Massive performance drop after upgrade from 23.05 to 23.09
-
@stephenw10 said in Massive performance drop after upgrade from 23.05 to 23.09:
Try running top with:
top -HaSPto show the per core usage.I'm happy to do that if I can help narrow down the problem.
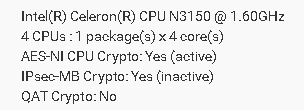
yes QAT is activated
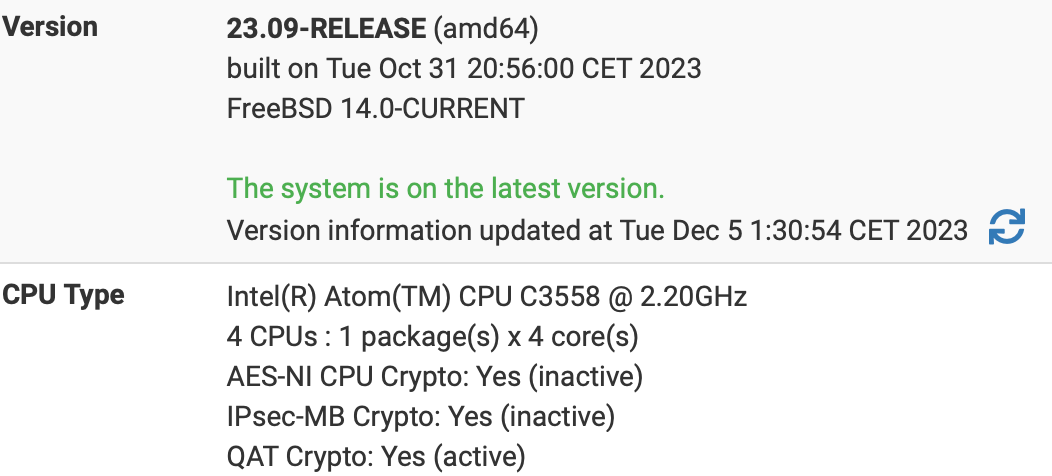
-
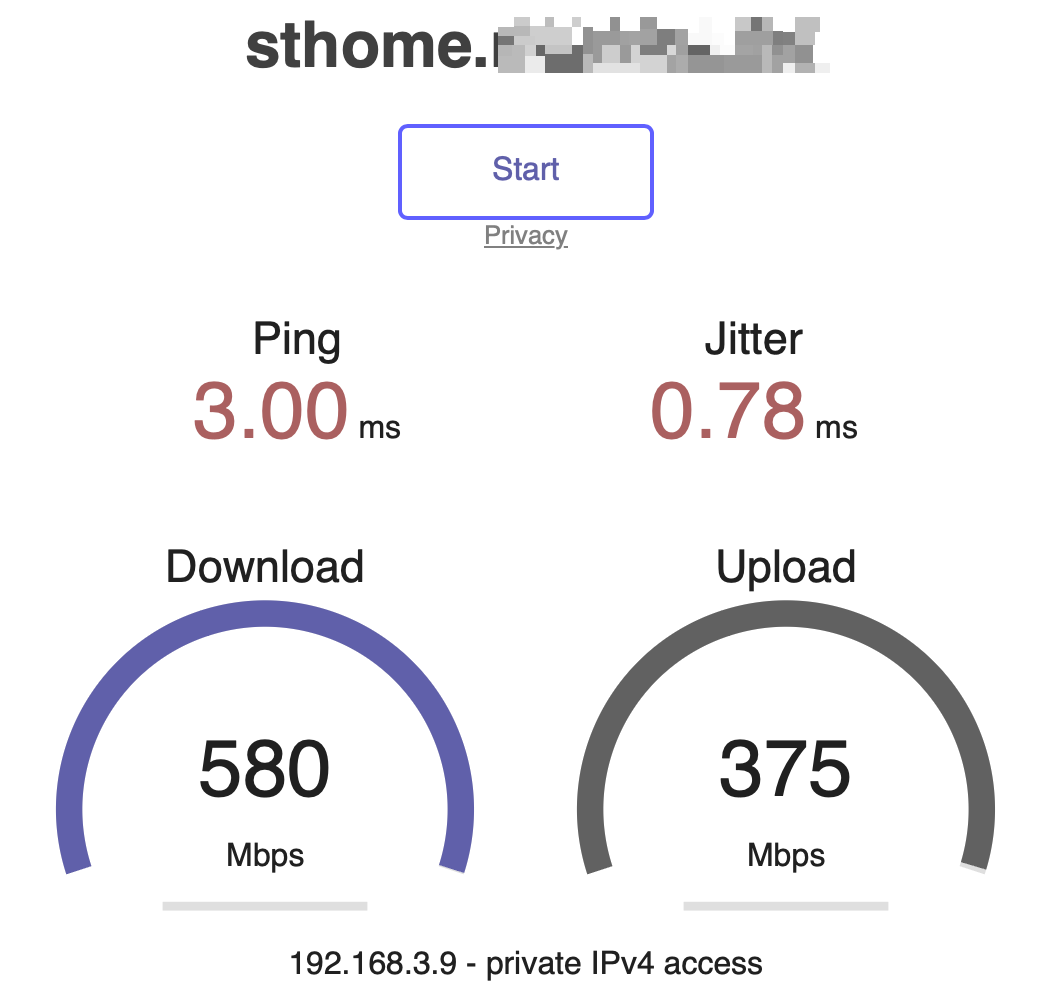
I have now tested 23.09.1. the values are slightly better. But I would have thought it would be more (I have no comparison with the netgate 6100) I now have 60MByte/s in the download.
[23.09.1-RELEASE][admin@fw1.in.xxx.de]/root: openssl speed -elapsed -evp aes-256-gcm You have chosen to measure elapsed time instead of user CPU time. Doing AES-256-GCM for 3s on 16 size blocks: 25549143 AES-256-GCM's in 3.02s Doing AES-256-GCM for 3s on 64 size blocks: 18785835 AES-256-GCM's in 3.02s Doing AES-256-GCM for 3s on 256 size blocks: 7343485 AES-256-GCM's in 3.04s Doing AES-256-GCM for 3s on 1024 size blocks: 2143908 AES-256-GCM's in 3.01s Doing AES-256-GCM for 3s on 8192 size blocks: 281723 AES-256-GCM's in 3.03s Doing AES-256-GCM for 3s on 16384 size blocks: 141599 AES-256-GCM's in 3.03s version: 3.0.12 built on: reproducible build, date unspecified options: bn(64,64) compiler: clang CPUINFO: OPENSSL_ia32cap=0x4ff8e3bfefebffff:0x2294e283 The 'numbers' are in 1000s of bytes per second processed. type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes AES-256-GCM 135556.07k 398687.98k 618589.50k 729886.52k 761360.76k 765346.97k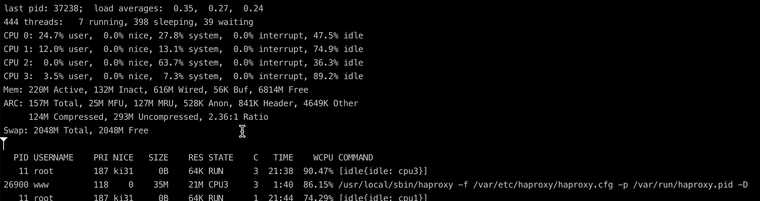
-
You should openssl speed back at essentially the 23.05.1 speeds.
Had you never tested that in 23.05.1?
-
@stephenw10 I can't say, I always only had 23.09 on the netgate 6100
-
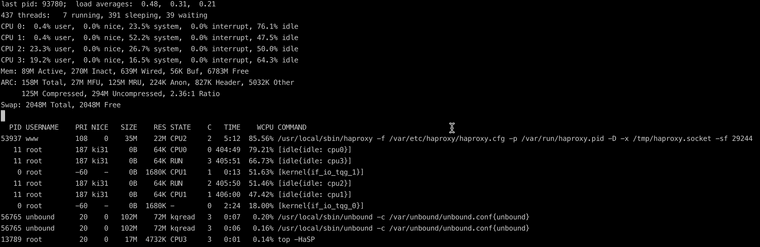
Do you still see HAProxy using close to 100% of one CPU core?
Is that speedtest actually using multiple streams?
-
@stephenw10 As you can see in the screenshot, the cpu is very busy https://forum.netgate.com/assets/uploads/files/1702051796330-scr-20231208-oypq.png. I can't say anything about the second question, I didn't develop it. I just use it.
-
Hi,
i can confirm that with 23.09.1 AES-NI Acceleration is back. For me this was a massive Performance drop in OpenVPN with 23.09 which is now fixed with 23.09.1.
23.05.1
root: openssl speed -elapsed -evp aes-256-gcm You have chosen to measure elapsed time instead of user CPU time. Doing aes-256-gcm for 3s on 16 size blocks: 15066311 aes-256-gcm's in 3.00s Doing aes-256-gcm for 3s on 64 size blocks: 7855959 aes-256-gcm's in 3.01s Doing aes-256-gcm for 3s on 256 size blocks: 2719459 aes-256-gcm's in 3.00s Doing aes-256-gcm for 3s on 1024 size blocks: 756518 aes-256-gcm's in 3.00s Doing aes-256-gcm for 3s on 8192 size blocks: 97459 aes-256-gcm's in 3.00s Doing aes-256-gcm for 3s on 16384 size blocks: 48892 aes-256-gcm's in 3.01s OpenSSL 1.1.1t-freebsd 7 Feb 2023 built on: reproducible build, date unspecified options:bn(64,64) rc4(16x,int) des(int) aes(partial) idea(int) blowfish(ptr) compiler: clang The 'numbers' are in 1000s of bytes per second processed. type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes aes-256-gcm 80353.66k 167158.48k 232060.50k 258224.81k 266128.04k 266321.96k23.09
You have chosen to measure elapsed time instead of user CPU time. Doing AES-256-GCM for 3s on 16 size blocks: 5880314 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 64 size blocks: 1862428 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 256 size blocks: 493665 AES-256-GCM's in 3.01s Doing AES-256-GCM for 3s on 1024 size blocks: 125115 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 8192 size blocks: 15699 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 16384 size blocks: 7843 AES-256-GCM's in 3.00s version: 3.0.12 built on: reproducible build, date unspecified options: bn(64,64) compiler: clang CPUINFO: OPENSSL_ia32cap=0x43d8e3bfefebffff:0x2282 The 'numbers' are in 1000s of bytes per second processed. type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes AES-256-GCM 31361.67k 39731.80k 42016.66k 42705.92k 42868.74k 42833.24k23.09.1
You have chosen to measure elapsed time instead of user CPU time. Doing AES-256-GCM for 3s on 16 size blocks: 15367274 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 64 size blocks: 7672483 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 256 size blocks: 2691809 AES-256-GCM's in 3.01s Doing AES-256-GCM for 3s on 1024 size blocks: 754613 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 8192 size blocks: 97312 AES-256-GCM's in 3.00s Doing AES-256-GCM for 3s on 16384 size blocks: 48977 AES-256-GCM's in 3.01s version: 3.0.12 built on: reproducible build, date unspecified options: bn(64,64) compiler: clang CPUINFO: OPENSSL_ia32cap=0x43d8e3bfefebffff:0x2282 The 'numbers' are in 1000s of bytes per second processed. type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes AES-256-GCM 81958.79k 163679.64k 229104.41k 257574.57k 265726.63k 266784.97kThis is with enabled AES-NI CPU Acceleration
-
Issue is resovled for me on 23.09.1, thx to whom ever fixed it.
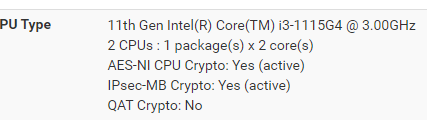
You have chosen to measure elapsed time instead of user CPU time.
Doing AES-256-GCM for 3s on 16 size blocks: 126245097 AES-256-GCM's in 3.00s
Doing AES-256-GCM for 3s on 64 size blocks: 75396240 AES-256-GCM's in 3.00s
Doing AES-256-GCM for 3s on 256 size blocks: 41552001 AES-256-GCM's in 3.01s
Doing AES-256-GCM for 3s on 1024 size blocks: 15179553 AES-256-GCM's in 3.00s
Doing AES-256-GCM for 3s on 8192 size blocks: 2251028 AES-256-GCM's in 3.02s
Doing AES-256-GCM for 3s on 16384 size blocks: 1139204 AES-256-GCM's in 3.09s
version: 3.0.12
built on: reproducible build, date unspecified
options: bn(64,64)
compiler: clang
CPUINFO: OPENSSL_ia32cap=0xfffab2234f8bffff:0x18405f5ef1bf07ab
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
AES-256-GCM 673307.18k 1608453.12k 3536560.96k 5181287.42k 6099157.46k 6033040.27kStill not line speed, but back to the level it was on 23.05.01
-
@micneu said in Massive performance drop after upgrade from 23.05 to 23.09:
I have now tested 23.09.1. the values are slightly better. But I would have thought it would be more (I have no comparison with the netgate 6100) I now have 60MByte/s in the download.

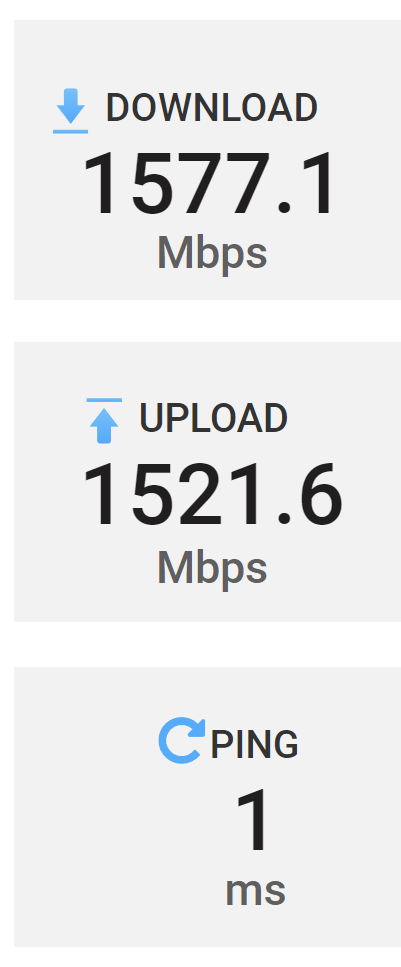
Please, what the software You use for this testing (the picture looks like Speedtest from Fast.com”)?
-
@sunny1081 said in Massive performance drop after upgrade from 23.05 to 23.09:
Issue is resovled for me on 23.09.1, thx to whom ever fixed it.


You have chosen to measure elapsed time instead of user CPU time.
Still not line speed, but back to the level it was on 23.05.01
Please, what exactly software You are using for this test? (on picture)
-
Do you restrict the number of states allowed on some connections? I noticed once I said for example 1 state allowed at a time for GUI it start to speed up a lot. Some I added expire timers on like my VPNs etc.
ACL for the HA proxy system should only have how many states??? Maybe just one as it is linked to the other proxy.
I don't know if that helps, but some cookies kept creating multiple states for some weird reason and slowing everything down. But that was just me this fixed it for me with KEA use also.