselect them.. if you do and then hit save, and then go back into it.. They are selected again, but this is not even enabled.
I have no groups listed
No categories selected, nothing in safesearch, its not enabled.. I don't use dns-bl, my clients use pihole on my network for this sort of thing.. The only thing I use pfblocker for is creating aliases I use in my own firewall rules.