Pfsense with pihole correct configuration?
-
@agaitan026 And part 2
You need a pi-hole now. That is if you want to use a pi-hole. Pfblockerng works very well. You could just use that and be happy. Really happy. It will block ads and more. It just works with ipv6, no complications. If you want use a pi-hole you know why you want to use a pi-hole and don’t need me to sell you on the idea.
Once you have one get it connected. We’re going to talk about using it on a different private network than the one(s) your other devices are on. Different physical network or VLAN doesn’t make any difference.
OK, it’s now connected. In my case it’s on the 192.168.10.0/24 network. You will want to make sure it’s always at the same address. Static DHCP reservation or static IP setup on the pi-hole. I like doing it with a static IP on the pi-hole not DHCP reservation. Do it how you want. Mine’s at 192.168.10.40. I can ping it. I can ssh into it. I can open the GUI.
The way this works is like this:
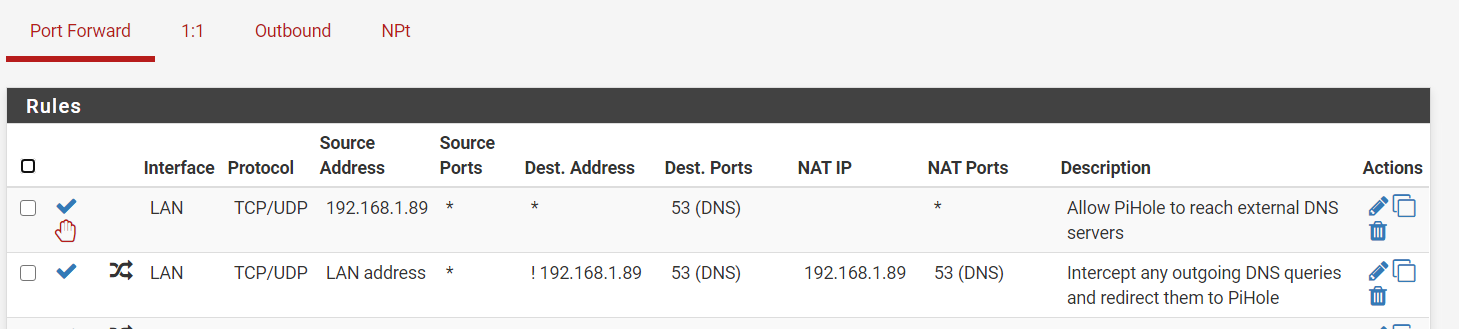
Device goes to the pi-hole for name resolution. It goes there because we told it to with DHCP. Those devices that don’t listen to DHCP go there because I redirect them with NAT. My choice. Again, handle this however you want.
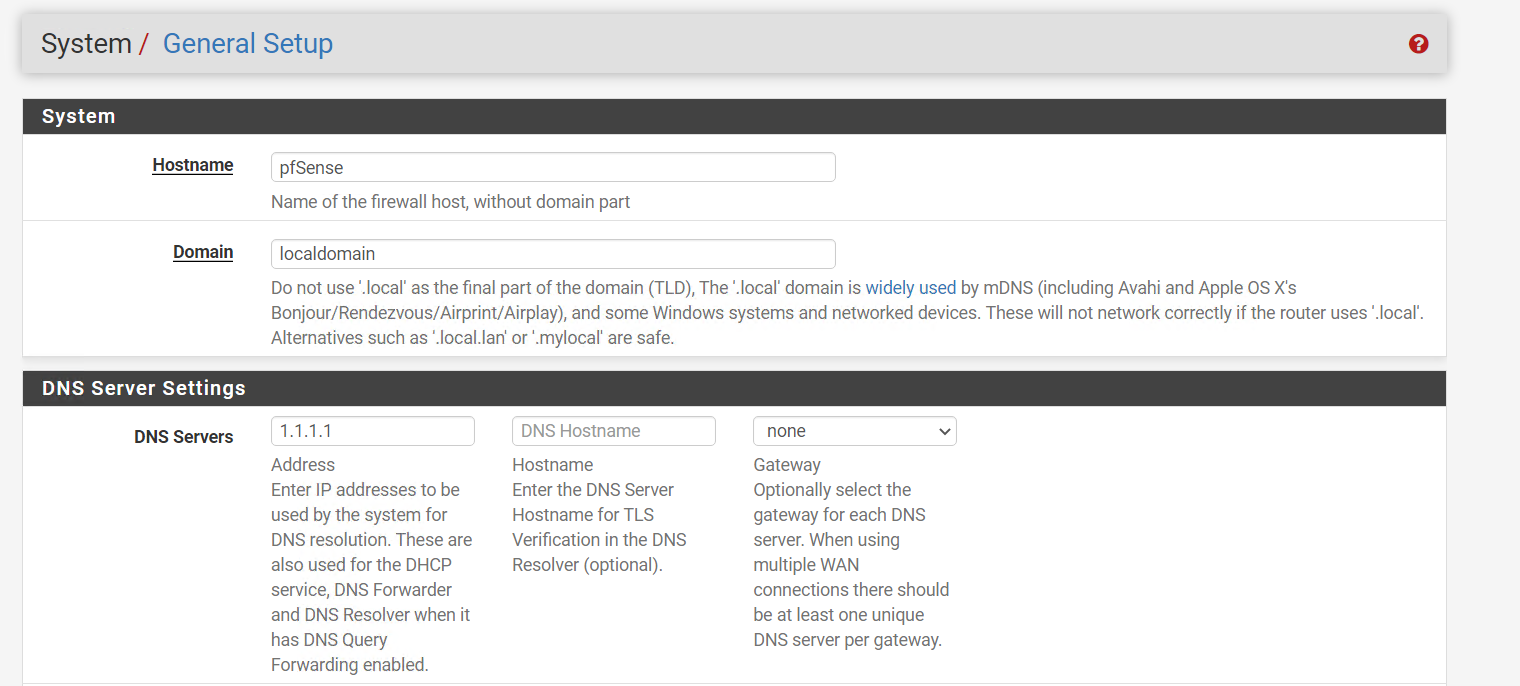
The pi-hole forwards to the gateway (pfsense).
Device -> pi-hole -> Unbound
Notice there has been no mention of cloudflare or google or cloud9. I’ll rant about this for a moment.
<rant>
DNS privacy is a hot topic. Lots and lots of FUD. Who do you trust and why? Think you can hide from your ISP? Not unless you route EVERYTHING through a VPN. Yes, you can deny them the ease of logging your DNS traffic. They are still handling all your traffic. They will just scrape what they want out of your traffic. Do you trust cloudflare or google more than your ISP? Why? Do you trust some VPN service? If there is money to be made it will be made. Some VPN service in a sketchy Caribbean jurisdiction? They can say anything they want. It means nothing. VPN in a European or US jurisdiction? They will respond to legal requests. Do they say they’re not logging? Are they full of sh_t? What will they do when they get a secret court order to start logging based on some remnant of our post 9/11 insanity? Look at the business model. They appear to have a lot of infrastructure around the world. All for $40 a year? They’re full of sh_t.The people selling you on this crap are smart. Look, look at what I’m doing to keep your online life private, they say. Private DNS (ODoH, is the latest BS), I’m so great and we’re the good guys. At the same time they are tracking every click you make and logging every step you take with your smartphone.
It’s like organic food. What do you want? Do you want your carcinogens from the regular list or from the list of approved organic carcinogens? If I had a penny for every crunchy self-righteous statement made by the lemmings I’d be richer than Jeff Bezos. Anything produced on an industrial scale is managed by accountants. Money not only talks, it’s the only thing that talks.
By the way. If you want good food buy local. Visit the farm. Have a look around. The good ones will welcome you. The thing is you are going to have to pay. Good stuff done carefully costs. Treating employees right costs.
Just resolve using unbound. If you really care about your privacy, DNS is the least of your worries.
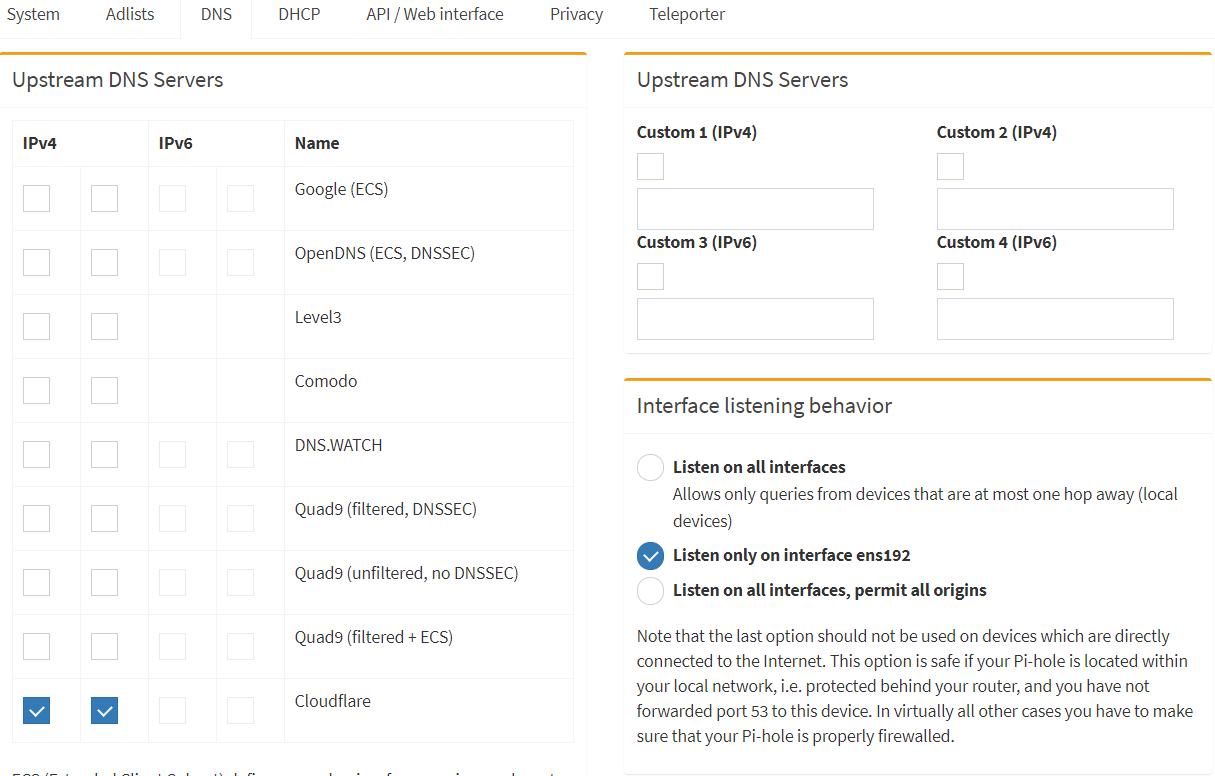
</rant>Once you’re up and running you want to see this in your pi-hole.
Remember, my pi-hole is on the 192.168.10.1/24 network so 192.168.10.1 is unbound. Also, there is no monkey business going on in this network. No redirection or rules blocking port 53.
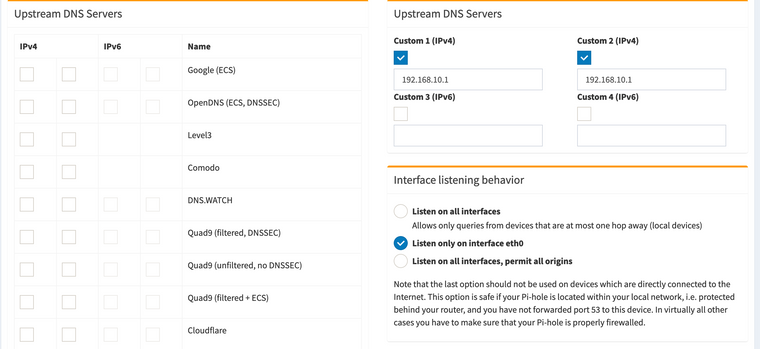
Now you can do this:
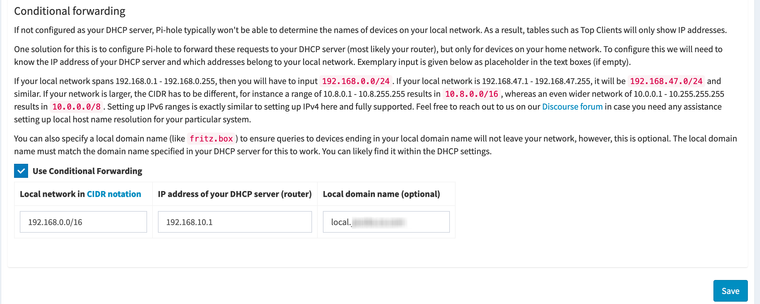
Adjust for your situation. I have a few networks so I just cover the entire 192.168.0.0/16 range.
Now I can see my hosts by the hostnames I setup in their DHCP static reservations. Otherwise it’s a hot mess in the pi-hole logs.
What’s left to do is to get your client devices pointed to the pi-hole. Simple really. Just have DHCP tell them were to go. In the DHCP server settings for each network (other than the one your pi-hole is on, sorry to be redundant but it is worth pointing out again) you do:
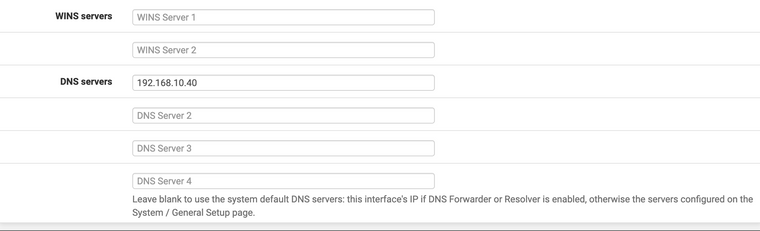
That points every device on that network to the pi-hole. Each individual static reservation should have nothing for DNS servers because we did that above for the generic baseline setup. You could do it device by device in their static reservations. Up to you. If you want to exempt some devices from filtering you can do it static reservation by static reservation or use pi-hole groups. Your choice.
Things should now be working good.
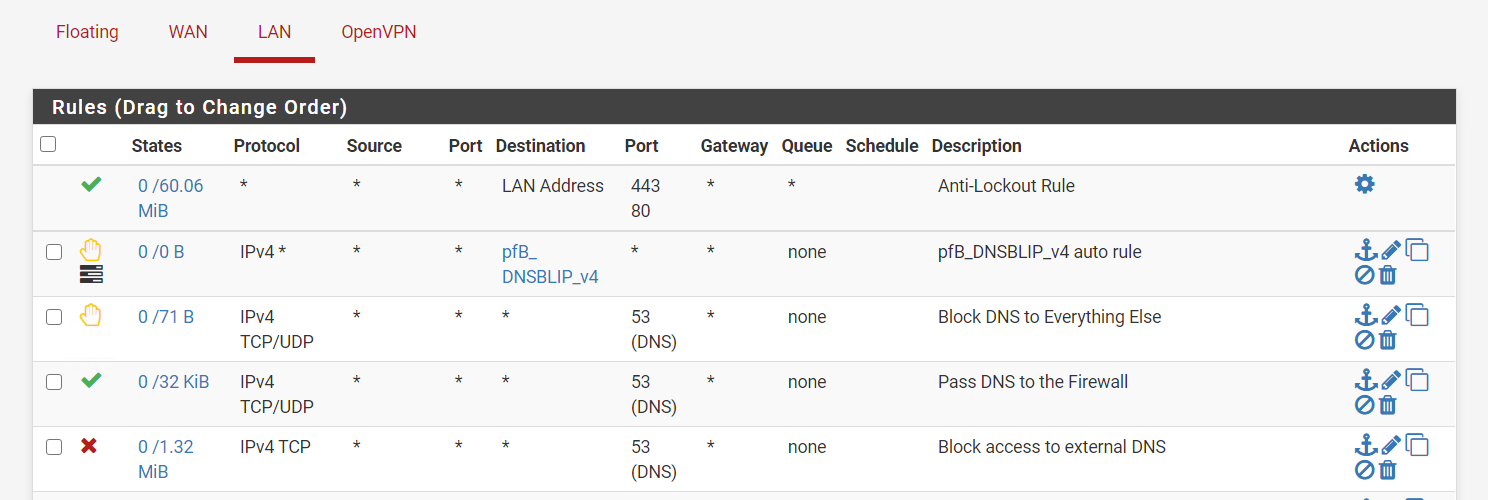
If you have locked down networks, like a guest network, you will need a rule to allow those clients to get to the pi-hole. Add a pass rule.If you want to do redirection on networks that contain devices that don’t play by the rules, add the NAT port forward and it will add the correct pass rule.
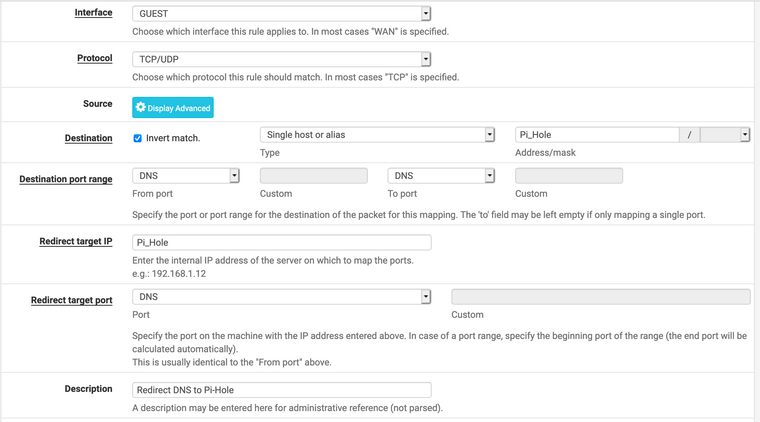
You should get a rule that looks like this on the corresponding network.

Creating an alias with the ip of your pi-hole will make the above rules clearer when you look at them later.
That's it for now. I hope that helps.
-
@jwj said in Pfsense with pihole correct configuration?:
ODoH, is the latest BS
But the company providing the proxy for that and then the dns provider - they would never collude ;) heheheh... They only have your privacy in mind ;)
Its like they are on a mission to F up dns beyond nonsense.. In the sake of privacy my ASS!!
If you are concerned about your isp easy sniffing your dns, then just resolve through a vpn tunnel.. But as stated - they still handling your traffic - so not like they can not find out where your going and when, etc.
The only way to hide where your going from your isp is full vpn.. But then your just handing all that info over to your vpn provider and giving them money to to boot..
If you really care about your privacy, DNS is the least of your worries.
QFT
Here is the thing - anything that centralizes dns, and lets devices or software just use what they want other than what you tell them for dns.. Is not in anyone's best interest that is for damn sure.
-
@johnpoz Yeah man. I just don't get the amount of attention this gets or the amount of emotional energy people put into it. Truly a not seeing the forest for the trees situation.
This guy should know better than give any attention to it:
https://www.schneier.com/blog/archives/2020/12/oblivious-dns-over-https.html
and, well, I guess this is an unsurprising bit of click bait:
https://arstechnica.com/information-technology/2020/12/cloudflare-apple-and-others-back-a-new-way-to-make-the-internet-more-private/
Was going to wade into the comments. Decided to not inflict that pain on myself.
-
@jwj thank you for your tips. I tried but not working. Im not sure if its because i have whm/cpanel on one of my VMs if i try to browse to a website from whm vm doesnt works but if i try google.com it works
What im doing wrong?
Thank you
-
@agaitan026 I have no clue. Sorry.

-
@agaitan026 said in Pfsense with pihole correct configuration?:
Im not sure if its because i have whm/cpanel on one of my VMs
Having a hard time coming up with how that would have anything to do with anything... Unless its trying to do something with dns on its own, and not paying attention to your settings in unbound, etc. And your trying to use it to figure out your dns working or not working?
Forget whatever it is your doing on some vm..
Do a simple query to pfsense IP.. Does dns work or not? Use your fav tool, dig, host, nslookup, etc..
Is pfsense running as a VM?
-
@johnpoz correct, pfsense is running on a vm, pihole is in another vm with another vlan
-
Ok so pfsense is a vm, which we have no idea if how you have setup and connected to the internet.
Does pfsense dns work or not - its 2 seconds to validate via simple queries to it via your fav tool.. Dig is mine..
-
@johnpoz working
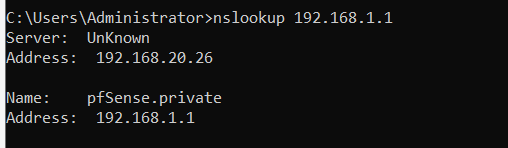
i have pfsense 192.168.1.1 and pihole 192.168.20.26 another vlan
i can browse any website except websites inside the cpanel vm
like this
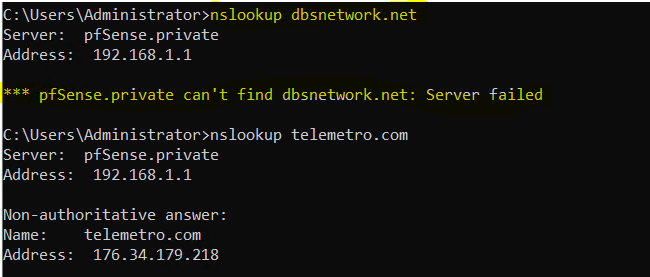
on yellow a domain from whm vm in the same machine as pfsense and pihole
strange by enabling this setting in Services / DNS Resolver / General settings
DNS Query Forwarding
Enable Forwarding ModeIf this option is set, DNS queries will be forwarded to the upstream DNS servers defined under System > General Setup or those obtained via DHCP/PPP on WAN (if DNS Server Override is enabled there).now i can browse whm websites without issues im not sure if thats the correct behavior and setting
-
Have already been over this multiple times..
There is not right or wrong setting be it you want to forward or not forward...
When you enable that - you forward, when its not enabled you resolve..
Where you resolving when you tried to lookup dbsnetwork.net?
Seems you point the NSs for that to yourself? Your hosting the NS for that domain it seems?
-
@johnpoz correct ns point to same ip
-
Well you have a problem there.. I see that they don't even answer via tcp as well.
So you have communication problem talking to yourself it seems then.. Hosting dns on the same device is not a good idea! The 2 NSs are on the same network.
-
@johnpoz yes thats true. I should use maybe amazon route 53 or another service. I got another vm that points to route 53 ns and doesnt have any issue.
So that's my big problem. A basic ns thing
You recommend another rather than amazon route 53?