ATT Internet AIr
-
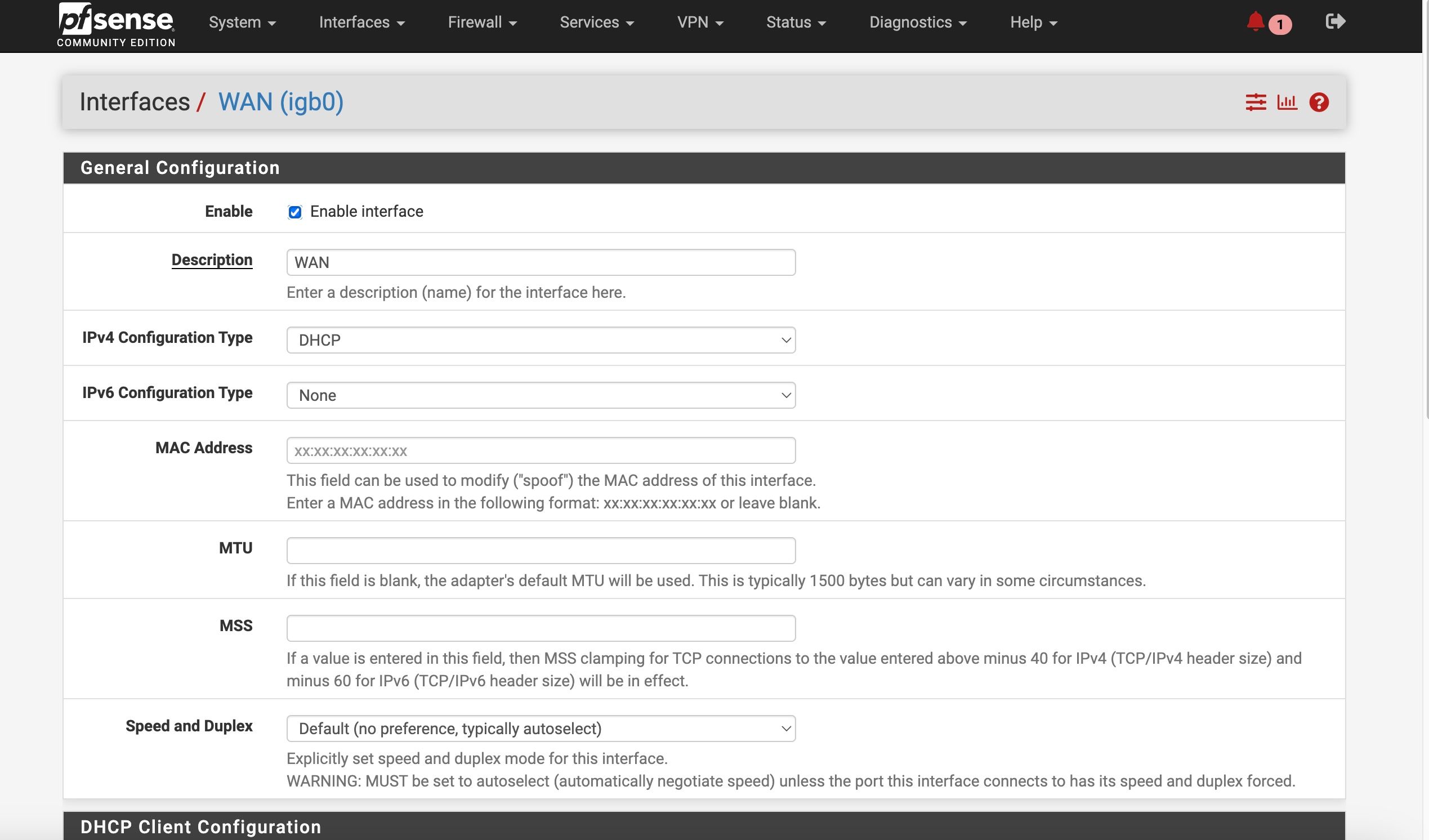
Though the source port should be empty because that's the port the client uses to connect from which is usually some high numbered random port.
Also you should se https (or both) if the router supports it.
-
@stephenw10
So freaking weird
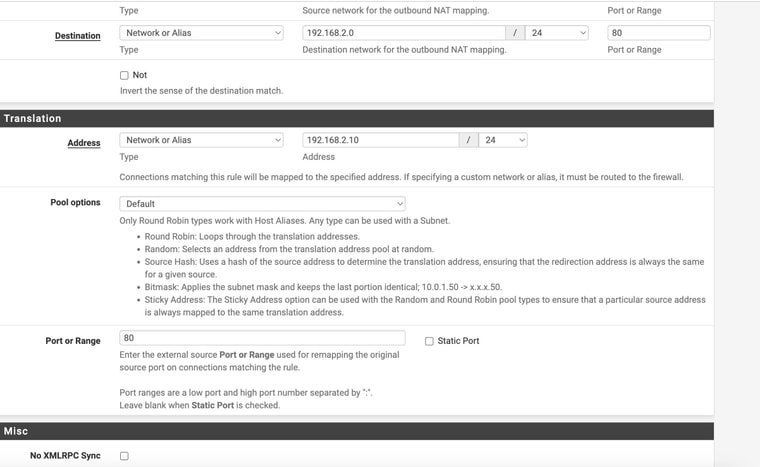
I made the change of the source port and then I could no longer access http://192.168.2.1
I can still ping the addressSo weird - I tried changing it back and it still wouldn't work
hitting my head lol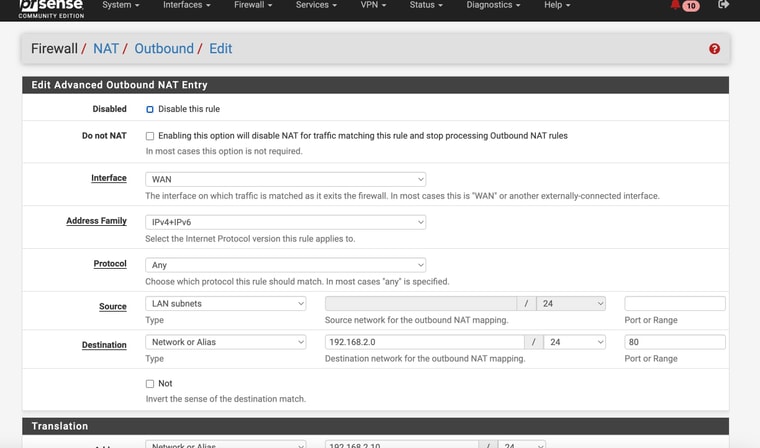
-
Hmm, odd. Try removing the ports entirely. There's no real reason to specify a port there, all traffic between LAN and the modem would need to be NAT'd.
-
@stephenw10 Well I tried to remove all the port entries and still no success
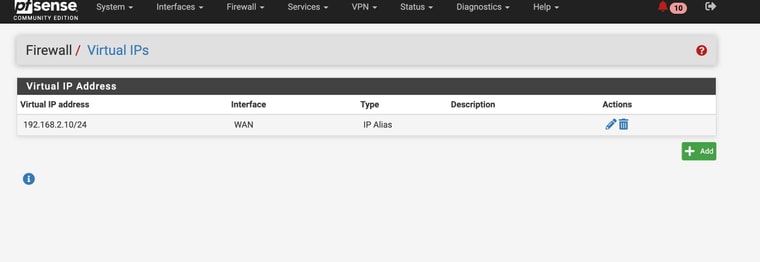
Whats really odd is that if I activate my Wireguard VPN into my network -- viola , I have access to http://192.168.2.1. (notice in my settings for the tunnel I have allowed IP ranges including 192.168.2.0/24
-
Hmm, almost sounds like that NAT rule is actually breaking the connection. Since with the source port set to 80 it would not have been matching the traffic.
Try disabling the rule.
-
@stephenw10 OMG!! That worked - after all that
Thanks again
-
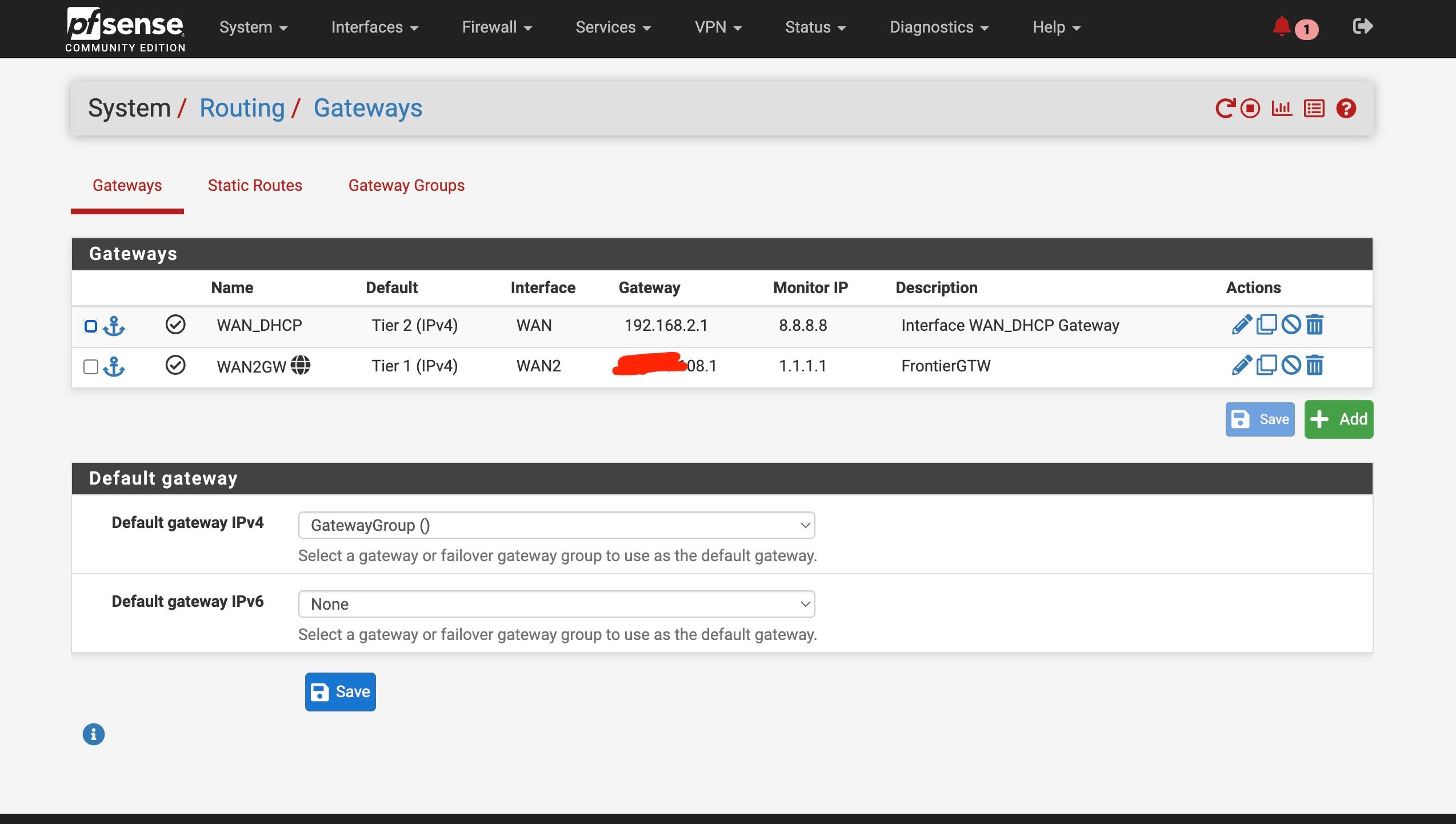
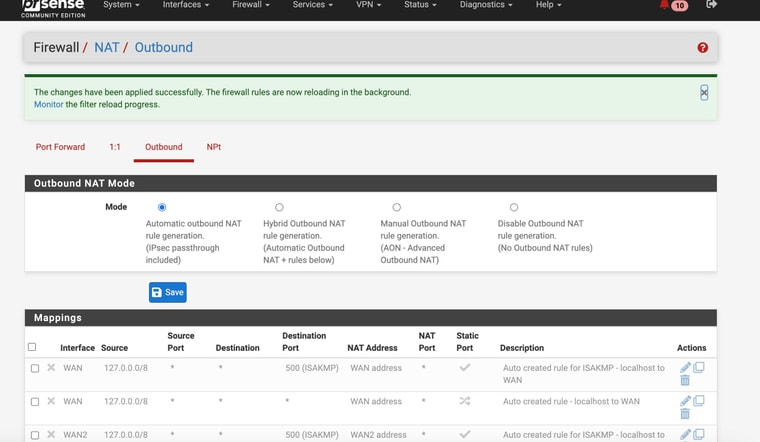
@stephenw10 Oddly I changed back to "Auto Mode" for Outbound NAT and it still worked
-
Hmm, interesting! That still using 192.168.2.1 to access it? It seems like the Nighthawk has a route to the public IP then. In which case that's no problem.
-
@stephenw10 yes still using 192.168.2.1
-
Should be fine then. Some modems do not require a NAT rules and can use the public IP on WAN to reply to.
-
@stephenw10
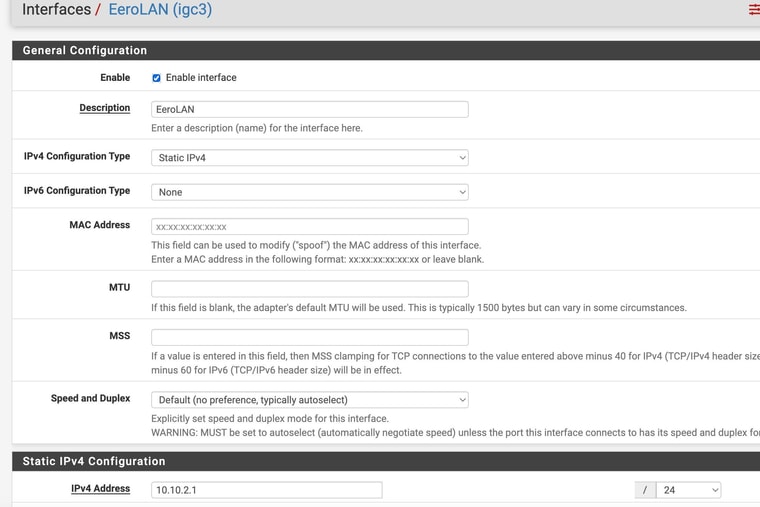
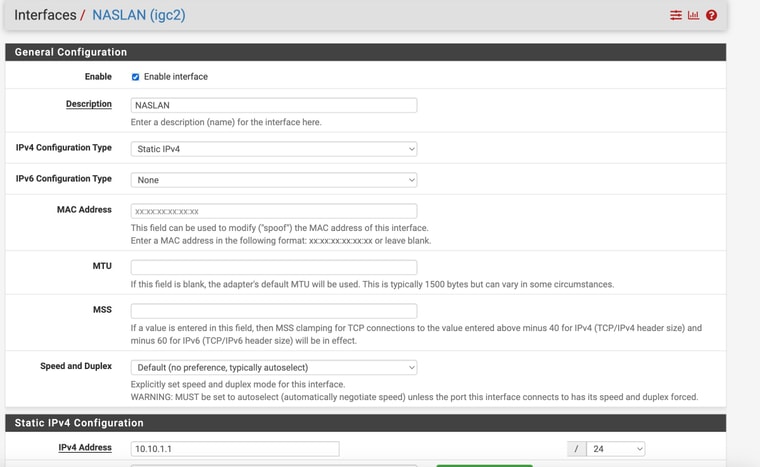
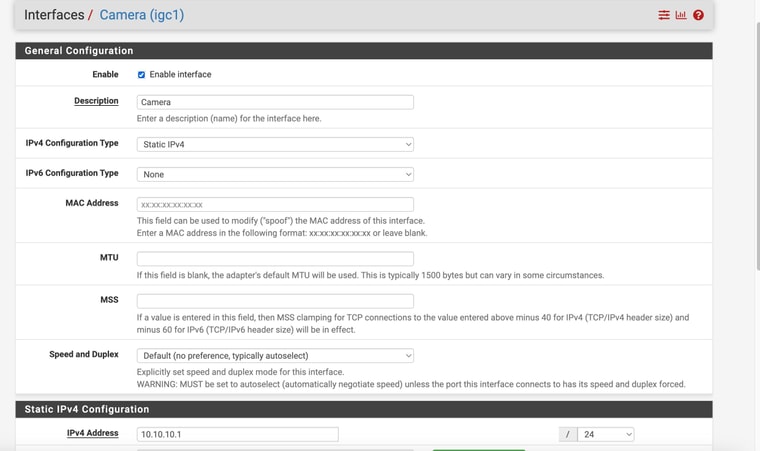
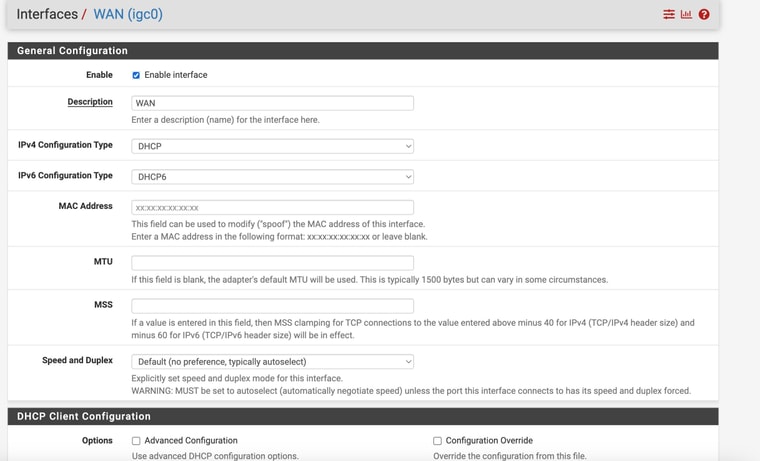
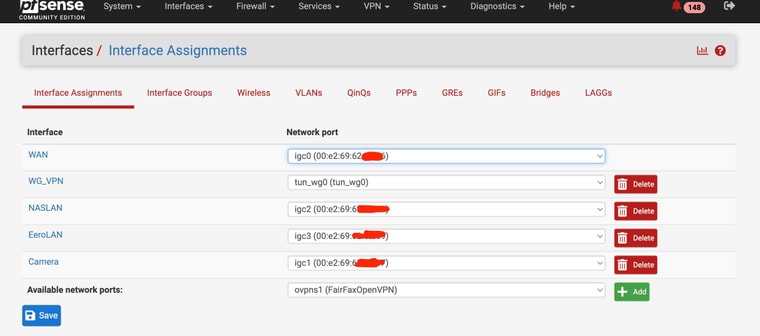
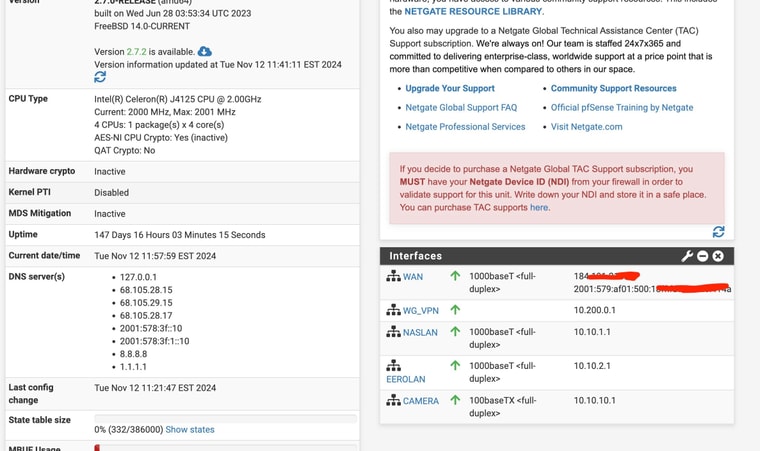
Now that I have survived that ordeal , lol (with you help) - I have to replicate the process at our second location.My pfsense device at that location only has 4 ethernet ports just like the one I have at location 1 - however, at location 2, I have all 4 ports used as per the pics. 2 are for security camera ports, one for and eero wifi and 1 for my NAS.
I have them on differnt networks.
What would be the best way to salvage my current equipment and still setup a failover internet (second WAN)? since my ports are filled
-
-
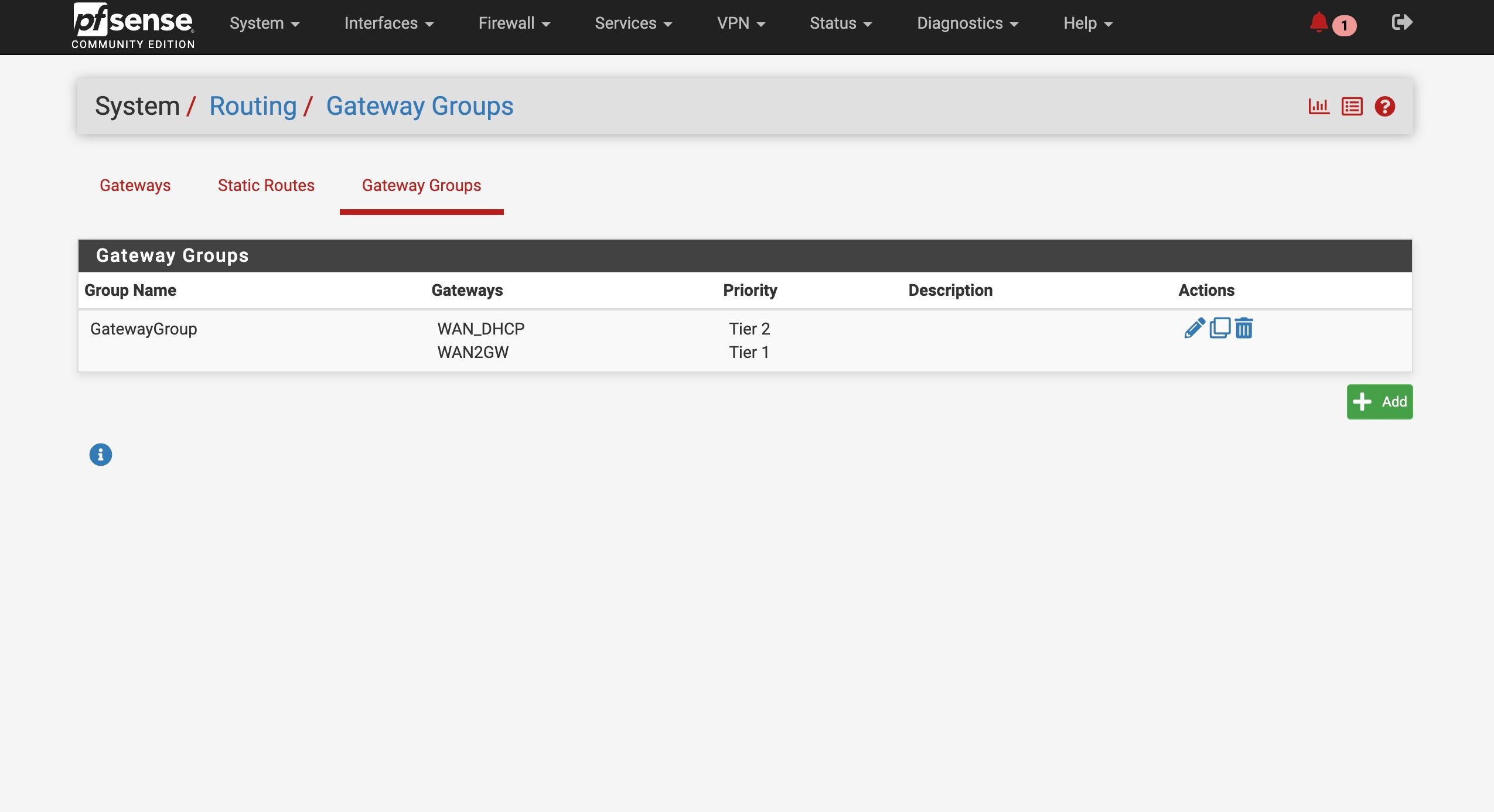
Add a VLAN capable switch and use it to separate some ports is what I would do there.
It might be possible to use the eero device to do that if it supports VLANs.
I assume you need to be able to filter between those three interal interfaces with different rules for each?
-
@stephenw10
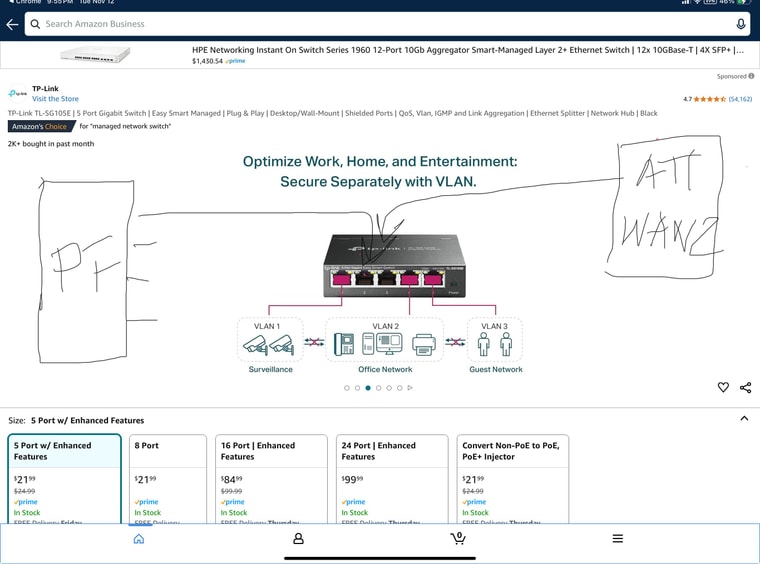
Haven’t used VLAN for this but wanted to make sure == I could buy this $20 switch
Change maybe my pFsense Camera interface to a VLAN parent interface?
Connect to one of the switch ports
And then have one port assigned as the Camera VLAN
And then could I assign another VLAN port as the WAN2 connection for my ATT failover ??Would that work? Can a VLAN port be used as a WAN connection
-
Yes exactly like that. The ports on the switch can be configured as access ports on different VLANs. The link to pfSense can carry all the VLANs. pfSense treats the VLANs as separate interfaces. And yes it can be a WAN, or any interface type.
-
@stephenw10 Perfect. thanks
-
Currently at my primary business location I have cameras on the same subnet as other devices - like the NAS, etc. My second business location as you might remember from above discussion has cameras on a seperate subnet.
Ideally I would like to keep acessing my cameras with the Synology Surveillance station which is within my network. However an alternative is to use the camera manufacturer software - but that requires a port forward., to be accessed externally.Is there a way to open several LAN IP addresses to a specific port - or even entire subnet to a particular port ? Or do a I need to change each individual camera to a non-default individual port?
Just trying to be the safest possible if I end up opening another port externally
-
Hmm, well I would avoid opening port forwards to each camera like that if at all possible. Especially if they are on the same subnet as other local resources.
To do it you would need to use a different external port for each camera and forward that to the internal camera IP. That way they can all be forwarded from the same external IP. But don't do that!
-
@stephenw10
OK. Maybe I better just keep doing the VPN connection and use of surveillance station which is part of the Symbology NAS
If that is the case and a VPN is used for external access with no open external ports is there really a strong security reason to have the cameras on a different subnet? -
Because any IoT device like that is always going to be a target for exploits. They usually only see updates for limited time (if you're lucky!). And if they are on the same subnet as other things then if a camera is compromised anything running on it will be able to directly connect. Or at least try to.