Update 2.4.3 to 2.4.4 HAProxy Error code: SSL_ERROR_RX_RECORD_TOO_LONG
-
Re: Problem with new update to HaProxy
My setup is a little different than @cjbujold but essentially the same outcome.I can confirm this is an issue with the way the haproxy package updates and translates the config from haproxy-1.7.10 to haproxy17-1.7.11_1.
In haproxy-1.7.10, my ssl offload frontends have only one backend:
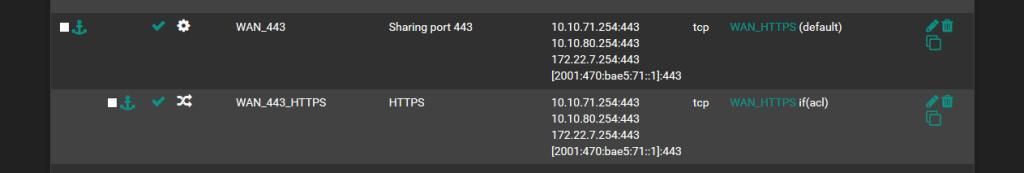
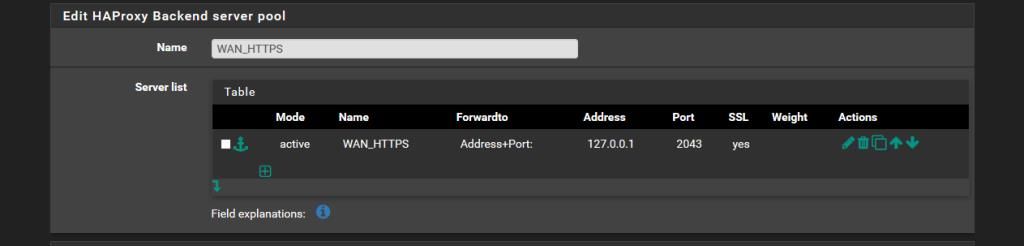
Above you can see that SSL is set to 'yes' in my working 1.7.10 setup but below I only see 'check-ssl' in the rendered config.backend WAN_HTTPS_tcp_ipvANY mode tcp log global balance roundrobin timeout connect 30000 timeout server 7200000 retries 3 server WAN_HTTPS 127.0.0.1:2043 check-ssl verify none resolvers globalresolvers send-proxyAfter updating to haproxy17-1.7.11_1, I suddenly have 2 different backends and a broken config throwing the Error code: SSL_ERROR_RX_RECORD_TOO_LONG that brought me here:
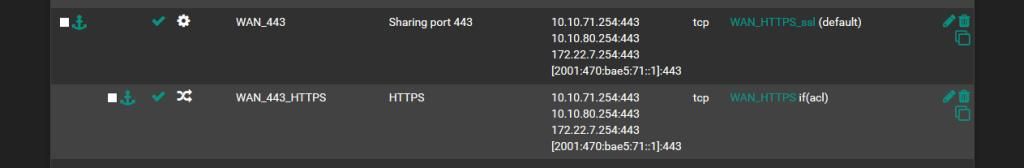
After reading the linked post and fixing my issue, I went back to see what happened and found that when updating the config the Encrypt(SSL) flag gets set on the backend of the same name, not the new shared backend that's been magically created.
It's right there in the rendered config:
backend WAN_HTTPS_ssl_ipvANY mode tcp id 122 log global timeout connect 30000 timeout server 7200000 retries 3 server WAN-HTTPS 127.0.0.1:2043 id 123 check-ssl verify none resolvers globalresolvers send-proxy backend WAN_HTTPS_ipvANY mode tcp id 121 log global timeout connect 30000 timeout server 7200000 retries 3 server WAN-HTTPS 127.0.0.1:2043 id 140 ssl verify none resolvers globalresolvers send-proxyMoving the 'ssl' flag to the magic backend fixes the issue:
backend WAN_HTTPS_ssl_ipvANY mode tcp id 118 log global balance roundrobin timeout connect 30000 timeout server 7200000 retries 3 server WAN_HTTPS 127.0.0.1:2043 id 119 ssl check-ssl verify none resolvers globalresolvers send-proxy backend WAN_HTTPS_ipvANY mode tcp id 117 log global balance roundrobin timeout connect 30000 timeout server 7200000 retries 3 server WAN_HTTPS 127.0.0.1:2043 id 100 resolvers globalresolvers send-proxyHope this helps somebody fix it quick. Users and Devs alike.

Also Charles
-
@WispAwayIS
Hi you can likely resolve the issue by configuring the two separated ssl checkboxes on the backend server configuration properly. Your screenshot above shows an old package version with only 1 ssl checkbox.As for the configuration upgrade in the pfSense package, yes i'm sorry there is a problem in some cases with it. But the package with 2 checkboxes has been around for quite a while now and i don't think i should try and fix the old upgrade code. As it seemed at the time there was a chance it would do the wrong thing either way.. i tried to upgrade it seamlessly but obviously there was a mistake in the 'config upgrade code' somewhere. But now it no-longer needs to 'auto-magically' determine if the backend should or shouldn't use ssl encryption for traffic, for checks or both.. Also i think most users have already upgraded their haproxy package quite a while.. but maybe i'm wrong there..
-
Forget about HAproxy "stable" - it like dinosaur, use only devel version which is "stable and old too but not dinosaur". I hope with pfSense 2.5 it will update to 1.9 or 2.0