Multi threading and Snort and Programming questions
-
Hello does anyone know if Snort utilizes multi threading? I was looking at the open source code it does not seem to from the sections I looked at. I am a currently a college programming student that is specializing in cyber security. I also noticed that decoy scans with Nmaps if set to the same IP of the host caused issues with Palo Alto Firewalls that they would block that IP and close the connection to the routers when lab testing.
I was wondering if there is a way to code a black hole area for this situation with a separate thread, the hacker would think it worked however system stays online. I was also working last week on a lab and noticed a scan when ran on a host it had the ability to kick back thousands of http get requests to the attacker to stall him, one just returned nothing but ABCDE.... What if we could make it return positive things when scans are ran?

Positive scan returns that mimic the scans so the hacker has confusion and only sees positive words of encouragement. This is my code in Python. If it had threads you could have this reply running and keep working.
-
Imagine the faces of the guys running decoy scans non stop if this was the reply.
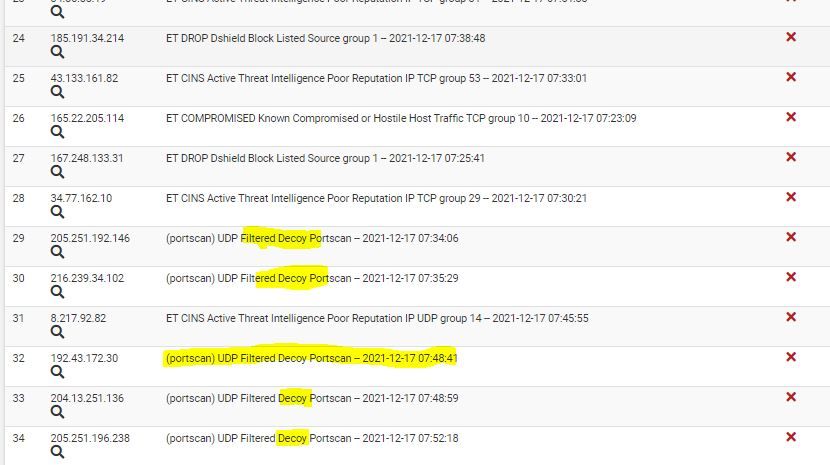
I get hit with more decoy scans with UDP scans over anything else. Nothing stops hackers like positive words coming from the firewall. A firewalls that is Adaptable, empowering, and honorable sorry I spelled that wrong in file for the array it was iterating over with use of pop.
-
We could maybe adapt the reply that is returned when the endless UDP scans are ran. They get worse every day like something is being planned same IP addresses on my system also. Why UDP scans? why not TCP? I don't know what has prompted the attackers to do this. However, I thought why not use the code I worked on in Sierra College's Python class.

I was also doing a lab and I was confused because one scan kicked back replies that were actually HTTP GET requests directed at my system because I was scanning. However I feel that would make an attacker more angry. Positive words like this would confuse an attacker and he might just move on.
-
-
And, if they move to make this reply as a DOS move it to HTTP get requests at that point and disable this reply for a pre set timer.
