How to reach a webserver when all traffic is encrypted via OpenVPN?
-
I currently have a router that is unable to put into bridge mode but I was able to get pfsense to be part of that dmz in that router which exposed it to the internet. Everything was working fine and I was able to reach my web url. Then I configured PIA via OpenVPN with the LAN and DMZ subnets going through this vpn for the outbound traffic. I've lost connection to this web interface that is sitting on my LAN side. I tried configuring a rule on the firewall that would use the regular WAN GW for that specific 192.168.0.150 address but still unable to reach it form the outside.
here is a diagram before I configured OpenVPN for outgoing traffic to be encrypted.
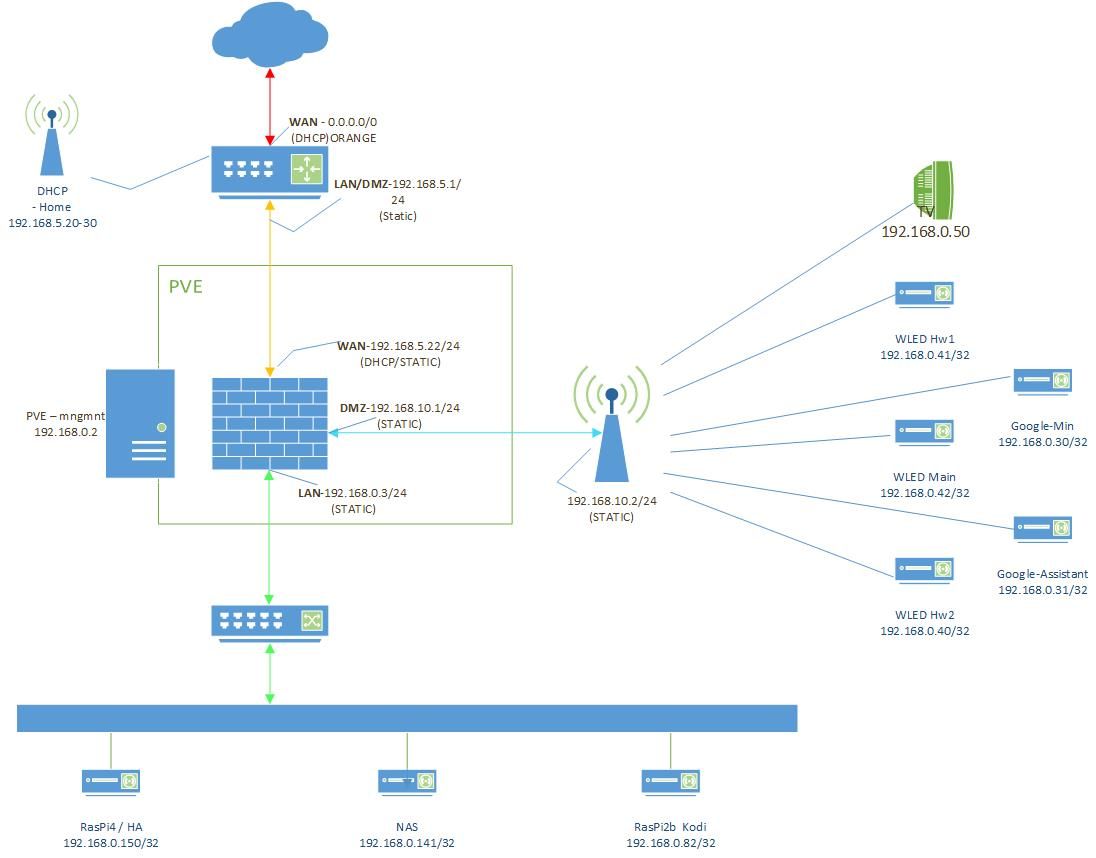
-
What does "DHCP/STATIC" on the WAN interface mean?
If you have a static interface setting ensure there is the routers internal IP added as a gateway to the WAN interface.
Ensure that the VPN tunnel network doesn't overlap with 192.168.0.150.
Does your router masquerading on inbound traffic?
Or if it doesn't is it necessary to see the origin public IP on the webserver? -
@viragomann said in How to reach a webserver when all traffic is encrypted via OpenVPN?:
192.168.0.150
DHCP/STATIC means I get a DHCP address from my router of 192.168.5.22 but I have set it up as a static address under the DHCP server in my router so that it doesn't change. This was the only option available at the time so that my pfSense WAN would get an IP.
My WAN interface has a gateway of 192.168.5.1 which is the LAN side of my Router.
My VPN tunnel IP is a class A so it doesn't overlap with my local Class C
Not sure what you mean by masquerading inbound traffic from my router.
my webserver 192.168.0.150 is on the LAN portion under the pfSense. I had portFWD rule to allow external access. So I changed my pfsense https admin to a different port and then fwd port 443 to go to webserver. This worked but now that I have configured PIA with OpenVPN to encrypt all traffic I have lost all connectivity from the outside trying to reach it.Also I have duckDns configured. I went and tried to update my domain in duckdns to reflect the new PIA VPN IP address. Still failed. Reverted back to my original public IP of the ISP router and it still fails.
-
You won't get it forwarded from the VPN provider.
If you have a gateway defined on WAN pfSense should direct response traffc back correctly.
"Masquerading" is the replacement of the origin IP by the routers IP. Also known as SNAT.
In pfSense that's what the outbound NAT do on WAN interface for outgoing traffic by default.
You can do the same on packets destined to the webserver if you don't care about the origin IPs. -
@viragomann said in How to reach a webserver when all traffic is encrypted via OpenVPN?:
If you have a gateway defined on WAN pfSense should direct response traffc back correctly.
Ok. Yes my pfsense does a NAT from 192.158.0.0/24 to 192.168.5.22 on the WAN and redirects it to my ISP router with that address.
I went to duckdns.org and updated my IP to reflect the ISP's public IP address but it still isn't hitting my router for some reason after x minutes <mydomain.>duckdns.org gets back the VPN IP address.
I'm wondering if I can filter out my 192.168.0.150 to not have incoming or outgoing vpn traffic?
I tried to add an alias and the address and then use the WAN gateway instead of vpn under the LAN interface but that didn't work.