PfSense VLAN + switch tagging trunk questions
-
I have several VLANs setup on one interface that will be connected to one port on my HPE 1820 24g switch. Should this switch uplink to the pfsense interface be made a trunk on the HPE? Do we tag ports that will serve as trunk?
-
Yes the switch port should be a trunk connection to carry multiple VLANs.
You don't need to do anything in pfSense to mark it as trunk. The interface serving as the VLAN parent will always send the VLAN packets tagged.
Steve
-
This is probably a question for another forum but in which circumstances would I tag a port with multiple VLANs instead of trunking it? I can't seem to wrap my head around tagging vs trunking. To give an example I have a Ubiquiti AP that I have setup with 3 SSIDs (VLANs) . The switch interface is tagged with the three VLANs.This appears to work. Yet when I read Ubiquiti documentation, it says that I should be using a trunk between the switch and AP.
-
This is probably a question for another forum but in which circumstances would I tag a port with multiple VLANs instead of trunking it?
You don't. A port is either a trunk port or assigned to a VLAN (including native). About the only exception I know of is with Cisco switches and VoIP phones, where Cisco Discovery Protocol will recognize a phone and put it on a VLAN, while the port is assigned to another. Similar can happen with switches that can be configured to recognize MAC address prefixes, to put phones etc., on a VLAN.
-
Much of the confusion here is due to the different terminology and subtle differences in the way settings are applied between manufacturers.
The term trunk port or trunk connection is actually a Cisco term I believe but has come to be widely used to mean a link/port carrying tagged VLAN traffic, usually multiple VLANs but doesn't have to be.
I like to think of it like this, effectively there are three options for traffic on a VLAN leaving a switch port:
Tagged; the packet leaves the port with VLAN tags. Trunk port.
Untagged; the VLAN tags are stripped when the packet leaves the port. Access port. The PVID would almost always be set to that VLAN to re-tag the packets coming back in.
Excluded; packets from that VLAN are not permitted to leave via that port.
And indeed some switches mark the ports exactly like that which I always found the easiest to read. At least some HP switches are like that but lower end maybe…
It is better to avoid untagged and tagged traffic on the same link if you can. It's easy to make mistakes doing that. Some switches can behave unexpectedly. However it is valid.
The definitions between trunk port and access port blur when you have a port that is tagged on some VLANs but untagged on another.
They blur even further when you have multiple VLANs untagged on one port! Many (most?) switches won't allow that and it's of 'limited' use. ;)
My own exposure to different switches is limited, open to thoughts on that.
Steve
-
Thanks for your replies.
The 1820 web administration has a VLAN section to define the VLANs and configure the ports as tagged, untagged or excluded. What adds to the confusion is that the web administration also has a separate section for trunking.
More a question for HP, but if tagging = trunking, why can I apply a bunch of VLAN tags to a port in one section and then in a separate assign that port as a proper trunk? I would refer to a manual but the only one I can find is no help.
I've attached screenshots of the web adminstration GUI.


-
On HP tagging != trunking. Trunking is used for link aggregation. No need to touch that if you just need VLAN functionality.
-
Thanks Andy. I did a bit more digging and found that same answer too.
Cheers. -
…..and there's the confusion! ;)
But that's especially confusing. Good to know. Thanks.
Steve
-
@SR190 has anyone been able to resilve this as i have not been able to transport vlan traffic to tagged ports
Here is my setup
Port 48 goes to my pfsense firewall
Untagged vlan 1 by default on port 48
Vlan 11 tagged on port 48
Vlan 12 tagged on port 48
Vlan 13 tagged on port 48The switch model is hpe 1820-48G
-
Have you configured those VLANs on pfSense?
-
@JKnott yes all vlans are configured on pfsense.
-
Well, fire up wireshark, to see what's happening. Wireshark has a column for VLAN ID, but you have to enable it.
-
I assume you have those VLANs untagged on other ports on the switch where you testing connecting hosts to them?
-
@JKnott said in PfSense VLAN + switch tagging trunk questions:
Well, fire up wireshark, to see what's happening. Wireshark has a column for VLAN ID, but you have to enable it.
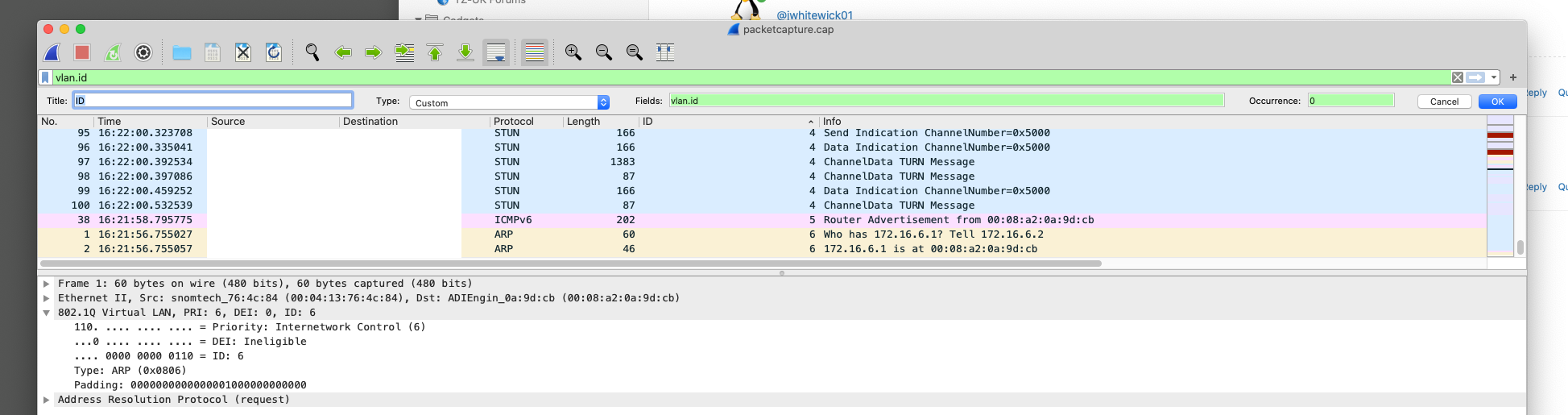
-
All I can see is there's no VLAN traffic at whatever point you're looking at. Are the VLANs configured on that interface? You'll have to do something to generate traffic on the VLANs, such as pinging a non-existent address. This will cause multiple ARP broadcasts, which give you something to watch for.
-
The ID column shows traffic tagged vlan 4, 5 & 6.
-
Sorry, my mistake. I haven't had my morning beer yet.

So, you have VLANs enabled on that switch. Is that traffic coming from the switch where you're monitoring or is it being received by it? With managed switches, you can test at each end and then see what happens. So, if you see those tagged frames coming in, are they being sent out on the appropriate port? I see STUN packets. That implies VoIP or perhaps games? Where is that port you're monitoring in relation to your Internet connection. Hopefully, you're not trying to send VLAN frames out to the Internet.
-
Yup vlan 4 is my IOT vlan and vlan 6 is VOIP, the screen shot was just to show @jwhitewick01 what to set as a column rule.
I did a capture on my pfsense parent interface.
-
Then why is VLAN4 showing a STUN packet? That should be on VLAN6. Is that packet incoming to pfSense? Or outgoing? I also see a router advertisement on there. I assume that MAC address matches the pfSense port and you don't another router out on VLAN5. And that 172.16.6.1 is pfSense on VLAN6. There is at least some communication between 172.16.6.2 and .1 Is that .2 on the correct VLAN?