NTP server remain in Soliciting pool server
-
So your saying ntp works talking to your ntp server locally, but does not get answers remotely? But it not getting answers is related to what? How is an ntp server not answering something you clearly sent out pfsense issue? If it was something wrong with the query - then your local ntp server wouldn't answer it either.
Your local ntp server taking a different path to sync to outside, is it not syncing to outside?
-
my local ntp server reach internet through pfsense box and works fine, sync and serve.
pfsense box using my local ntp server works fine:
ntpq> readvar associd=0 status=0618 leap_none, sync_ntp, 1 event, no_sys_peer, version="ntpd 4.2.8p11@1.3728-o Wed Feb 28 13:29:50 UTC 2018 (1)", processor="amd64", system="FreeBSD/11.1-RELEASE-p10", leap=00, stratum=3, precision=-22, rootdelay=36.095, rootdisp=47.551, refid=10.10.11.2, reftime=deec69b4.f16fb644 Sun, Jul 8 2018 12:45:08.943, clock=deec69bf.29ca9dae Sun, Jul 8 2018 12:45:19.163, peer=44435, tc=6, mintc=3, offset=2.311372, frequency=3.350, sys_jitter=0.000000, clk_jitter=0.134, clk_wander=0.052ntpq> peers remote refid st t when poll reach delay offset jitter ============================================================================== 10.10.11.2 .POOL. 16 p - 64 0 0.000 0.000 0.000 *wpad.*****.** 193.204.114.105 2 u 35 64 377 0.145 2.311 0.049ntpq> as ind assid status conf reach auth condition last_event cnt =========================================================== 1 44434 8811 yes none none reject mobilize 1 2 44435 161a no yes none sys.peer sys_peer 1 -
Why would you have it marked pool when clearly its not?
So my question is does this ntp server take the same "path" to the internet that pfsense would take on its own? Or are you routing this traffic different pfsense local traffic would take - ie the default route/gateway?
You stated
i have only an internet interface that isn't WAN (now is disabled for migration reason
-
for pool configuration is just an oversight.
ntp server take the same path of pfsense (not WAN)
-
Well that makes zero sense - is the ntp server using the same servers you were trying to sync pfsense with?
You sure the ref time thing is not an issue. I don't recall every seeing such a ref time.. it is one of the rollover dates.. Now that your ntp is syncing and your time is good. What if you change to from your local server to external on pfsense?
So your saying that when you ntp server that is internal talks to the outside to sync its time its using the same bath and "the same source ip" as when pfsense itself goes out to the internet to talk to ntp. That 80.19.a.b address, your sure its not say 80.19.a.c ? or something like that?
Makes not sense that ntp server would answer your client, but not the client on pfsense?
What version of pfsense are you using? 2.4.3p1?
-
yes the same servers.
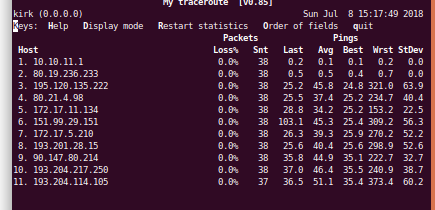
mtr from my local server:
mtr from my pfsense box
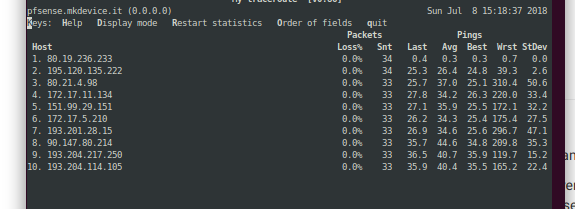
it's the same...
-
Not what I asked exactly... I asked if the source IP is the same..
While you might hit the same gateway that .233, maybe your coming from .A when natting your clients behind pfsense but pfsense is using .B as its IP. For example if you have a VIP setup when you have multiple IPs from the ISP..
You only have the 1 public IP, and no vips setup on pfsense where it could be using a different source IP.
Just makes no sense that your not getting any replies to your queries when pfsense does them, but do get replies when client behind pfsense does the query.
-
80.19.236.233 is my public router
80.19.236.234 is my pfsense public interface directly connected to 80.19.236.233
ntp internal server is 10.10.11.2 connected to pfsense 10.10.11.1
-
Well then why does server X not respond to a ntp query when it comes from pfsense, but does respond when it comes from client behind pfsense? That is the million dollar question.
Since the source IP is the same. The clients are the same ntp version it looks like.
ntpd 4.2.8p11@1.3728-o
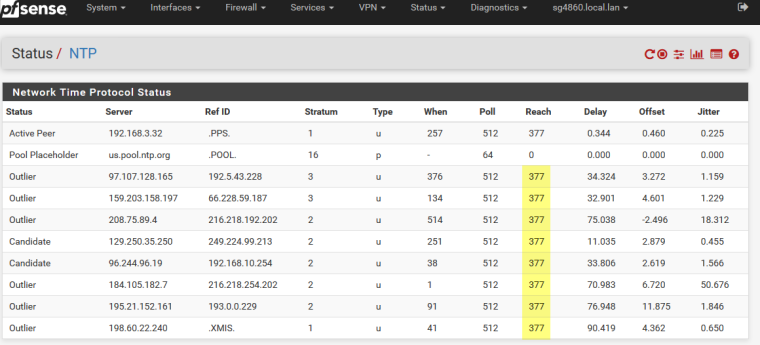
So I would suggest you set pfsense to use both your local ntp, and public ntp. It will now query both of them. Are you not seeing answers from the public ones? See my output below, you see pfsense syncs to my local stratum 1 ntp server I run. But it also asks pool as backup to if my local goes down (pi with gps as my ntp server). you will notice that they all show reach of 377.. Means talking to them and getting answers..
-
@johnpoz said in NTP server remain in Soliciting pool server:
Well then why does server X not respond to a ntp query when it comes from pfsense, but does respond when it comes from client behind pfsense? That is the million dollar question.
yes, pfsense box not respond to a ntp query but a client of pfsense box works.
I tried to configured local and public ntp server but public doesn't work as usual...
-
Makes ZERO sense... Really going to need a sniff on your outbound interface so we can see the ntp queries from your client behind pfsense and the queries from pfsense itself so we can try and figure out why the ones from pfsense do not get any responses.
I would suggest you sniff on your outbound interface for 123 udp with host of one of the public servers your client and pfsense are doing queries for.
Then download this and open in wireshark.. Maybe we can spot the difference in the queries that would explain why the server doesn't respond, or its possible maybe it is and its not getting back to you. I run a server in the pool.. So its open to the internet IPv4 and IPv6.. Let me send you the IP in a private chat - and set pfsense to use that server. And I can sniff on my wan to see if getting your query and if I send a response.
I will setup a sniff right now for your 80.x.x.x IP... Give me 2 seconds.
-
Ok I have sniff running for your IP on my wan udp 123... Set pfsense to use this IP and see if you get any responses or not.. Let me know after its been running a few minutes and I will stop the sniff and take a look
BTW: please do not post my full public IP its 64.53.x.x
-
Ok, some ntp packet sent to your ntp but without any response.
-
No nothing captured.. I never got those packets.
-
Not from that IP you say is your public IP. You sure pfsense is sending them out the right hole??
-
Since it seems now via chat you do have VIPs... How about you post your outbound nats so we can figure out what IP pfsense would use vs your clients when talking outbound.
-
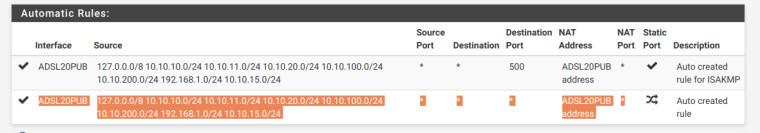
-
There are no hybrid rules above that? Or below that? From those your clients and pfsense itself would be using whatever the IP of ADSL20PUB is... Do you have other connections? What interfaces do you have your ntp set to use in the ntp setup page?
Do you have any port forwards setup on your client interfaces for ntp? (udp 123)
-
@johnpoz said in NTP server remain in Soliciting pool server:
There are no hybrid rules above that? Or below that?
No only Automatic outbound NAT rule generation.
Do you have other connections?
No, only ADSL20PUB, WAN is disabled
What interfaces do you have your ntp set to use in the ntp setup page?
all interfaces except ADSL20PUB
Do you have any port forwards setup on your client interfaces for ntp? (udp 123)
No, only 1:1 nat on virtual IP
-
well makes no sense at all then dude... I suggest you sniff on this adsl20pub interface with pfsense and clients doing ntp to same server so we can try and figure out what is going on.
From your outbound nat it would not be possible for your clients to be using any other IP other than adsl20pub interface. So how is it exactly you have VIPs setup?? Are they for inbound only traffic?
What I can tel you is I never saw an traffic from your IP o 123 UDP.. So if I never got it - its impossible for me to answer.
So your dong 1:1 nat, but you outbound nat to your adsl20pub... So if your on a client and you go to whatsmyip you see the adsl20pub IP??
Are you doing a 1:1 nat with this .234 IP?
Make sure your client that is working behind is pointing to a different ntp server than pfsense when you do your sniff so we can be sure of which traffic is what in the sniff.