pfSense ignores static routes
-
Not using Multi WAN but even then this option worked for me.
-
Well, since no one understands what exactly was fixed and how, just by changing disable reply to (which is a very sane setting IMHO) you are setting yourself up for failure next time anything breaks.
And certainly pf doesn't ignore static routes
Glad this worked for you, but still, this worked out of luck (and you will be needing it)Regards
-
Prob has something to do with his vips and 1:1 natting.. Which not exactly clear on the how and why of such a setup..
If you hit vip address, your reply should come from that vip.. If he doesn't want it to come from that vip there is where the reply-to is coming into play.
I concur with you @technophile not actually understanding what fix it and how is not a good solution...
Tech: So what did you do to fix your problem?
User: Oh I clicked on some shit
Tech: Rolleyes!!!The network (as explained) seems borked out of the gate to me.. If his transit is public.. Why is he routing over this public space back to rfc1918 space to a different router? If he wanted to obfuscate his public space he should of called that out in his OP.. and prob used the documentation nets 192.0.2/24, 198.51.100.0/24 or 203.0.113.0/24
If the space he is using as transit is clearly public and the reason for the nats to his servers on rfc1918 space then he should use a different transit network to get to other rfc1918 space where this traffic is not natted, or use a tunnel to transverse the public space which amounts to a different transit, etc. etc.
My GUESS is some sort of asymmetrical routing problem where say rfc1918 space hits the public IP without the source being natted to some public transit being used and now needs to get back to the rfc1918 space via different route.
You could go down a deep rabbit hole trying to figure out what is actually going on, etc. But without the details from him just guessing.. For now the solution is "clicked some shit" ;)
-
@johnpoz said in pfSense ignores static routes:
Tech: So what did you do to fix your problem?
User: Oh I clicked on some shit
Tech: Rolleyes!!!Much better:
Patient calls doctor:
Patient: My Finger hurts.
Doctor: Can you explain exactly where it hurts and what you did before.
Patient: Never mind, I cut the finger of. It hurts no more.15 Minutes later the patient calls again:
Patient: Now my hand hurts.
... -
hehehhe - good one!
-
As I had explained originally, pfSense was ignoring the static route for 192.168.0.0/16 networks and instead of routing the traffic to the specified gateway for 192.68.0.0/16 it was directing the traffic to the default gateway. Since the problem got rectified I believe the reply to setting was overruling the static route setting.
-
The users on the 192.168.0.0/16 network need to access the servers behind pfSense using their actual IP addresses so that the access can be logged. Otherwise I could have conveniently done NAT for the entire block and this issue of specifying a static route and gateway won't have arisen.
There is no asymmetrical routing. It is RFC 1918 space leaving the public IP without a source NAT and trying to get back to the RFC space via the SAME route, which wasn't happening even after specifying the static route.
-
In the forums, similar cases of pfSense ignoring the static routes have been discussed in the past. In many cases, people mentioned using a floating rule to override this behaviour which did not work for me.
-
Hi.
I had this problem in 2.5.1 and 2.5.2, i tried ANYTHING, even opnsense but i had similar issues;
i found a permanent fix by removing all static routes and migrating them to firewall rules.Let's say we have three connection WAN1, WAN2 and WANX, we want to use WAN1 and WAN2 in load balancing and WANX ONLY for some routes (no internet is available here!):
1- remove all static routes, they will be ignored anyway and may give error on UI
2- Configure your gateways and create a gateway group for WAN1 and WAN2, in this example we call it LoadBalance
3- Create like usual a firewall rule in LAN to redirect internet traffic to LoadBalance gateway
4- Create one or multiple firewall rules under LAN with source LAN NET and with destination the nework of your static rules
5- Put the "static route" rules on TOP and the load balancing rule on the bottom, save and apply
Everything should now work fineExample: (note: networks in routes are redacted for privacy)
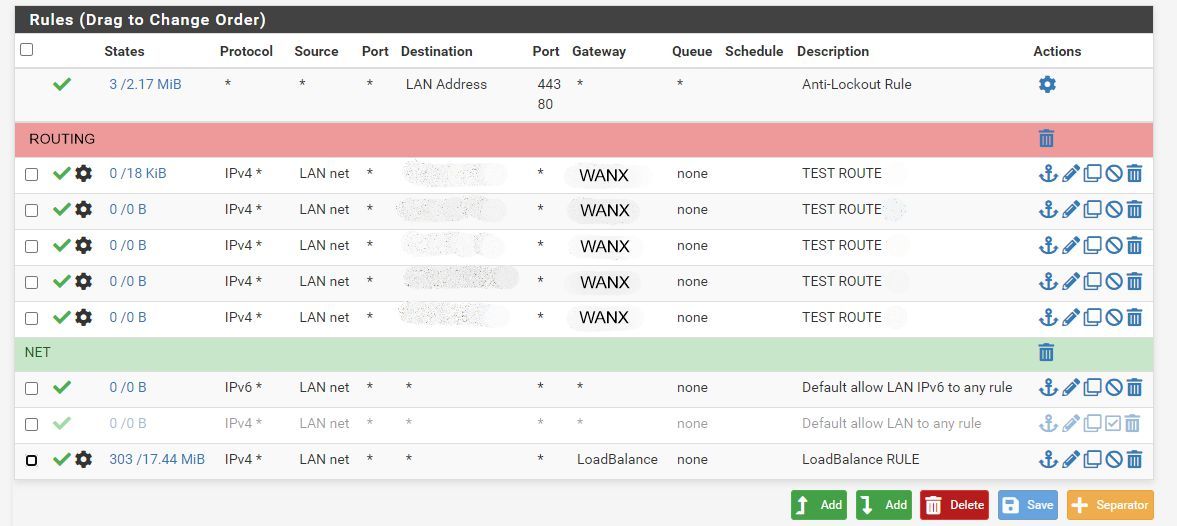
-
I had this same issue and what worked for me is creating a floating rule on the downstream PfSense to allow WAN to LAN connections. YMMW.