VLAN issue
-
I created a VLAN with ID 50 on pfsense with LAN as its parent interface, re1.50. Created an interface called VLAN50 and gave it an ip 192.168.50.1. In the firewall below VLAN50, I created an allow ipv4 all for now. No outbound NAT has been configured, I just want to see VLAN 50 working for now and be able to ping pfsense from a host.
I am running a bunch of Unifi switches. Firmware is 3.9.54.9373, and Unifi software is version 5.9.29.
I read this thread as well:
https://forum.netgate.com/topic/135525/pfsense-with-unbiquiti-8-port-switch-and-vlansBasically, I created a network, vlan only, called vlan50 and id 50. Next I created a profile, vlan50 with native network vlan50.
I don't think its necessary, but I created a trunk profile with LAN and VLAN50 selected. The reason I don't think its necessary is because by default, the port config on the switches has all profiles selected so by default, all ports are trunks?
I created a VM under virtual box, with network bridged and created a enp0s3.50 vlan network as follows:
$ cat ifcfg-vlan50VLAN=yes TYPE=Vlan PHYSDEV=enp0s3 VLAN_ID=50 REORDER_HDR=yes GVRP=no MVRP=no PROXY_METHOD=none BROWSER_ONLY=no BOOTPROTO=none IPADDR=192.168.50.10 PREFIX=24 DEFROUTE=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=vlan50 UUID=3d4576d5-da57-4745-b909-3b3340a42d7c DEVICE=enp0s3.50 ONBOOT=yesInterfaces are up and I can ping my own ip address. Whatever else I ping, I get network is unreachable. I see nothing on pfsense with tcpdump.
When I ping pfsense on 192.168.50.1, I get destination host unreachable. On pfsense with tcpdump I see the following:
tcpdump -i re1.50 net 192.168.50.0/24 -vvv -nnntcpdump: listening on re1.50, link-type EN10MB (Ethernet), capture size 262144 bytes 13:12:08.750422 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.10, length 46 13:12:08.750447 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.50.1 is-at 00:01:2e:78:04:f5, length 28 13:12:09.752472 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.10, length 46 13:12:09.752495 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.50.1 is-at 00:01:2e:78:04:f5, length 28 13:12:10.754608 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.10, length 46 13:12:10.754633 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.50.1 is-at 00:01:2e:78:04:f5, length 28I've been at this for 2 days now reading and digging on the net, on these forums, on ubnt knowledgebase and how to's but I can't get it to work.
Any help would be greatly appreciated!
Thanks! -
Looks like pfSense is doing everything it is supposed to, as long as the re1 MAC address is 00:01:2e:78:04:f5.
Sorry. Can't help with the UBNT switch.
You might want to post your pfSense VLAN50 rules just to be sure there's not something silly done there (like TCP-only instead of protocol any).
-
Thanks, I should have mentioned that, that mac is from re1 interface.
The client config looks good right? So the problem would most likely be in the switch configs.
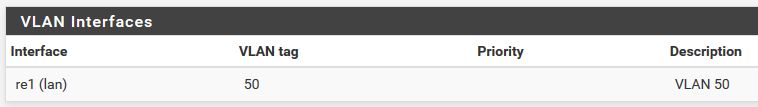
VLAN interface:
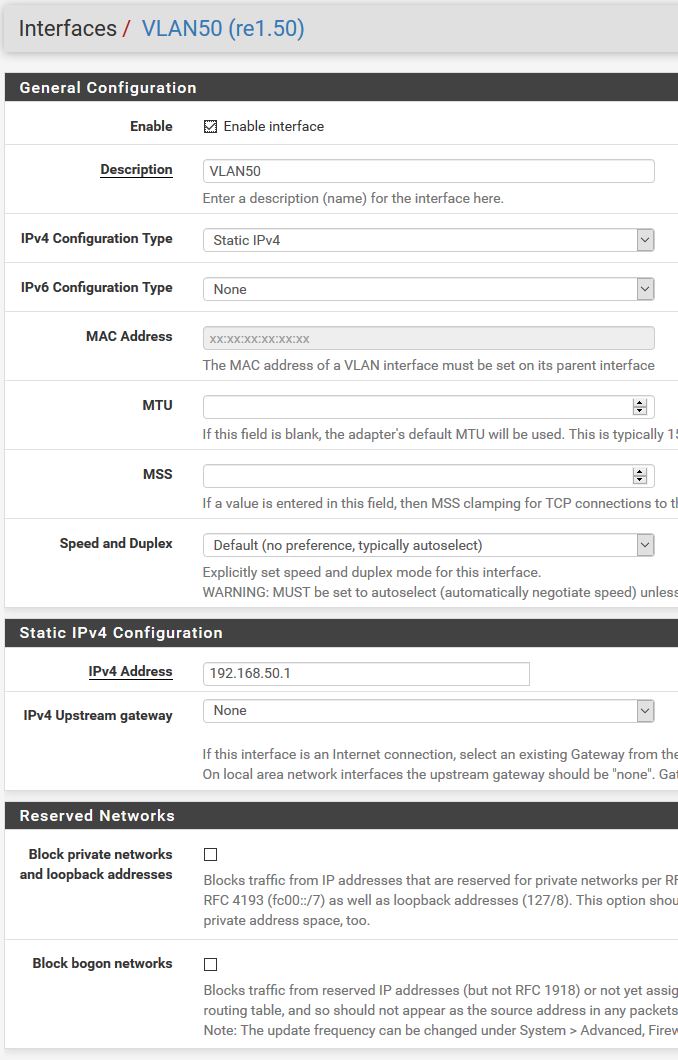
Interface config:
Firewall rule for vlan50:
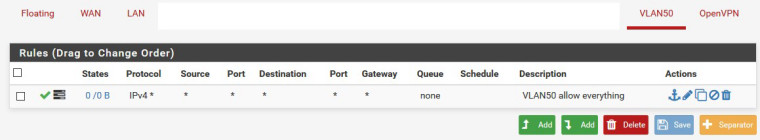 image url)
image url) -
The only thing I see that might be an issue is the netmask on the pfSense VLAN50 interface (since you cut it off and it matters). Other than that, I'd look at the other gear - either the switch or the virtualbox.
Sorry. I can't really speak to the client config since I don't use virtualbox ever. I can move this thread to virtualization if you like.
Since the ARP request is making it through to the firewall it looks like everything is OK at layer 2.
-
@derelict Thank you.
The netmask is /24.
I've posted on the ubnt forums too, can we leave this here for now? If it turns out my switches are oke too, we can move it if that's oke.
A tcpdump on the client shows some weirdness:
tcpdump: listening on enp0s3, link-type EN10MB (Ethernet), capture size 262144 bytes 14:39:41.930296 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.113, length 46 14:39:42.100801 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:42.205517 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.103, length 46 14:39:42.821884 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.1 (ff:ff:ff:ff:ff:ff) tell 172.16.10.156, length 46 14:39:42.928984 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.113, length 46 14:39:43.050400 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.114, length 46 14:39:43.103602 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:44.045721 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.114, length 46 14:39:44.087673 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.25 tell 172.16.10.162, length 46 14:39:44.087683 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.26 tell 172.16.10.162, length 46 14:39:44.105009 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:44.865275 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.25 tell 172.16.10.162, length 46 14:39:44.865284 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.26 tell 172.16.10.162, length 46 14:39:45.045539 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.114, length 46 14:39:45.865749 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.25 tell 172.16.10.162, length 46 14:39:45.865761 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.26 tell 172.16.10.162, length 46 14:39:46.103501 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:46.982038 IP (tos 0x0, ttl 64, id 6838, offset 0, flags [DF], proto UDP (17), length 323) 172.16.10.186.36682 > 172.16.10.255.21027: [udp sum ok] UDP, length 295 14:39:47.106551 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:48.084188 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.156, length 46 14:39:48.109377 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:49.084293 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.156, length 46 14:39:50.084301 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.156, length 46 14:39:50.104693 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:50.575609 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.104, length 46 14:39:50.812860 IP6 (hlim 255, next-header ICMPv6 (58) payload length: 152) fe80::201:2eff:fe78:4f5 > ff02::1: [icmp6 sum ok] ICMP6, router advertisement, length 152 hop limit 64, Flags [managed, other stateful], pref medium, router lifetime 60s, reachable time 0ms, retrans time 0ms prefix info option (3), length 32 (4): fd12:19f1:239f:3a6f::/64, Flags [onlink, auto, router], valid time 86400s, pref. time 14400s 0x0000: 40e0 0001 5180 0000 3840 0000 0000 fd12 0x0010: 19f1 239f 3a6f 0000 0000 0000 0000 route info option (24), length 24 (3): ::/0, pref=medium, lifetime=60s 0x0000: 0000 0000 003c 0000 0000 0000 0000 0000 0x0010: 0000 0000 0000 rdnss option (25), length 24 (3): lifetime 20s, addr: fd12:19f1:239f:3a6f::1 0x0000: 0000 0000 0014 fd12 19f1 239f 3a6f 0000 0x0010: 0000 0000 0001 dnssl option (31), length 40 (5): lifetime 20s, domain(s): internal.mydomain.com. 0x0000: 0000 0000 0014 0869 6e74 6572 6e61 6c0b 0x0010: 7072 6976 6174 6562 6974 7303 6e65 7400 0x0020: 0000 0000 0000 mtu option (5), length 8 (1): 1500 0x0000: 0000 0000 05dc source link-address option (1), length 8 (1): 00:01:2e:78:04:f5 0x0000: 0001 2e78 04f5 14:39:50.845458 IP6 (hlim 1, next-header UDP (17) payload length: 108) fe80::84f7:949b:9751:1baa.546 > ff02::1:2.547: [bad udp cksum 0xca92 -> 0x47f5!] dhcp6 solicit (xid=dd5f80 (client-ID type 4) (option-request DNS-server DNS-search-list DNS-server DNS-search-list client-ID) (elapsed-time 3415) (Client-FQDN) (IA_NA IAID:666206221 T1:3600 T2:5400)) 14:39:51.093836 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 330) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 302 14:39:51.106354 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:51.116226 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 377) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 349 14:39:51.144523 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 321) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 293 14:39:51.158795 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 385) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 357 14:39:51.180479 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 387) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 359 14:39:51.202432 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 375) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 347 14:39:51.225470 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 330) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 302 14:39:51.236811 IP (tos 0x10, ttl 128, id 0, offset 0, flags [none], proto UDP (17), length 328) 0.0.0.0.68 > 255.255.255.255.67: [udp sum ok] BOOTP/DHCP, Request from 08:00:27:b5:80:0d, length 300, xid 0x86373e17, secs 40, Flags [none] (0x0000) Client-Ethernet-Address 08:00:27:b5:80:0d Vendor-rfc1048 Extensions Magic Cookie 0x63825363 DHCP-Message Option 53, length 1: Discover Requested-IP Option 50, length 4: 172.16.10.196 Hostname Option 12, length 8: "centos01" Parameter-Request Option 55, length 18: Subnet-Mask, BR, Time-Zone, Classless-Static-Route Domain-Name, Domain-Name-Server, Hostname, YD YS, NTP, MTU, Option 119 Default-Gateway, Classless-Static-Route, Classless-Static-Route-Microsoft, Static-Route Option 252, NTP END Option 255, length 0 PAD Option 0, length 0, occurs 20 14:39:51.245543 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 377) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 349 14:39:51.267740 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 321) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 293 14:39:51.289074 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 385) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 357 14:39:51.310752 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 387) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 359 14:39:51.335803 IP (tos 0x0, ttl 2, id 0, offset 0, flags [DF], proto UDP (17), length 375) 172.16.10.187.1900 > 239.255.255.250.1900: [udp sum ok] UDP, length 347 14:39:51.575450 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.104, length 46 14:39:52.005551 IP (tos 0x0, ttl 128, id 32446, offset 0, flags [none], proto UDP (17), length 72) 172.16.10.162.57621 > 172.16.10.255.57621: [udp sum ok] UDP, length 44 14:39:52.108636 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:52.575684 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.104, length 46 14:39:53.488896 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.1 (ff:ff:ff:ff:ff:ff) tell 172.16.10.113, length 46 14:39:53.629994 IP (tos 0x0, ttl 128, id 32448, offset 0, flags [none], proto UDP (17), length 305) 172.16.10.162.63983 > 172.16.10.255.21027: [udp sum ok] UDP, length 277 14:39:53.630017 IP6 (flowlabel 0xdeb65, hlim 1, next-header UDP (17) payload length: 285) fe80::74ab:e9b5:eca0:7349.63982 > ff12::8384.21027: [udp sum ok] UDP, length 277 14:39:53.630043 IP6 (flowlabel 0xdeb65, hlim 1, next-header UDP (17) payload length: 285) fe80::74ab:e9b5:eca0:7349.63982 > ff12::8384.21027: [udp sum ok] UDP, length 277 14:39:53.630047 IP6 (flowlabel 0xdeb65, hlim 1, next-header UDP (17) payload length: 285) fe80::74ab:e9b5:eca0:7349.63982 > ff12::8384.21027: [udp sum ok] UDP, length 277 14:39:53.630051 IP6 (flowlabel 0xdeb65, hlim 1, next-header UDP (17) payload length: 285) fe80::74ab:e9b5:eca0:7349.63982 > ff12::8384.21027: [udp sum ok] UDP, length 277 14:39:53.630054 IP6 (flowlabel 0xdeb65, hlim 1, next-header UDP (17) payload length: 285) fe80::74ab:e9b5:eca0:7349.63982 > ff12::8384.21027: [udp sum ok] UDP, length 277 14:39:53.630132 IP6 (flowlabel 0xdeb65, hlim 1, next-header UDP (17) payload length: 285) fe80::74ab:e9b5:eca0:7349.63982 > ff12::8384.21027: [udp sum ok] UDP, length 277 14:39:53.700715 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.1 (ff:ff:ff:ff:ff:ff) tell 172.16.10.114, length 46 14:39:53.739636 LLDP, length 90 Chassis ID TLV (1), length 7 Subtype MAC address (4): f0:9f:c2:10:10:e1 0x0000: 04f0 9fc2 1010 e1 Port ID TLV (2), length 4 Subtype Local (7): 0/7 0x0000: 0730 2f37 Time to Live TLV (3), length 2: TTL 120s 0x0000: 0078 Port Description TLV (4), length 6: Port 7 0x0000: 506f 7274 2037 System Name TLV (5), length 15: switch-dinner 0x0000: 7377 6974 6368 2d65 6574 6b61 6d65 72 System Description TLV (6), length 36 USW-8P-150, 3.9.54.9373, Linux 3.6.5 0x0000: 5553 572d 3850 2d31 3530 2c20 332e 392e 0x0010: 3534 2e39 3337 332c 204c 696e 7578 2033 0x0020: 2e36 2e35 System Capabilities TLV (7), length 4 System Capabilities [Bridge] (0x0004) Enabled Capabilities [Bridge] (0x0004) 0x0000: 0004 0004 End TLV (0), length 0 14:39:54.110608 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:55.029515 IP (tos 0x0, ttl 4, id 13994, offset 0, flags [DF], proto UDP (17), length 542) 172.16.10.148.42009 > 239.255.255.250.1900: [udp sum ok] UDP, length 514 14:39:55.033736 IP (tos 0x0, ttl 4, id 13995, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.42009 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.036366 IP (tos 0x0, ttl 4, id 13996, offset 0, flags [DF], proto UDP (17), length 594) 172.16.10.148.42009 > 239.255.255.250.1900: [udp sum ok] UDP, length 566 14:39:55.038724 IP (tos 0x0, ttl 4, id 13997, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.44699 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.040659 IP (tos 0x0, ttl 4, id 13998, offset 0, flags [DF], proto UDP (17), length 598) 172.16.10.148.44699 > 239.255.255.250.1900: [udp sum ok] UDP, length 570 14:39:55.042674 IP (tos 0x0, ttl 4, id 13999, offset 0, flags [DF], proto UDP (17), length 596) 172.16.10.148.35323 > 239.255.255.250.1900: [udp sum ok] UDP, length 568 14:39:55.044116 IP (tos 0x0, ttl 4, id 14000, offset 0, flags [DF], proto UDP (17), length 608) 172.16.10.148.38867 > 239.255.255.250.1900: [udp sum ok] UDP, length 580 14:39:55.048468 IP (tos 0x0, ttl 4, id 14001, offset 0, flags [DF], proto UDP (17), length 606) 172.16.10.148.47675 > 239.255.255.250.1900: [udp sum ok] UDP, length 578 14:39:55.048487 IP (tos 0x0, ttl 4, id 14002, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.44073 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.050476 IP (tos 0x0, ttl 4, id 14003, offset 0, flags [DF], proto UDP (17), length 598) 172.16.10.148.44073 > 239.255.255.250.1900: [udp sum ok] UDP, length 570 14:39:55.052087 IP (tos 0x0, ttl 4, id 14004, offset 0, flags [DF], proto UDP (17), length 600) 172.16.10.148.54757 > 239.255.255.250.1900: [udp sum ok] UDP, length 572 14:39:55.054000 IP (tos 0x0, ttl 4, id 14005, offset 0, flags [DF], proto UDP (17), length 598) 172.16.10.148.54944 > 239.255.255.250.1900: [udp sum ok] UDP, length 570 14:39:55.055928 IP (tos 0x0, ttl 4, id 14006, offset 0, flags [DF], proto UDP (17), length 600) 172.16.10.148.44532 > 239.255.255.250.1900: [udp sum ok] UDP, length 572 14:39:55.060302 IP (tos 0x0, ttl 4, id 14007, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.46734 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.061447 IP (tos 0x0, ttl 4, id 14008, offset 0, flags [DF], proto UDP (17), length 594) 172.16.10.148.46734 > 239.255.255.250.1900: [udp sum ok] UDP, length 566 14:39:55.062719 IP (tos 0x0, ttl 4, id 14009, offset 0, flags [DF], proto UDP (17), length 606) 172.16.10.148.33746 > 239.255.255.250.1900: [udp sum ok] UDP, length 578 14:39:55.063827 IP (tos 0x0, ttl 4, id 14010, offset 0, flags [DF], proto UDP (17), length 608) 172.16.10.148.39098 > 239.255.255.250.1900: [udp sum ok] UDP, length 580 14:39:55.065059 IP (tos 0x0, ttl 4, id 14011, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.55489 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.066251 IP (tos 0x0, ttl 4, id 14012, offset 0, flags [DF], proto UDP (17), length 592) 172.16.10.148.55489 > 239.255.255.250.1900: [udp sum ok] UDP, length 564 14:39:55.067512 IP (tos 0x0, ttl 4, id 14013, offset 0, flags [DF], proto UDP (17), length 582) 172.16.10.148.40727 > 239.255.255.250.1900: [udp sum ok] UDP, length 554 14:39:55.112258 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:55.137680 IP (tos 0x0, ttl 4, id 14022, offset 0, flags [DF], proto UDP (17), length 542) 172.16.10.148.48085 > 239.255.255.250.1900: [udp sum ok] UDP, length 514 14:39:55.137702 IP (tos 0x0, ttl 4, id 14023, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.48085 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.140768 IP (tos 0x0, ttl 4, id 14024, offset 0, flags [DF], proto UDP (17), length 594) 172.16.10.148.48085 > 239.255.255.250.1900: [udp sum ok] UDP, length 566 14:39:55.141572 IP (tos 0x0, ttl 4, id 14025, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.44011 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.142718 IP (tos 0x0, ttl 4, id 14026, offset 0, flags [DF], proto UDP (17), length 598) 172.16.10.148.44011 > 239.255.255.250.1900: [udp sum ok] UDP, length 570 14:39:55.143835 IP (tos 0x0, ttl 4, id 14027, offset 0, flags [DF], proto UDP (17), length 596) 172.16.10.148.53804 > 239.255.255.250.1900: [udp sum ok] UDP, length 568 14:39:55.149332 IP (tos 0x0, ttl 4, id 14028, offset 0, flags [DF], proto UDP (17), length 608) 172.16.10.148.48237 > 239.255.255.250.1900: [udp sum ok] UDP, length 580 14:39:55.151837 IP (tos 0x0, ttl 4, id 14029, offset 0, flags [DF], proto UDP (17), length 606) 172.16.10.148.59330 > 239.255.255.250.1900: [udp sum ok] UDP, length 578 14:39:55.154954 IP (tos 0x0, ttl 4, id 14030, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.37272 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.159330 IP (tos 0x0, ttl 4, id 14031, offset 0, flags [DF], proto UDP (17), length 598) 172.16.10.148.37272 > 239.255.255.250.1900: [udp sum ok] UDP, length 570 14:39:55.161384 IP (tos 0x0, ttl 4, id 14032, offset 0, flags [DF], proto UDP (17), length 600) 172.16.10.148.48142 > 239.255.255.250.1900: [udp sum ok] UDP, length 572 14:39:55.163873 IP (tos 0x0, ttl 4, id 14033, offset 0, flags [DF], proto UDP (17), length 598) 172.16.10.148.34308 > 239.255.255.250.1900: [udp sum ok] UDP, length 570 14:39:55.165182 IP (tos 0x0, ttl 4, id 14034, offset 0, flags [DF], proto UDP (17), length 600) 172.16.10.148.33365 > 239.255.255.250.1900: [udp sum ok] UDP, length 572 14:39:55.166383 IP (tos 0x0, ttl 4, id 14035, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.48212 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.169097 IP (tos 0x0, ttl 4, id 14036, offset 0, flags [DF], proto UDP (17), length 594) 172.16.10.148.48212 > 239.255.255.250.1900: [udp sum ok] UDP, length 566 14:39:55.169106 IP (tos 0x0, ttl 4, id 14037, offset 0, flags [DF], proto UDP (17), length 606) 172.16.10.148.54962 > 239.255.255.250.1900: [udp sum ok] UDP, length 578 14:39:55.170284 IP (tos 0x0, ttl 4, id 14038, offset 0, flags [DF], proto UDP (17), length 608) 172.16.10.148.45418 > 239.255.255.250.1900: [udp sum ok] UDP, length 580 14:39:55.172449 IP (tos 0x0, ttl 4, id 14039, offset 0, flags [DF], proto UDP (17), length 551) 172.16.10.148.50282 > 239.255.255.250.1900: [udp sum ok] UDP, length 523 14:39:55.173034 IP (tos 0x0, ttl 4, id 14040, offset 0, flags [DF], proto UDP (17), length 592) 172.16.10.148.50282 > 239.255.255.250.1900: [udp sum ok] UDP, length 564 14:39:55.173960 IP (tos 0x0, ttl 4, id 14041, offset 0, flags [DF], proto UDP (17), length 582) 172.16.10.148.52523 > 239.255.255.250.1900: [udp sum ok] UDP, length 554 14:39:55.216924 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.103, length 46 14:39:55.952001 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.113, length 46 14:39:56.117870 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:56.217172 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.103, length 46 14:39:56.951549 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.113, length 46 14:39:57.217881 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.103, length 46 14:39:57.428221 IP (tos 0x0, ttl 64, id 28319, offset 0, flags [DF], proto UDP (17), length 72) 172.16.10.10.57621 > 172.16.10.255.57621: [udp sum ok] UDP, length 44 14:39:57.684851 IP6 (hlim 255, next-header ICMPv6 (58) payload length: 152) fe80::201:2eff:fe78:4f5 > ff02::1: [icmp6 sum ok] ICMP6, router advertisement, length 152 hop limit 64, Flags [managed, other stateful], pref medium, router lifetime 60s, reachable time 0ms, retrans time 0ms prefix info option (3), length 32 (4): fd12:19f1:239f:3a6f::/64, Flags [onlink, auto, router], valid time 86400s, pref. time 14400s 0x0000: 40e0 0001 5180 0000 3840 0000 0000 fd12 0x0010: 19f1 239f 3a6f 0000 0000 0000 0000 route info option (24), length 24 (3): ::/0, pref=medium, lifetime=60s 0x0000: 0000 0000 003c 0000 0000 0000 0000 0000 0x0010: 0000 0000 0000 rdnss option (25), length 24 (3): lifetime 20s, addr: fd12:19f1:239f:3a6f::1 0x0000: 0000 0000 0014 fd12 19f1 239f 3a6f 0000 0x0010: 0000 0000 0001 dnssl option (31), length 40 (5): lifetime 20s, domain(s): internal.mydomain.com. 0x0000: 0000 0000 0014 0869 6e74 6572 6e61 6c0b 0x0010: 7072 6976 6174 6562 6974 7303 6e65 7400 0x0020: 0000 0000 0000 mtu option (5), length 8 (1): 1500 0x0000: 0000 0000 05dc source link-address option (1), length 8 (1): 00:01:2e:78:04:f5 0x0000: 0001 2e78 04f5 14:39:57.951680 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.113, length 46 14:39:58.068151 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.114, length 46 14:39:58.125198 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:58.659466 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.1 (ff:ff:ff:ff:ff:ff) tell 172.16.10.103, length 46 14:39:59.068468 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.114, length 46 14:39:59.126840 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:39:59.309134 IP (tos 0x0, ttl 64, id 28448, offset 0, flags [DF], proto UDP (17), length 298) 172.16.10.10.53340 > 172.16.10.255.21027: [udp sum ok] UDP, length 270 14:40:00.068095 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 172.16.10.254 tell 172.16.10.114, length 46 14:40:00.129107 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:40:02.122090 IP6 (hlim 1, next-header Options (0) payload length: 56) :: > ff02::16: HBH (rtalert: 0x0000) (padn) [icmp6 sum ok] ICMP6, multicast listener report v2, 2 group record(s) [gaddr ff02::1:ff87:8782 to_in { }] [gaddr ff02::1:ff51:1baa to_ex { }] 14:40:02.129679 IP (tos 0x10, ttl 128, id 0, offset 0, flags [none], proto UDP (17), length 328) 0.0.0.0.68 > 255.255.255.255.67: [udp sum ok] BOOTP/DHCP, Request from 08:00:27:b5:80:0d, length 300, xid 0xb6f9e717, Flags [none] (0x0000) Client-Ethernet-Address 08:00:27:b5:80:0d Vendor-rfc1048 Extensions Magic Cookie 0x63825363 DHCP-Message Option 53, length 1: Discover Requested-IP Option 50, length 4: 172.16.10.196 Hostname Option 12, length 8: "centos01" Parameter-Request Option 55, length 18: Subnet-Mask, BR, Time-Zone, Classless-Static-Route Domain-Name, Domain-Name-Server, Hostname, YD YS, NTP, MTU, Option 119 Default-Gateway, Classless-Static-Route, Classless-Static-Route-Microsoft, Static-Route Option 252, NTP END Option 255, length 0 PAD Option 0, length 0, occurs 20 14:40:02.130587 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.50.1 tell 192.168.50.99, length 28 14:40:02.855660 IP6 (hlim 1, next-header Options (0) payload length: 56) :: > ff02::16: HBH (rtalert: 0x0000) (padn) [icmp6 sum ok] ICMP6, multicast listener report v2, 2 group record(s) [gaddr ff02::1:ff87:8782 to_in { }] [gaddr ff02::1:ff51:1baa to_ex { }] 14:40:02.986257 IP6 (hlim 255, next-header ICMPv6 (58) payload length: 24) :: > ff02::1:ff51:1baa: [icmp6 sum ok] ICMP6, neighbor solicitation, length 24, who has fe80::84f7:949b:9751:1baa ^C 119 packets captured 119 packets received by filter 0 packets dropped by kernelThanks again! Appreciate the help.
-
The problem was indeed in the switch config, I probably messed that up or something. With the help of the UBNT community I cleared the config and reconfigured it, now its working.
-
Thanks for letting us know.