IPv6 Native with Telstra, Australia
-
This post is deleted! -
My WAN interface has local IPv6: fe80::20c:29ff:fe05:a3a1
-
After further analysis, I think the key thing here is that Telstra appears to be responding validly, yet pfsense won't pick it up:
22:13:15.293243 4c:16:fc:2f:08:93 > 33:33:ff:05:a3:a1, ethertype IPv6 (0x86dd), length 96: (class 0xc0, hlim 255, next-header ICMPv6 (58) payload length: 32) 2001:8003:0:bdf:f0:3:9:0 > ff02::1:ff05:a3a1: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has fe80::20c:29ff:fe05:a3a1
-
Maybe check pfSense ICMP6 default rules in /tmp/debug.rules. If there is no rule allowing ICMP6 neighbour solicitation in on WAN interface 2001:8003:0:bdf:f0:3:9:0 then add such a rule.
(You could also verify this by checking Firewall log ... you should see the ICMP6 being blocked)
-
@dugeem Thanks for looking at this. I see no IPv6 traffic in my logs being dropped, and I've read that rules for IPv6 are auto created and no manual rules are required.
According to johnpoz "The icmpv6 rules that are required for IPv6 to work are allowed but hidden, just like dhcp is when you enable dhcp.. There is no need to worry about setting rules to allow the required stuff for IPv6 to function."
-
@Derelict Any ideas on this one? Basically pfsense won't accept Telstra's neighbor solicitation resulting in IPv6 not working on Australia's largest ISP. Other third party routers are working - just not pfsense. I have posted a heap of info above to help troubleshoot.
-
@johnpoz Same thing - if you've got any ideas on this one? Ta.
-
Set the DHCPv6 Debug Log flag on the WAN, and post the WHOLE DHCP logs filtering on command dhcp6c.
Post a screen shot of your Interfaces > WAN especially the DHCP6 section, not a textual representation.
You might also want to packet capture on WAN for DHCP6 traffic and post that capture file, not some textual representation of the same. dhcp6 traffic should be on UDP port 547.
Are they supposed to be delegating a /64, /60, /56, or /48?
What is the exact guidance Telstra gives for configuring your own DHCP6 router?
Since the typical settings don't work you need to find whatever secret sauce they require. You might also consider packet capturing a device that does work if Telstra can't tell you what they require.
-
I'll do this over multiple posts.
DHCP logs with debug on:
Feb 27 03:12:41 dhcp6c 52296 reset a timer on em0, state=SOLICIT, timeo=6, retrans=64469
Feb 27 03:12:41 dhcp6c 52296 send solicit to ff02::1:2%em0
Feb 27 03:12:41 dhcp6c 52296 set IA_PD
Feb 27 03:12:41 dhcp6c 52296 set IA_PD prefix
Feb 27 03:12:41 dhcp6c 52296 set option request (len 4)
Feb 27 03:12:41 dhcp6c 52296 set elapsed time (len 2)
Feb 27 03:12:41 dhcp6c 52296 set identity association
Feb 27 03:12:41 dhcp6c 52296 set client ID (len 14)
Feb 27 03:12:41 dhcp6c 52296 Sending Solicit
Feb 27 03:12:09 dhcp6c 52296 reset a timer on em0, state=SOLICIT, timeo=5, retrans=31928
Feb 27 03:12:09 dhcp6c 52296 send solicit to ff02::1:2%em0
Feb 27 03:12:09 dhcp6c 52296 set IA_PD
Feb 27 03:12:09 dhcp6c 52296 set IA_PD prefix
Feb 27 03:12:09 dhcp6c 52296 set option request (len 4)
Feb 27 03:12:09 dhcp6c 52296 set elapsed time (len 2)
Feb 27 03:12:09 dhcp6c 52296 set identity association
Feb 27 03:12:09 dhcp6c 52296 set client ID (len 14)
Feb 27 03:12:09 dhcp6c 52296 Sending Solicit
Feb 27 03:11:53 dhcp6c 52296 reset a timer on em0, state=SOLICIT, timeo=4, retrans=16326
Feb 27 03:11:53 dhcp6c 52296 send solicit to ff02::1:2%em0
Feb 27 03:11:53 dhcp6c 52296 set IA_PD
Feb 27 03:11:53 dhcp6c 52296 set IA_PD prefix
Feb 27 03:11:53 dhcp6c 52296 set option request (len 4)
Feb 27 03:11:53 dhcp6c 52296 set elapsed time (len 2)
Feb 27 03:11:53 dhcp6c 52296 set identity association
Feb 27 03:11:53 dhcp6c 52296 set client ID (len 14)
Feb 27 03:11:53 dhcp6c 52296 Sending Solicit
@derelict said in IPv6 Native with Telstra, Australia:
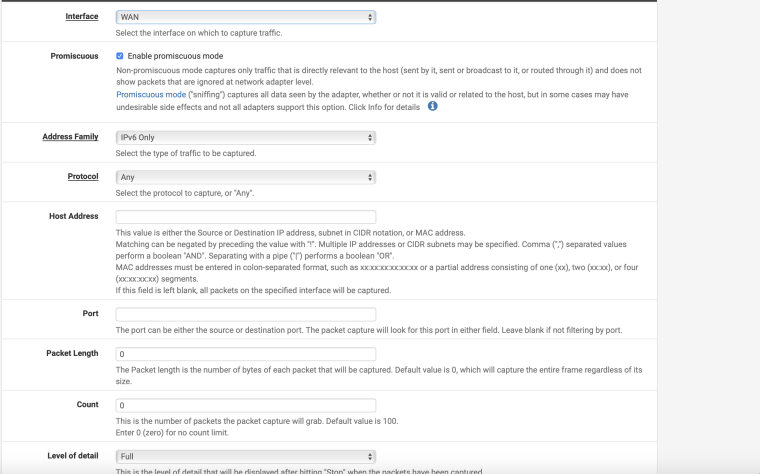
Ugh. Yes they do. Look at the packet capture settings again.
To avoid any confusion, I have even simplified my packet capture settings. here they are:
-
Here is the total information I have received from Telstra to date.
Telstra uses Ipv6 PD /56 via dhcpv6.
This is Native Ipv6 in a dual ipv4/ipv6 stack enviroment, no tunnel broker or 6rd.
Telstra's supported router uses DHCPv6 and get a PD (prefix delegation) back, it will then assign the addresses to LAN clients.
This means while the Telstra router may show it doesn't have a ipv6 address, It's still handing out PD ipv6 addresses to clients.I can see it sending Ipv6 DHCPv6
13:30:59.553687 In
Juniper PCAP Flags [no-L2, In]
-----original packet-----
PFE proto 6 (ipv6): (hlim 1, next-header: UDP (17), length: 146) fe80::20c:29ff:fe05:a3a1.dhcpv6-server > ff02::1:2.dhcpv6-server: [udp sum ok] dhcp6 Relay-forwardIt’s also unable to establish Ipv6 neighbours which I suspect is a reason why it’s not functioning correctly
13:31:01.106029 In
Juniper PCAP Flags [no-L2, In]
-----original packet-----
PFE proto 6 (ipv6): (hlim 255, next-header: ICMPv6 (58), length: 32) fe80::20c:29ff:fe05:a3a1 > ff02::1:ff2f:893: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has fe80::4e16:fcff:fe2f:893
source link-address option (1), length 8 (1): 00:0c:29:05:a3:a1
0x0000: 000c 2905 a3a113:31:02.073018 Out
Juniper PCAP Flags [no-L2]
-----original packet-----
PFE proto 6 (ipv6): (class 0xc0, hlim 255, next-header: ICMPv6 (58), length: 32) 2001:8003:0:bdf:f0:3:9:0 > ff02::1:ff05:a3a1: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has fe80::20c:29ff:fe05:a3a1
source link-address option (1), length 8 (1): 4c:16:fc:2f:08:93
0x0000: 4c16 fc2f 0893 -
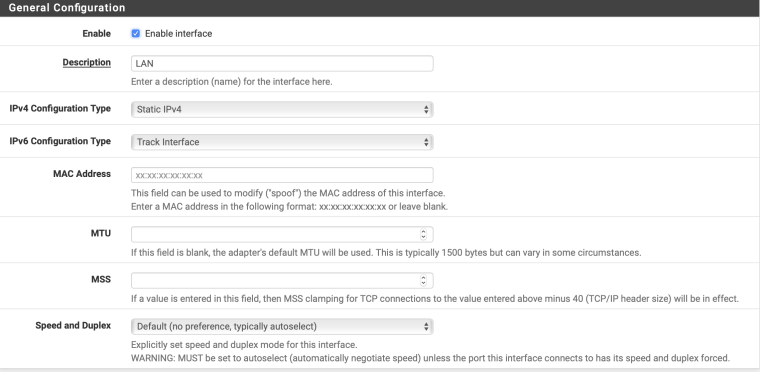
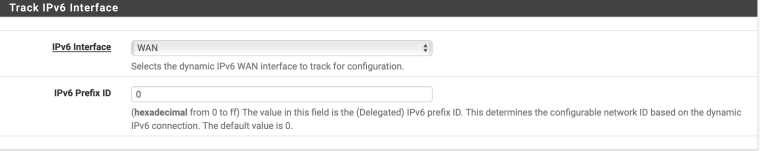
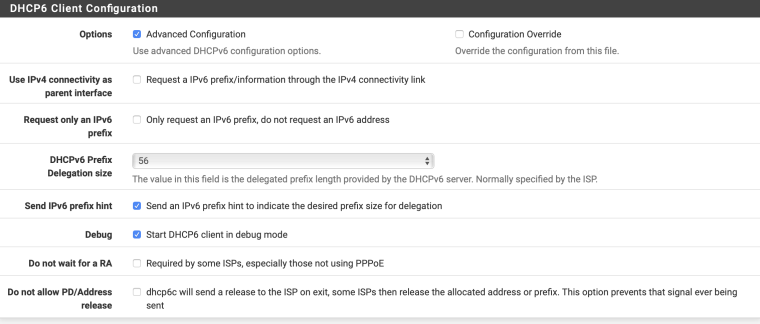
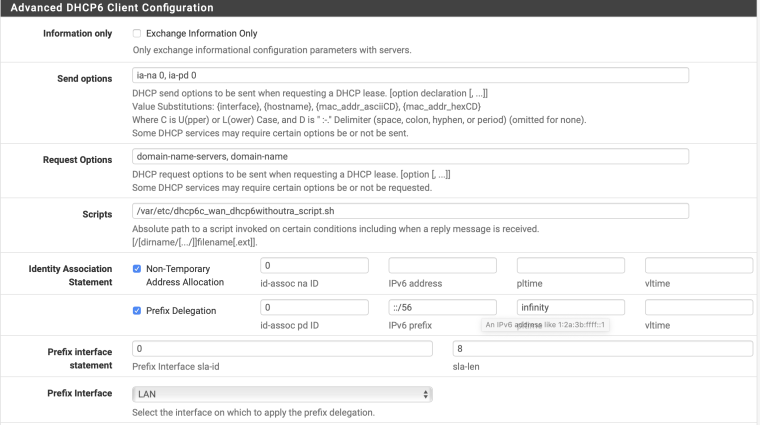
What's with all that advanced configuration? Especially setting LAN as the PD interface. Is that you stabbing in the dark with your fingers crossed?
Feb 26 08:17:55 dhcp6c 79587 reset a timer on igb1, state=INIT, timeo=0, retrans=891 Feb 26 08:17:56 dhcp6c 79587 Sending Solicit Feb 26 08:17:56 dhcp6c 79587 a new XID (781bad) is generated Feb 26 08:17:56 dhcp6c 79587 set client ID (len 14) Feb 26 08:17:56 dhcp6c 79587 set identity association Feb 26 08:17:56 dhcp6c 79587 set elapsed time (len 2) Feb 26 08:17:56 dhcp6c 79587 set option request (len 4) Feb 26 08:17:56 dhcp6c 79587 set IA_PD prefix Feb 26 08:17:56 dhcp6c 79587 set IA_PD Feb 26 08:17:56 dhcp6c 79587 send solicit to ff02::1:2%igb1 Feb 26 08:17:56 dhcp6c 79587 reset a timer on igb1, state=SOLICIT, timeo=0, retrans=1091 Feb 26 08:17:56 dhcp6c 79587 receive advertise from fe80::2e86:d2ff:fe89:2019%igb1 on igb1 Feb 26 08:17:56 dhcp6c 79587 get DHCP option client ID, len 14 Feb 26 08:17:56 dhcp6c 79587 DUID: 00:ff:ee:dd:cc:09:0f:68:00:08:a2:0a:59:41 Feb 26 08:17:56 dhcp6c 79587 get DHCP option server ID, len 14 Feb 26 08:17:56 dhcp6c 79587 DUID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c Feb 26 08:17:56 dhcp6c 79587 get DHCP option DNS, len 32 Feb 26 08:17:56 dhcp6c 79587 get DHCP option identity association, len 40 Feb 26 08:17:56 dhcp6c 79587 IA_NA: ID=0, T1=43200, T2=69120 Feb 26 08:17:56 dhcp6c 79587 get DHCP option IA address, len 24 Feb 26 08:17:56 dhcp6c 79587 IA_NA address: 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb pltime=86400 vltime=86400 Feb 26 08:17:56 dhcp6c 79587 get DHCP option IA_PD, len 41 Feb 26 08:17:56 dhcp6c 79587 IA_PD: ID=0, T1=43200, T2=69120 Feb 26 08:17:56 dhcp6c 79587 get DHCP option IA_PD prefix, len 25 Feb 26 08:17:56 dhcp6c 79587 IA_PD prefix: 2600:aaaa:ccc:ab00::/56 pltime=86400 vltime=86400 Feb 26 08:17:56 dhcp6c 79587 server ID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c, pref=-1 Feb 26 08:17:56 dhcp6c 79587 reset timer for igb1 to 0.973168 Feb 26 08:17:57 dhcp6c 79587 picked a server (ID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c) Feb 26 08:17:57 dhcp6c 79587 Sending Request Feb 26 08:17:57 dhcp6c 79587 a new XID (804c2e) is generated Feb 26 08:17:57 dhcp6c 79587 set client ID (len 14) Feb 26 08:17:57 dhcp6c 79587 set server ID (len 14) Feb 26 08:17:57 dhcp6c 79587 set IA address Feb 26 08:17:57 dhcp6c 79587 set identity association Feb 26 08:17:57 dhcp6c 79587 set elapsed time (len 2) Feb 26 08:17:57 dhcp6c 79587 set option request (len 4) Feb 26 08:17:57 dhcp6c 79587 set IA_PD prefix Feb 26 08:17:57 dhcp6c 79587 set IA_PD Feb 26 08:17:57 dhcp6c 79587 send request to ff02::1:2%igb1 Feb 26 08:17:57 dhcp6c 79587 reset a timer on igb1, state=REQUEST, timeo=0, retrans=909 Feb 26 08:17:57 dhcp6c 79587 receive reply from fe80::2e86:d2ff:fe89:2019%igb1 on igb1 Feb 26 08:17:57 dhcp6c 79587 get DHCP option client ID, len 14 Feb 26 08:17:57 dhcp6c 79587 DUID: 00:ff:ee:dd:cc:09:0f:68:00:08:a2:0a:59:41 Feb 26 08:17:57 dhcp6c 79587 get DHCP option server ID, len 14 Feb 26 08:17:57 dhcp6c 79587 DUID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c Feb 26 08:17:57 dhcp6c 79587 get DHCP option DNS, len 32 Feb 26 08:17:57 dhcp6c 79587 get DHCP option identity association, len 46 Feb 26 08:17:57 dhcp6c 79587 IA_NA: ID=0, T1=43200, T2=69120 Feb 26 08:17:57 dhcp6c 79587 get DHCP option status code, len 2 Feb 26 08:17:57 dhcp6c 79587 status code: success Feb 26 08:17:57 dhcp6c 79587 get DHCP option IA address, len 24 Feb 26 08:17:57 dhcp6c 79587 IA_NA address: 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb pltime=86400 vltime=86400 Feb 26 08:17:57 dhcp6c 79587 get DHCP option IA_PD, len 47 Feb 26 08:17:57 dhcp6c 79587 IA_PD: ID=0, T1=43200, T2=69120 Feb 26 08:17:57 dhcp6c 79587 get DHCP option status code, len 2 Feb 26 08:17:57 dhcp6c 79587 status code: success Feb 26 08:17:57 dhcp6c 79587 get DHCP option IA_PD prefix, len 25 Feb 26 08:17:57 dhcp6c 79587 IA_PD prefix: 2600:aaaa:ccc:ab00::/56 pltime=86400 vltime=86400 Feb 26 08:17:57 dhcp6c 79587 dhcp6c Received REQUEST Feb 26 08:17:57 dhcp6c 79587 nameserver[0] 2001:578:3f::30 Feb 26 08:17:57 dhcp6c 79587 nameserver[1] 2001:578:3f:1::30 Feb 26 08:17:57 dhcp6c 79587 make an IA: PD-0 Feb 26 08:17:57 dhcp6c 79587 status code for PD-0: success Feb 26 08:17:57 dhcp6c 79587 create a prefix 2600:aaaa:ccc:ab00::/56 pltime=86400, vltime=86400 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab01:208:a2ff:fe0a:593f/64 on lagg0.223 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab02:208:a2ff:fe0a:593f/64 on lagg0.999 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab03:208:a2ff:fe0a:593f/64 on lagg0.1003 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab10:208:a2ff:fe0a:593f/64 on lagg0.1004 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab04:208:a2ff:fe0a:593f/64 on lagg0.224 Feb 26 08:17:57 dhcp6c 79587 make an IA: NA-0 Feb 26 08:17:57 dhcp6c 79587 status code for NA-0: success Feb 26 08:17:57 dhcp6c 79587 create an address 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb pltime=86400, vltime=11447309925244555648 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb/128 on igb1 Feb 26 08:17:57 dhcp6c 79587 executes /var/etc/dhcp6c_wan_script.sh Feb 26 08:19:06 dhcp6c dhcp6c REQUEST on igb1 - running rc.newwanipv6 Feb 26 08:19:06 dhcp6c 79587 script "/var/etc/dhcp6c_wan_script.sh" terminated Feb 26 08:19:06 dhcp6c 79587 removing an event on igb1, state=REQUEST Feb 26 08:19:06 dhcp6c 79587 removing server (ID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c) Feb 26 08:19:06 dhcp6c 79587 got an expected reply, sleeping.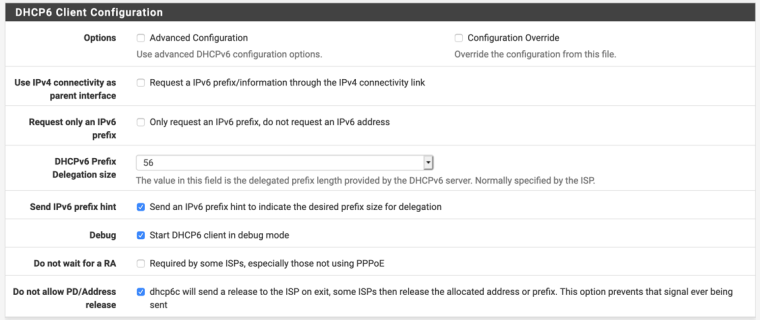
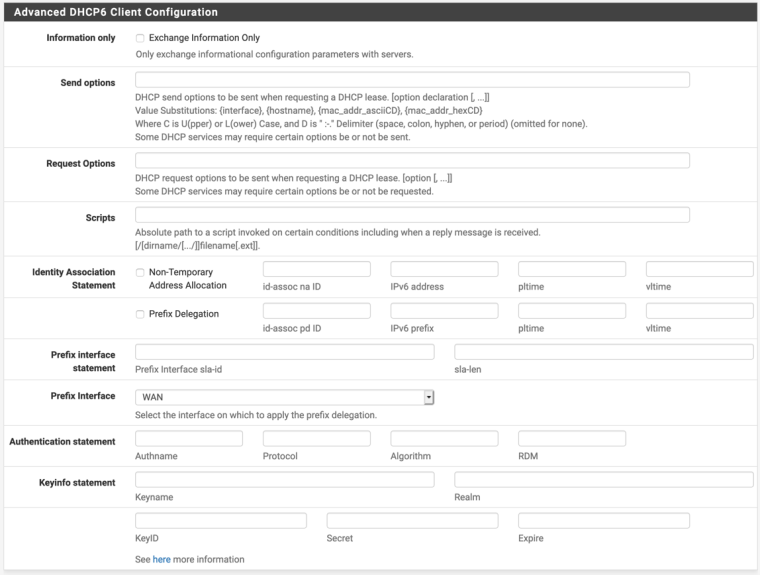
And if I do check advanced configuration to view it:
-
-
@derelict said in IPv6 Native with Telstra, Australia:
What's with all that advanced configuration? Especially setting LAN as the PD interface. Is that you stabbing in the dark with your fingers crossed?
It's me following other ISP implementations where people have said its close to how Telstra work. That said, you are right - its me stabbing in the dark trying to get it to work. I am reading info on how other 3rd party routers have got theirs up and running with Telstra and trying to translate that into pfsense. But long and short - its flying darts blind folded.
-
I would get rid of all of that and start over with basically what I have there and start the information gathering and pasting evolution over again.
No need to fly blind with actual information from the ISP and an ISP willing to help.
-
So I now have the config you posted above. Results below. I would also say the ISP doesn't know a thing about pfsense, so not sure how much help they will be to us. That said, the guy does respond to me if I have specific questions.
Here is the debug DHCP log with the config you suggested above:
Feb 27 03:43:11 dhcp6c 17859 reset a timer on em0, state=SOLICIT, timeo=3, retrans=8065
Feb 27 03:43:11 dhcp6c 17859 send solicit to ff02::1:2%em0
Feb 27 03:43:11 dhcp6c 17859 set IA_PD
Feb 27 03:43:11 dhcp6c 17859 set IA_PD prefix
Feb 27 03:43:11 dhcp6c 17859 set option request (len 4)
Feb 27 03:43:11 dhcp6c 17859 set elapsed time (len 2)
Feb 27 03:43:11 dhcp6c 17859 set identity association
Feb 27 03:43:11 dhcp6c 17859 set client ID (len 14)
Feb 27 03:43:11 dhcp6c 17859 Sending Solicit -
@derelict Here is the new packet capture from the settings you told me to implement:
-
@derelict Interestingly, zero UDP packets in the packet captures. All ICMP neighbor solicitation.
-
@derelict Also, no idea how to packet capture their router doing DHCPv6 negotiation. Their router plugs straight into the IPoE interface and I don't have a hub where I can plug wireshark or anything like that to capture packets. Any ideas welcome on how to achieve that. Their router also has custom firmware so no ability to packet capture off of it. I can check their limited logs, but that's about it. Let me know if you want me to that.
-
-
They do not have to know anything about pfSense. They should be able to tell you what is required of ANY dhcp6 client to pull an address and PD. Then we just make pfSense do what they require instead of guessing.