Remote access connection issues
-
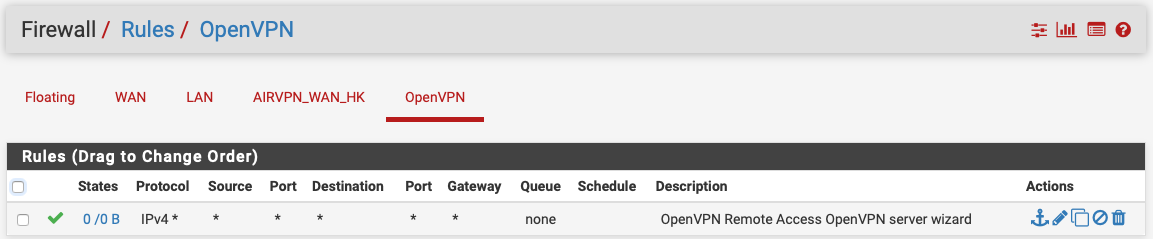
I had setup a remote access vpn using the wizard in pfSense more than a year ago, and it worked flawlessly. I recently changed hardware, and restored my backup. Now, when outside my network, I can connect to the OVPN server on the pfSense box, but have no access to the LAN. I've made sure the OpenVPN rule is in place (see below), but I'm not sure where else to look to resolve this issue. Any suggestions.
-
Are the routes set on the client?
What is your LAN subnet?
-
Post your server1.conf.
-
@viragomann I exported a new client config once I restored from backup, in case there were some backend changes. Whatever routes were setup in the server would have been passed to the client since I used the client export package in pfsense.
My LAN subnet is 192.168.11.0/24 and tunnel subnet is 10.0.11.0/24
-
@marvosa Be glad to but I've only used the pfsense gui, I don't think you're asking for a pic of the front end configuration. Where is the server.conf file located?
-
Also, I've never had any rules set related to the different subnets. Before the new hardware, I was able to access devices on the LAN when connected through the VPN simply by using their IP address
-
@bwanajag said in Remote access connection issues:
I exported a new client config once I restored from backup, in case there were some backend changes. Whatever routes were setup in the server would have been passed to the client since I used the client export package in pfsense.
If we don't know neither the routes nor you provide the server configuration, it'd not possible to help here. Both would be better.
You can also take a screenshot from the server settings page and insert it here. -
@bwanajag The OpenVPN configs are located in /var/etc/openvpn. You can get there via the shell or the GUI (Diagnostics -> Edit File)
-
Here are the server and client configs:
Server:
dev ovpns2 verb 1 dev-type tun dev-node /dev/tun2 writepid /var/run/openvpn_server2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-256-CBC auth SHA1 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 20.21.20.29 engine rdrand tls-server server 10.0.11.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server2 username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server2 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'pfso_scert' 1" lport 1194 management /var/etc/openvpn/server2.sock unix max-clients 7 push "dhcp-option DOMAIN 192.168.11.1" push "dhcp-option NTP 192.168.11.1" push "redirect-gateway def1" client-to-client ca /var/etc/openvpn/server2.ca cert /var/etc/openvpn/server2.cert key /var/etc/openvpn/server2.key dh /etc/dh-parameters.2048 tls-crypt /var/etc/openvpn/server2.tls-crypt ncp-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC:AES-256-CBC compress lz4-v2 persist-remote-ip float topology subnetClient:
persist-tun persist-key cipher AES-256-CBC ncp-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC:AES-256-CBC auth SHA1 tls-client client remote 20.21.20.29 1194 udp lport 0 verify-x509-name "pfso_scert" name auth-user-pass remote-cert-tls server compress lz4-v2 <ca> -----BEGIN CERTIFICATE----- (removed) -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- (removed) -----END CERTIFICATE----- </cert> <key> -----BEGIN PRIVATE KEY----- (removed) SMMQfc7Uii8d4I0Ee7NTnq9X -----END PRIVATE KEY----- </key> <tls-crypt> # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- (removed) -----END OpenVPN Static key V1----- </tls-crypt> -
How are you trying to access your resources? I see one issue:
push "dhcp-option DOMAIN 192.168.11.1"You are pushing a DNS domain of 192.168.11.1 to your clients, so all of your name searches are being appended with "192.168.11.1" which is incorrect. The DNS Default Domain box in your config should have the name of your domain (e.g. MyDomain.com) in it, not an IP. Are you even using AD? If not, you shouldn't be pushing a DNS default domain.
I also see you have an AirVPN client tunnel configured. Is that new? I would modify the firewall rule on the OpenVPN tab, so it's explicit to your remote access tunnel network and your LAN. In other words, change the source to 10.0.11.0/24 and change the destination to "LAN net".
What do the rules look like on your AirVPN_WAN_HK tab? Hopefully, you don't have an any/any in there :)
Another question, what version of PFsense were you running on your old hardware? What version are you running now?