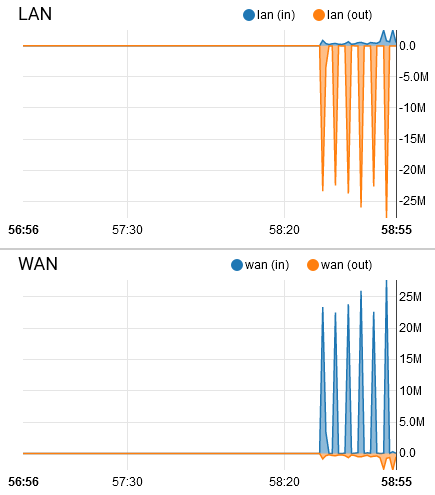
I have no idea whos causing this traffic....
-
Also if you go to just the traffic graph section.. You might catch the burst being listed, and what local IP is involved.. But sniff be easier to be honest.
Other options looking via the iftop package or the darkstat package to see who is generating traffic.
And concur such bursting does seem like some sort of streaming going on - I see such patterns when clients streaming from my plex..
-
Graph section ? Packet sniffing ? These options are in the GUI, right in front of our nose.
Because Cool_corona asked the question, he wasn't using these for reasons.Two more solutions : one with the GUI involved, and one that needs a pair of baskets ....
First approach :
Place 2 firewall rules on my LAN.
The first contains an alias, used as a Source, Destination and protocol is set to any. Init the alias with all the IP's used on the LAN network.
The second rule is any to any block rule a block rule.Check that the spikes are there.
Now, remove an LAN IP from the alias.
Check again - if the spikes are gone, you found the IP. If not, remove another IP from the alias.With the IP, locate the device. Locate the owner of the device. Have a chat.
Second approach :
Even more easier : disconnect physically all LAN devices, and while the spikes are not there, hook them back up one by one. Tip : locate a switch, all the cables are there.
As soon as the spikes come back, you have the device by it's "tail". -
@Gertjan said in I have no idea whos causing this traffic....:
Second approach :
Even more easier : disconnect physically all LAN devices,While that can work sure - I wouldn't call it easier ;) Seems like a lot of work to me - compared to just simple sniff.. hehehe Unless your goal is to get up out of your chair.. Which could be good thing ;)
All valid methods of how to skin this specific cat ;)
Other methods, firewall rule is option I didn't think of actually.. would show you where the traffic is going as well which could be insightful in figuring out what exactly the traffic is.
-
@johnpoz said in I have no idea whos causing this traffic....:
All valid methods of how to skin this specific cat ;)
CAT 6?

-
@Cool_Corona , Decoy network?
-
-
@Cool_Corona said in I have no idea whos causing this traffic....:
Any ideas?
L3 switch + mirror port and / or SPAN protocol is your good friend, if you want to get a detailed picture
-
While sure he could view the traffic via a span port.. There really is no need, just diagnostic menu packet capture will allow him to do a sniff and see the traffic flow through pfsense to figure out what IP is involved and where it going.
-
@johnpoz said in I have no idea whos causing this traffic....:
just diagnostic menu packet capture
Sorry, I was thinking about Wireshark (it was missed), plus what was described above.
Personally, I like it better as packet capture in pfsense tool+++edit:
much more configurable and detailed -
You understand you can just download whatever the packet capture captures into wireshark right? Just click the download button ;) And then open it up with wireshark or whatever your fav tool is..
A pcap is a pcap ;) While true the gui interface doesn't really show you a lot of detail on the capture. but if all he is really interested is the IP causing the traffic and what port its talking to - the gui would provide that info for sure. You can also always up the level displayed - but yeah I pretty much always download the pcap into wireshark when want to analyze some sniff.
-
@johnpoz said in I have no idea whos causing this traffic....:
You understand you can just download whatever the packet capture captures into wireshark right?
I agree with you, I may just be used to clicking the Wireshark icon and the SPAN VLAN is connected anyway.
I handle multiple things on multiple networks and it’s that simple..if don't need deep investigation the pfSense GUI is enough
-
@DaddyGo said in I have no idea whos causing this traffic....:
Sorry, I was thinking about Wireshark (it was missed), plus what was described above.
Personally, I like it better as packet capture in pfsense toolI mentioned Packet Capture. I also prefer Wireshark, but it won't run on pfsense, so either you run it on a computer that can see the traffic or use Packet Capture and download to Wireshark. If you have a managed switch, you can set up port mirroring to watch the desired connection, at least on the LAN side.
-
It's also possible to do remote capture.
Wireshark connects to pfSense over SSH in that case. -
I used to do that, when I had a Linux firewall. However, it's not possible to run it on pfsense, IIRC.
-
@JKnott said in I have no idea whos causing this traffic....:
I also prefer Wireshark, but it won't run on pfsense, so either you run it on a computer that can see the traffic or use Packet Capture
I agree with you too

so I wrote the L3 switch (above) + mirror port
(even on a smaller network, it’s worth just keeping one in your desktop drawer for testing)we use SPAN VLAN on the Cisco network and we are testing here with Wireshark
(I got used to it and simple method)I don't like TP-Link, but for a mobile test device it fits a lot (we use it :-)) TL-SG105E, it knows the port mirroring and thats all
-
My bet is someone streaming off plex ;) or something similar - there is another thread about graphs showing double - and the @Cool_Corona posted image looks exactly like how plex can stream data to a client..
Here is mine that I just used for image in that other thread.
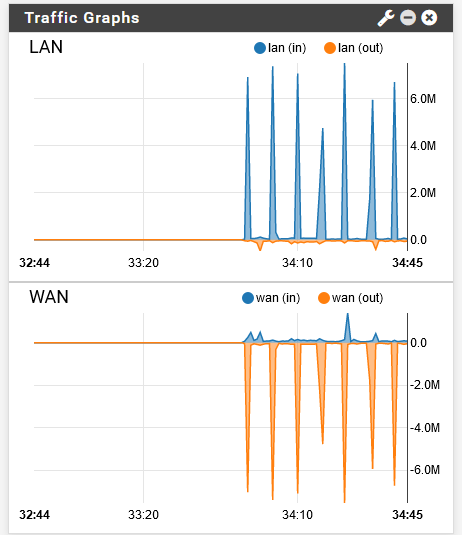
While someone streaming off my plex, lower data rates is all - he prob has higher bitrate movies on his ;)
Here is plex showing the data
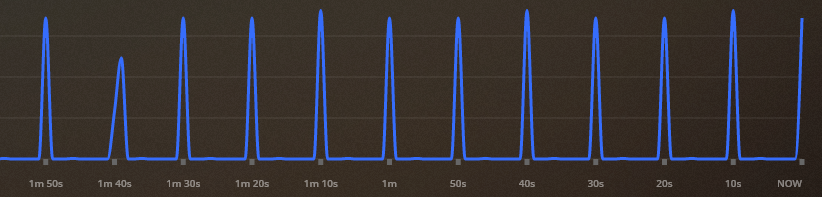
-
@DaddyGo said in I have no idea whos causing this traffic....:
(even on a smaller network, it’s worth just keeping one in your desktop drawer for testing)
See my post Creating a "data tap". I also use a TP-Link TL-SG105E switch. I carry it in my computer bag and have also used it as a plain switch on occasion. Since I use a port based VLAN on it, instead of tags, it works fine.
-
@JKnott said in I have no idea whos causing this traffic....:
I also use a TP-Link TL-SG105E switch
Well, then we think on the same way

-
One crude option is watching the traffic graph live (Status -> Traffic Graph) and changing the interface to LAN. Depending on your network design, if you're not seeing any data, you may also have to change the filer to "Remote".
Another option is to install the ntopng package. In the ntopng settings menu, make sure that all of your LAN interfaces are tagged. Once in the ntopng webgui, click on the "Flows" menu across the top and you will see details (protocol, source, destination, throughput, etc) about each connection. From there I would sort by the "Actual Thpt" column so the connections generating the most bandwidth are at the top of the list.
Yet another option is installing the softflowd package and pointing it at a netflow collector like PRTG.
I would use ntopng. You should be able to find the offending device in a few min.
-
I think I saw similar forum thread from Belgian op not long ago. I am not sure if he already found the solution.
Wireshark is a great tool but if I may suggest, use QRadar CE (FREE) to analyze your live Pfsense logs.


Like today, I found a lot offensive IP addresses.