Access Modem GUI Behind Firewall
-
@Globaltrader312 yeah sometimes you don't need an IP or nat. My old modem use to answer with no need for a different interface IP on the 192.168.100 network.. It would intercept the traffic sent out the wan because it was to 192.168.100.1 and send the answer back to the source IP which was just my public IP.
But even if that was the case, natting to an IP that is on the network you want to talk to isn't going to break anything.. But you seemed confused on where you want to set it and what rules you need..
if your vigor interface bge1 is connected to the vigor device, and this device has an IP of 192.168.5.1 and you put an IP of 192.168.5.x on your bge1 interface.. Pfsense knows how to get there.. You need to nat it because its quite possible if your source is say 192.168.1.x the vigor devices isn't going to send the answer back to your 192.168.5.2 IP.
You don't seem able or willing to follow simple instructions or provide info asked for.. Why in the world would you create an any any rule on your wan2 for trying to talk to something connected to bge1 interface?? Just at a complete loss..
This takes all of 2 seconds to validate you your setup.. Sniff on bge1 - does pfsense send the traffic out this interface? Does it nat to your 192.168.5.x address. If it is not - then you got something wrong in what you setup in pfsense.. Its just that simple..
This is step one - because if your not sending traffic out your bge1 interface - how do you expect to talk to an IP on the other end of the wire you have connected to bge1?
Set up a static route, under System / Routing / Static Routes... create one with :
You do not need a route.. If pfsense has an interface connected to network X.. Why would it send traffic out any other gateway be it default or not when it has an interface attached to that network?
Unless you had a specific route, to this 192.168.5.X address it would always pick the interface it has in network 192.168.5.x
Viewing the routing table in pfsense could be helpful info.. But there is zero reason to create a route, unless he has created a route with a better route for 192.168.5 out some other interface.
Here is my routes - why would it send traffic out the default for any of the networks its directly attached too?
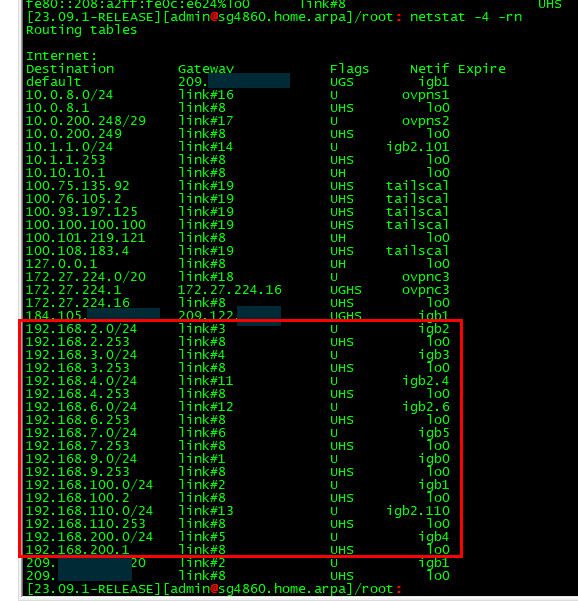
See the route for 192.168.100.0/24 - that is the network its attached to via the VIP I created on mine, etc..
If he is sending the traffic out some other interface because of policy routing then no its never going to work.. But create a route isn't going to fix his policy routing rule that would be sending traffic out the wrong gateway... He just needs a rule above his policy route that allows the traffic and uses pfsense normal routing..
-
sorry the answers always come a little late
so I have deleted the static route again.
then i checked the routing tbale once see screen shot interface and IP are visible.
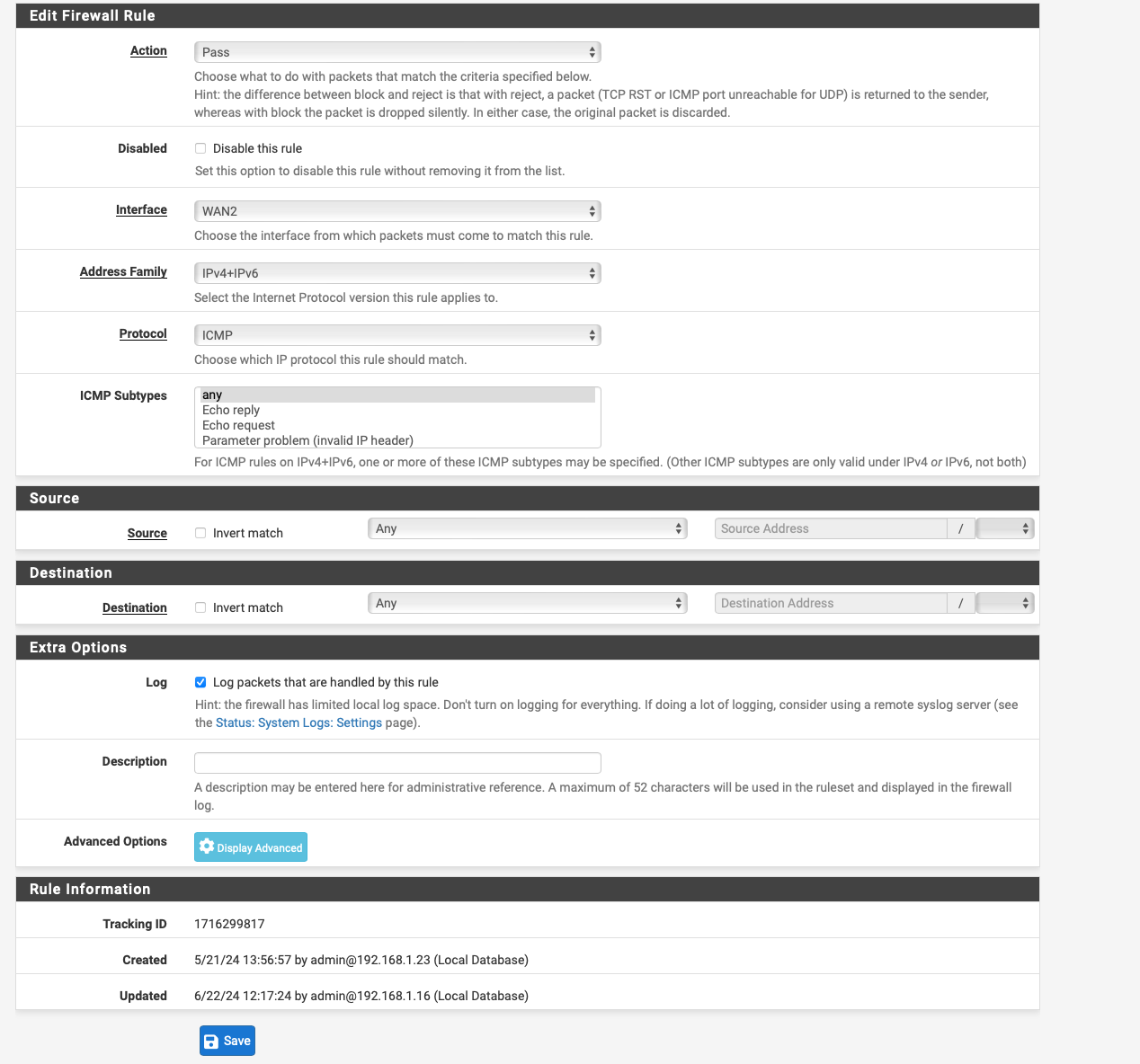
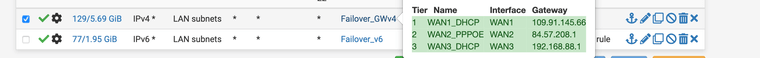
I created these any to any in the firewall for the lan rules for IPV4 and IPv6 according to the instructions for the failover setup erv, otherwise I created them separately.
I have selected the failover gateway in the dropdown under advanced in the lan rules I think the firewall will send everything over it can it be because of that ? see screen shot....
I would like to do your steps I'm just stuck at the point where I write I should create a rule about the Policy Based rules which exactly only the outbound nat I have or another ?
I will do the sniff and then send the info.
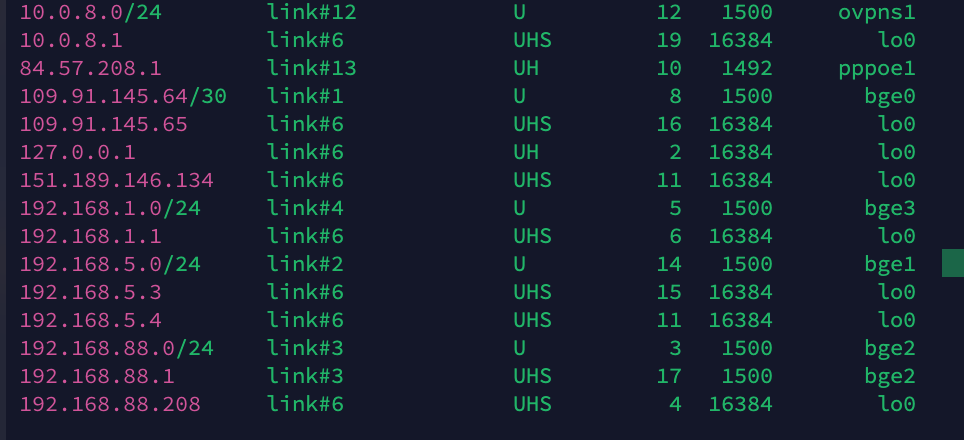
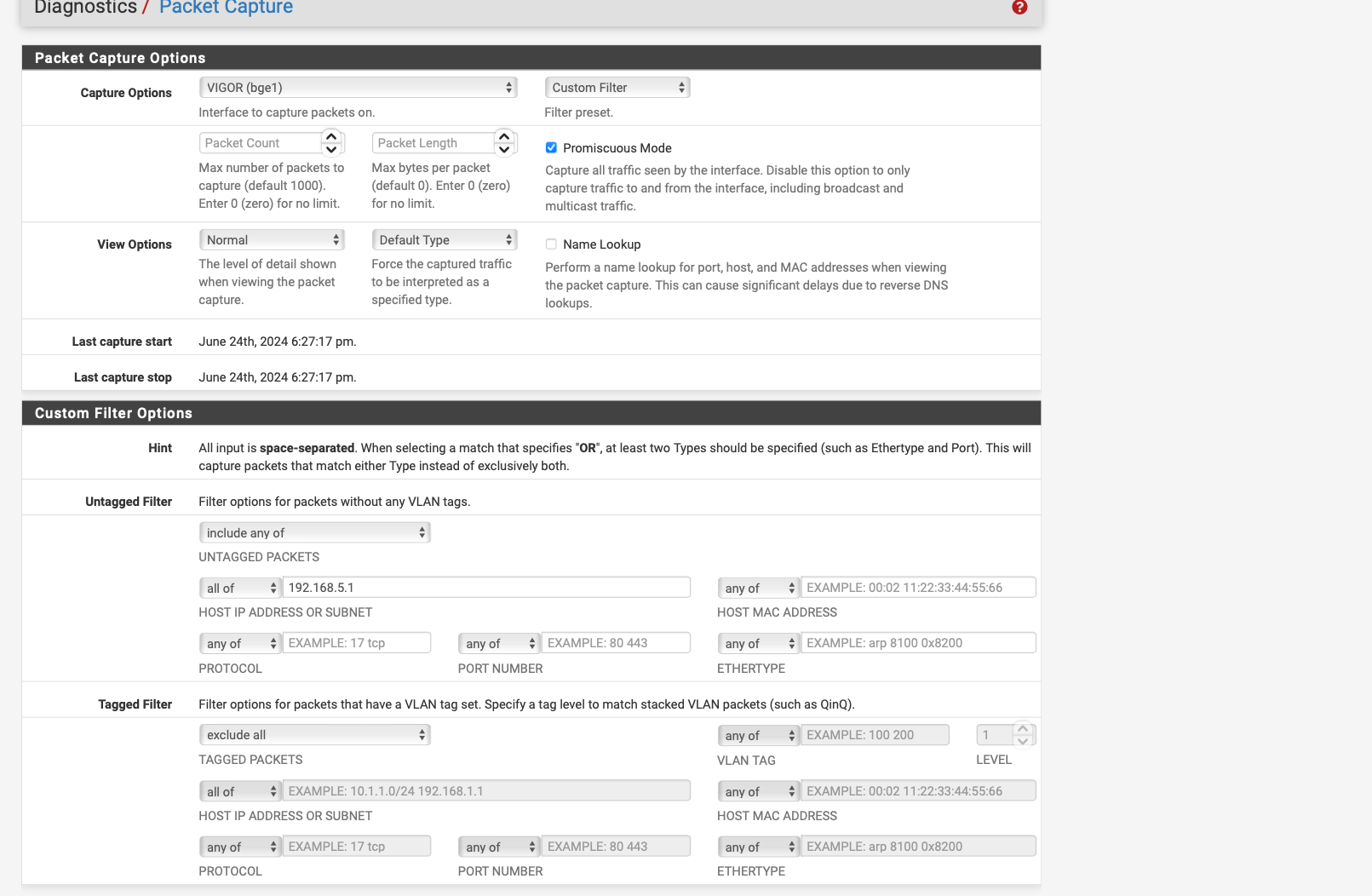
 no traffic comes through when I check with packet capture on interface Vigor BGE 1
no traffic comes through when I check with packet capture on interface Vigor BGE 1 -
@johnpoz said in Access Modem GUI Behind Firewall:
Set up a static route, under System / Routing / Static Routes... create one with :
You do not need a route.. If pfsense has an interface connected to network X.. Why would it send traffic out any other gateway be it default or not when it has an interface attached to that network?
Unless you had a specific route, to this 192.168.5.X address it would always pick the interface it has in network 192.168.5.x
Viewing the routing table in pfsense could be helpful info.. But there is zero reason to create a route, unless he has created a route with a better route for 192.168.5 out some other interface.
If he is sending the traffic out some other interface because of policy routing then no its never going to work.. But create a route isn't going to fix his policy routing rule that would be sending traffic out the wrong gateway... He just needs a rule above his policy route that allows the traffic and uses pfsense normal routing..
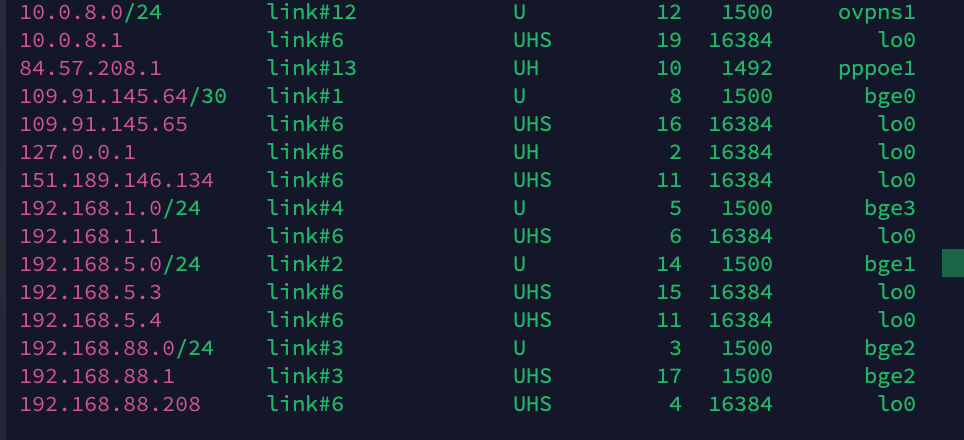
No you are of course absolutely right, his routing table clearly shows 192.168.5.0/24 as well, and I find it strange that it wouldn't "just work". Very confusing all of it though... and if there is some policy rule as well, I missed that...
A question though... will pfsense process send a request to an unknown IP via the WAN, even if it belongs to an RFC 1918 range? I guess I was thinking it would just drop it?
-
@Gblenn said in Access Modem GUI Behind Firewall:
and I find it strange that it wouldn't "just work".
because as you can see by his lan rules - he is policy routing.. Which has been brought up multiple times already.. He needs a rule to allows the normal routing to work..
Here
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
-
@johnpoz I apologise for asking this question.
I have looked at the instructions, unfortunately I do not understand one point in the instructions it says to create an alias for RFC1918 and in the picture it can also be seen that RFC1918 was set as destination.
but when i want to create a new rule, the destination RF1918 is displayed as invalid IP so i don't quite understand how i can set this i can only set an IP subnet e.g. 192.168.0.0/16
-
@Globaltrader312 Huh.. You don't need to create such an alias you could just put in 192.168.0.0/16 cidr in the rule.. Or just your 192.168.5.1/32 or 192.168.5.0/24
But creating an alias for all rfc1918 space would be done in the alias section
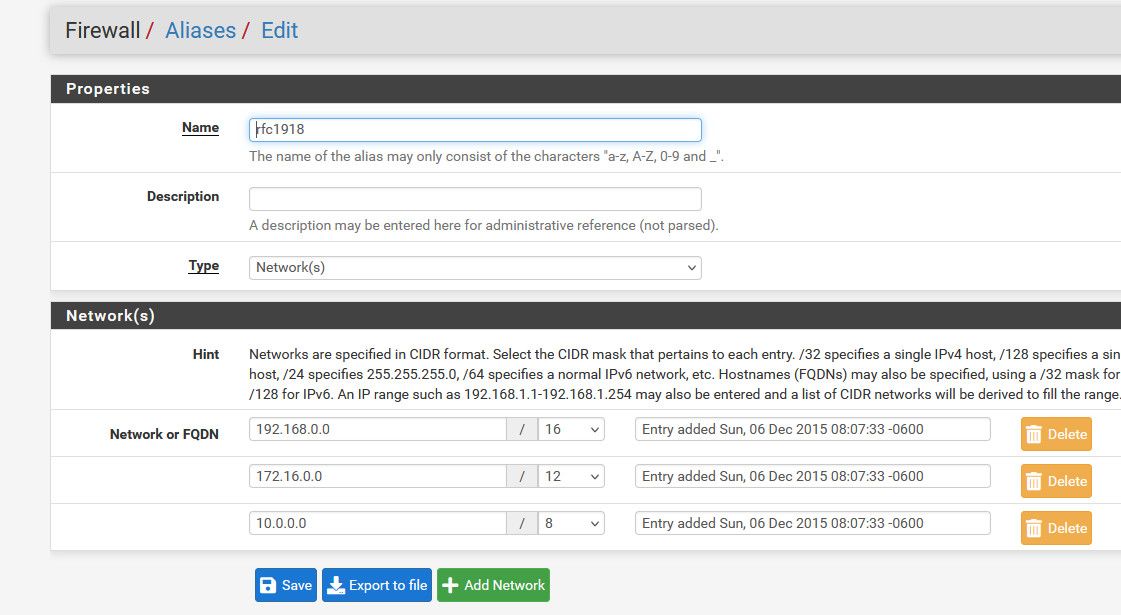
Here would be an example of using it in rule - this isn't a rule like you need but just an example of using the alias in a firewall rule
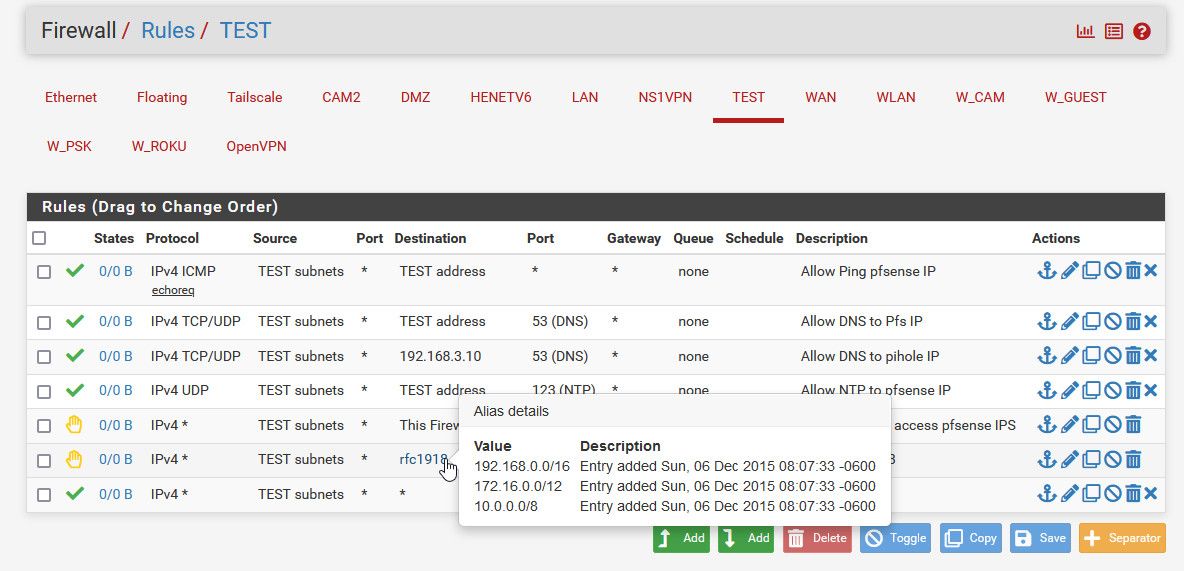
-
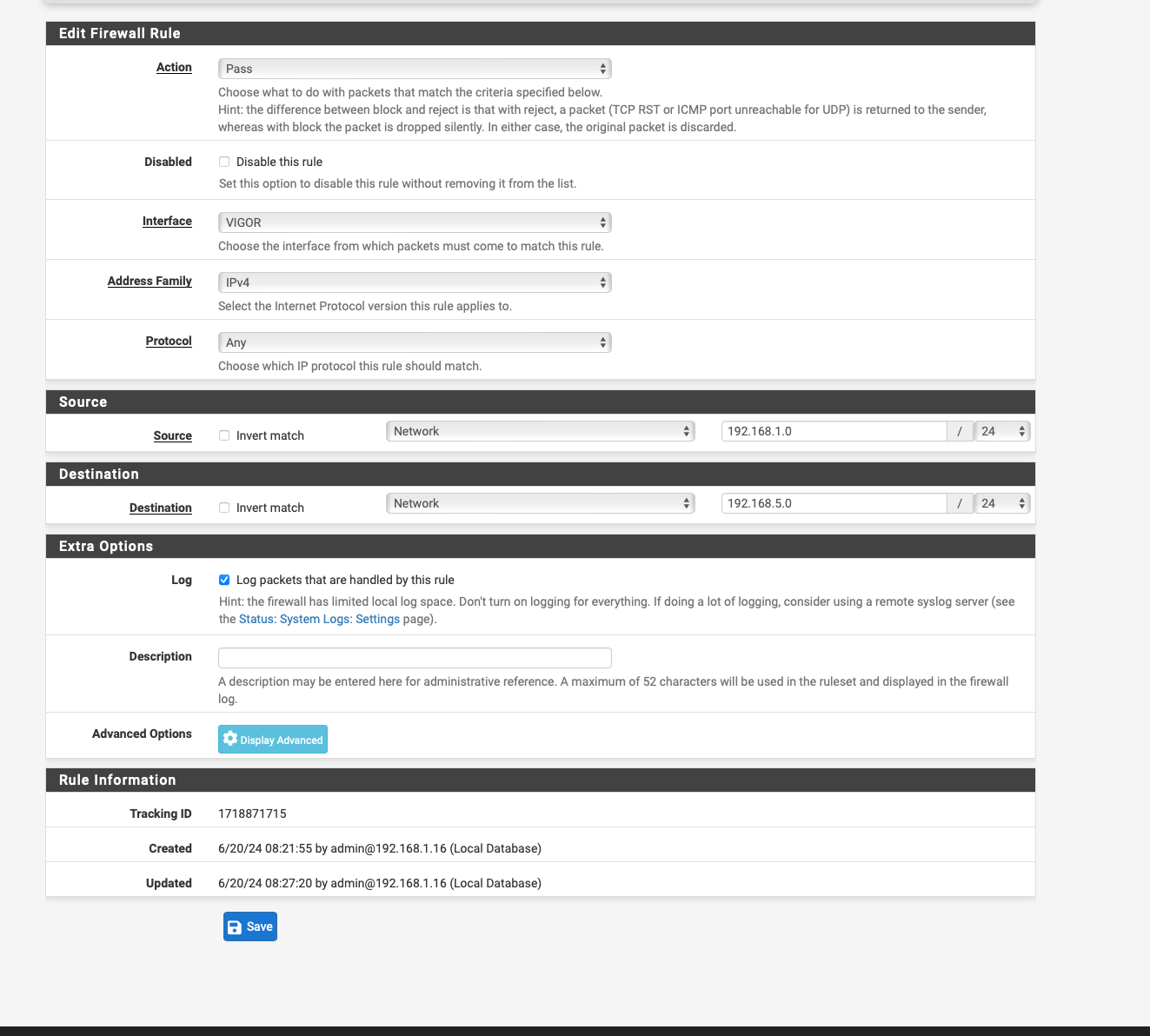
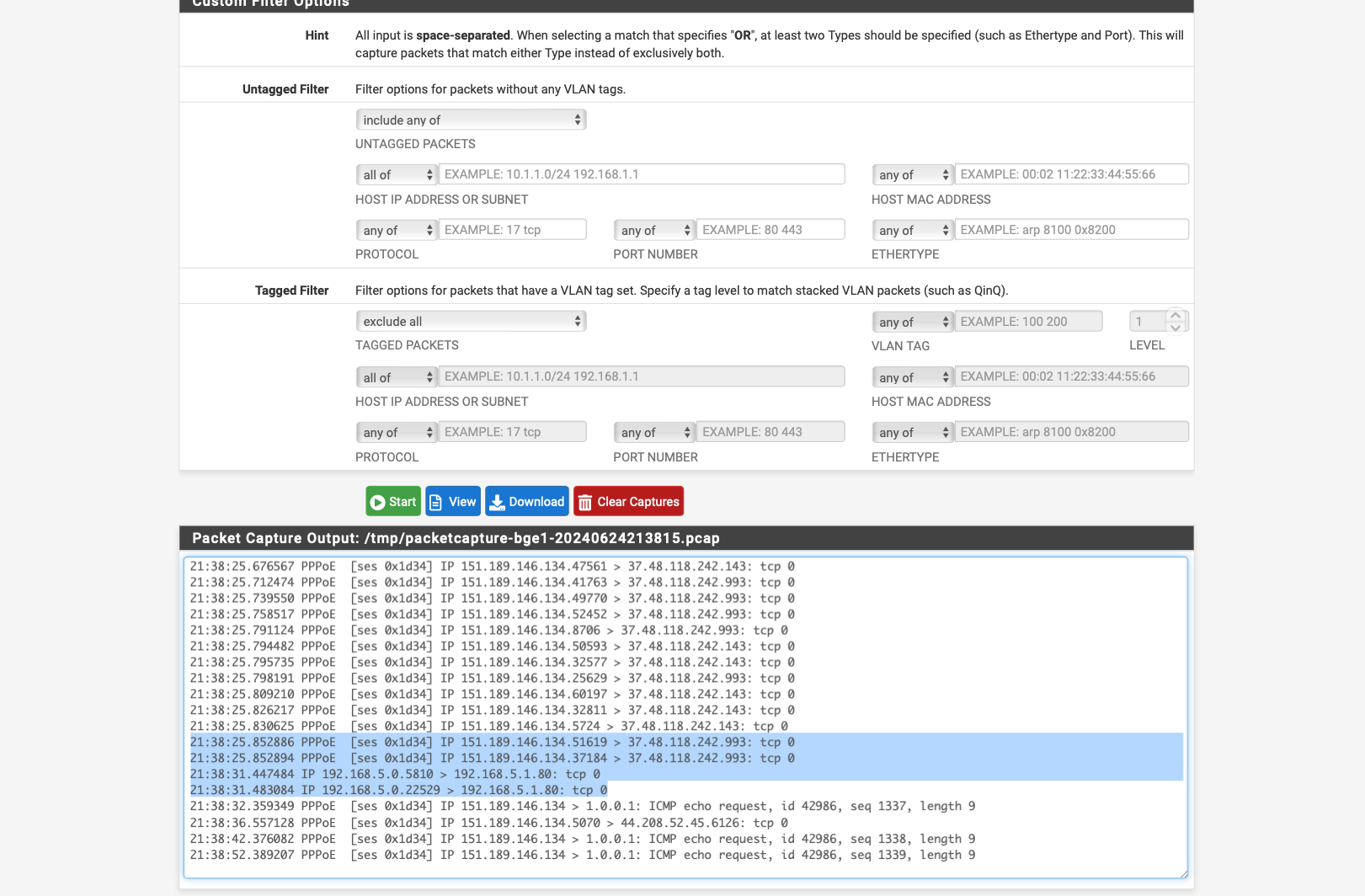
I have now created the rule via the Policy Based Rules and traffic is also flowing see screen shot and packet capture
but the GUI of the Vigor is still not accessible.
can it be that I still have to enter the changed ports from vigor in the firewall 8080 and 444 which I changed because of an advice from another user a few posts before.
-
@Globaltrader312 well if your device is not listening on port 80 any more, and you try and talk to port 80 which is what your sniff shows - then yeah its not going to answer. Either change its port back to 80, or talk to it on port whatever you changed it too
http://192.168.5.1:port
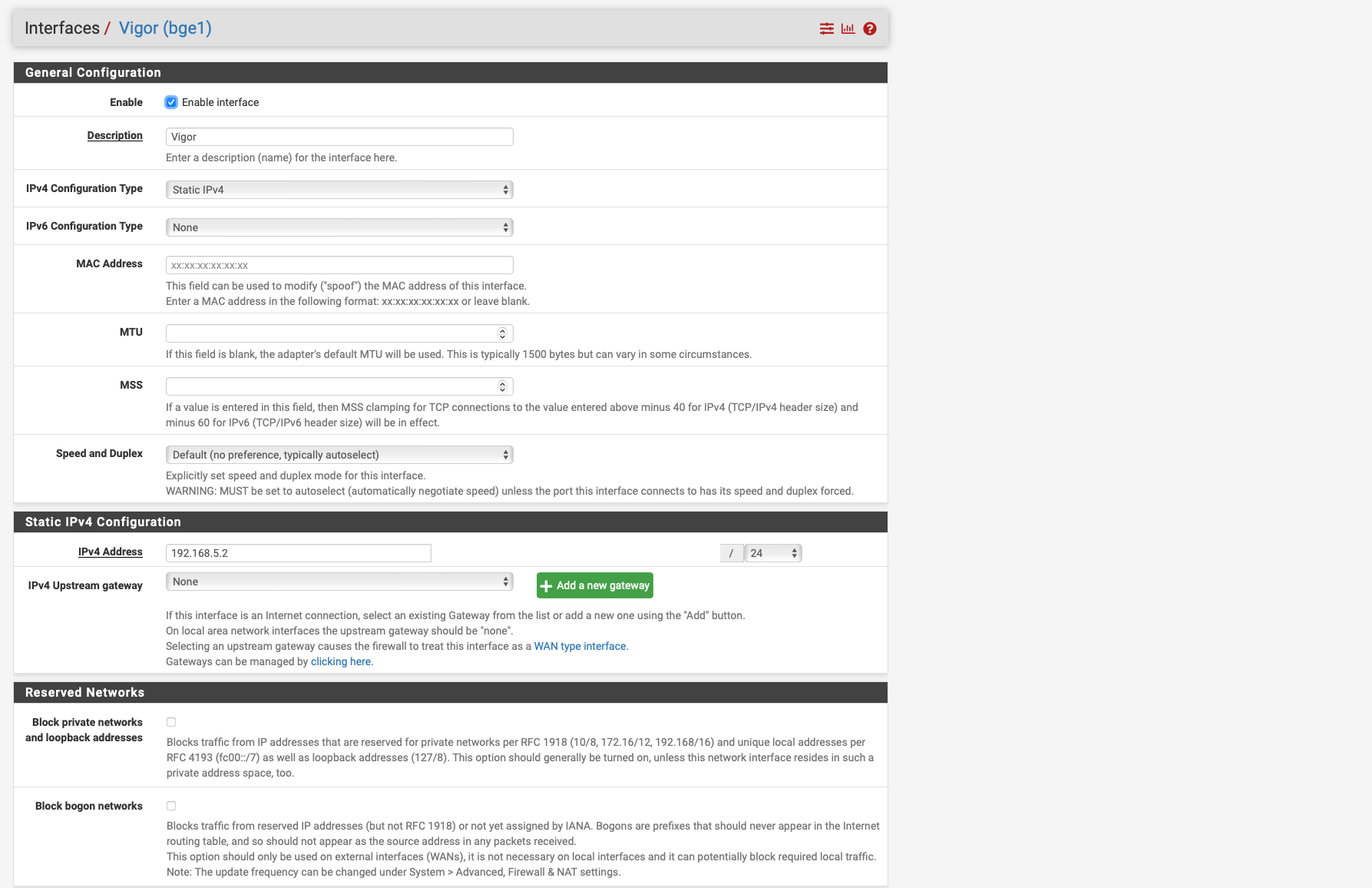
But your sniff shows 192.168.5.0 -- that is not really a valid IP address using a /24 mask.. I thought you set your pfsense interface to be .2 and or .3 why would it be using .0??
-
so i have now set the ports back to 80 and 443 it still does not work unfortunately
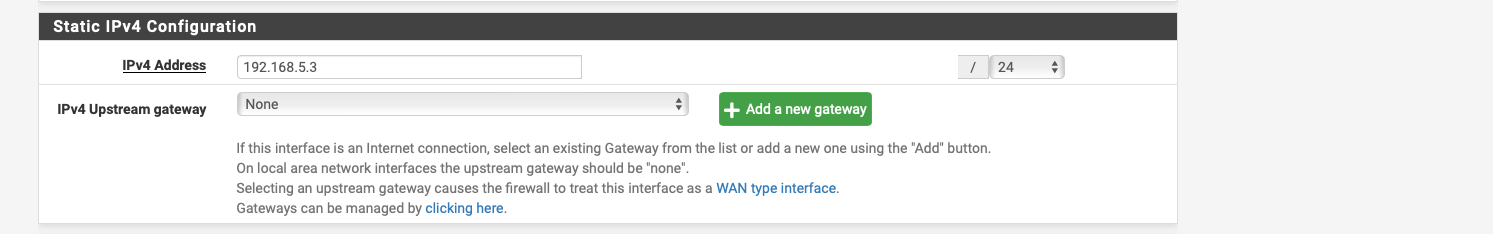
the 192.168.5.0/24 is because when I set Vigor to /32 under interfcaes no packets get through.
if i set it to /24 then packets go through at 192.168.5 but it says 192.168.5.0 / 24.
-
@Globaltrader312 no idea what your talking about?
Your address there is 192.168.5.3, why would pfsense change the address it sends from to .0??? That doesn't happen
The mask of /24 means this
The Wire or network is .0, the host address on this /24 network is .1 to .254, the broadcast address is .255
What you show there is correct, the interface address would be .3, there is no scenario that I can think of where pfsense would jsut on its own change that to .0 as its source address when natting to that interface.
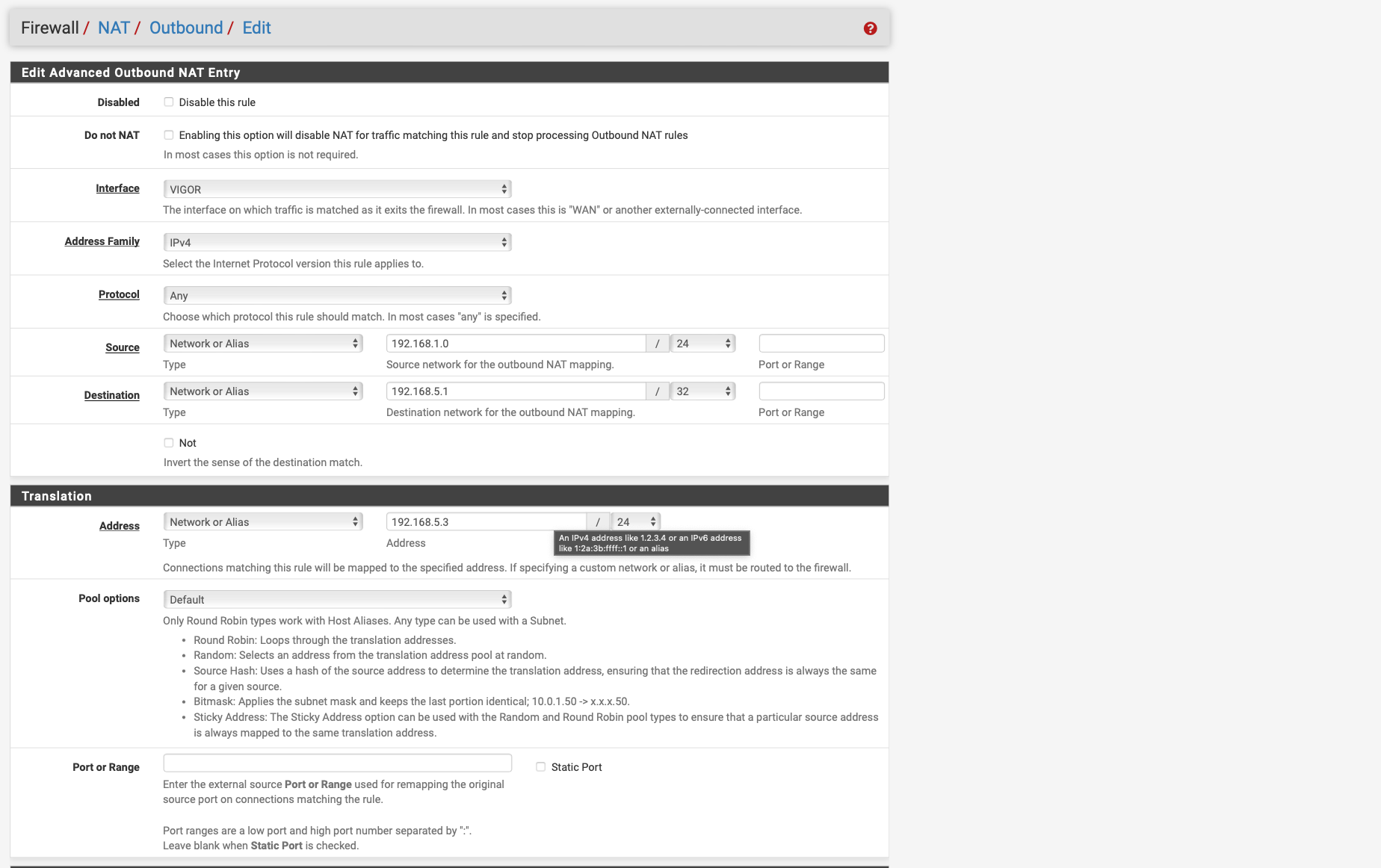
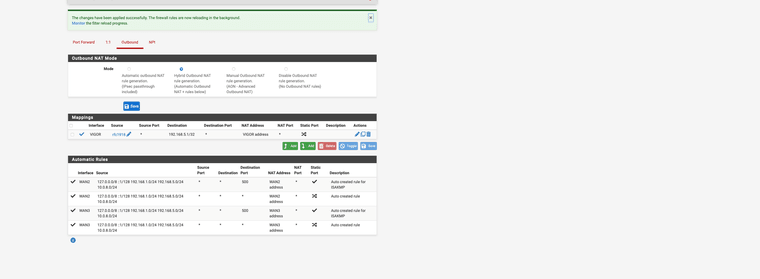
Please post your outbound nat rule..
Why do you show .3 and .4?
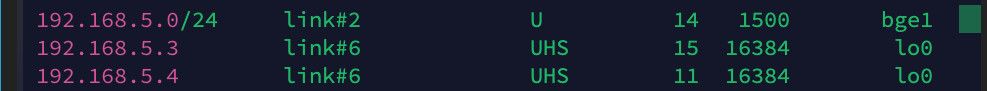
Did you create a vip or something? And your natting to the vip address? VIP is not something you need to create.. VIP was my attempt at showing you how it can be done when your actual interface has a actual public IP like mine does... You are using PPPoE so you don't need to create a vip
-
-
@Globaltrader312 just show your outbound nat tab.. Not the specific details of 1 of them - for a we know this one isn't even being used because you have some other one above it.
Example here is mine
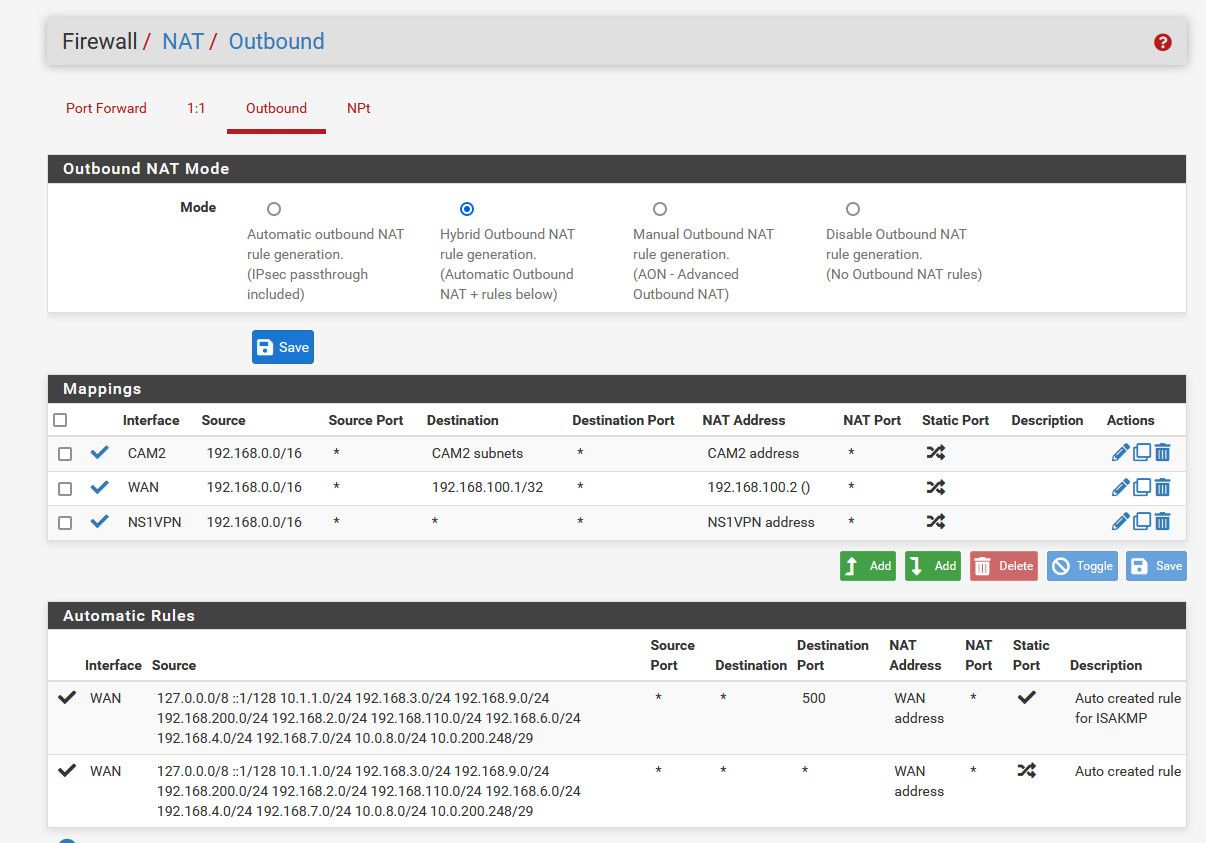
But this isn't right
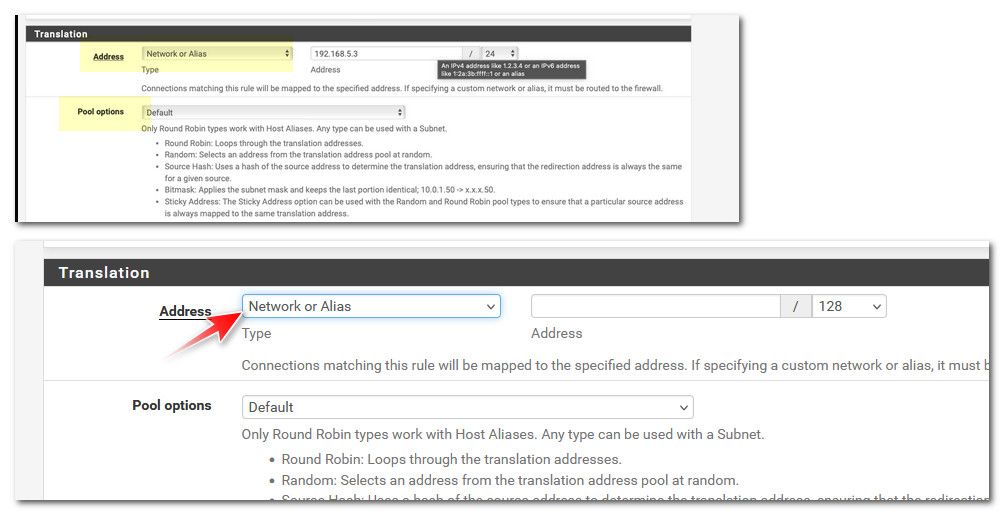
Click the dropdown and pick the Vigor address, which would be 192.168.5.3 from your screenshot
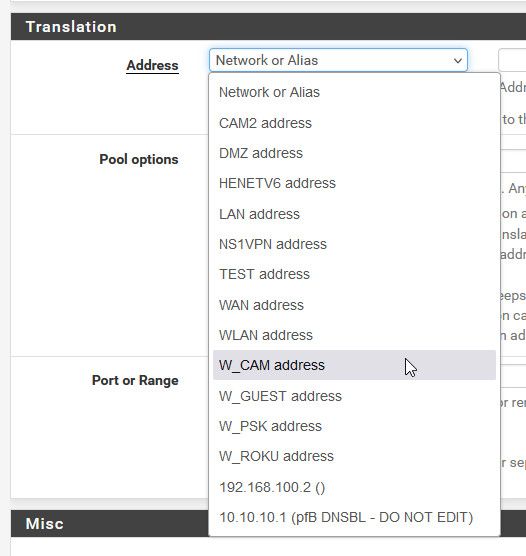
-
thank you guys for your help it works after i entered the alias rfc1918 as soure and selected 192.168.5.0/24 as destination and Vigor aadress as translation address.
-
@Globaltrader312 so if you would of followed the instructions, you would of been done in like 2 seconds.
And actually understood that you were policy routing.. How did you think something would work when your shoving it out some gateway that is not connected to what you want to talk too?
-
Great job, and you also learned port forwarding, ACL ordering, alias creation and much more. I love this forum you can learn so
much. Now you just need a OpenVPN configured with a NAS server for private cloud use