pfBlockerNG devel GeoIP Problems
-
Hi, I've recently started using pfBlockerNG devel after using pi-hole quite happily for a few years. I wanted to eliminate hardware and the new version of pfBlockerNG looks more user friendly than when i used it in its previous form.
The DNSBL side of things works absolutely fine and i am more than happy with that.
However I've had severe problems with the IP blocking side of things. My setup is not that complicated i don't think. I host a few services behind a nginx reverse proxy and i use cloudflare in front of that to obscure my ip address. Personally 99% of the time i only connect to these services through a vpn direct to the pfsense, but i have one external user that just uses the WAN url so comes through whichever cloudflare proxy they get relayed to. I very occasionally use the WAN address too.
I have 2 distinct problems:
-
ignoring the one remote user, which i will come to in the second point, i don't expect anyone anywhere to need to need an inbound connection. Therefore i feel like i should be able to block inbound connections for all GeoIP lists and for "top spammers" block in both directions. This is the approach taken in the best How To guide out there imo, the Lawrence Systems https://www.youtube.com/watch?v=OJ8HHwpGxHw . However despite trying many times this will just not work for me. Even if i try just the top spammers list and just inbound connections this breaks my pfsense in that i lose all external access, it sends the CPU crazy, it becomes unresponsive and if you set this immediately before the cron job runs to update things you can be waiting a long time for it to fail/complete. Further investigation confirms the reason for this is that every single DNS query is blocked by pfBlockerNG. this can be several million queries in just a few minutes, hence the cpu going crazy. It can only be fixed by excluding the country from the top spammers list that i am in (the UK). this makes no sense to me. as i understand it the top spammers list is just that, a list of suspect external ip addresses broken down by country. i don't see any reason why i shouldnt be able to block the whole list inbound and outbound. I've confirmed with another new pfblockerNG user that he experiences exactly the same and is also in the dark as to why it happens given the description of the options set. Finally there are other posts out there on the same topic but none have really satisfactory conclusions, its mostly, just don't do it because you don't want to block the whole world. well, as i understand it i'm not blocking the whole world, just all the top spammers in the world.
-
the second problem relates to the use of cloudflare. i found another post https://www.reddit.com/r/pfBlockerNG/comments/ar81e9/how_to_create_whitelist_ip_rangecloudflare/ where you recommended creating an alias for the list of cloudflare servers using their own list via a url and putting this above the blocked addresses on the ipv4 tab. this all makes sense. However in this other post the suggested solution was to use this cloudflare whitelist to permit outbound. Well thats the opposite of both what i and the user want to do. We are proxying in from a cloudflare server to our WAN address. If i block the world inbound and try and access my server using the WAN address i see all the requests coming from cloudflare servers blocked in pfBlocker reports. BUT the current version of pfBlockerNG devel requires some additional information if you want to use the whitelist for inbound connections. It wants an advanced inbound custom protocol to be set, well thats easy enough, but then it also wants advanced inbound custom port or destination settings, which also have to be set via aliases. Well this final bit is too much for me, i'm afraid i don't understand what it wants from me and a few users i've canvassed are also struggling. There seems to be very little info out there on how to configure this either.
i accept for both issues it could be a misunderstanding on my part of how it is supposed to work rather than any issues with pfBlocker itself, but equally i hope this feedback is useful as i'm not the only one suffering with this confusion :)
for now i have resolved this by only geoblocking top spammers inbound excluding the UK and those countries that i felt were "dangerous" and are not likely to be hosting cloudflare servers, but if its possible i'd like to resolve both the above issues to further harden my setup.
Cheers
-
-
Also seeing the same issue with Top Spammers.
If I enable it and use the default of all the entries, then I get blocked access to the Internet.
If I uncheck the (2) UK entries, then everything works.
I don't use CloudFlare, so not seeing that issue.
-
I think there is a misunderstanding. Top-Spammer in geo-ip blocks the whole country in the list, not just spammers. That is why the USA is not in that list, otherwise it probably would be the first place. It has nothing to do with spammers in particular other than that much spam is coming from those countries.
-
@Bob-Dig thanks for the response but that doesnt explain what is being seen in the first issue i reported.
Even if i try just the top sp*mmers list and just inbound connections this breaks my pfsense in that i lose all external access. I can see in the log that all outbound DNS queries are blocked.
Further, as i say the Lawrence systems video explicitly adds the top sp*mmers list and blocks it both directions.
According to Kapersky, the USA is the second biggest source of sp*m after China...
had to * as the post got flagged as sp*m lol
-
@spaceboy said in pfBlockerNG devel GeoIP Problems:
Further, as i say the Lawrence systems video explicitly adds the top sp*mmers list and blocks it both directions.
This guy is from the US, not the UK.
But sure, you got a point somewhat there with inbound only, that has someone other to explain.
-
bump. hoping for a response from the developer if possible please
-
@spaceboy said in pfBlockerNG devel GeoIP Problems:
Even if i try just the top sp*mmers list and just inbound connections this breaks my pfsense in that i lose all external access. I can see in the log that all outbound DNS queries are blocked.
Hello!
Check the system firewall log for the name of the rule that is blocking your outbound dns requests. It should not be a pfb rule if you are only using it to block inbound.
John
-
Sorry if this has been answered elsewhere, but it seems that this problem still exists.
I have been tinkering with this since yesterday, and, to me, this particular rule have very weird behaviors.Enabling top spammers rule, just for inbound, also kills my internet connection.
Here's the rule, in floating: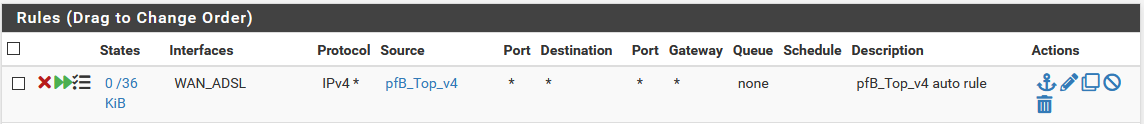
Here are the logs:
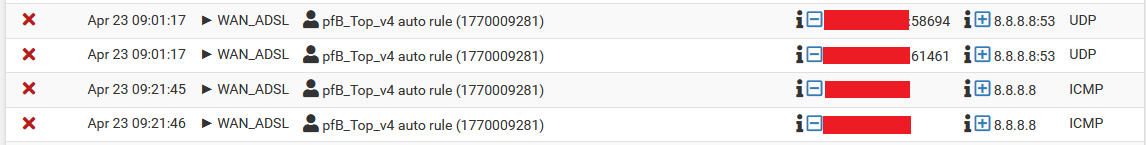
The same logs in text format:
Apr 23 09:01:17,1770009281,pppoe0,WAN_ADSL,block,4,17,UDP,x.x.x.x,8.8.8.8,58694,53,out,US,pfB_Top_v4,8.8.0.0/14,US_v4,dns.google,wan,null,+
Apr 23 09:01:17,1770009281,pppoe0,WAN_ADSL,block,4,17,UDP,x.x.x.x,8.8.8.8,58694,53,out,US,pfB_Top_v4,8.8.0.0/14,US_v4,dns.google,wan,null,-
Apr 23 09:21:45,1770009281,pppoe0,WAN_ADSL,block,4,1,ICMP,x.x.x.x,8.8.8.8,request,52656,out,US,pfB_Top_v4,8.8.0.0/14,US_v4,dns.google,wan,null,+
Apr 23 09:21:46,1770009281,pppoe0,WAN_ADSL,block,4,1,ICMP,x.x.x.x,8.8.8.8,request,49017,out,US,pfB_Top_v4,8.8.0.0/14,US_v4,dns.google,wan,null,+I have found 2 ways to make this work:
=> in the floating auto generated rule, change direction to in (any by default)
=> or, disable "Floating rules" in the "IP Interface/Rules Configuration" of pfBlockerNGBut, a question remains: why does this rule triggers knowing that the source IP of the blocked packets is not in the 8.8.0.0/14 network (it's my public ADSL IP) ???
-
@glab66 just coming back to this many months later to confirm that your solution works.
any chance anyone involved with the development of pfblocker can respond here and confirm if this is a known problem?
thanks!
-
Don't use floating I guess. It is not the default anyways.
-
G Gblenn referenced this topic on