How do I allow VNC from one subnet to another?
-
I don't see anything at all in the log either. But is the rule enough, or is there some kind of an "outbound NAT" if that's even a thing that's necessary to get to the other subnet?
I am pretty sure there's nothing in the system that can resolve to a public IP, no. And 5900 is for VNC, yeah.
When I capture, I get this in Wireshark, in red:
14 1.776350 192.168.0.50 192.168.10.102 TCP 66 52111 → 5900 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1
-
Ok you sent syn.. Sniff on the airplay interface when you do that... Do you see the syn going to the IP 192.168.10.102, the thing you wan to to vnc too... If you do but you see no answer, then that means its not listening on 5900, or it has a firewall... Or its not using pfsense as its gateway.
No there is no outbound nat to do, pfsense does not NAT between local networks. Unless you put some gateway on pfsense interface for your local networks - they are LAN side network and no there would be no nat between them, unless you messed with the outbound nat rules.
-
Thanks! I set up a VM on the server directly on the 1.x segment, and it turned out that I could both sniff and get to the 10.x segment from that. So it seems the problem is in my server, which is kind of logical when I think about it. The Windows Server 2016 needs to know that requests to 10.x should go through the 1.x network. I tried setting up a static route in Routing and remote access on the server, but that didn't work, so I have to experiment a bit more to find out how I can route that.
-
HUH??
So you have multihomed server, ie it have interfaces in more than 1 network? Why would it go through your 1 network if its on the 10 network already??
Why don't you draw up how you have this server actually connected... Multihoming a server is normally BAD IDEA!!!!
-
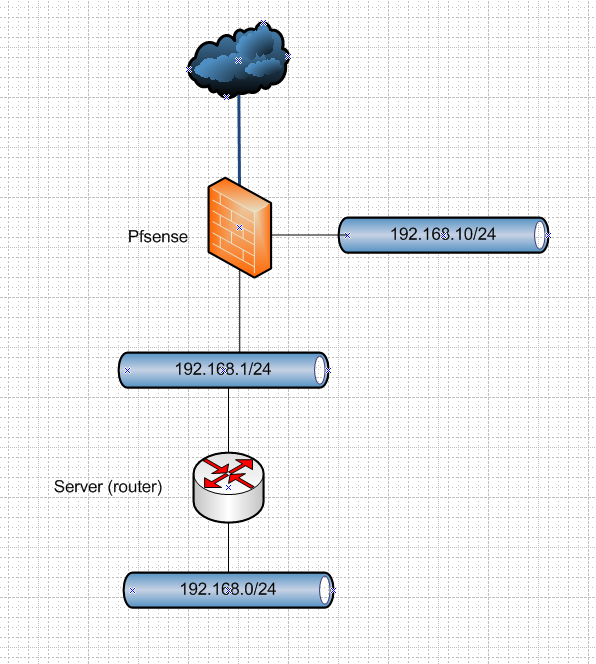
The server does not have (shared/NAT-ed/routed) interfaces in more than one network. The pc I want to connect from is on the server's internal network, 192.168.0.x, the server uses the 1.x segment from the pfSense box as it's WAN, and then I wanted to go like this:
Pc on 192.168.0.50 --> Server internal NIC 192.168.0.1 --> Server WAN 192.168.1.4 --> pfSense egetnett (the server's wan) 192.168.1.1 --> pfSense Airplay 192.168.10.x
-
If your server is a downstream router... Then its wan this 192.168.1 network becomes a transit.. There should be NO hosts on this network.. It is a transit network between routers.. If your going to put hosts on it.. Then this server (router) would need to nat traffic from the 192.168.0 to 192.168.1.x (its wan address).. If you expect the 192.168.10 to know how to get back to it..
If you do not nat, then pfsense needs to know to get to the 192.168.0 network to talk to this servers (downstream router) IP on the 192.168.1 network.
-
The server sees the .1 network as a pure WAN, yeah. The server has no outgoing DNS, DHCP or anything else to that net, everything there is controlled by the pfSense box.
But I'm afraid I need it dumbed a bit down, sorry... Do you mean that I need to put some kind of a static route from the 10.x network to the 0.x network with the server's external IP as the gateway? I thought the 10.x network would see the contact coming from the server's external IP on the 1.x network (192.1681.4), and that the rest had to be done in the server.
-
If your server nats the 192.168.0 netework to to its WAN ip 192.168.1.x then you have not problems. If it is NOT natting this and pfsense is seeing a source IP of 192.168.0 on its egetnett interface then for starters you need to allow for that.. Since 192.168.0 is NOT egetnett network 192.168.1
And pfsense also needs to know how to get to 192.168.0 via a route and a gateway..
where did you sniff this
14 1.776350 192.168.0.50 192.168.10.102 TCP 66 52111
If you sniffed that on pfsense then your server is NOT natting to its 192.168.1 address.And its not a static route from the 10 network.. Its route on PFSENSE saying hey to get to 192.168.0 talk to 192.168.1.x
So you need a gateway setup. And you need to create the route... And then you will need to enable the rules on egetnett to allow for 192.168.0
And if you want 192.168.0 to get to the internet you would have to make sure that pfsense does outbound natting of this 192.168.0 networkFor the life of me have no idea why you would do it this way... Why not just directly connect 192.168.0 to pfsense - what is the point of this server doing routing downstream of pfsense?
So you have other devices on this egetnett? If so them talking to stuff on the 192.168.0 is going to be asymmetrical..
-
I understand. I see that nothing happens in the Firewwall log when I try to VNC out, and there's no mentioning anywhere in the firewall logs about a 0.x segment, only 192.168.1.4 (the server's external network) so that should mean that the server should NAT to the WAN.
The sniffing was done on the internal network, on the same 0.50 pc that's trying to get to the VNC's on the 10.x network.
And 0.x has always gotten to the Internet, that's a problem. It's just getting from the internal network via the Server and to the 10.x segment that doesn't work. Which led me to think that I needed a static route to the 10 network. pfSense sees "hey, 192.168.1.4 on the Egetnett wants to talk to somebody on the .10 net, so I'll route it". And it can. So I think this is a matter of finding out how the Server can be aware that it needs to go to the pfSense on 192.168.1.1 to get to the 10.x network. I guess that's what you're saing in the bottom added part, right?
-
OMG dude...
Sniff on pfsense egetnett interface for 5900 tcp... Try and get to your 192.168.10 address from your 192.168.0 address.
Do you see traffic?? What is the source IP?
Now sniff on the airplay interface for tcp 5900 and try and get there again... Do you see pfsense send on the traffic???
"hey, 192.168.1.4 on the Egetnett wants to talk to somebody on the .10 net, so I'll route it".
Pfsense KNOWS how to route to any network connected to it... You do not have to create any routes... You have to allow it via a firewall rule on egetnett interface.
You say that 192.168.0 can get to the internet... So how is the default gateway of this server your 192.168.0 behind NOT pfsense IP address in the 192.168.1 network?? If its NOT then NO its never going to get to the 10.. Does this server your 192.168.0 have some other default gateway.. Does it have some other connection to the internet that you say the 192.168.0 can get to?
This is your network???
-
I need to set up something that can sniff on that network. I'll try to do that tomorrow and see if I can find out something.
The default gateway to Internet in my internal network is the server , 192.168.0.1, and the default gateway for Window's Routing and remote access (and NAT) on the server is 192.168.1.1, which is the pfSense box. And the 0 segment has no other way to the internet than Server --> pfSense --> ISP Internet router
-
Sniff on pfsense egetnett when you try and got vnc on the 192.168.10 address... If pfsense does not SEE this then no you can never get there.. Maybe your server is blocking it from going out?
This is really 30 seconds to figure out with simple packet capture on pfsense to validate traffic gets there and is sent on..
-
Sorry, I answered before you put in that network pic. Yeah, that's basically my network, at least the part of it that I am trying to get to work now.
I hadn't seen the package capture function on pfSense before, but I tried it now. I did packet capture on the Egetnett and nothing was shown that tried to go from 0.50 to the 10.x segment. Then I tried a VM that's connected directly to the 1.x segment (physically on the server, but totally separate from the 0.x network), and there I could see the packages going back and forth.
So it seems obvious that the server has no idea where to send stuff to 10.x segment, I need to figure out how to tell it that.
-
@mastiff said in How do I allow VNC from one subnet to another?:
from 0.50 to the 10.x segment.
OMG dude... No shit you would not see traffic from 0.x your server is NATTING the traffic to 192.168.1.4 - how else could stuff on the 0 get to the internet... Pfsense has NO clue to the 192.168.0 network..
Your server has only its default gateway right 192.168.1.1 (pfsense) so it sends ALL traffic there that is not local.. Do you maybe have this 192.168.0 with a /16 mask or something??
-
No, it's a 24 mask. But I meant that I don't see any VNC traffic AT ALL when when trying to get from 0.50 to the 10.x segment. So there's no VNC traffic coming out of 1.4 either.
-
Well then you need to figure that out on your downstream server - pfsense can not let you into the 10 network on port 5900 if it never gets there.
Seems pretty impossible if your default gateway is pfsense, unless your server is blocking traffic to rfc1918 space.. Can your 192.168.0.50 box ping say 192.168.1.1?
You would have to allow that on your egenett rules.. I don't recall what they were now..
From the rules you listed - sorry but its not possible for those 192.168.0 boxes to be getting internet through pfsense.. Since rules on that interface only allow access to the egetnet address.. So unless you were using proxy?? On pfsense?
Unless you have rules below what you posted for 5900 dest..
-
Yeah, I know. It has to be lost somewhere on the server, I guess that's because it doesn't know where to send requests to the 10.x subnet. I tried to set up static routes to do that, but it didn't do anything.
And yes, I can ping both the pfSense box and the VM that's running on the Egetnett. So the server should not block 1918. I am not using proxy. And yes, I have other rules, I just cut out the rule for the 5900. Default LAN to any rule should cover that, right? Also now for testing I have a rule on Egetnett allowing anything to Airplay net.
-
FOUND IT! It was the server, and I saw it when I used route print. An old, static route from an experiment several weeks ago was overriding the new static route I had set up. I deleted the old route, and now it works. Thanks for you help!

Edit: The weird thing is that the old route was taking presedence over the new route, which I had with metric 1. I have no idea why.
-
9 days ago in #2 I told you about Asymmetric/check your Routing.

-Rico
-
Rico, turned out that it wasn't that at all. The routing I thought was wrong was only for internal use on the server, I didn't check the RAS routing table, which was correct. So something strange happened in the pc. But now I'm back with the problem, only different. After fiddling with the rules for both airplay and egetnett I see what seems to be happening. I see the VNC packages on the Airplay net, but they are blocked. Because I get this:
Dec 9 20:43:58 AIRPLAY Default deny rule IPv4 (1000000103) 192.168.10.101:5900 192.168.0.50:50613 TCP:SANow that confuses the heck out of me, because I keep getting that even with this rule on the very top of Airplay:

Shouldn't that rule let everything through? Also I can't understand why I'm seeing the internal IP of the client, and not the 192.168.1.4 IP of the server, but perhaps that's the way it is so that the server can send it on to the correct client?