[SOLVED] No DNS response from WAN to OPT2 interface
-
Traffic from internal LAN and OPT1 flows out to the Internet and back without problems. Traffic to Internet from LAN and OPT1 works. Traffic between LAN and OPT1 works. Traffic between LAN and OPT2 works. It seems DNS responses received on WAN are not returned to OPT2. pfSense firewall logs show DNS responses going out of OPT2 but packet captures show responses are not coming into OPT2. No other traffic for Internet proceeds because DNS fails. I appreciate any help. I did not attach packet captures for the external WAN but they are consistent with the information above.
WAN is public IP assigned by ISP
LAN - 192.168.0.1/24
OPT1 - 192.168.20.1/24
OPT2 - 192.168.30.1/24
NAT set to pfSense default
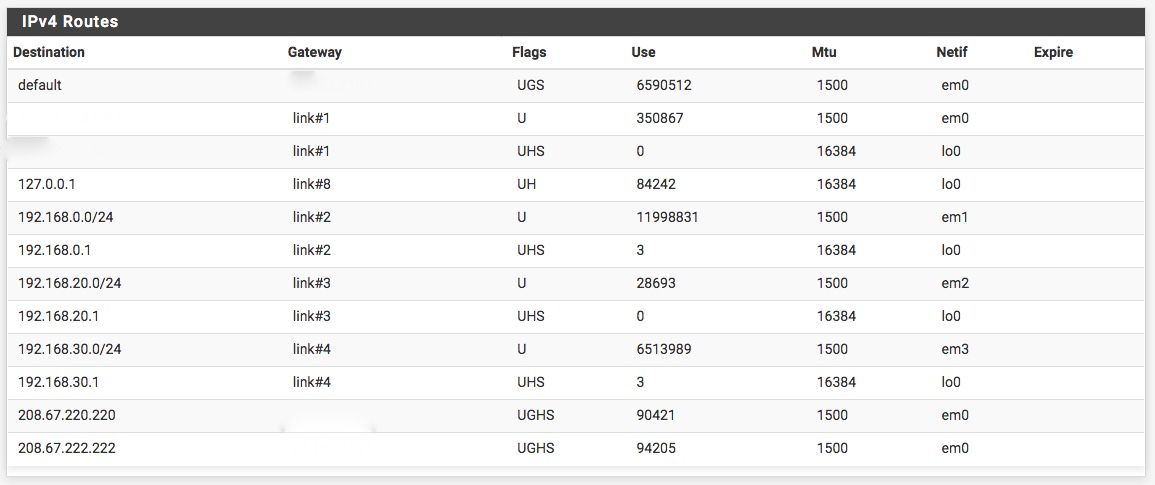
Routing tables look normal
no floating rules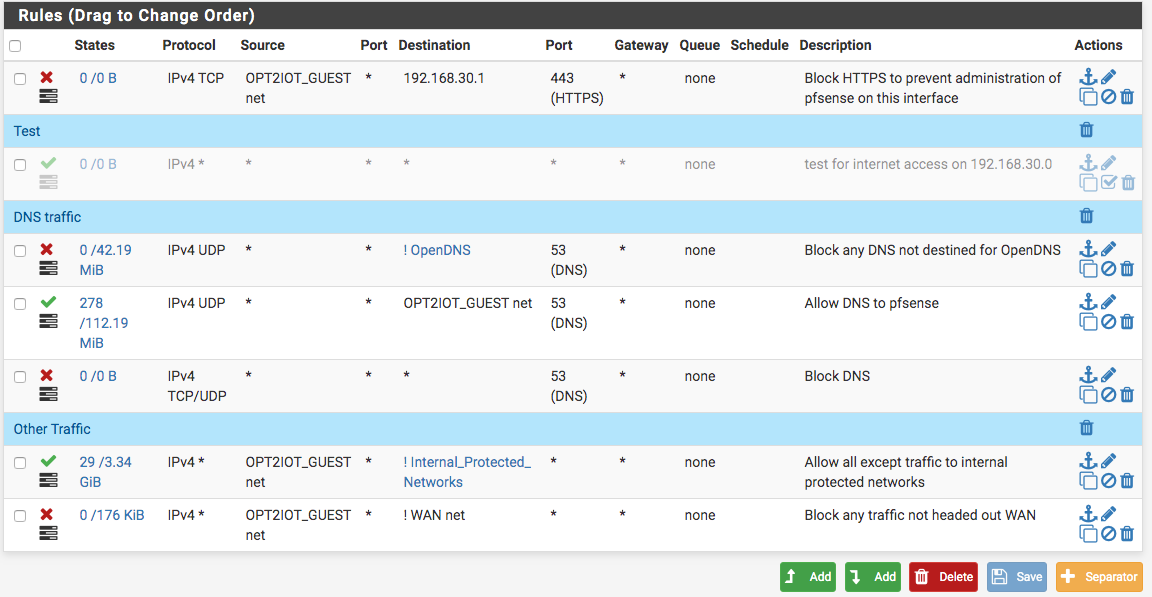
-
What interface is your screenshot from? You cut off the top part, so it’s not clear which one (LAN or an OPT port) we’re looking at.
Jeff
-
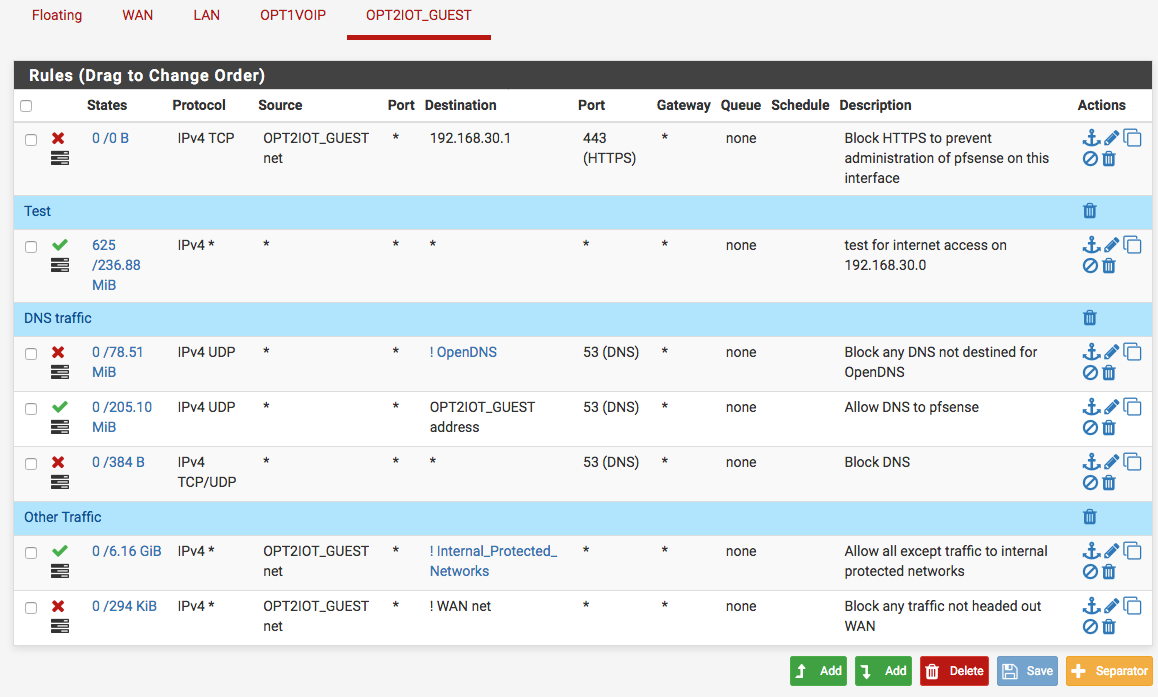
My screenshot is for the OPT2 interface titled OPT2IOT_GUEST. I did not want all interfaces listed in the screenshot so I did not include the list.
-
If you turn on your test rule does it work?
I would make your each "source" the opt interface. May not make a difference but its what I would do..
Destination of the allowed DNS rule should be interface address. I.E. "OPT2IOT_GUEST address".
-
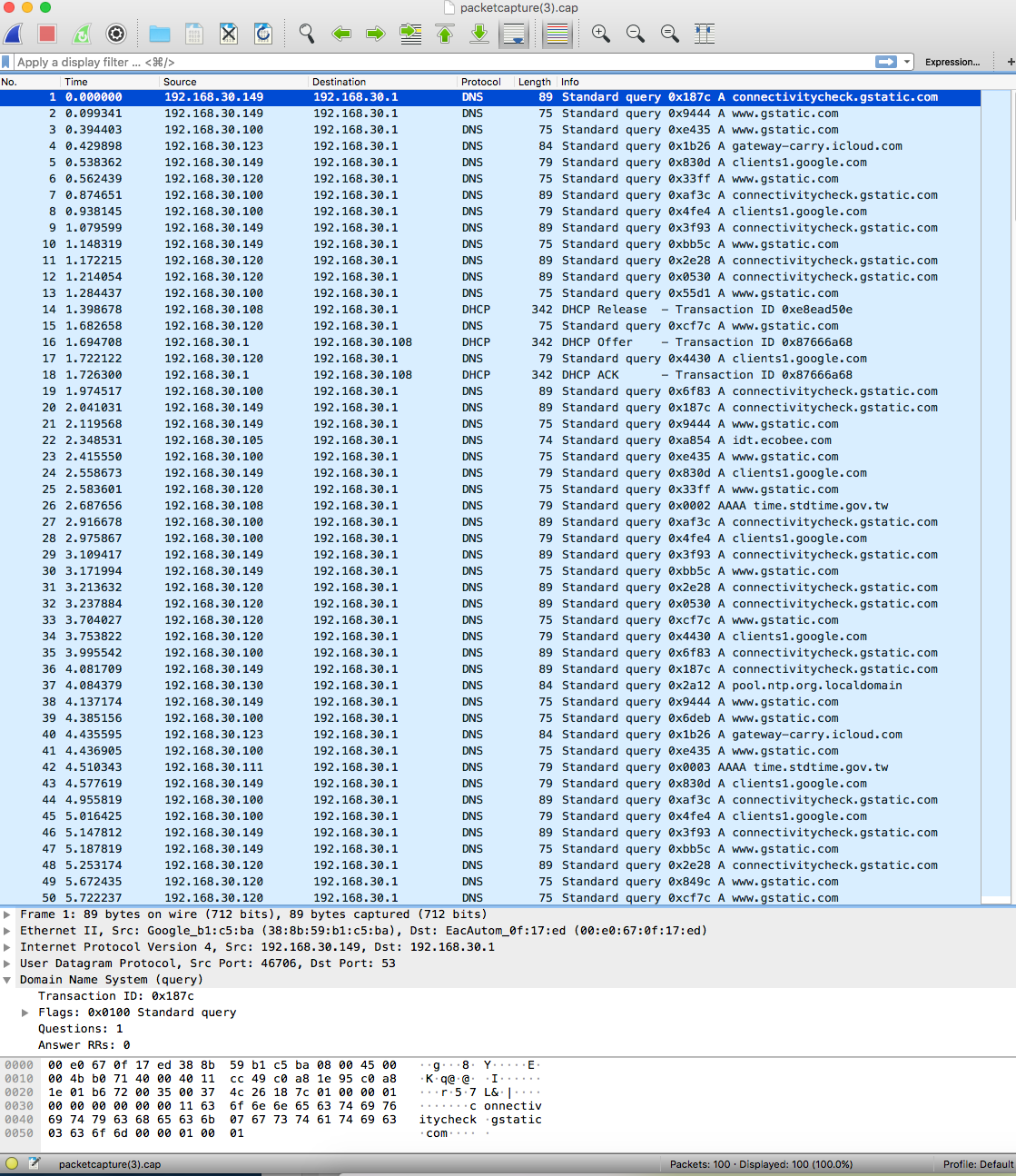
No change with allow all test rule enabled and changing DNS rule destination from OPT2IOT_GUESTnet to OPT2IOT_GUESTaddress. Then reset all states and captured packets below. I am at a loss. It seems like routes or NAT are incorrect, but I cannot find anything wrong there either, but everything works on the other interfaces as expected. Thanks again for any suggestions.
Rules on OPT2
Packet Capture only DNS out (disregarding DHCP) - no responses allowed back to OPT2
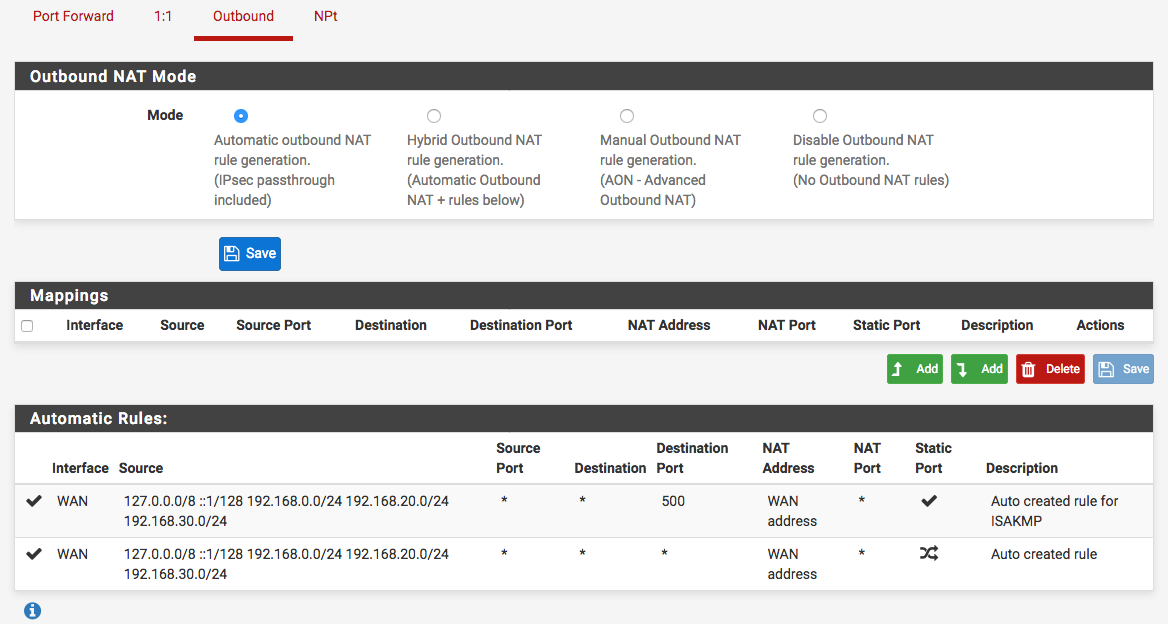
NAT
Routes with public IPs removed
-
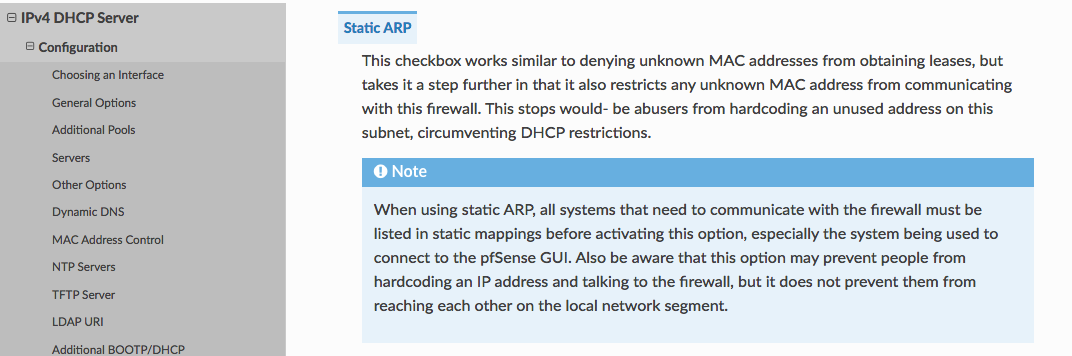
SOLVED - I figured out my problem. It was caused by this setting below (Static ARP under the DHCP Server configuration for the interface), which I had enabled on the interface because I interpreted it incorrectly. It essentially took precedence over any and all allow rules configured for the OPT2 interface, and prevented any host without a statically assigned DHCP address from communicating with the interface even though the host received the dynamic DHCP assignment from the OPT2 interface. I hope this saves other folks time and headache.
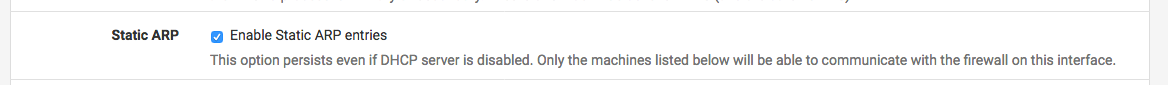
As explained in docs.netgate[.]com