Forwarding and ping from WAN dont work. (SOLVED)
-
This is how I understand those fields in NAT config page:
Destination - the address where traffic comes to
Destination port - the port of the address where traffic comes to
Redirect target IP - the address of NATed device, aka the IP that matches Destination address.
Redirect target port - the port of the address of NATed device, aka the port that matches Destination port.@NogBadTheBad Thanks for the SC, but its using same ports on both sides. All manuals and guides are doing this, so I could not double check which side is what, if my understanding of the labels are wrong!
-
@stefoo said in Forwarding and ping from WAN dont work.:
Also, VPN thing is too complicated to have on low technical device owners.
NONSENSE!!! Plain and simple... Your users so freaking stupid they can not click a button?

If you have users so freaking stupid they can not click a button to connect to a vpn, then they are too freaking stupid to have the phone in the first place.
it is no different then them connecting to freaking the camera interface.. They just need to click a vpn button first.
-
@johnpoz
)
I feel you mate!
Monkeys dont mind one button more, its me too laizy set up openvpns on their devices now.
But it will come to that at next stage.
Now I need to figure out just why my port forwarding is not working.Cheers.
-
Here is what I can tell you - in the 10+ years I have been here, I do not recall ever seeing an issue with port forwarding that was not PEBKAC...
The troubleshooting doc gives you all the info you need to find where your problem is in like 1 minute.
Sniff on the wan - does the traffic get there? Sniff on the interface on your lan side your wanting to send it out of - does it get sent? Do you get an answer from the client you sent the traffic too? Maybe he is sending back RST.. Maybe your sending it to the wrong IP, maybe its not even listening on the port your sending too, etc.
Typical problems is device doesn't even have a gateway - many an IP camera has zero support for a gateway - so no you can not talk to it from another network. So you have to source nat for that to work. Or if they do have gateway set - its to some other IP other than pfsense, etc.
If it takes you more than 1 minute to figure out where the problem is you need to step back, take a breath - maybe have a beer. Think for 2 seconds, read through the troubleshooting guide and follow the steps.. Pfsense can not forward what it never sees - so step 1 is ALWAYS validate traffic actually gets to pfsense on the port your trying to forward!!
-
You cannot ping or connect inbound sourced from the WAN address like that. It has to do with all of the route-to and reply-to that are placed on pfSense WAN interfaces by default.
This does not impact traffic coming in from the outside. Only traffic with the WAN address as the source address.
Port forwards will work fine even if that test fails.
-
@stefoo said in Forwarding and ping from WAN dont work.:
Monkeys dont mind one button more, its me too laizy set up openvpns on their devices now.
It are lazy and/or ignorant people who feed the botnet army of IoT devices.
Good luck getting all those IP cams cleaned afterwards (as well as all your client's network hosts). -
...just saw: External access to pfSense on port 80 (HTTP)
"Lazy" can't describe that ignorance, you're either mad or shining bright like a slice of bread. -
Thanks to everybody for contributing.
The original post was not related to security, but thanks for you concerns.
FYI, this is my second PFS box, the first one was with everything you say.@johnpoz I am not so experienced and more over with diagnosis.
I did a packet capture and found traffic is reaching internal IP. So it is not problem of forwarding.
I changed the forwarding to a Ubiquti device that has gateway. Again I cant open it, I am not reaching any login screen.
How should diagnose further? -
@stefoo said in Forwarding and ping from WAN dont work.:
I changed the forwarding to a Ubiquti device that has gateway
is this gateway pfsense? Do you not get an answer if you see pfsense forward the traffic..
For a forward to work, the dest box your forwarding too has to send the traffic back to the IP that forwarded it ;) you can not send your answer via some other gateway..
I am not reaching any login screen
You are actually testing this from OUTside right... You can not attempt to hit your wan IP from a box inside to be forwarded back inside and expect that to work without setting up NAT Reflection. You need to be validating your port forwards from external to pfsense. can you see me . org is great place to test if ports are open and reaching client your forwarding to and it answers..
Here I forwarded 22 to one of my unifi AP that is on 192.168.2.2
That took all of 30 seconds.
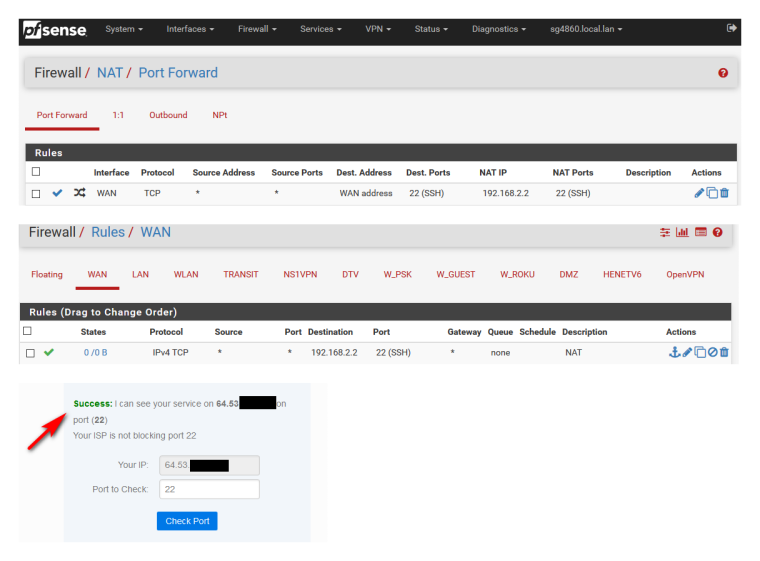
-
!!! This is again of those cases where something is tripping !!!
Yes, I am testing only from outside.
Here is my packet captureOn WAN
4:57:58.011987 IP 185.12.24.42.62203 > 57.237.109.180.8007: tcp 0
14:58:01.731203 IP 185.12.24.42.62219 > 57.237.109.180.8007: tcp 0
14:58:01.985091 IP 185.12.24.42.62224 > 57.237.109.180.8007: tcp 0On LAN
14:54:13.272152 IP 185.12.24.42.61019 > 192.168.100.7.80: tcp 0
14:54:13.272415 IP 192.168.100.7.80 > 185.12.24.42.61019: tcp 0
14:54:13.527480 IP 185.12.24.42.61028 > 192.168.100.7.80: tcp 0I used www.yougetsignal.com/tools/open-ports/ to check my open ports. It says port 8007 is not open, while I have those rules:
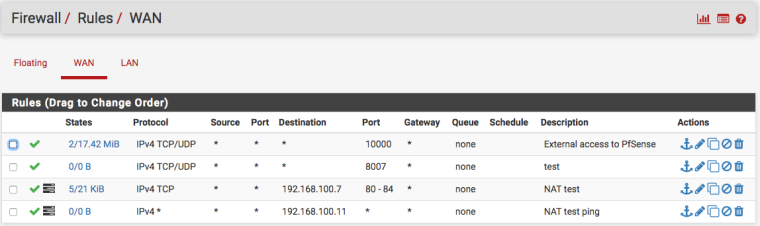
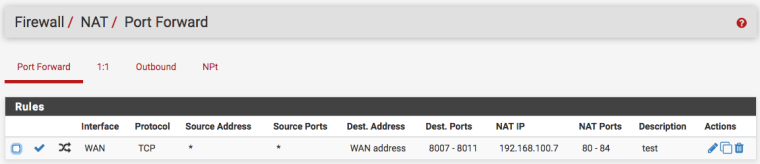
-
@stefoo said in Forwarding and ping from WAN dont work.:
14:54:13.272415 IP 192.168.100.7.80 > 185.12.24.42.61019: tcp 0
Your box your forwarding too clearly sends a response - what is this response? Is it a RST? Did that actually go back to pfsense IP (mac address?) open that sniff in wireshark
BTW your rules are WRONG... Just let your port forward create the rules...
They should look like this..
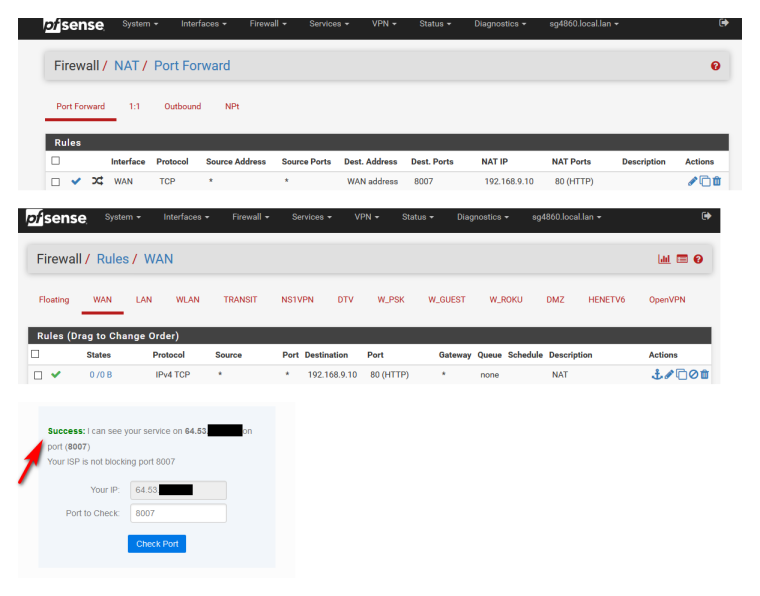
Why do you have that 8007 rule to any in there?
-
I added that rule just in case, otherwise I leave NAT create its rules.
I have a question. If a port is forwarded than is it closed? Because port open checker is reporting that port is closed while when sniffing when checker connects its obvious traffic gets trough.
@johnpoz I guess its not RST. Sorry, I am not good in reading captured packets.
WireShark on WAN
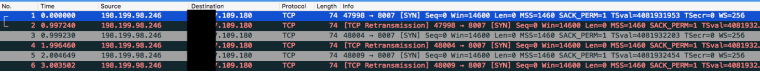
WhireShark on LAN
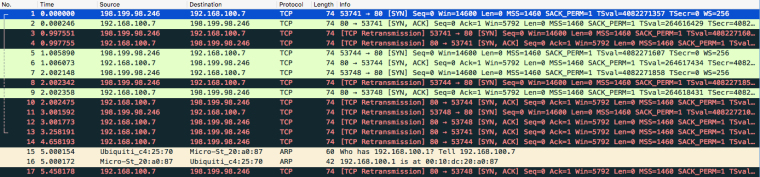
-
So from that your seeing syn,ack which is the proper answer to a syn - but its not going back out your wan..
Your taking those sniffs on pfsense lan interface.. And its sending it to pfsense lan mac - from that arp I assume pfsense lan IP is 192.168.100.1 with mac address 00:10:dc:20:a0:87
Do you have more than 1 wan? What are you rules on your lan? Are you using any sort of captive portal on the lan side?
What do you have for outbound nat?
Does this clients internet work? Can it go through pfsense for internet and that works? When you sniffed on wan did you limit that to IP or something. You sure pfsense not sending that traffic back out to your outside IP but didn't nat it - ie sending it out with the 192.168.100.7 address?
-
This post is deleted! -
IT WAS CAPTIVE PORTAL BLOCKING DEVICE TO WAN.
@johnpoz Next time I will take 3 beers. One is for you.
Thanks for helping. -
And PEBKAC strikes again ;) This is the root cause of all port forwarding issues...
-
I dont completely agree, although this CP has made me confused not once.
While forwarding is different case, because connection is established from outside, so CP should not ask devices for rights to respond.
Maybe I am wrong.
What got me confused was that ping from WAN.
Well! Now at least that PEBKAC can sniff and diagnose a bit better ;) -
That is number 9 of things to check here:
https://www.netgate.com/docs/pfsense/nat/port-forward-troubleshooting.html#common-problems
When I emphasize check (really check) everything there, this is what I am talking about.
It is invariably something on that list.
-
Hi,
Can I ask a bit of hinting about NAT reflection, I guess.
The case is ... I got the the forwarding to work ok. I got the DDNS to work with the forwarding ok. My ports are not 1:1, hence I forward 77 to 88.
But when I try to connect from the internal network by the domain:port it does not connect.
I guess its not connecting since the reflection is connecting to ports 77 while on the internal network services are on 88?
I tried to override that by playing with settings, but no luck.
So far have no idea what to search for to understand better the case.Thank you again for any comments and ofc your critique.
-
Nat reflection is ALWAYS the worse option to choose.. I don't understand why anyone would ever want to nat reflect..
if host.domain.tld is on the same network next to you - then why would you not just resolve host.domain.tld to that IP.. Why would you ever want to go to the public IP to be reflected back in??
As to forwarding port X to port Y.. That is always a work around in itself to all to go to the same service with the limitation of napt and only 1 public IP, etc.
If you want to go to host.domain.tld:port then go there where host.domain.tld resolves to the local IP and not the public ip..