DNS Resolver Timeouts
-
@bingo600 Yeah, tried that already, didn't make a difference. In Site A where unbound is perfectly working, I have that checked and the DHCP service restart is very fast that it is barely noticeable. These are both for home sites and it's not like the lease of my few DHCP clients are always expiring.
-
@kevindd992002 said in DNS Resolver Timeouts:
What can Wireshark provide that the packet capture
you can see an online and / or real-time scan on the Wireshark screen - when you launch an action
do you pass this on site B?
(for this installation, for example, the DNS goes through a tunnel)translate this, of course, into your example (GW A site)
-
@daddygo said in DNS Resolver Timeouts:
@kevindd992002 said in DNS Resolver Timeouts:
What can Wireshark provide that the packet capture
you can see an online and / or real-time scan on the Wireshark screen - when you launch an action
do you pass this on page B?
(for this installation, for example, the DNS goes through a tunnel)translate this, of course, into your example (GW A site)

Sorry, what? What do you mean by "page B"?
Let's forget about the tunnel for now. Like I said, that is my last resort/workaround. Let's treat site B as an independent site without an S2S VPN. My goal here is to simply use unbound on site B as a resolver (not forwarder) without any issues.
-
@kevindd992002 said in DNS Resolver Timeouts:
Let's treat site B as an independent site without an S2S VPN
Okay then we misunderstand each other...
can you draw a quick diagram of what you want to achieve?
A site pfSense A
B site pfSense Bor exactly what
-
@daddygo said in DNS Resolver Timeouts:
@kevindd992002 said in DNS Resolver Timeouts:
Let's treat site B as an independent site without an S2S VPN
Okay then we misunderstand each other...
can you draw a quick diagram of what you want to achieve?
A site pfSense A
B site pfSense Bor exactly what
It looks like it, yes.
So I have two sites that are connected through IPsec VPN, yes, but I just gave that information here because it was one of the tests I had (using the DNS resolver on the far end of the tunnel).
Site A (main site)
- WAN interface has a public static IP
- no problems with being a DNS resolver (without forwarding)
Site B (remote site)
- WAN interface is assigned a private IP since it is behind a CGNAT
- when DNS resolver (without forwarding) is set, tons of timeouts are seen in Status -> DNS Resolver and the whole network is affected, browsing is very intermittent
- when DNS resolver (with forwarding to 1.1.1.1, or 8.8.8.8, or even to the ISP's own DNS servers) is set, same behavior, lots of timeouts. I must say though, that this was my workaround before like a few months ago and it worked. For some reason, it is also timing out these past few days I tested.
- when DNS Forwarder (dnsmasq) is enabled instead, everything is working properly. It's been almost two days without any issues.
- as soon as I go back to using DNS resolver (unbound), then the problem is immediately back
-
@kevindd992002 said in DNS Resolver Timeouts:
It looks like it, yes.
so I understand, so in terms of your question, it has nothing to do with A - B.
in summary:
- The pfSense installation which is used in point B, works with a timeout.... DNS, if UNBOUND is used
- in addition, it is behind CGNAT
Can you do a test with this for both conditions? (Unbound / Forwarder):
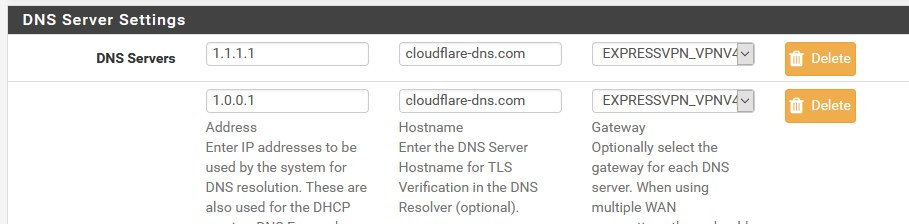
https://www.grc.com/dns/benchmark.htmFinaly, you can show UNBOUND settings such as:
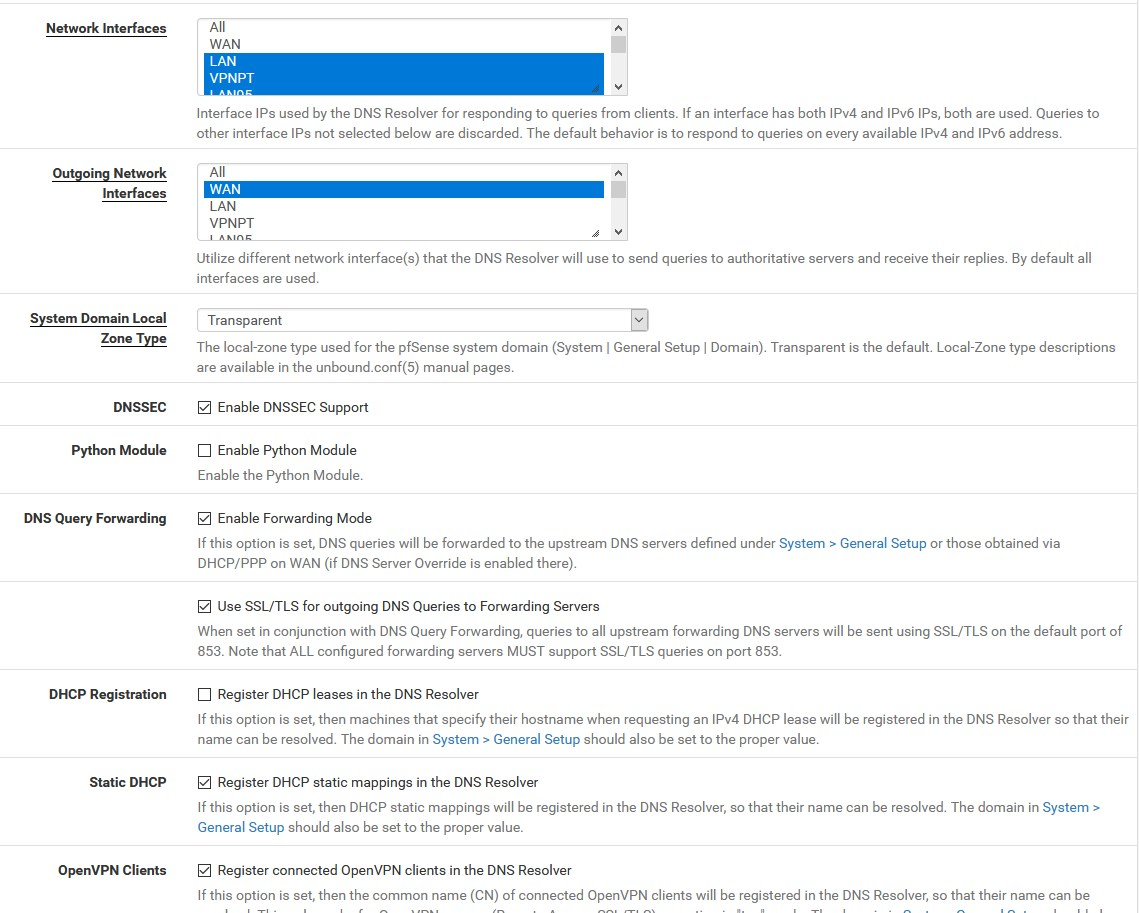
-
You got it.
I have to get back to you after Christmas for that benchmark test (which I'm familiar with as I used it before). I'm physically at site A right now and while troubleshooting another issue with IPsec, I accidentally lost access to site B's pfsense and no one is physically there to undo what I did.
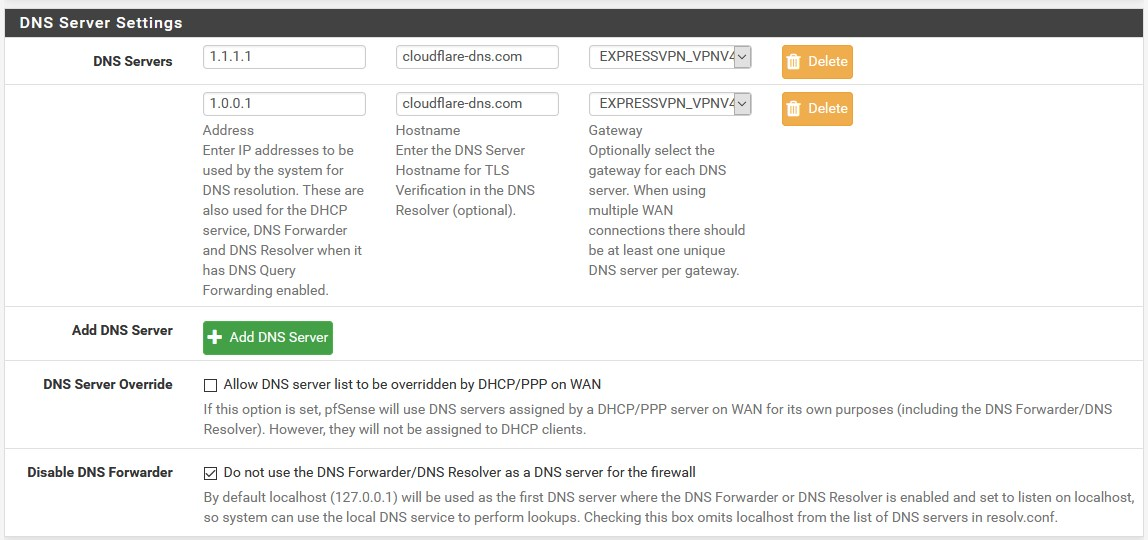
As for the settings, they are exactly the same with the unbound settings I have site A and here they are:
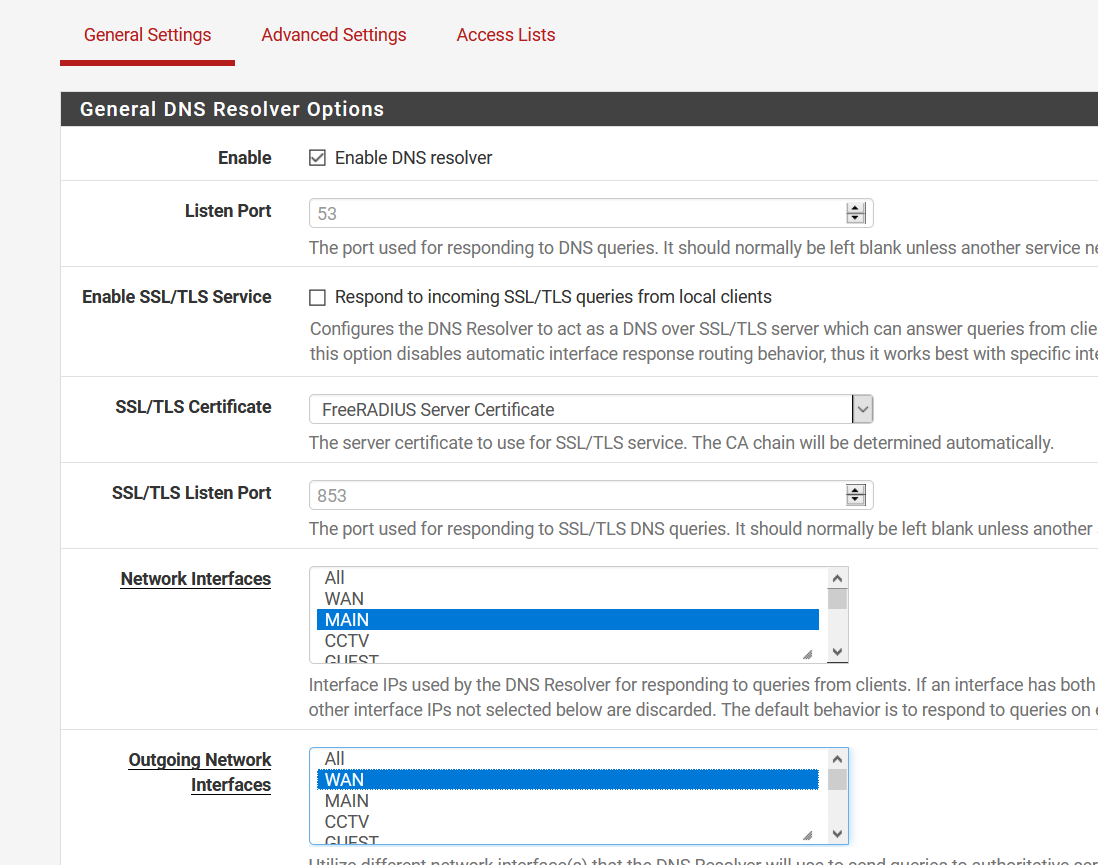
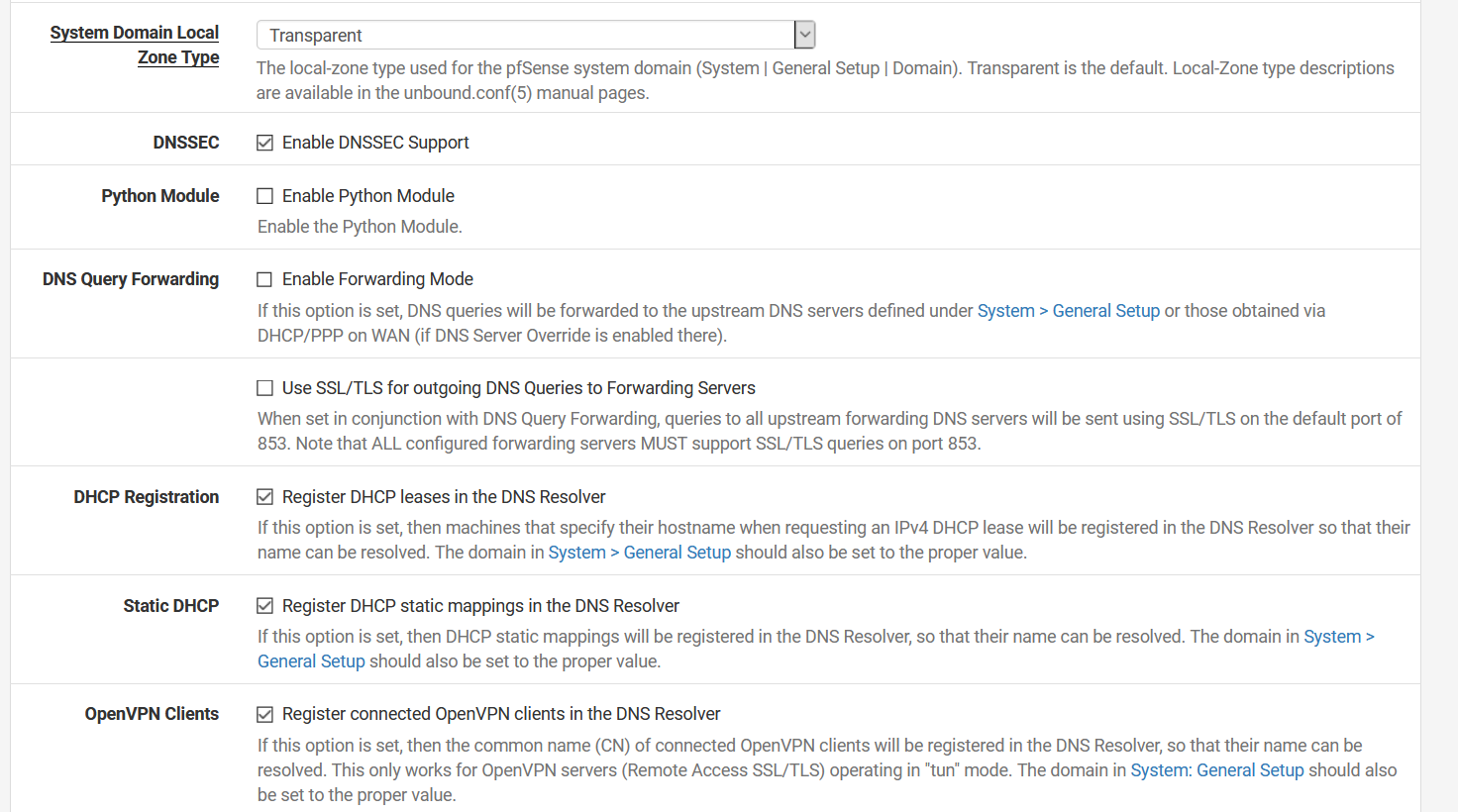
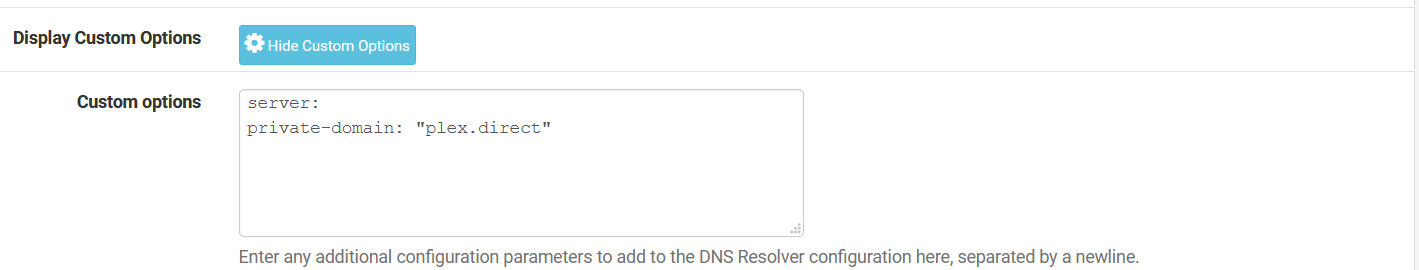
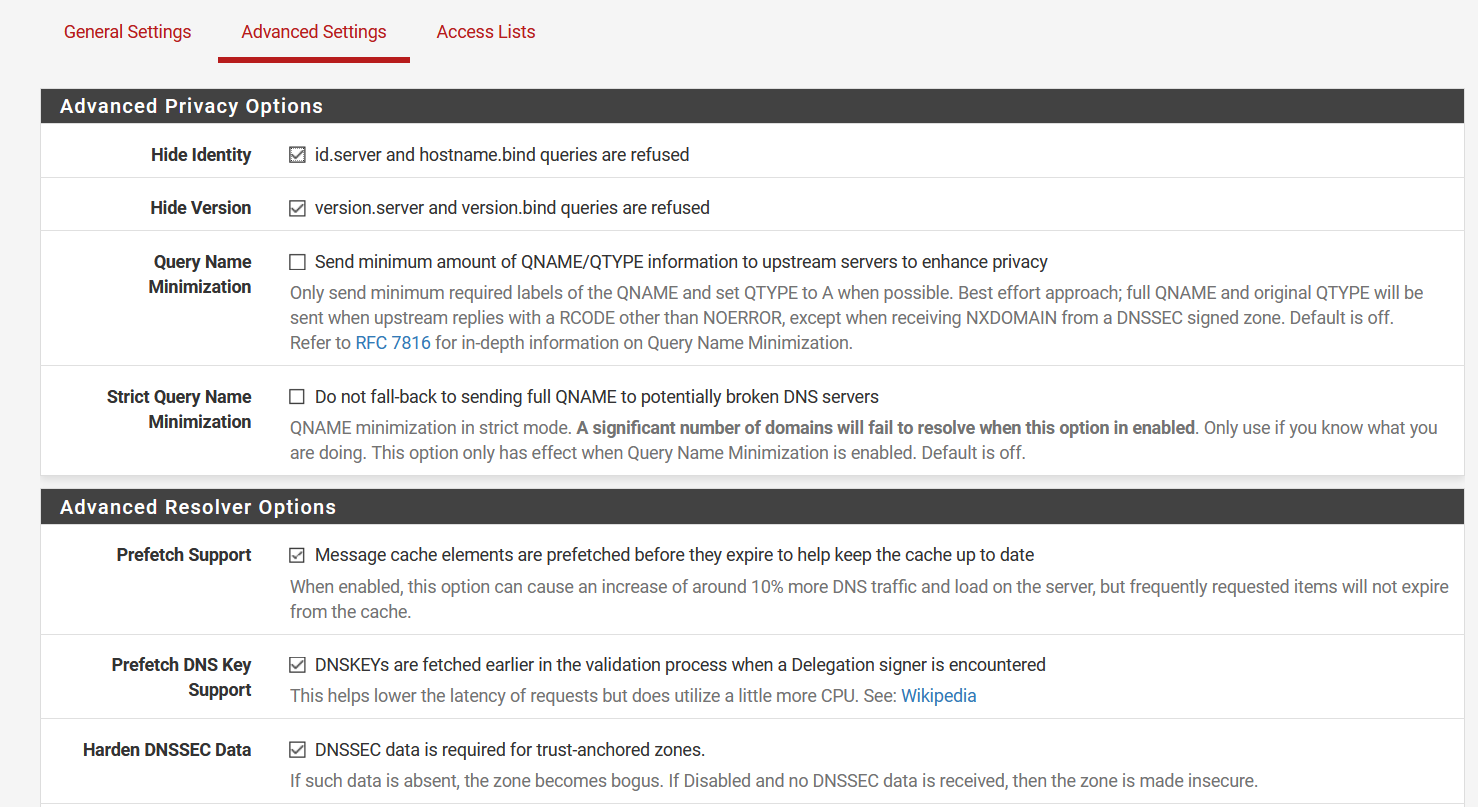
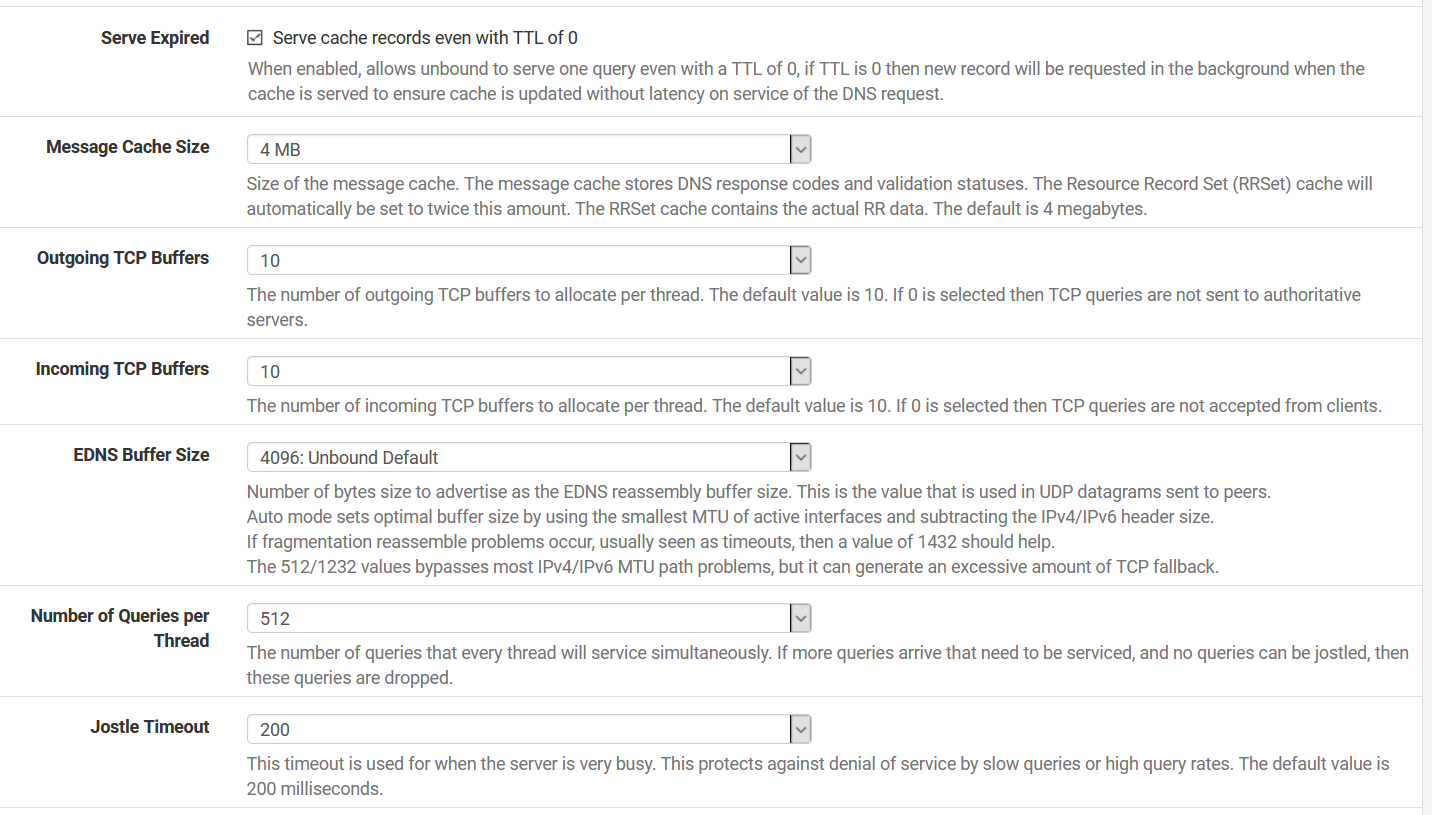
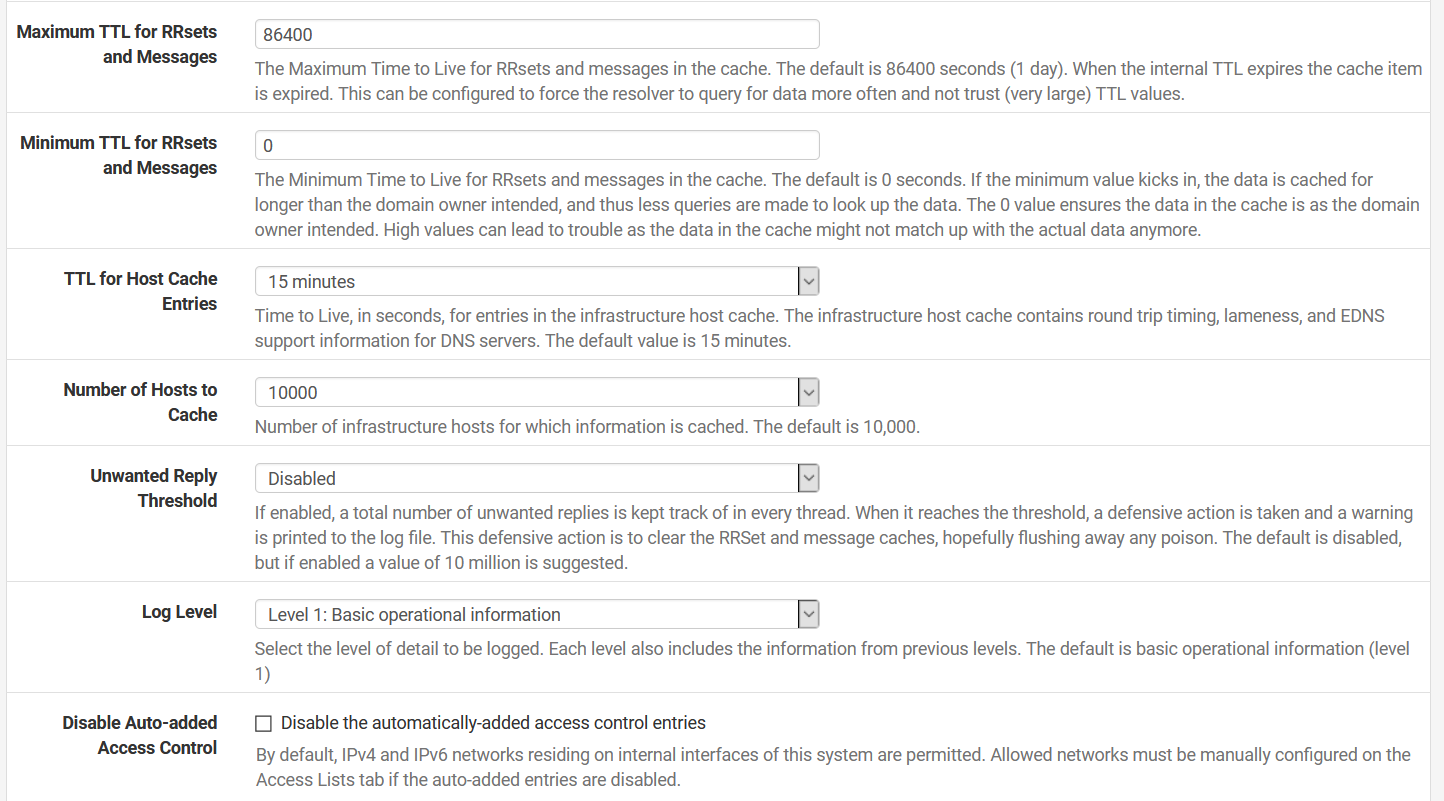
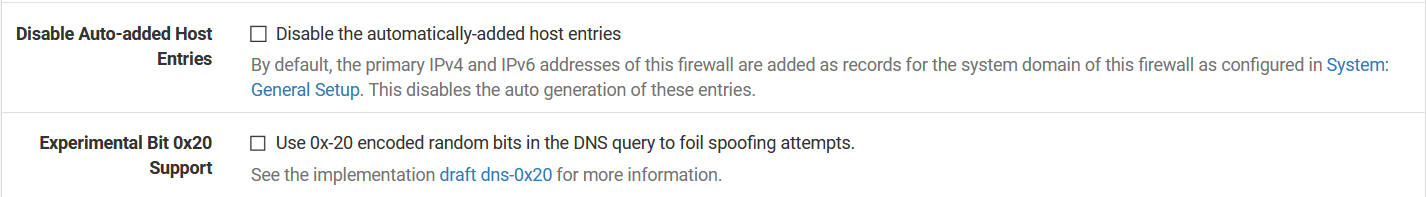
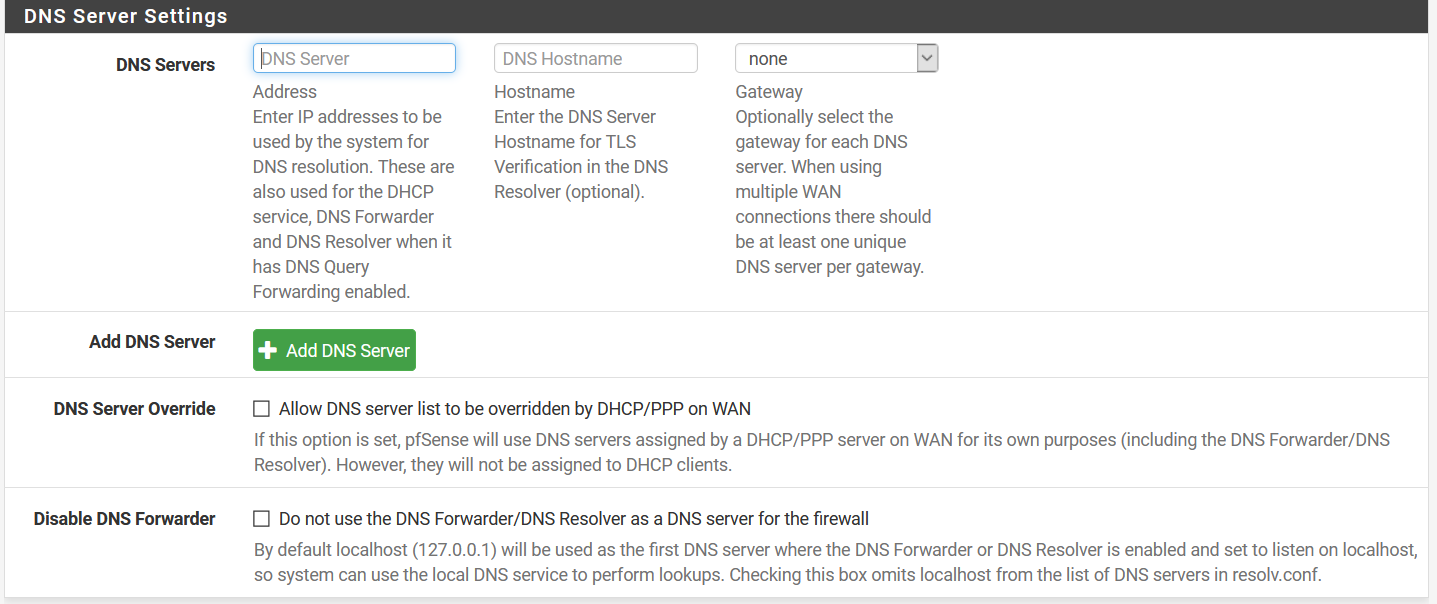
I don't have a DNS server in the DNS settings under General because I don't need one. I'm using unbound as a "resolver" so it queries the root hints directly. In the settings that you've shown, it looks like you're using unbound as a forwarder too, why?
-
How is this not the same exact problem you had before.. If you have a shit isp, then you have a shit isp..
Your previous thread showed loss on your isp.. If either of these sites its on that isp, or whatever isp they have is loosing packets.. Then yes you can have issue, be it dns or anything else.
Doesn't matter if you forward or tunnel or whatever.. If your isp sucks it sucks.. Nothing pfsense can do about that.
Previous you had sniffs showing traffic leaving your wan, with no answer.. There is nothing pfsense can do to fix that..
-
@kevindd992002 said in DNS Resolver Timeouts:
it looks like you're using unbound as a forwarder too, why?
Forwarding Mode to 1.1.1.1 = general tab
as I try to achieve more privacy and greater security

CloudFlare / 853 DoT
-
@daddygo said in DNS Resolver Timeouts:
as I try to achieve more privacy and greater security
Well that sure isn't doing anything about that..
-
@johnpoz said in DNS Resolver Timeouts:
Well that sure isn't doing anything about that..
I say I'm trying

at least I don't interrogate root servers through my own ISP, hihihihi
-
@johnpoz said in DNS Resolver Timeouts:
How is this not the same exact problem you had before.. If you have a shit isp, then you have a shit isp..
Your previous thread showed loss on your isp.. If either of these sites its on that isp, or whatever isp they have is loosing packets.. Then yes you can have issue, be it dns or anything else.
Doesn't matter if you forward or tunnel or whatever.. If your isp sucks it sucks.. Nothing pfsense can do about that.
Previous you had sniffs showing traffic leaving your wan, with no answer.. There is nothing pfsense can do to fix that..
Right, I just actually continued that old thread to this thread to make it "cleaner". The only new information I have now is that I tried with dnsmasq and it seems to have no timeouts. As to why, I don't know. But I was still having problems with unbound set as forwarder.
If you see my packet captures in the OP of this thread, it still does show traffic leaving the WAN and not getting any replies back. You're still right, I'm still pushing hard for my ISP to fix this shit, but what I don't understand is why dnsmasq seems to be working just fine?
-
@kevindd992002 said in DNS Resolver Timeouts:
I'm still pushing hard for my ISP to fix this shit
Indeed, if you have a shitty ISP, there’s nothing you can do, but my tests suggested above they are caught quickly
-
@daddygo said in DNS Resolver Timeouts:
I say I'm trying
But all you have accomplished is handing your info off to someone else on silver platter. With explicit trust of what they hand you back.. Your sure not hiding anything from your ISP that.. Since they still know every IP you go to, and simple if they wanted to to just sniff your sni for any https traffic to know what specific domain your going to.. Just like they could with your dns.
So what your trying to hide from the root servers?
Oh - the other thing you did accomplish is slowing down dns.. Guess you got that going for you ;)
-
@johnpoz said in DNS Resolver Timeouts:
@daddygo said in DNS Resolver Timeouts:
I say I'm trying
But all you have accomplished is handing your info off to someone else on silver platter. With explicit trust of what they hand you back.. Your sure not hiding anything from your ISP that.. Since they still know every IP you go to, and simple if they wanted to to just sniff your sni for any https traffic to know what specific domain your going to.. Just like they could with your dns.
So what your trying to hide from the root servers?
Oh - the other thing you did accomplish is slowing down dns.. Guess you got that going for you ;)
@DaddyGo sorry but I'm on @johnpoz on this one. He is completely right. If you're using unbound, then its primary purpose should be a "resolver" like what I've been telling you with my earlier posts. I guess you misunderstood again.
-
@johnpoz said in DNS Resolver Timeouts:
Oh - the other thing you did accomplish is slowing down dns.. Guess you got that going for you ;)
I'm not that simple.....

look at the following...it's not that bad (3 ms)
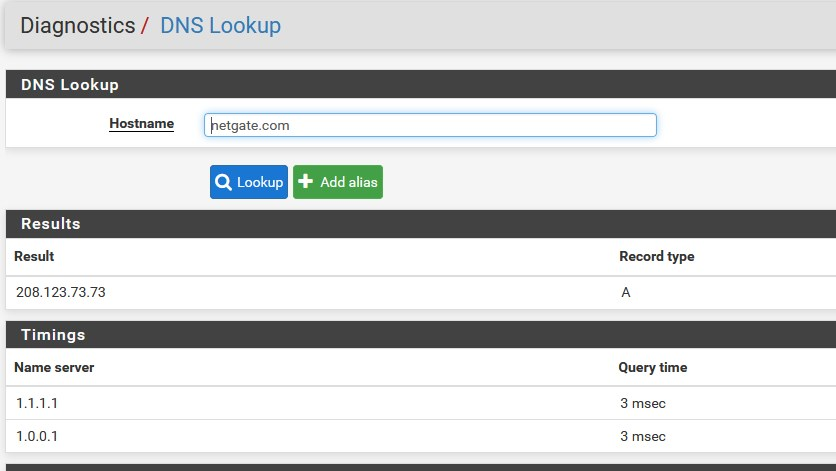
which I did not show...... where is the ISP here.....
+++edit:
our ISP can't even set foot on us, only the VPN IP can see and it's done -
Handing info over to company B, because you don't trust company A - while company A still has all this info (if they want it). When you don't even know if company A is doing anything with that info in the first place in no way shape or form increasing privacy or security. If anything it lowers both of those..
I could see doing dot if for example you knew that company A was intercepting your dns and messing with it..
But unless company A is doing that, forwarding all your dns to company B does not provide anything of value..
edit:
Your doing a query through a vpn, to cloudflare over dot in 3 ms.. Sorry but BS!!edit: So you have hidden your traffic from your ISP with your vpn.. .You have hidden your IP from the bad old root servers. But now you have handed over all your dns to xyz dns provider.. So how does that again do anything for privacy or security... You have just handed over all your info on a silver platter is all..
You have just traded where you going via IP and sni from your isp to your vpn provider.. How does that improve anything? Again unless you know your isp is messing with this traffic or filtering it, etc.
-
@johnpoz said in DNS Resolver Timeouts:
Your doing a query through a vpn, to cloudflare over dot in 3 ms.. Sorry but BS!!
I know your opinion on this theme (DNS) John, so I do not argue...
indeed, you are half right, but he / she who does nothing will stick his / her head in the sand...or rather I quote
 :
:As Edward Snowden says:
“Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.”
+++edit:
otherwise pls. name a secure third party DNS provider, 1.1.1.1 is only because we have a lot of services running on them, otherwise we use ExpVPN DNS servers / VPN servers
They run in RAM and restart every 24 hoursgood old root servers:
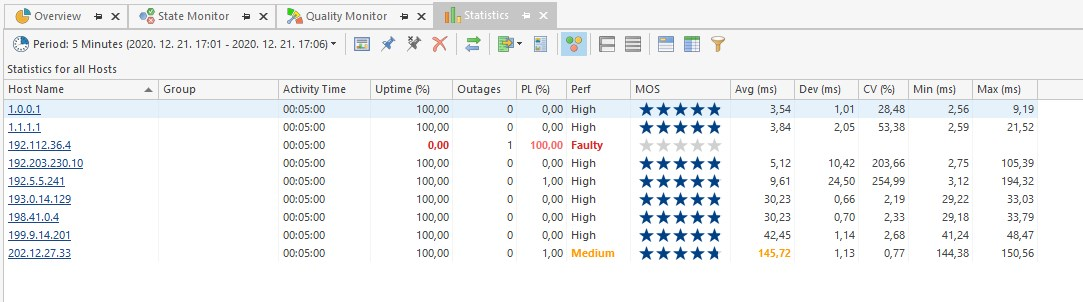
-
@kevindd992002 said in DNS Resolver Timeouts:
I guess you misunderstood again.
for sure, that's right

-
@daddygo So to try and resolve this problem for Site B, I want to use unbound on Site B and forward all requests to the unbound in Site A (which acts as a real unbound, not forwarding, DNS server). The problem is when I do this, I still get DNS query timeouts even though the unbound server in Site A is perfectly working. This is randomly happening and is evident when shows me entries with a "retried" status:
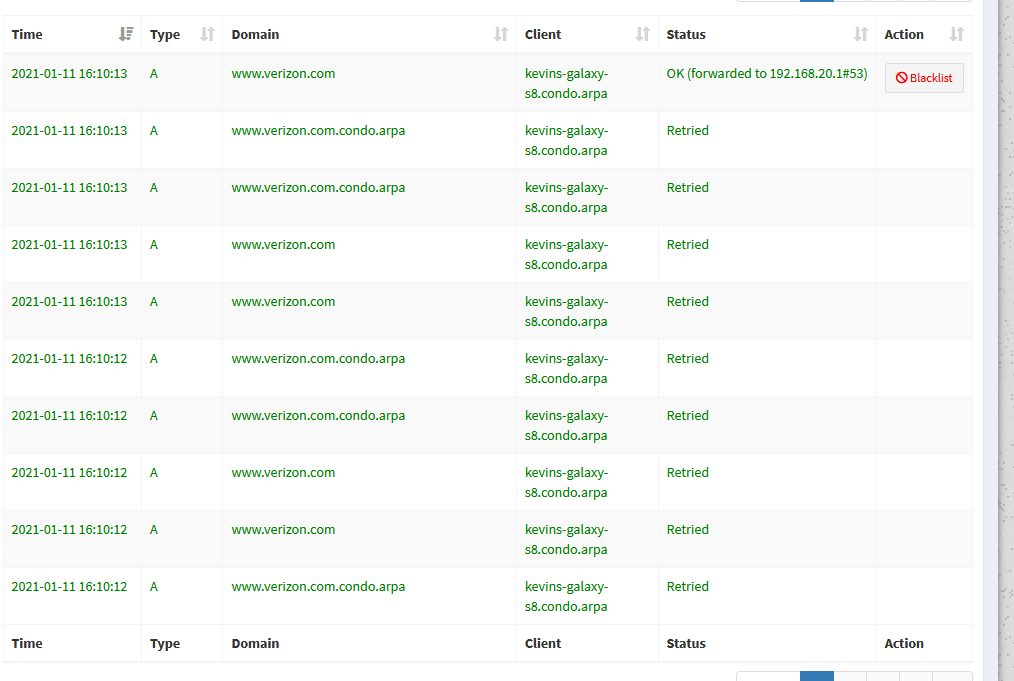
When I do a DNS bench test, I get 100% results but then again this test is only ran for a very few seconds and does not catch when the drops are happening:
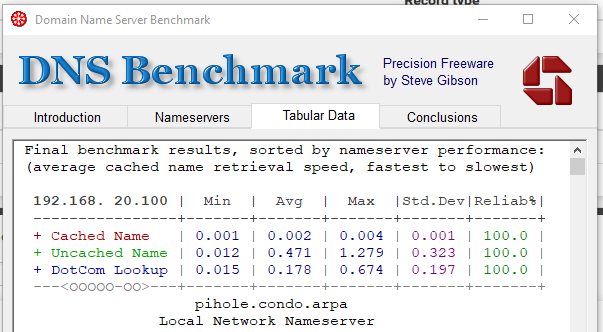
I also get a fairly stable IPsec tunnel between the two sites:
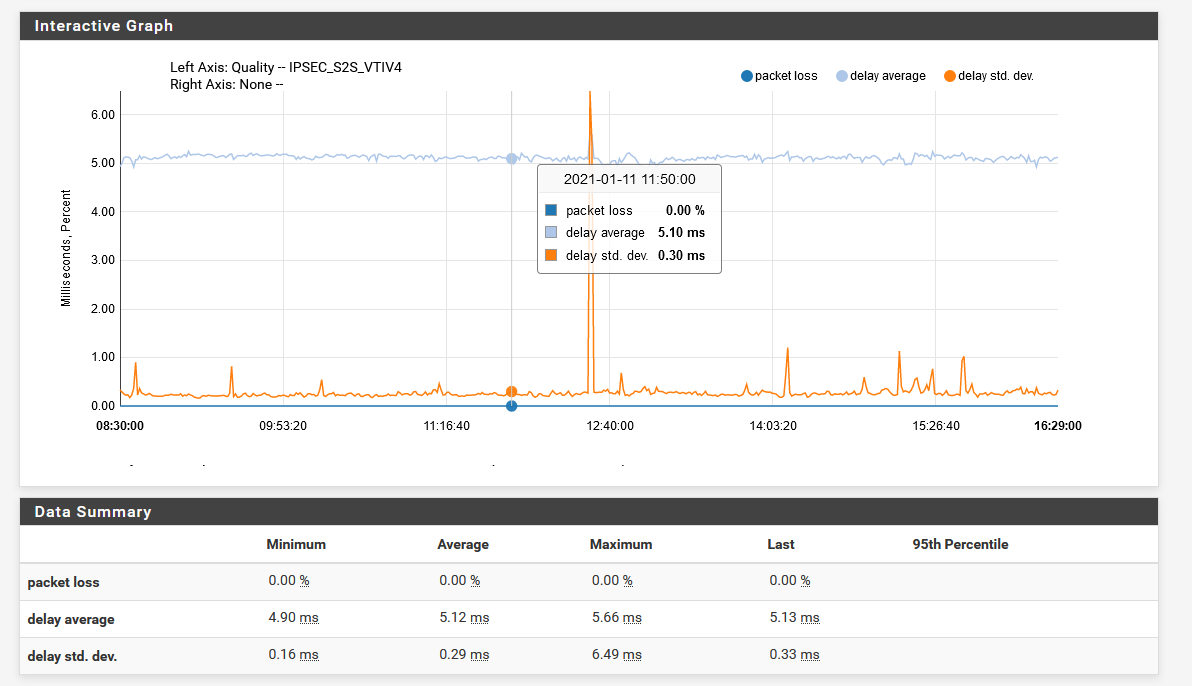
So I'm not sure why there are DNS drops here. How can I troubleshoot further?