Nintendo Switch & Switch 2 - Needs static port on its outbound NAT
-
Just to confirm, making those changes did make it work for me.
Thanks again.sirjorj
-
Good advice jimp! I will purchase it this weekend
-
This worked for me like a charm for months. Yesterday I received a second DSL and setup a multi-wan. Got the usual error again. So I added the static NAT for the second WAN line as well and to ne safe added a firewall rule so that the console only uses the original first WAN.
Now sometimes it works and sometimes it does not. In the states diag I only see the first DSL being used. I am puzzled by this.
-
If your Multi-WAN setup is using Load Balancing, you might need to force the switch to a failover group instead so it is not balanced. It might be sending some traffic out WAN1, other traffic out WAN2, and since the far side sees different addresses it may be cutting that off.
-
Already did that… Quote: "added a firewall rule so that the console only uses the original first WAN. "
One day later everything seems to be fine. Maybe some missing old states.... Will monitor it...
-
These kind of posts are why I love this platform. I've never seen a platform where the actual people working on it post informational things like this for everyone to use.
Major kudos to the Pfsense team.
-
This worked for the Switch AND for the PS4 that had NAT type 3.
-
Sorry for reviving an old post but should I disable static ports on all other mappings? For example, the automatically created rules for localhost to WAN, LAN to WAN, OPT1 to WAN, etc.? I also have multiple game systems that require the static port on. Is it all right to have static ports on all of them ON at the same time? I'm still very new to pfSense (this is my post here, in fact!).
-
Thank you very much a very simple and elegant solution. You made my son very happy. I will be adding other console to help with gaming.
Thank Again. :)
-
Sorry for reviving an old post but should I disable static ports on all other mappings? For example, the automatically created rules for localhost to WAN, LAN to WAN, OPT1 to WAN, etc.? I also have multiple game systems that require the static port on. Is it all right to have static ports on all of them ON at the same time? I'm still very new to pfSense (this is my post here, in fact!).
As long as they do not need the same source port to talk with the same destination address:port it should be OK. There can only be one state for each local_wan_ip:port <-> remote_ip:port combination. Setting static port just means that the source port is left untranslated when connections are made outbound. If the local machine connects using source port 55000, then that port will be used on the WAN interface as the source port. Without static set, the port can be randomly selected from the ephemeral port space (1024 to 65535) and translated on WAN.
-
this solved my problem on both the wii u and switch. thank you!
-
Hi thank you for this guide. I had problems getting the NAT type from a D to a C or B even after following your steps but I eventually figured out what was happening.
In the step below, I found that the Mappings order was important. I originally added the rule as the last entry. When I moved the Mappings entry up above the other LAN entries I started getting NAT type B.
…
3. Add Outbound NAT rule
- Firewall > NAT, Outbound tab
- Click +
- Set the console address as the source (Type = Network, then enter the IP address, pick /32 for the CIDR)
- Check Static Port
- Save/Apply
...
-
Well, i did exactly this, but my switch still says its type D :(
Maybe someone sees anything I missed here: https://forum.pfsense.org/index.php?topic=141535.0
-
I posted this in a different thread by accident ….
having some trouble here - I'm getting the error Nintendo code:
error code: 2618-0516
NAT traversal process has failed
etc…I've attached the firewall/nat/outbound screen - have I missed anything?

-
I posted this in a different thread by accident ….
having some trouble here - I'm getting the error Nintendo code:
error code: 2618-0516
NAT traversal process has failed
etc…I've attached the firewall/nat/outbound screen - have I missed anything?
Looks like your NAT rule is set on the internal (LAN) interface when it should be on the WAN interface. Edit that rule, change it to WAN, Save, Apply.
-
Yes! ;D as simple as that. Just changed it to "WAN". Nothing else. Thank you very much for a helpful thread!!
-
At least with the one online multiplayer game I have used so far (Fast RMX) the only requirement for Nintendo Switch online multiplayer is static port outbound NAT. It did not appear to require UPnP, but it's safer to enable that in case another game needs it later.
So as with the Wii U, 3DS, and other similar consoles the best course of action is:
1. Set a static IP address for the device via DHCP static mappings
- Status > DHCP Leases, find the device, click + to add a mapping, set a static address, save, etc.
2. Switch to Hybrid Outbound NAT
- Firewall > NAT, Outbound tab
- Select Hybrid Outbound NAT, Save
3. Add Outbound NAT rule
- Firewall > NAT, Outbound tab
- Click +
- Set the console address as the source (Type = Network, then enter the IP address, pick /32 for the CIDR)
- Check Static Port
- Save/Apply
4. (Optional, So far) Enable UPnP & NAT-PMP
- Enable UPnP & NAT-PMP
- Allow UPnP Port Mapping
- Pick External (WAN) and Internal Interfaces (LAN)
- Set other options as desired
- Save
EDIT: My son is using the Splatoon pre-release global test fire and the online multiplayer is working fine, still only using static port outbound NAT. No UPnP.
THANK YOU!!!! For taking the time to outline this. Works perfect for the new Nintendo Switch in the house. Kids have been trying to play Splatoon 2 online and kept having issues until I found this.
Thanks again for helping a NOOB who loves pfSense!
-
Hey Dude,
Thanks a million for that post. I just spend my whole afternoon trying to get Splatoon 2 multiplayer working on my son's Nintendo Switch
After I found this post it worked in a flashTHANK YOU !!!
-
Please keep future posts in this thread related to the Nintendo Switch only, thanks!
I split off an tangent conversation into a new thread.
-
I'm not having any luck getting the NAT type to report anything other than type D
Hopefully I'm just missing something.. Here are my settings.
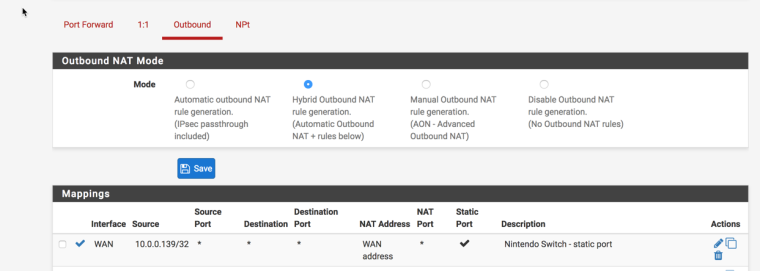
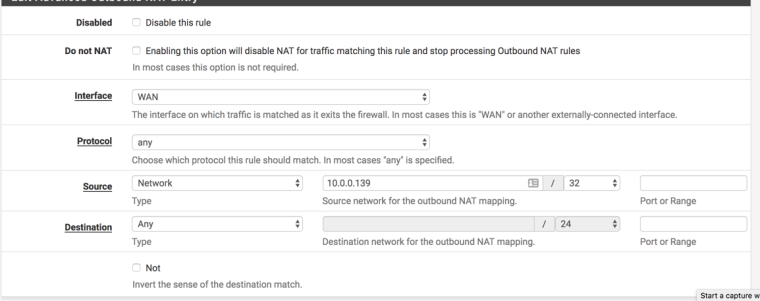
thanks