NTP server remain in Soliciting pool server
-
Well then why does server X not respond to a ntp query when it comes from pfsense, but does respond when it comes from client behind pfsense? That is the million dollar question.
Since the source IP is the same. The clients are the same ntp version it looks like.
ntpd 4.2.8p11@1.3728-o
So I would suggest you set pfsense to use both your local ntp, and public ntp. It will now query both of them. Are you not seeing answers from the public ones? See my output below, you see pfsense syncs to my local stratum 1 ntp server I run. But it also asks pool as backup to if my local goes down (pi with gps as my ntp server). you will notice that they all show reach of 377.. Means talking to them and getting answers..
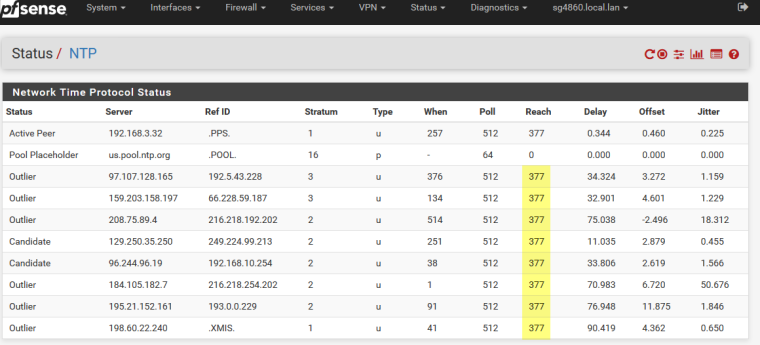
-
@johnpoz said in NTP server remain in Soliciting pool server:
Well then why does server X not respond to a ntp query when it comes from pfsense, but does respond when it comes from client behind pfsense? That is the million dollar question.
yes, pfsense box not respond to a ntp query but a client of pfsense box works.
I tried to configured local and public ntp server but public doesn't work as usual...
-
Makes ZERO sense... Really going to need a sniff on your outbound interface so we can see the ntp queries from your client behind pfsense and the queries from pfsense itself so we can try and figure out why the ones from pfsense do not get any responses.
I would suggest you sniff on your outbound interface for 123 udp with host of one of the public servers your client and pfsense are doing queries for.
Then download this and open in wireshark.. Maybe we can spot the difference in the queries that would explain why the server doesn't respond, or its possible maybe it is and its not getting back to you. I run a server in the pool.. So its open to the internet IPv4 and IPv6.. Let me send you the IP in a private chat - and set pfsense to use that server. And I can sniff on my wan to see if getting your query and if I send a response.
I will setup a sniff right now for your 80.x.x.x IP... Give me 2 seconds.
-
Ok I have sniff running for your IP on my wan udp 123... Set pfsense to use this IP and see if you get any responses or not.. Let me know after its been running a few minutes and I will stop the sniff and take a look
BTW: please do not post my full public IP its 64.53.x.x
-
Ok, some ntp packet sent to your ntp but without any response.
-
No nothing captured.. I never got those packets.
-
Not from that IP you say is your public IP. You sure pfsense is sending them out the right hole??
-
Since it seems now via chat you do have VIPs... How about you post your outbound nats so we can figure out what IP pfsense would use vs your clients when talking outbound.
-
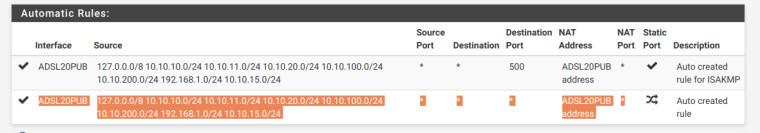
-
There are no hybrid rules above that? Or below that? From those your clients and pfsense itself would be using whatever the IP of ADSL20PUB is... Do you have other connections? What interfaces do you have your ntp set to use in the ntp setup page?
Do you have any port forwards setup on your client interfaces for ntp? (udp 123)
-
@johnpoz said in NTP server remain in Soliciting pool server:
There are no hybrid rules above that? Or below that?
No only Automatic outbound NAT rule generation.
Do you have other connections?
No, only ADSL20PUB, WAN is disabled
What interfaces do you have your ntp set to use in the ntp setup page?
all interfaces except ADSL20PUB
Do you have any port forwards setup on your client interfaces for ntp? (udp 123)
No, only 1:1 nat on virtual IP
-
well makes no sense at all then dude... I suggest you sniff on this adsl20pub interface with pfsense and clients doing ntp to same server so we can try and figure out what is going on.
From your outbound nat it would not be possible for your clients to be using any other IP other than adsl20pub interface. So how is it exactly you have VIPs setup?? Are they for inbound only traffic?
What I can tel you is I never saw an traffic from your IP o 123 UDP.. So if I never got it - its impossible for me to answer.
So your dong 1:1 nat, but you outbound nat to your adsl20pub... So if your on a client and you go to whatsmyip you see the adsl20pub IP??
Are you doing a 1:1 nat with this .234 IP?
Make sure your client that is working behind is pointing to a different ntp server than pfsense when you do your sniff so we can be sure of which traffic is what in the sniff.
-
@johnpoz said in NTP server remain in Soliciting pool server:
well makes no sense at all then dude...
yes...doesn't has sense at all.
So how is it exactly you have VIPs setup?? Are they for inbound only traffic?
only 3 web server (one for each VIP configured) with 80, 443 and 8080 port open
So your dong 1:1 nat, but you outbound nat to your adsl20pub... So if your on a client and you go to whatsmyip you see the adsl20pub IP?
my 1:1 natted server show VIP assigned on whatsmyip
normal client (as ntp server) show ADSL20PUB main address
juniper@kirk:~$ curl ipinfo.io/ip 80.19.236.234 -
pfsense box show:
[2.4.3-RELEASE][admin@pfsense.mkdevice.it]/root: curl ipinfo.io/ip 80.19.236.234 -
you do understand that ntp is going to bind to one of the IPs your listening on and use that for its queries right.. So that could be different when it goes outbound.. But if you have auto outbound nat then its should be the your adsl20pub IP.
Set your ntp server to use say 1.2.3.4 (some public ntp server) grab listing for your country on the ntp site. Set your client to use different public ntp server say 4.5.6.7... Then sniff on your adsl20pub interface for udp 123 and we should see these queries go out. We can then look at them in wireshark and try and figure out why queries pfsense is doing is not getting answered. My IP never saw queries from that 80.19.236.234 address that is for sure. And I get and answer 100's of ntp queries every few minutes My IP is member of ntp pool.
-
attached two trace, one of my ntp local server and one of pfsense box with the same server configured.