Firewall Rule to Allow RDP from WAN to LAN......Need help
-
Hi everyone,
Here is my setup -
Airtel Internet Modem -->Asus RT-AX88U Wireless Router --->PFsense-->LAN and DMZ
so basically I have a Airtel Modem(192.168.10.1) connected to a hardware router IP- 192.168.50.1 which is connected to Pfsense IP 192.168.50.100(Virtual Machine in Vmware Workstation)
The WAN IP for the Pfsense is 192.168.50.100 and the LAN IP is 192.168.30.1
I have port forwarded port 3389 from Hardware router (Asus RT-AX88U) to the LAN ip- 192.168.30.30.(ie)Also have a the matching port forward rule 192.168.50.109(Machine trying RDP) to 192.168.30.30.
There is a default rule in LAN that says from LAN Net any thing can go any where on any port. I have created a WAN rules that reads:
Protocol Source Source port Destination Destination Port Gateway
TCP any any 192.168.30.30 3389 defaultdo I need to Setup any NAT from WAN to LAN or some thing I have missing here...
Pls advise...
Thanks,
DINU
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
do I need to Setup any NAT from WAN to LAN or some thing I have missing here...
You want to allow RDP from the public internet? Yeah that is BAD freaking idea, have you not been paying attention to the news?
Are you going to lock down the source to a specific IP? If you need to rdp to boxes on your network from outside, I highly suggest you VPN into your network.
You have a triple nat there.. So yeah you would have to forward traffic from your "modem" to your Asus, and then from Asus to pfsense, and then from pfsense to your end IP.
But again I highly suggest you rethink doing such a thing.
-
I am not looking to RDP from Public internet... I am trying to RDP from WAN(Private IP) to LAN IP
My WAN IP is private IP (ie) 192.168.50.X and trying to RDP LAN IP (ie) 192.168.30.X
to Access from public internet I will create Open VPN.. that setup yet to configure...
-
If you want to rdp to something behind pfsense, then yes you have to create port forward in pfsense. If source hitting pfsense wan is also rfc1918, you would also have to disable the default block of rfc1918 address in pfsense.
-
Already both Block private networks and loopback addresses & Block bogon networks in WAN have been untick...
-
And did you allow for rdp from a remote network in your host? Out of the box windows firewall not going to allow rdp from something not on the local network.
-
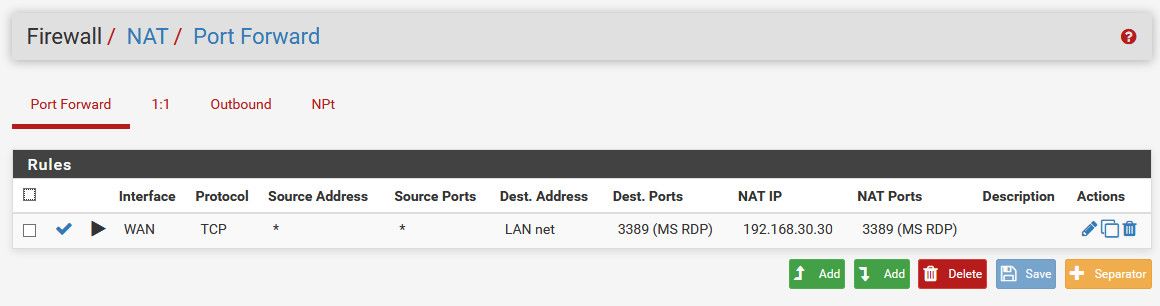
My NAT rule as follows :
Interface Protocol Source Address Source Ports Dest. Address Dest. Ports NAT IP NAT Ports
WAN TCP * * LAN net 3389 (MS RDP) 192.168.30.30 3389 (MS RDP)yes in host RDP access is allowed...
-
Don't set a source port.
You had to go pretty deep into advanced settings and ignore warnings to get to that point.
I'd have to see a diagram to see if setting the source network of LAN net is applicable. It probably should not be set either.
-
Source port is not set it is any (*)
Let me check the advanced settings...
-
How abouts you post an actual screen capture of the rule instead of a textual approximation of the same.
And there are two parts to a port forward. The NAT/PAT rule and the firewall rule. Best you post both.
-
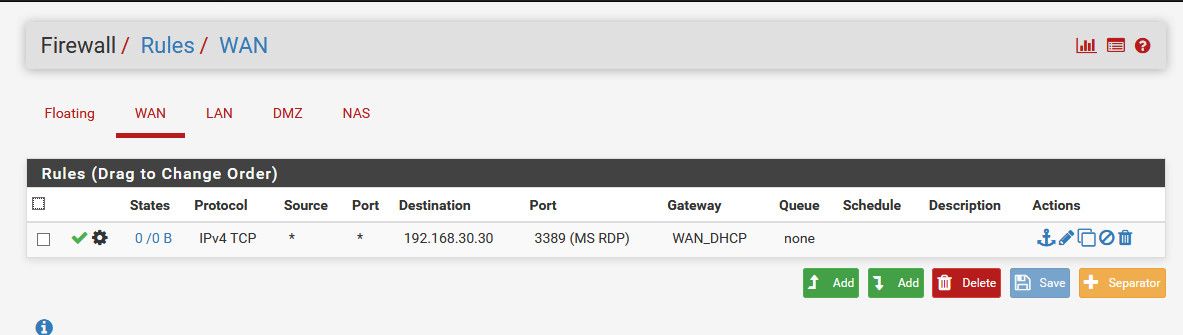
Attach firewall rule & NAT == > WAN
-
OK so you have a port forward on WAN with a destination address of LAN Net. How exactly do you expect that to work?
Why did you set the rule association to Pass? No docs state to do that.
And you are forcing the connection out WAN by setting that gateway on the rule.
-
Any update ???
-
Update? How exactly do you expect such a mess to work??
If you have questions about what something is or means, you need to ask.. Don't just go random clicking shit and picking stuff from the drop down..
To create a port forward in pfsense, really the only thing you have to touch is the port, redirect port, and the IP you want to send it too.. Everything else is going to be pretty much default.
And let the port forward create the firewall rule - which is default..
-
Turn the firewall off on the machine that your are trying to RDP into.
It will treat anything outside its own subnet as public and block it.
Your post with the graphic looks correct although MS recommends a TCP/UDP connection. I do not believe I ever have though. I normally do not leave such a rule in place any longer than I need it.
-
^ looks correct? What are you looking at? It sure not the mess he posted.. Has gateway set on his wan rule, the dest is Lan Net vs wan address in his port forward.
Here is the 3 things that need to be touched to port forward rdp
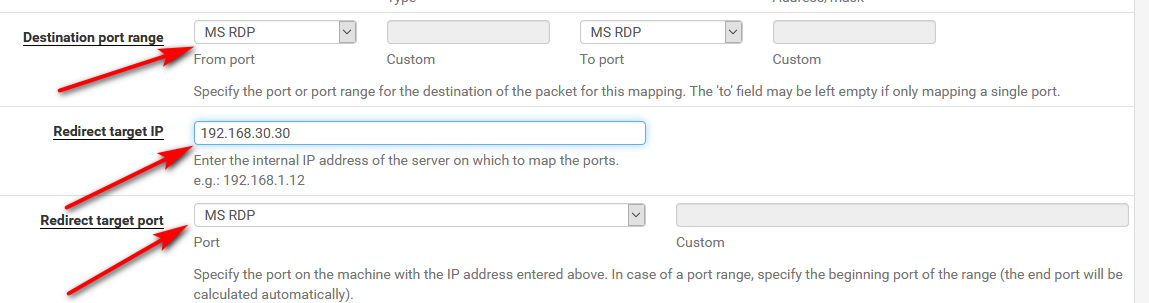
That is it, don't touch anything else - the defaults are all you need. It will create the firewall rule for you. You just need to make sure you turn off the default block rfc1918 rule because your source is actually rfc1918.
edit: Lets get tcp working before he worries about having a UDP connection ;) But sure if he wanted he could change it from default of tcp to tcp/udp.
-
I have tried with NAT Rule that did not helped so used PASS and took the screen shot at that time..
In one of the forum in netgate to mentioned gateway instead of default so I have tried that as well whether it may help...
-
List of things to check is here:
https://docs.netgate.com/pfsense/en/latest/nat/port-forward-troubleshooting.html
-
It should take you like 2 minutes top to trouble shoot a port forward..
Sniff on wan, do you see traffic to 3389? Sniff on Lan - do you see pfsense sending 3389 on to IP you want to send it to..
If you do - your problem is prob firewall on host your sending too, maybe rdp isn't even listening? Maybe it is using a different gateway other than pfsense? Maybe where you wanted to send it is now on a different IP? etc. etc..
Troubleshooting a port forward does not mean randomly changing settings ;)
-
Hi,
And make sure you have enabled "Remote Desktop" on your computer you are trying to RDP :)