ACME using dynv6
-
@brtech
as said, I had to copy the dns_dynv6.sh script into the directory /usr/local/pkg/acme/dnsapi.
Additionally I had to add the following code part to the acme.inc file located one stage above:$acme_domain_validation_method['dns_dynv6'] = array(
'name' => "DNS-dynv6",
'fields' => array(
'DYNV6_TOKEN' => array('name' => "dynv6_token",
'columnheader' => "API Token",
'type' => "textbox",
'description' => "dynv6 API Token (Look
in dynv6 account settings - HTTP Tokens)" ) ));I inserted it at about line 657 where all the other dyndns packages are defined.
-
Sorry, meant to post back that it all seemed to work using the nsupdate rfc option in the dropdown after I checked.
So I didn't end up having to make any changes to pfsense at all
-
@brtech didn't understand - where do you run "nsupdate rfc"?
-
It's in the dropdown for method: "DNS-NSupdate / RFC 2136"
-
@brtech ah, ok, I understand - you are manually entering the required parameters in that method. I didn't realize that this would also have been possible...
-
Yes, works really well using the various key parameters from dynv6, only issue is that the certbot hooks I was previously using used _acme_challenge.mydomain.dynv6.net for one domain and _acme_challenge_domaina.mydomain.dynv6.net etc for my other domains.
I need to grep the code and see if there is a way of influencing the record being written.
If I was using different domains then I'd be fine.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
@brtech This is an older topic, but it looks like it's your most recent activity on the forum. Hopefully you have notifications enabled for replies...
In any case, I'm having some difficulty with ACME / dynv6 / DNS-NSupdate. Attempts to have a certificate issued soon fail with, "TSIG error with server: tsig verify failure update failed: REFUSED". I think I'm missing something in the pfSense / ACME config side, but I'm not sure. I haven't entered the tsig (host)name anywhere in the pfSense / ACME config, which seems important, but I'm not sure where to enter it. I entered only the tsig secret in the Key: field. I confirmed I'm using the tsig secret that was generated for the zone in question. I'm including anonymized screenshots below of my config and certificate issuing attempt output. Any suggestions? Thank you!

-
RFC2136 : using TSIG : the key name is mandatory here.
Example : when I generated a "TSIG key" at the server side (I'm using the domain name server bind), I get this :
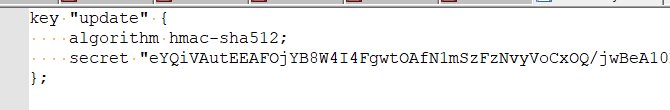
so my key is "update".
edit : if possible, look at the transaction logs 'at the other side'.
-
@regexaurus I found dynv6 to be so flakey I just moved to another provider, since doing that it's been 100%.
You'll find that some days it'll work and others it won't.
Figure for the cost of a few coffees for 3 years that it's worth picking a big one and going with it (I use the CNAME to reflect the ACME alias to the new provider)
-
@Gertjan I had tried putting the TSIG key name in the Key Name: field (pfSense / ACME), but when I clicked Issue/Renew, it seemed to time out. I think I wasn't patient enough and should have tried clicking Issue/Renew again after 10+ minutes or so.
I found the text above the Key Name: field confusing: "(Optional) A name for the key, if it is different than _acme-challenge.[Domainname]". I thought putting the TSIG key name in that field might keep the ACME validation process from working. But I put the TSIG key name in the Key Name: field again, set DNS-Sleep to 900, and clicked Issue/Renew again. This time, at some point I checked my Dynv6 records and noticed a _acme-challenge.myhostname.dynv6.net record. The ACME certificate request process still seemed to time out / stall somewhere. The Issue/Renew button appeared with a broken link icon. I'm fairly certain this was before 15 minutes (900 seconds) was up. But I clicked Issue/Renew again and this time very quickly had a bunch of happy green log output and the certificate was installed.
@brtech I had used Dynv6 a while back and reached a similar conclusion. I thought maybe they've improved reliability by now...Thank you both!
-
@regexaurus said in ACME using dynv6:
I found the text above the Key Name: field confusing: "(Optional) A name for the key, if it is different than _acme-challenge.[Domainname]". I thought putting ...
If the insertion of a DNS TXT record into the domain name uses RFC2136 then the key and key name are mandatory.
That's the way 'bind' (world's most know domain name DNS server') works.
Other could have simplified the method somewhat.
So, yes, I agree, the world optional can be confusing, but normally, when you chose a DNS method you do this because the registrar you use instructed you about the method, and thus parameters, to use.The TXT record insertion works like a DNS request, and I can see these request that acme made in my domain name 'master' server.
Note : still, a acme "dns sleep" is need, as the domain name server, when it receives an zone update (the inserted TXT record) will signal the slave DNS server(s) - there will be 1 at least - and these will sync whenever the feel fit, so this can be done in "seconds" or way, way later (600 seconds ?).Who is dynv6 ?
-
@Gertjan said in ACME using dynv6:
Who is dynv6 ?
dynv6.com is nifty for DDNS. They allow you to "freeze" the Interface-Identifier (or host part) of a dns-record and only update the prefix from a given ipv6-address. Something the other sense can do now ootb (if I am not mistaken) and what is still missing in pfSense.
So for example with them you can use your pfSense LAN-ipv6-address to update only the prefix, while the Interface-Identifier of your actual server's dns-record stays the same. -
@Bob-Dig said in ACME using dynv6:
dynv6.com
Ah, ok, thanks.
One click into their interface I found https://dynv6.com/docs/apis#dns-update where, in their example, "tsig-123.dynv6.com" is the key name.
So : it's not optional.Btw : a bit out of subject, but I can't see the usefulness of publishing my "pfSense LAN-ipv6-address".
I do use
[25.03-BETA][root@pfSense.bhf.tld]/root: ps aux | grep 'ddns' root 50513 0.0 0.5 34784 18592 0- I Fri08 0:03.02 /usr/local/sbin/kea-dhcp-ddns -c /usr/local/etc/kea/kea-dhcp-ddns.confso my pfSense IPv6 DNS registered host names are updated into my main domain name server.
This allows me to use the host name of certain of my pfSense LAN based devices (only !) over IPv6.
So 'diskstation2.bhf.tld' will always point to the IPv6 of my NAS.
The usage of "kea-dhcp-ddns" isn't supported by pfSense at this moment, had to set it up and activated it manually. -
@Gertjan said in ACME using dynv6:
but I can't see the usefulness of publishing my "pfSense LAN-ipv6-address".
You don't publish it, you use it, to update only the prefix part of a given dns-record.
I for example changed to only use ULAs in my LANs. But also I have some "unused" VLANs set to "Track Interface" to get the daily changing prefixes to then use them with NPt for my ULA-LANs. I would benefit from what I have described before.
If you, as an expert user, found a solution, that works for you, that is great. I still wait for pfSense to bring a better solution to this for the rest of us. -
Hello,
I am also trying to use DNS-NSupdate / RFC 2136 with dynv6.com. I have used all the information in this and the other related thread, but acme.sh blocks when trying to read the key from the disk.
The logs show that the key file is expected in
/tmp/acme/home-mydomain-tld-test-dynv6/home.mydomain.tldnsupdatealias-mydomain-tld.dynv6.net.key
but is actually in
/tmp/acme/home-mydomain-tld-test-dynv6/home.mydomain.tldnsupdate_acme-challenge.alias-mydomain-tld.dynv6.net.keyDid I mess up the parameters or is there a bug in the call to acme.sh?
Thanks for your help,
Atanis