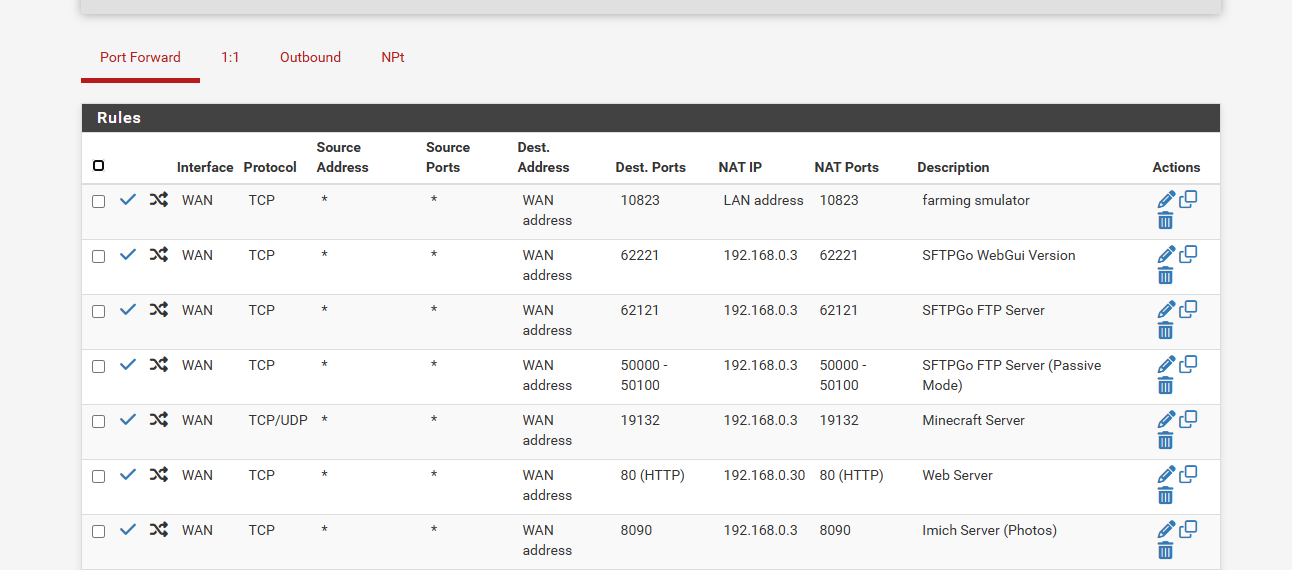
Port Forwarding stopped working after upgrading to 2.8.0
-
so i set General Setup
just the 2 dns serversi set the use remote dns ignore local
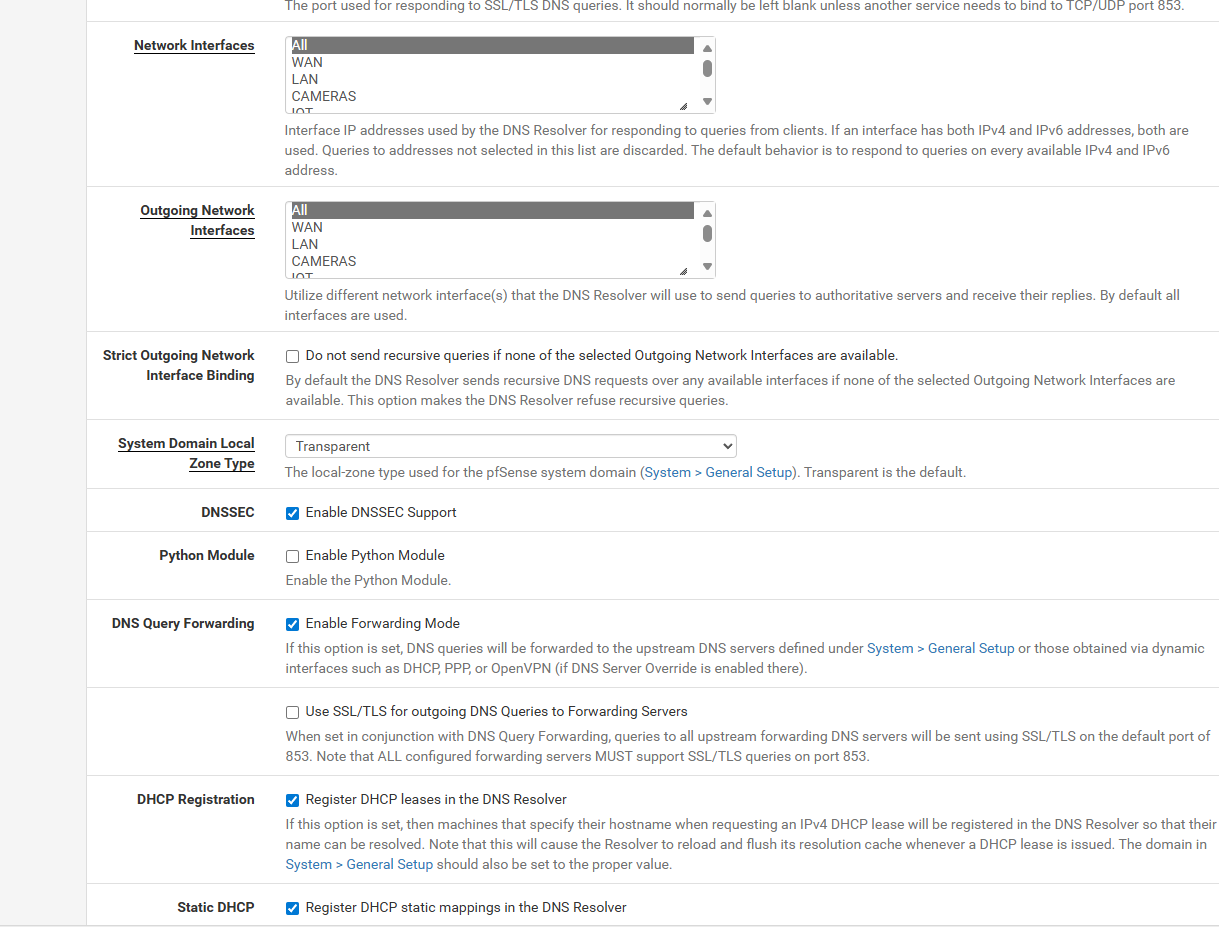
under dns resolver
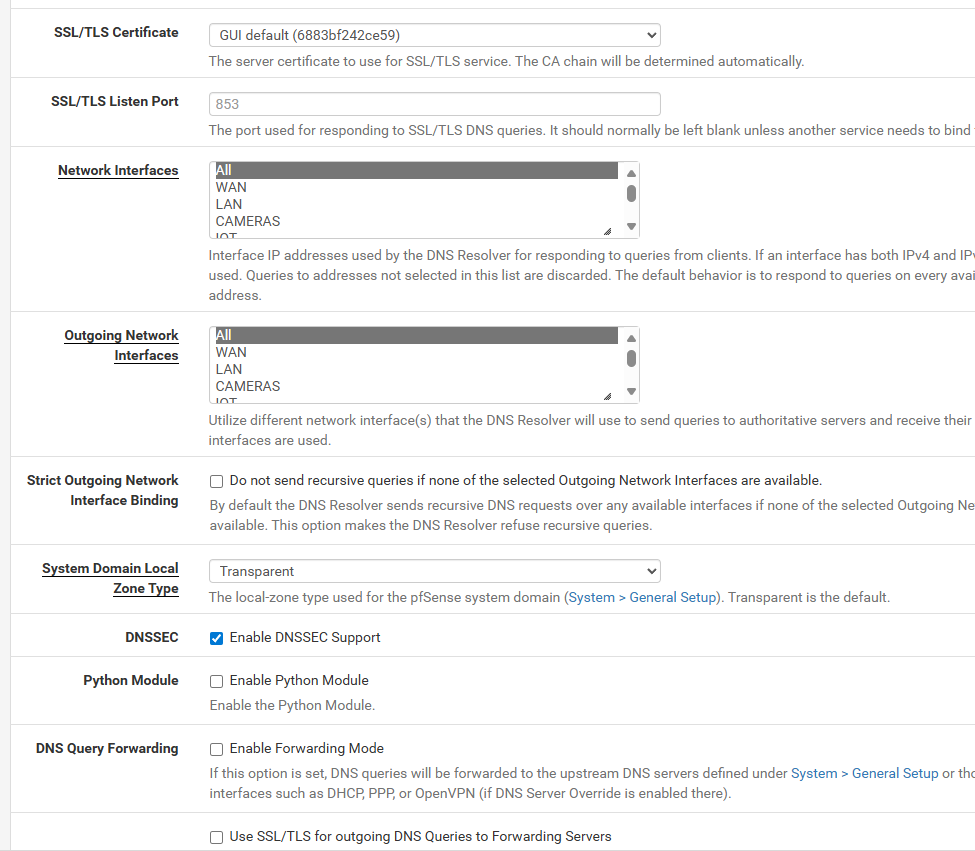
i unchecked dns sec, left the enable forwarding, and i set the incoming all and outgoing to just the 2 vpn servers
now i going to let that run all night and see what happens....
and ill look up that other information tommorow
-
You can't DNS Lookup 1.1.1.1, it's not an FQDN.
When you have the outgoing interfaces in Unbound set to only the VPNs then it will fail to resolve anything if the VPNs go down.
If pfSense itself it also set to use only the VPN DNS servers it won't be able to resolve the VPN servers to connect to them.
pfSense itself must have access to some other DNS server. Or the VPN servers must be entered as IP addresses directly.
I would revert to a much simpler more default config and make sure that works first.
-
@stephenw10 sorry i havent replied i was outta town for family issues and i didnt get notifications that you replied so i also tried other sites and youtube. but still stuck
so i did a more simplier as you mentioned
so couple issues i but i followed a Lawerence Systems setup of the pia vpn he had 2 different videos plus i watched ca couple others
they dont have any general/setup servers
and they dont touch the dns resolver.. so i set it to defaultall and all for incoming and outgoing
i check enable dnssec support
i check Register DHCP leases in the DNS Resolver
i check Register DHCP static mappings in the DNS Resolver
i check Register connected OpenVPN clients in the DNS Resolverand i removed the host overrides i had for the time being
so this setup works for a while till my internet bogs down for a while and then things dont work.. but i can disable my vpn or reboot and internet works again..
my wan connections still cant resolve home depot right i get that something goes wrong.. but if i change the dns in windows to 1.1.1.1 it can resolve home depot searchs fine.. remove to to use 192.168.0.1 it wont work righti even made the NAT simplier i went to also hybrid mode..
and i had another question i had posted in youtub but no replies
if i have the no wan egress so no VPN traffic can go out the WAN but i get like my ISP dns on the VPN or the 1.1.1.1 on the VPN as a dns... does it matter? does it still get monitored or does it only monitored going out the WAN
and so far the only way i can keep my internet from crapping total out
i set
General setup 1.1.1.1 wan_ppoe
Dns resolver All/All incoming/outgoing
i check enable dnssec support
i check Register DHCP leases in the DNS Resolver
i check Register DHCP static mappings in the DNS Resolver
i check Register connected OpenVPN clients in the DNS Resolver
i uncheck Enable Forwarding Modebut thats when i get cloudflare on my VPN
to get my ISP on my VPN
i set
general/setup - i remove all the dns's
Dns resolver All/All incoming/outgoing
i check enable dnssec support
i check Register DHCP leases in the DNS Resolver
i check Register DHCP static mappings in the DNS Resolver
i check Register connected OpenVPN clients in the DNS Resolver
i uncheck Enable Forwarding Modeso curious in the end if it matters if the dns of the isp or cloudflare matters on the vpn thats supposed to be secure... or can i block the cloudflare or the isp dns on the vpn side
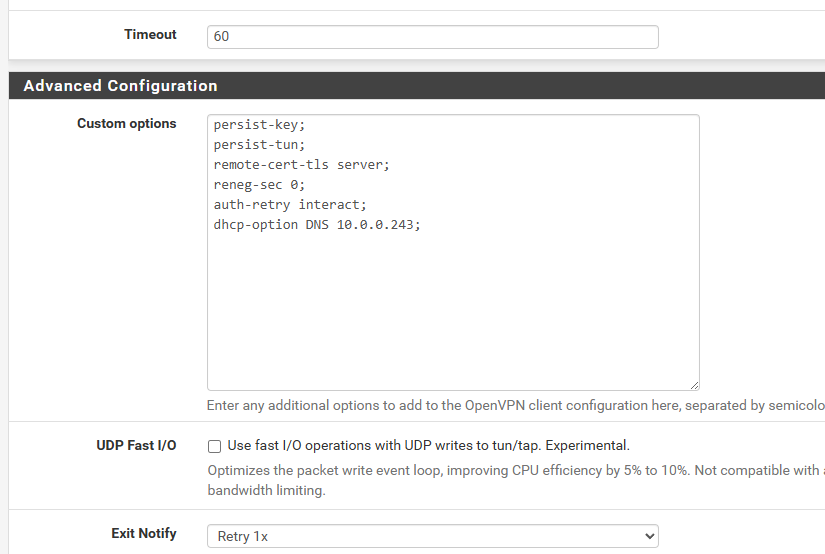
oh and i tried for the vpn settings
persist-key; persist-tun; remote-cert-tls server; reneg-sec 0; auth-retry interact; dhcp-option DNS 10.0.0.243;persist-key persist-tun remote-cert-tls server reneg-sec 0 auth-retry interact dhcp-option DNS 10.0.0.243i seen some use the ; on the back of each option and some dont but i didnt find any made a difference
sorry for the delay
-
@stephenw10
oh and what i did have that worked but dns still leaked to vpn sidewas 1.1.1.1 general setup to wan_ppoe this kept the wan from going down
and then had selected the VPN in the outgoing on outbound interface..
and i had unchecked the forwardingthat seemed to keep things going but WAN clients werent able to work Homedepote serach right
i also tried a setting i found under Adavanced Firewall
i set Firewall State Policy to
interface Bound States... to keep the states to the gateways i thought that would keep each dns in its own lane.. 1.1.1.1 only goes to wan_ppoe 10.0.0.243 goes out the one vpn gateway... under the general setup.. but that didnt keep them seperated either.. still went to the vpn side -
@stephenw10 said in Port Forwarding stopped working after upgrading to 2.8.0:
You can't DNS Lookup 1.1.1.1, it's not an FQDN.
You should be able to:
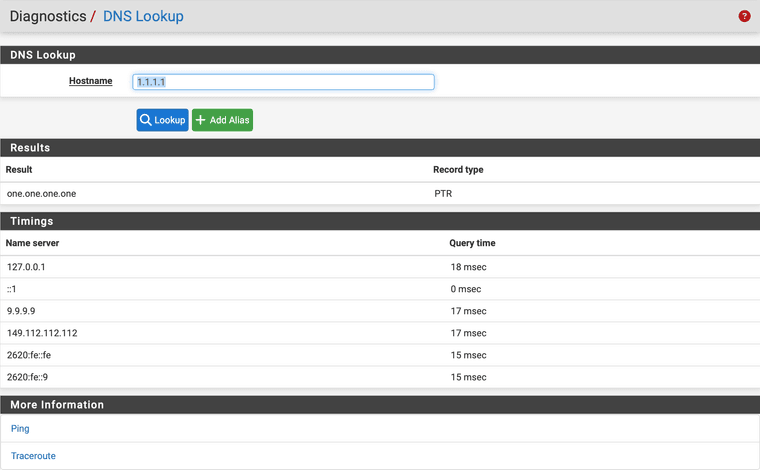
-
@dennypage ya i can do that
i changed the 1.1.1.1 in general setup to 103.86.99.100 NordVPN dns
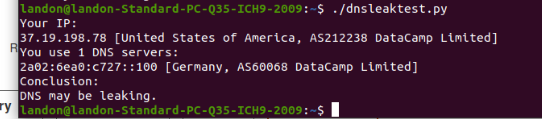
when i set the wan_ppoe to 1.1.1.1 i get like 10 Cloudflare DNS's on VPN side clients instead of 1 dns name for the 10.0.0.243 and tells me dns maybe leaking
but using the 103.86.99.100 only pops up 2 dns servers on the VPN side then
but here is the 103.86.99.100
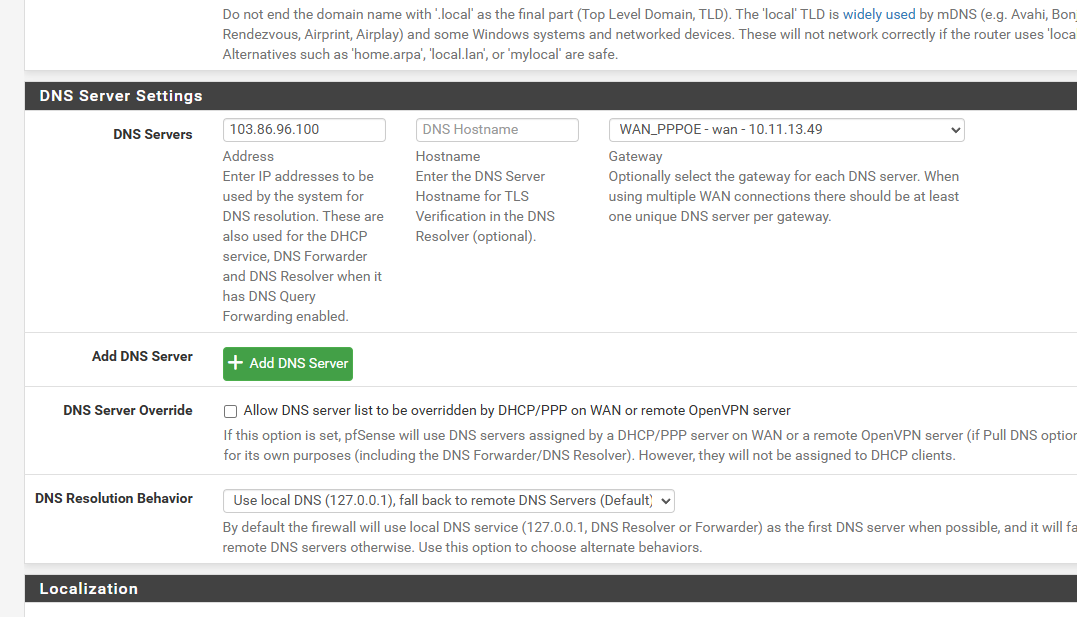
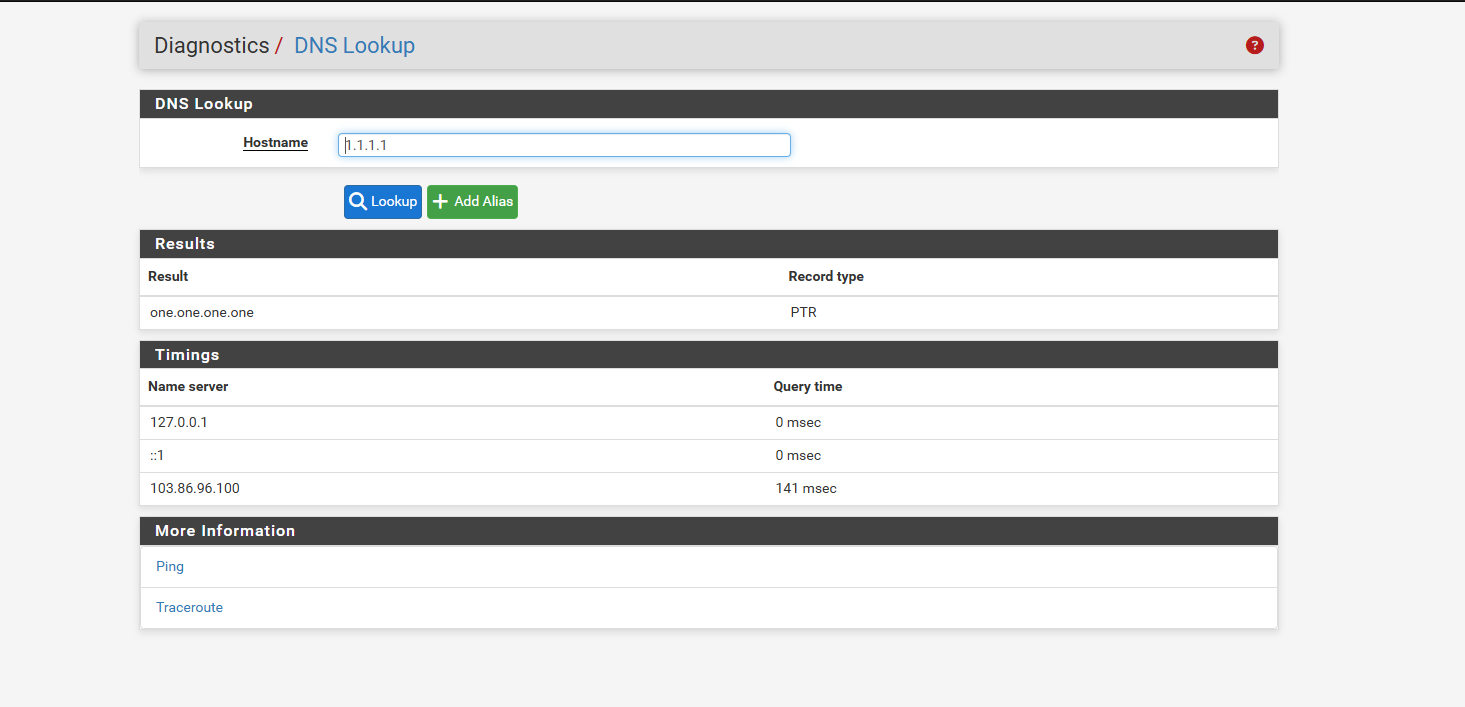
-
and this is my current settings
and yet WAN DNS keeps showing up on VPN side.. when really only 1 dnsbut i dunno if its just ok
as you can see with the current settings the 103 germany dns server shows up on the vpn side it doesnt leave just the 1 dns server... but i dunno is it ok since the traffic isnt going out the wan.. or does it matter and any dns's even though secure on vpn if the like cloudflare shows on the vpn side does it mean they see what your secure traffic is doing
-
oh and PIA VPN customer service are not willing to help there response is we dont know pfsense and to use community forums to get any help
-
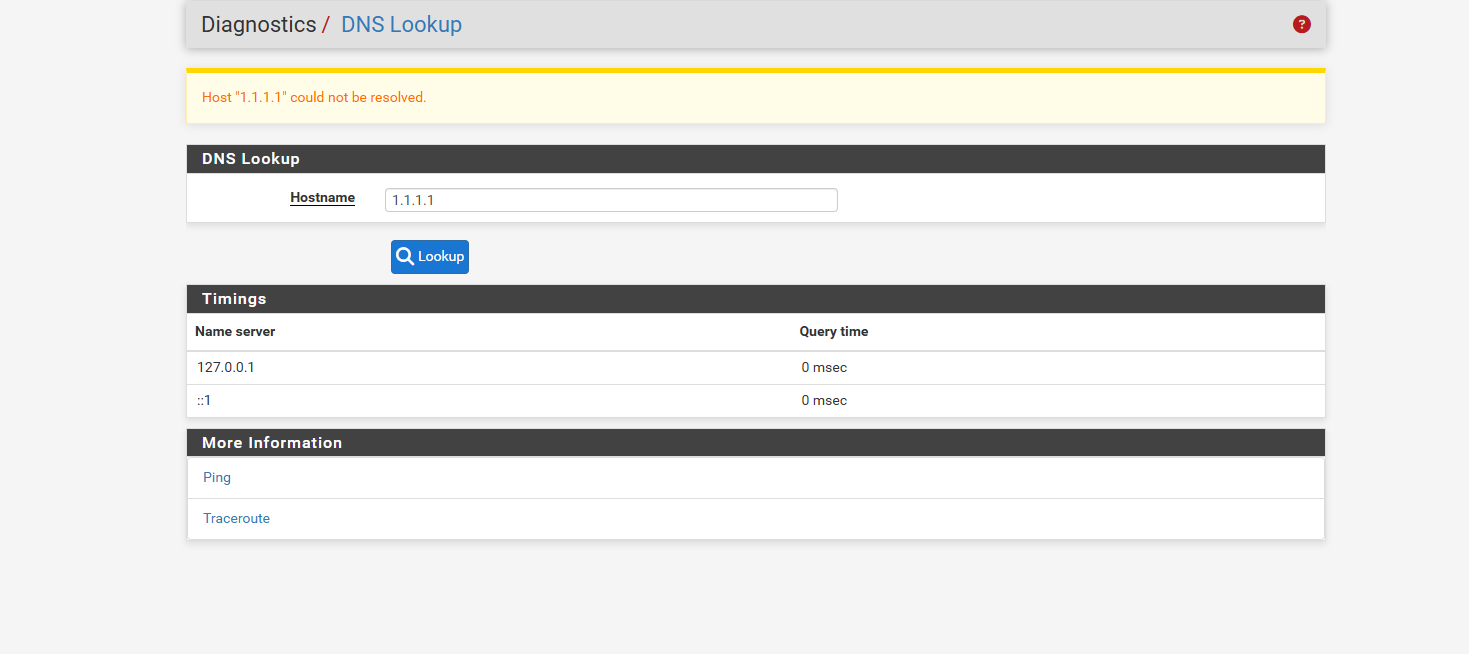
@dennypage so i was able to make the dnslookup 1.1.1.1 fail after several hours i defaulted my DNS Resolver.. so it is out the ALL interface.. no General Setup
Pfsense Cant ping doman names.. it can ping 1.1.1.1
pfsense cant dnslookup 1.1.1.1 but it could ping itWindows machine on WAN side lost its internet cant ping domain names but it can ping ip address 1.1.1.1
my Ubuntu 2 VMS 1 behind VPN and other on my DMZ which is just WAN
both can ping domain names both can go to like google. or amazon.com but windows machine looses it
and so does pfsense ... and pfsense default gateway is using the wan_ppoe not the automatic..
i swear it has to be my provider..also when my windows machine is using 192.168.0.1 as dns it should be using the ISP dns and resolve Home depot search engine but it cant.. but as soon as i change the 192.168.0.1 dns to 1.1.1.1 it can perfectly resolve it...
i guess also windows must resolve things differentl then ubuntu
i swear my 3megabit internet cant handle both vpn and wan tunneling when wan bogs down but it cant resolve in windows right unless pfsense factory reset then it can desolve right
i figure it has to be my provider too buggering up things i dunnoi swear its like it stalls out cuz everything requires faster then 3mb so if you go to long maxed out it really buggers it all up.. least thats my idea
but here is some screen shots
-
You can't use the ISPs DNS servers over the VPN. They are almost certainly only available from the WAN IPs so not via the VPN.
What do you have the DNS behaviour set to in General Setup?
That's important because it determines what pfSense can use to resolve the VPN servers (assuming you are still using FQDNs).@comet424 said in Port Forwarding stopped working after upgrading to 2.8.0:
if i have the no wan egress so no VPN traffic can go out the WAN but i get like my ISP dns on the VPN or the 1.1.1.1 on the VPN as a dns... does it matter?
You mean a firewall rule that blocks outgoing traffic on WAN? What exactly is that rule?
Does the setup work fine if you don't use VPNs at all?
-
This post is deleted! -
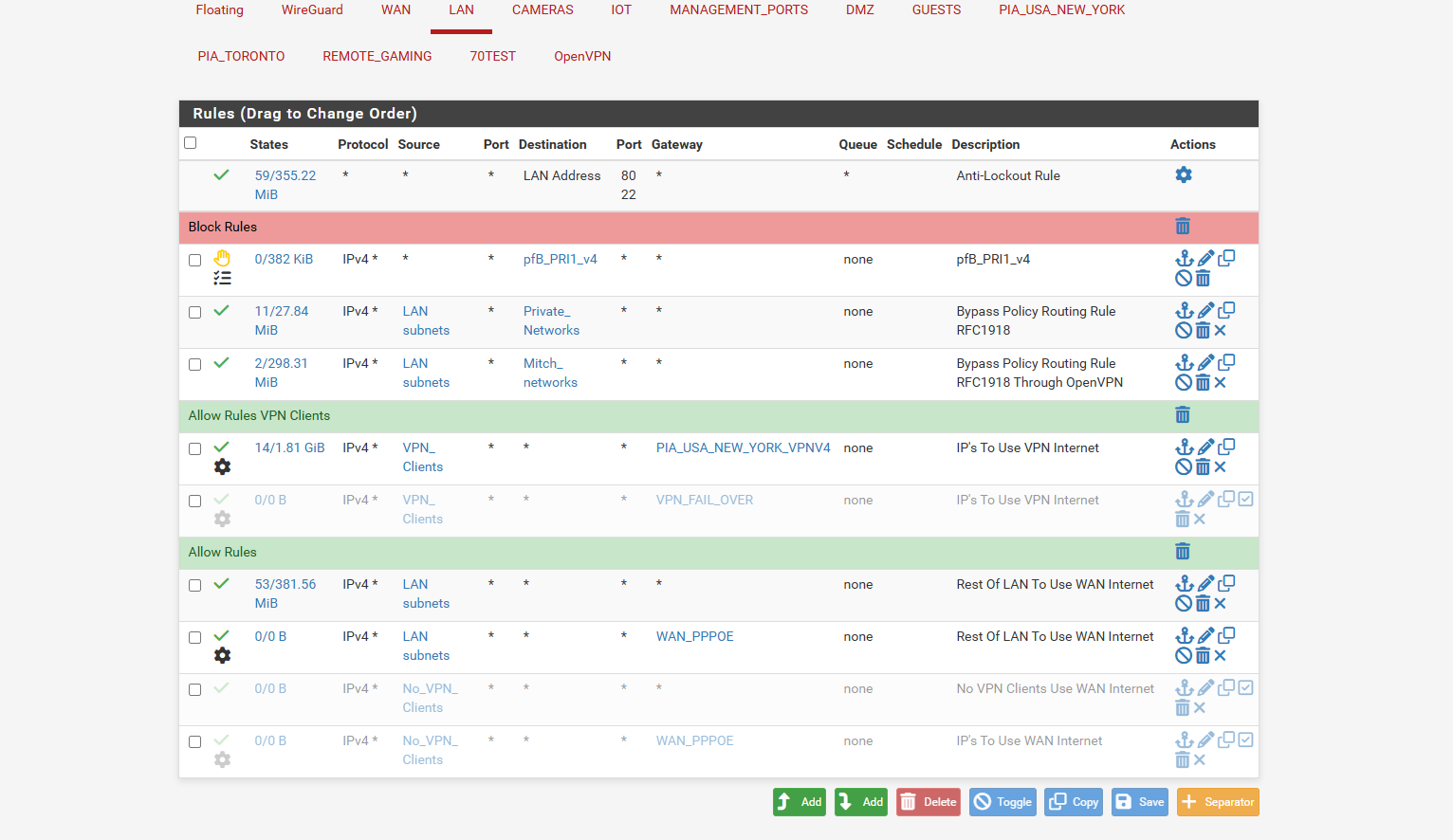
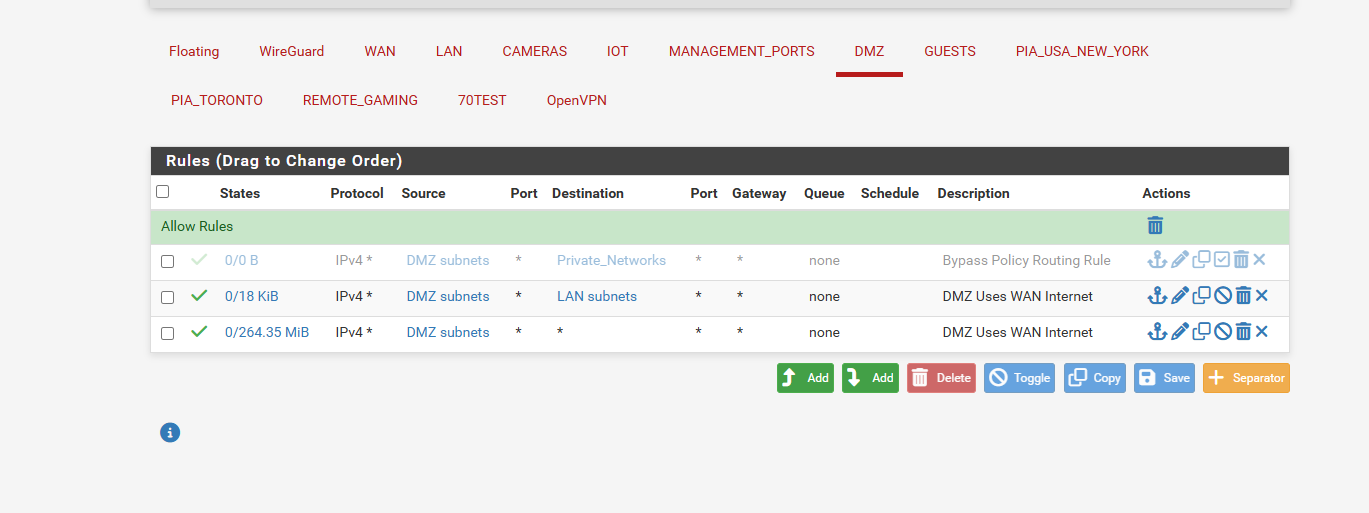
so i turn off the traffic rule for vpn and the VPN traffic is going out the WAN
so guess my blocking rule isnt working in the dns leak test now you see for the VPN it went from 1 ISP and VPN DNS to now 2 ISP DNS
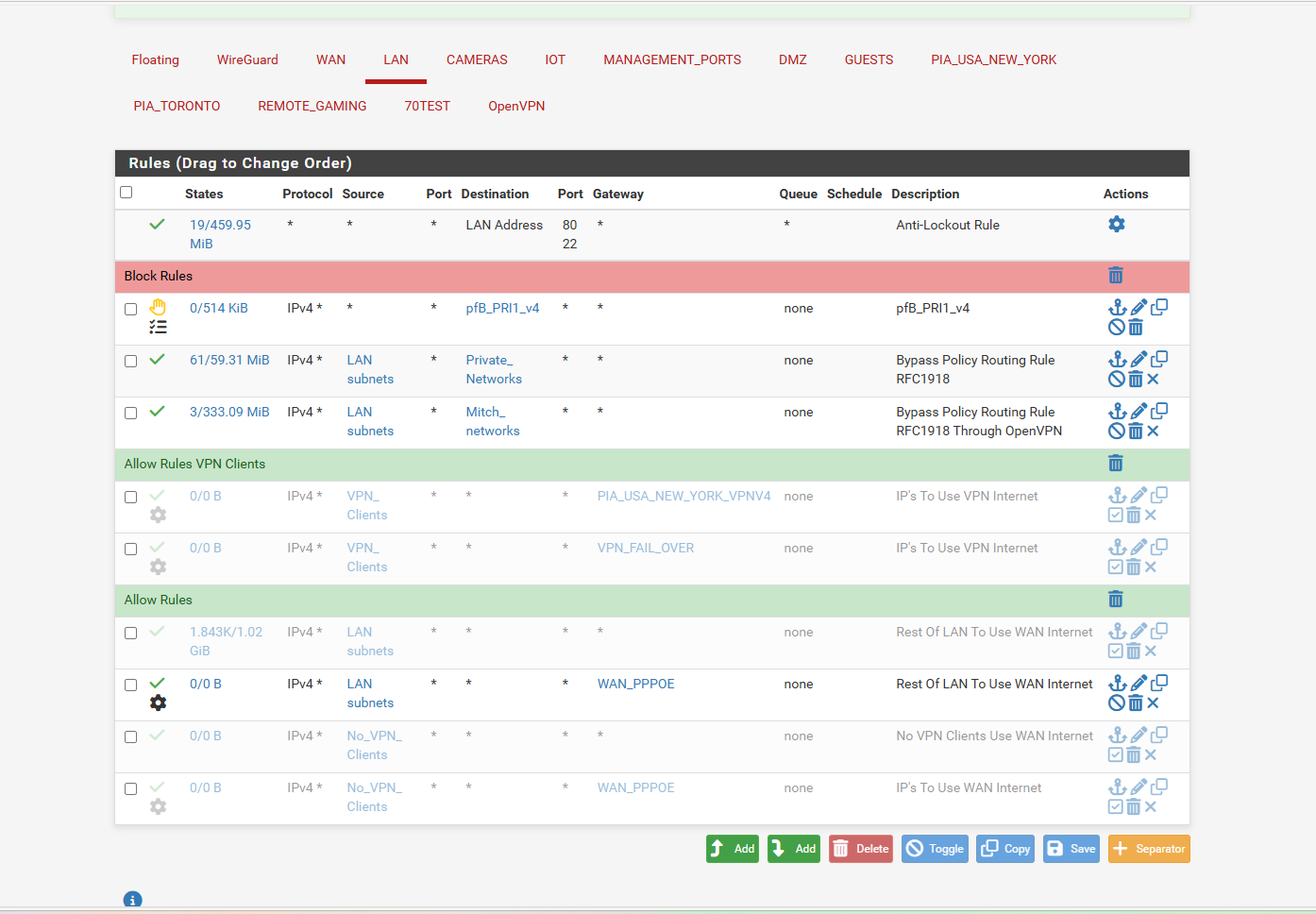
-
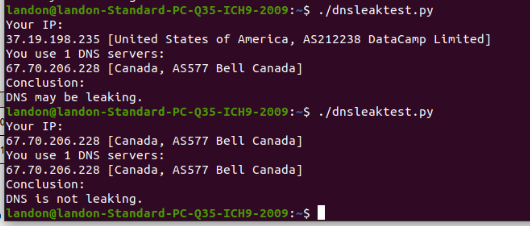
so when i disable the VPN
and i use the windows machine thats on the WAN
i get 1 DNS the ISP and i cant resolve a search in HD
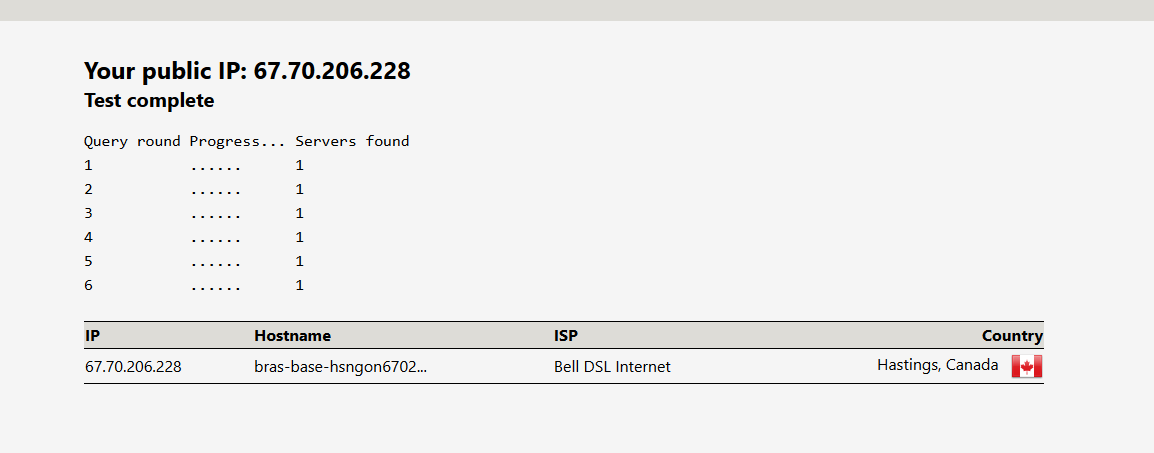
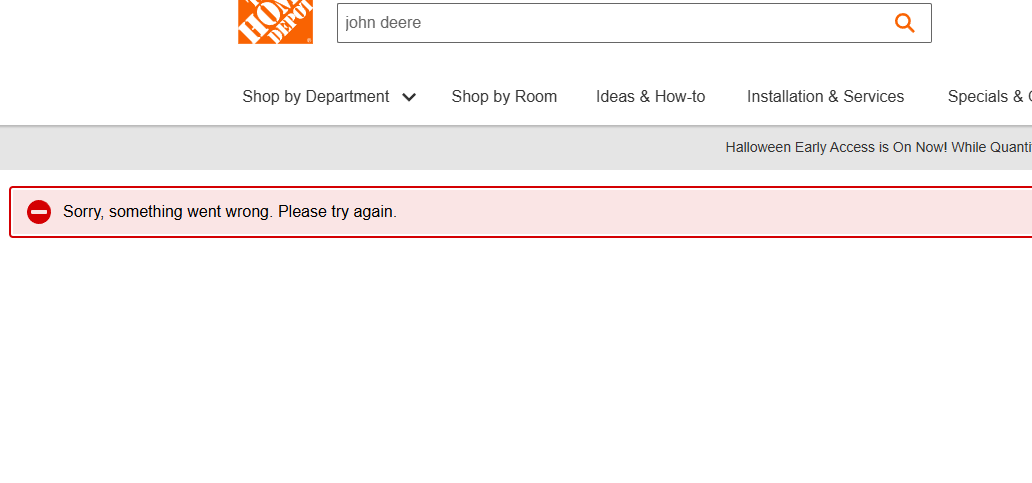
so it doesnt work right for WAN even though i disabled the VPN
-
and here is where i re activate the VPN rule in rules LAN
this is on the ubuntu VPN clients sidethe web gui points to cloudflare but the dns command line points to a PIA dns and ISP DNS
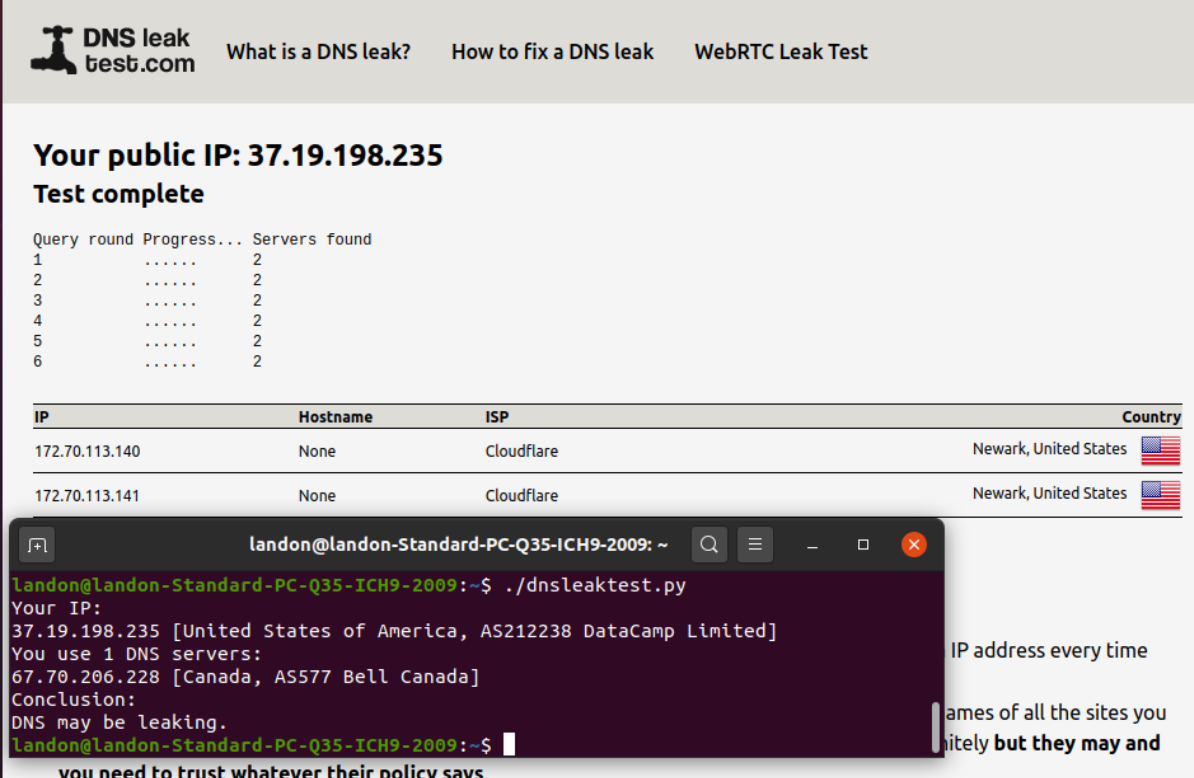
and this is the custom options for the one vpn
persist-key; persist-tun; remote-cert-tls server; reneg-sec 0; auth-retry interact; dhcp-option DNS 10.0.0.243;a few minlater the isp shows up on dnsleaktest website on VPN Clients
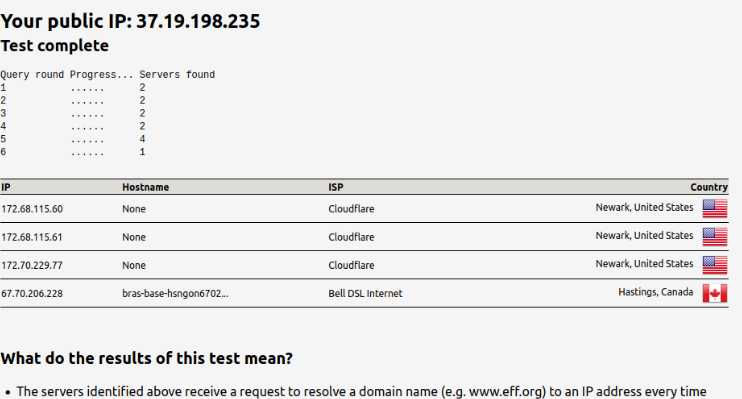
some articles videos use ; and some remove it so i dunno whats right
i followed both lawerenc System Videos neither use dns resolver and they dont address dns of ISP showing up on the vpn side or cloudflare
https://www.youtube.com/watch?v=ulRgecz0UsQ
https://www.youtube.com/watch?v=TglViu6ctWEand i followed this sheridan guy but also doesnt cover dns resolver or dns of isp or cloudflare showing up on the VPN side
https://www.youtube.com/watch?v=ffVPOaLCuMQi followed this guys tutorial. doenst use Dns Resolver.. but also sets the PIA interface to use the WAN NAT Address. in NAT Outbound.. where others use PIA Interface to go out the PIA NAT Address.
https://www.youtube.com/watch?v=SckOaNfptAAso unless i really messed up somewhere i dont know why they show up on the vpn as dnsleak.com also says leakage..
i even left them messages on how to stop the leakageand PIA customer service isnt willing to help.. they just stop replying and say go ask the community for help
also whats funny if i disable the VPN so the vpn clients use WAN connect
the windows machine gets the ISP DNS... but the ubuntu dnsleaktest website keeps pulling cloudflare.. but the command line will just pull the isp dns.. i guess ill try again restart from scratch and just setup the vpn and wan and a couple ips not the whole network.. as i cant figure it why things dont work and ill just do 1 check box at a time and test cuz its gotta be just 1 check box.. one semi colon something in the wrong spot thats doing it... -
OK so your block rule to prevent leak relies on tagging traffic from clients. Where is that being tagged?
Can you search in the HD site before you added any of the VPN stuff? If looks more like something is blocked there. Like maybe you have pfBlocker with DNSBL enabled that's blocking something required for that serach. Enabling the VPN with external DNS bypasses that.
-
@stephenw10 oh i guess i should labeled the screen shots like sections
so the WAN has the TAGGED section
and the VPN uses the TAG screen shot so
and i tried this morning and desktop windows seems to be working i let it rest cuz filter reload states reset ipconfig /flushdns didnt do anything..
so ill test more to see if its the pfblocker if it fails later today
and i have question if you have say 3 computers behind WAN or behind VPN and you run dnsleaktest should they not all respond with the exact same dns server? as my desktop comes with my ISP windows machine... ubunutu comes back with cira-cloud1 dns Firefox docker comes back wit cira-cloud dns or sometimes it comes back with cira-cloud1 plus my DSL dns
and on the VPN side i get the screen shots i sent i get vpn datacamp but also the ISP dns,, or on ubuntu i get Cloudflare and a windows machine i get cira-tsi.tor.teksavv... dns
so i confused cuz dnsleaktests tell me i leaking gui dnsleak tests show different from the command line dnsleaktest
does the semi colon in the vpn custom options matter? as some use it some dont use it
and does it matter what dns shows up on the vpn side if you block the vpn traffic going out the wan.. i asked PIA customer service they never bothered to even get back to me poor service. should stuck with nordvpn
-
Hmm, just to be clear you are taking about OpenVPN clients configured in pfSense? Conneting to PIA? Not a remote access OpenVPN server in pfSense?
The firewall rules applying the tags to traffic would need to be on the interface where traffic enters the firewall. So on LAN or some other internal interface.
And are you running any sort of DNS filtering like pfBlocker?
-
@stephenw10 hi
so i tested ya that pf blocker is causing Home Depot Search not to work right so i guess they block home depot search engine ips however that works.. i tested over a couple days now where i had it enabled and let it rest or just reconfigure on its own.. and and boom cant search home depot site .. i unblock it and in a few minutes i able to search on the home depot site.. so one of the ips shouldnt be blocked but dunno how you check thatas for the openvpn i have a few
so i have
WAN --- clients no vpn
PIA OpenVPN USA --- clients to use vpn
PIA OpenVPN Canada -- clients to use VPN
Site To Site OpenVPN -- connect to my sisters Pfsense constant connection
Remote Access OpenVPN -- to let me log into my network from my cell phone or laptopso firewall rules all i have is the No wan egreess so the PIA VPN cant go out the WAN connect
i do have the pfblocker off currently
and for DNS i set it to ALL All for inbound outbound..
and the LAN i have it set so the VPN Clients go out the PIA OpenVPN and the WAN go out the rest of the network..but even with that set on the PIA VPN side i get the isp or the other dns ips as you seen in the screen shot
now if there is other firewall routing i dont know them.. i only know how from the videos i posted..
-
You can look at the block logs in pfBlocker. It's probably a DNS entry rather than an IP that's blocked. Try disabling lists until it's accessible again.
-
@stephenw10 are the lists the items under Feeds? where there is white section some gray and green high lighted areas
if so i going to try to see if to disable them?