Interface range setup
-
@jt40
My DGS-1100-08's had a tendency of "forgetting their Mgmt IP , if using DHCP.
Kind'a forgot to renew after a while.That's why i switched to using static, when making the config permanent.
But it could be fixed in one of the updates ... Actually i think it is.
Re: Dlink configs.
You can only have 2 configs saved in the switch.You can save & restore configs easily to/from a pc.
/Bingo
-
@bingo600 said in Interface range setup:
@jt40
My DGS-1100-08's had a tendency of "forgetting their Mgmt IP , if using DHCP.
Kind'a forgot to renew after a while.That's why i switched to using static, when making the config permanent.
But it could be fixed in one of the updates ... Actually i think it is.
Re: Dlink configs.
You can only have 2 configs saved in the switch.You can save & restore configs easily to/from a pc.
/Bingo
You genius! Thanks.
I'm digging into the VLANs issue in these days, I found this article about static VLANs: https://eu.dlink.com/uk/en/support/faq/switches/layer-2-gigabit/dgs-series/uk_dgs_1210_setup_static_vlans
I don't understand why they are not tagged... In my case I tagged all of them in the switch plus PfSense, but the DHCP range is always the same...
I'll refresh that service as I did before, pretty sure nothing will change, are you aware of anything like that?
I don't even need to open Wireshark, the first problem is that I get the wrong IP range, that is the one from the UPLINK interface.
This is valid for each port in the switch, regardless if tagged or not assigned.
I'll try this option of untagging, but I can't see the difference right now between not tagging and not a member in this switch... -
@jt40 said in Interface range setup:
I'll try this option of untagging, but I can't see the difference right now between not tagging and not a member in this switch...
You have 3 vlan "modes" in the switch
1:
Not a member -
The specific port will NEVER transport that Vlan2:
Untagged member of Vlan xx (aka PVID or Native vlan) -
The specific port will act as a "Normal Ethernet port used for a PC or other non vlan enabled device", but all data sent/received with no vlan tag , this what a normal PC or other device would do. will (by the switch be "put in" or "gotten from" Vlan xx).
This is what you would use/set for most end devices.
NB: The port can ONLY be member of One untagged Vlan.3:
Tagged member of Vlan xx
Typically used for "Multi vlan capable devices".
Ie. Other switches , an AP (with multi SSID's) etc ...
You would at some time prob. use this for your UBI AP's.
You might even use both tagged (for SSID's) and untagged (for mgmt)I gave a brief intro to tagging here and a few posts down:
https://forum.netgate.com/post/944381/Bingo
-
@bingo600 said in Interface range setup:
@jt40 said in Interface range setup:
I'll try this option of untagging, but I can't see the difference right now between not tagging and not a member in this switch...
You have 3 vlan "modes" in the switch
1:
Not a member -
The specific port will NEVER transport that Vlan2:
Untagged member of Vlan xx (aka PVID or Native vlan) -
The specific port will act as a "Normal Ethernet port used for a PC or other non vlan enabled device", but all data sent/received with no vlan tag , this what a normal PC or other device would do. will (by the switch be "put in" or "gotten from" Vlan xx).
This is what you would use/set for most end devices.
NB: The port can ONLY be member of One untagged Vlan.3:
Tagged member of Vlan xx
Typically used for "Multi vlan capable devices".
Ie. Other switches , an AP (with multi SSID's) etc ...
You would at some time prob. use this for your UBI AP's.
You might even use both tagged (for SSID's) and untagged (for mgmt)I gave a brief intro to tagging here and a few posts down:
https://forum.netgate.com/post/944381/Bingo
So you mean the following?
- Untagged (The VLAN ID remains in that device that defines the VLAN) Why I should set this for my PC for example?
- Tagged (The VLAN ID will be included in the packet frames, plus it supports multi VLANs on the same port)
- Not a member (Not even a chance to set a VLAN, right? Or you can set it up but it remains always confined in that device?)
I understood that I always need to use VLAN tag for the following reasons:
- Well I need VLANs :D
- I need to use multi VLANs on the same port in most cases
- This is especially valid in the AP, I'll use multi SSID.
-
@jt40 said in Interface range setup:
Untagged (The VLAN ID remains in that device that defines the VLAN) Why I should set this for my PC for example?
Because you want whatever plugged into that port to be on vlan X.. And not have to tell that device to tag their traffic.
If you want PC to be on vlan X, the port on your switch you connect the PC would be set to vlan X with a pvid to X.. This tells the switch, hey any untagged traffic you see coming into this port is vlan X. Only send traffic out this port if too vlan X..
Understanding tagging and what a native vlan (untagged) is really step 1 in wanting to use a vlan capable switch and vlans on your network. Until you grasp the concept your not going to make much progress in using vlans on your network.
I need to use multi VLANs on the same port in most cases
This not normally true.. The only ports where you would carry multiple vlans would be ports that connect to other switches, or an AP or say a router where you need to carry multiple vlans over a single physical interface. Most devices connected to a switch would only ever be in a single vlan.. Other option where you might need to tag traffic is to say a VM host, where again you need to carry multiple vlan traffic over a single port, and you need something to understand what traffic goes where via the tag, or the lack of a tag.
With unifi AP, the management of that is normally untagged.. They not that long ago did enable the ability to use tagged traffic. But that is so far beyond your current grasp of vlans, save that for another day..
The port connected to your AP for example would carry untagged (native vlan) traffic for the vlan your management IP is in on the AP, and tagged traffic for any SSIDs you want to be in other vlans.
edit: here is a drawing I did many ages ago trying to help someone understand where tag and untagged go on a switch infrastructure.
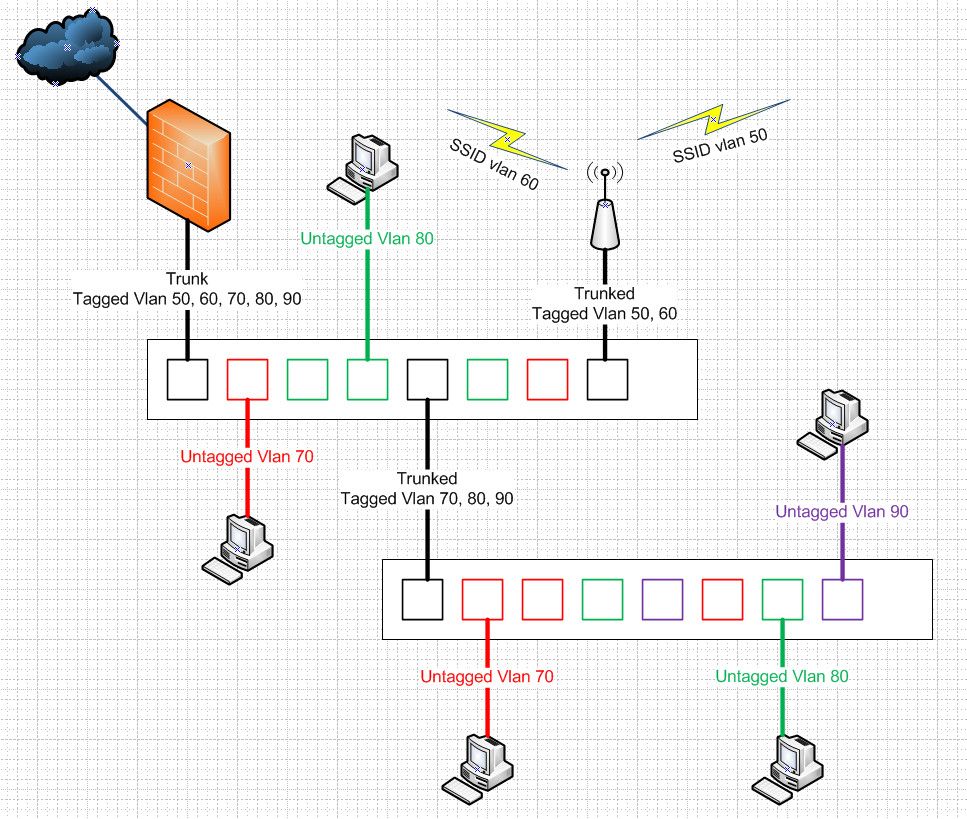
It is missing the untagged for the management of the AP, and possible any native network you had setup on the pfsense interface where the vlans 50,60, etc. are riding on.
-
@johnpoz Thank you, let's see if I understood.
The reason why I said I want to use VLAN tag everywhere, it's because I want every machine to be isolated, maybe in the future I'll ease some protocol but that's it (through FW rules, VLAN doesn't play much in it if the FW allows the traffic), that's the starting point for me.
Does it make sense to tag each interface is this case?I also know that I need truncate the port where multiple VLANs are tagged, for example the UPLINK interface, but not necessarily if there is only one VLAN tagged there and where others not tagged pass through, is it correct?
In my case, whatever traffic goes to the UPLINK most probably goes on Internet, so I truncate the port and tag everything.In any case, even if I tag only one VLAN on one port and there is only one end-user device attached to it, what can be the problem? What will stop the traffic? I don't trunkate the port but I'll have a single VLAN there.
The only useful and automated case I can think of is when you want that machine to communicate only in the LAN, precisely only in that network range, basically the default one of the switch, in my case given by the DHCP from the UPLINK/DOWNLINK interface in PfSense.
Hence, I skip the tag here and the traffic can't go on the next network node (PfSense), or eventually not out of that default network range in the LAN... -
@jt40 said in Interface range setup:
@johnpoz Thank you, let's see if I understood.
The reason why I said I want to use VLAN tag everywhere, it's because I want every machine to be isolatedThere are switches that provide such isolation. I think trying to do that with VLANs would be a real mess, if you have many systems.
-
@jt40 said in Interface range setup:
VLAN tag everywhere, it's because I want every machine to be isolated
WTF does that have to do with tagging everywhere? I don't think you grasp the concept at all..
If you want EVERY machine to be isolated then you need to setup private vlans on your switch.. They would still be in some vlan X, the switch would just keep them from talking to each other.
Did we not already go over this, or was that some other thread. It comes up quite often.
https://en.wikipedia.org/wiki/Private_VLAN
In the wireless world its called AP or Client isolation
whatever traffic goes to the UPLINK most probably goes on Internet, so I truncate the port and tag everything.
What??? The router is what isolates traffic at Layer 3.. Vlans isolate at Layer 2.. Your "uplink" from your router the internet has no need to know anything about any vlan IDS and unless you were getting multiple vlans from your ISP for different things like TV or voip, etc. There is no need to have anything to do with tagging on your pfsense wan interface.
I think your confusing vlans and what routing actually does..
-
@johnpoz said in Interface range setup:
unless you were getting multiple vlans from your ISP
Do ISPs provide VLANs? My IPTV is on the same subnet as my Internet connection. My home phone is connected to the same box, but I don't know the details of what's behind it.
I have seen VLANs from carriers over fibre, where they'll use QinQ, allowing one VLAN level for the customer and one for the carrier to separate customers. However, they'd be providing layer 2 connections, not 3, as you'd get from an ISP. Over IP you'd route the different subnets and not use VLANs.
-
@jt40
Could you please tell what D-Link switch model(s) you are using ?/Bingo
-
@jknott
In Europe it's quite normal that your ISP Box has multi-vlans comming in, if using cable or fiber.Vlan xx - VoIP
Vlan yy - TV
Vlan zz - InternetSo it can sometimes be "tricky" to get a pfSense to replace the ISP Box.
/Bingo
-
@bingo600 said in Interface range setup:
@jt40
Could you please tell what D-Link switch model(s) you are using ?/Bingo
I think I mentioned it previously, DGS-1210-16 , it has also Private VLANs but I didn't test it yet.
-
@jt40 said in Interface range setup:
it has also Private VLANs but I didn't test it yet.
Good - I would get just basic vlans working first... Put some devices in vlan X, create your vlan Y or Z or whatever for your wifi.. Get them working.
Then if you don't want pc1 talking pc2 that are in vlan X.. Then play with setting that as a private vlan in your switch.
But with just a couple of vlans you can get the handle on firewall rules allowing or blocking access between vlans, etc..
Once you got the basic setup - you can tweak and edit and config all you want to get it exactly how you want. But you have to learn to crawl before your running in the 400 meter dash for a Olympic gold medal ;)
-
@bingo600 said in Interface range setup:
In Europe it's quite normal that your ISP Box has multi-vlans comming in, if using cable or fiber
Are those actually coming in? Or just created at the box? The normal way would be to route the subnets to the appropriate LAN/VLAN.
For example, I run my guest WiFi on VLAN3. If I desired, I could configure a similar network elsewhere and route between the guest LANs through a VPN, without using VLANs. It's just basic routing. On the other hand, your ISP's box might be configured with different MAC addresses for the different services. So, there could be a few different ways to get those "VLANs" to a customer, without using VLANs directly from their office. Regardless, you don't see VLANs on IP, as they're layer 2, not 3.
-
@jknott normally this comes into play when user is trying to replace their isp device that handles the vlans from the isp automagically for the user..
The box quite often has a port you plug in your voip phone, and connection for your tv, etc.
Yes normally would split those out with a switch in front of pfsense, etc. And pfsense wan wouldn't have to know anything about the vlan or its tag..
I brought it up only as a point of discussion - trying to point out unless you have a not so common setup, or trying to do something specific based up your isp or wan connection pfsense is connected to. The wan interface has no need for any sort of vlan tag.
But there are some situations where you might want/need to do such a thing... I would bet my left nut none of that has anything to do with the OP setup. This discussion in multiple threads has been on going for what seems like years already ;)
There is a lack of understanding of basic networking concepts going on - what a network is, and how the mask defines that, how routing works, how firewall rules work, what a vlan is, what tag on a vlan is, etc.
It seems the OP has some grand plan in his head that he wants to get to - but doesn't understand the underlying concepts needed to implement it. What I have been trying to do from the get go is for him to get a basic working system. A wan/lan setup on pfsense where his clients can get to the internet ;) And then can move on from there.. But even that has been difficult road..
-
@jt40 said in Interface range setup:
@bingo600 said in Interface range setup:
@jt40
Could you please tell what D-Link switch model(s) you are using ?/Bingo
I think I mentioned it previously, DGS-1210-16 , it has also Private VLANs but I didn't test it yet.
Is D-Link calling "private vlan" for Assymetric vlan ??
This smells a bit of "private vlan" , but there's no explanation for the D-Link example
1:
https://eu.dlink.com/uk/en/support/faq/switches/layer-2-gigabit/dgs-series/uk_how_to_configure_vlan_asymmetric_dgs_1210_series2:
https://www.techsupportforum.com/threads/solved-d-link-dgs-1210-16.612703/3:
http://savazzi.net/internet/VLANs_on_DGS-1210.htm
http://savazzi.net/internet/VLANs_on_DGS-1210_2.htm/Bingo.
-
@bingo600 said in Interface range setup:
@jt40 said in Interface range setup:
@bingo600 said in Interface range setup:
@jt40
Could you please tell what D-Link switch model(s) you are using ?/Bingo
I think I mentioned it previously, DGS-1210-16 , it has also Private VLANs but I didn't test it yet.
Is D-Link calling "private vlan" for Assymetric vlan ??
This smells a bit of "private vlan" , but there's no explanation for the D-Link example
1:
https://eu.dlink.com/uk/en/support/faq/switches/layer-2-gigabit/dgs-series/uk_how_to_configure_vlan_asymmetric_dgs_1210_series2:
https://www.techsupportforum.com/threads/solved-d-link-dgs-1210-16.612703/3:
http://savazzi.net/internet/VLANs_on_DGS-1210.htm
http://savazzi.net/internet/VLANs_on_DGS-1210_2.htm/Bingo.
Yes, the explanation on the DLink interface leads to private VLANs (there is a link in localhost with an example), then there is another page where you can set the PVID.
Not sure why there are 2 pages for VLANs and Private VLANs, all in one page was too difficult :D .I'll reply to the others when I find some time to go deeper into this issue, thanks to everyone for now.
-
The adventure with DHCP on the switch just started :D
-
I tried to delete the previous IP interfaces from the switch, all of them plus the management, I can't access anymore the switch, it died in that way :D
I did it because I could not activate DHCP for the management interface, it was saying that I need to remove all the IP interfaces defined, 2 of them were for testing, the last one was the one auto-created by the switch, in fact it had assigned the IP for the management interface.
Just to remind you, my switch has a few L3 capabilities, as basis, obviously IP based stuff. -
I factory reset the switch, loaded the previous config, no error message and it was successful, but nothing changed.
- I rebooted, nothing changed
- I reloaded again the config, saved as the config 2, nothig changed.
- I changed the boot profile n.2, rebooted, nothing changed.
- In this specific topic, it must be a bug with the switch...
This is blocking my current VLAN setup, I don't want to re-setup again all from scratch, moreover, I need to discover what's wrong with this restore process, it has to work, in the future it can be extremely useful and I will almost depend from it.
The issue could be a conflict with the fact that I wasn't able to remove the last IP management interface. I didn't receive any error message though...
For the moment, the easy way to avoid it is to set up DHCP prior any change.On the other side, after the factory restore every device got a new IP, including the AP and the subsequent devices. At least one positive news :) .
I'll test the same again changing just a few things and making a new backup restore... Just to see if the IP config was the only hidden conflict. -
-
@jt40 said in Interface range setup:
loaded the previous config
Why.. Dude just reset the thing to factory.. Now it should come up as dumb switch everything in vlan 1, the default vlan. Plug it into your 1 network on pfsense.. Everything working all on the same LAN network.
Now set the management IP on the switch to be in your LAN network..
Get everything working this way.. Then an only then move towards adding a vlan..
Create the vlan on pfsense, assign this vlan to your lan interface on pfsense. Set this vlan up IP, dhcp, etc. firewall rules on the interface. I would start with any any until you got things working - you can then restrict your rules.
Now on your switch create your vlan with the ID you set in pfsense. Set the port that connects lan of pfsense to switch with your vlan TAGGED (often called trunk mode). So default vlan will be untagged and your new vlan will be tagged).. Now on the switch set a port to be in this vlan, untagged (normally called access mode).
Now connect a device, laptop, pc to this vlan port you setup on your switch - you should get dhcp from pfsense that you setup when you setup this vlan, etc.
Baby steps!! Get that working.. Now you know how to create vlans, and how to get them working on your switch. Now you can move on to your AP and setting up SSIDs on different vlans, etc.
-
@johnpoz said in Interface range setup:
Set the port that connects lan of pfsense to switch with your vlan TAGGED (often called trunk mode). So default vlan will be untagged and your new vlan will be tagged).. Now on the switch set a port to be in this vlan, untagged (normally called access mode).
Thanks, ok I'll follow the easy way for now.
Can you re-phrase it please? :)
You told me to do the following:- Create a VLAN in PfSense
- Create the same on the switch, TAGGED
- Assign the VLAN to the uplink port as UNTAGGED
I think that you wanted to say the following:
- Create a 2 VLANs in PfSense
- Create the same on the switch, one UNTAGGED for default traffic and the other TAGGED
- Assign the VLANs to the uplink port, UNTAGGED and TAGGED respectively
Then test the UNTAGGED and TAGGED mode.
Assuming that the above is correct, I have a question about the VLAN assignment on the UPLINK port.
Do I need to assign each VLAN in PfSense and the switch on the same respective port (UPLINK - DOWNLINK)?The following is only an observation, the UPLINK port should only let the traffic through, so I guess it should be only a VLAN UNTAGGED or without VLAN at this point, but the other ports should have the VLAN setup, what do you think?