Static route over OpenVPN VPN
-
@aziz-1
Make your server tunnel settings like this: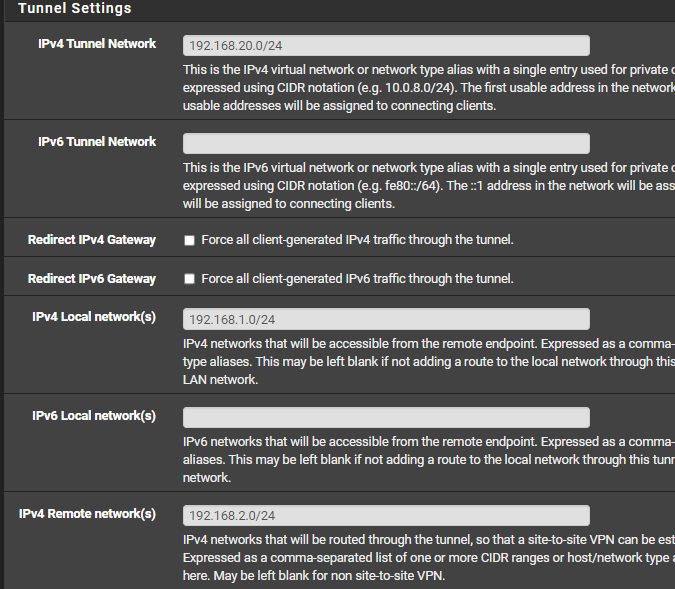
Make your client tunnel settings:
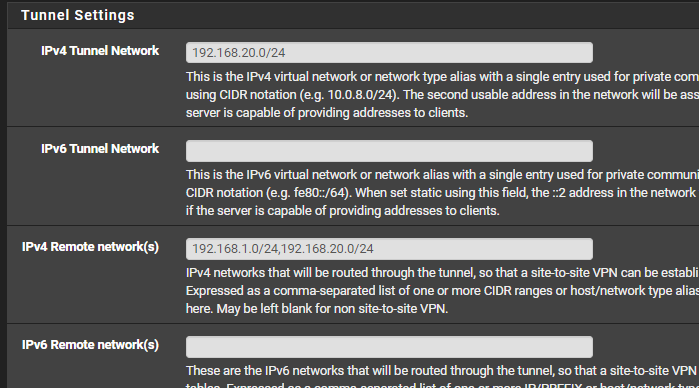
You don't need to add gateways or routes.
That's all you need to do.If this is only going to be the two sites, you should make it a site to site as described above.
-
@Jarhead Server side I have a PFSense v2.5.2Release(amd64)
Client side I have an Embedded OpenVPN.
I applied both config you mentioned at Server and Client side.Client side it's working : can ping LAN1 from LAN2.
Server side, I start suspecting something wrong with this version. I can't ping LAN2 from LAN1. Trace route shows the below (pinging from 192.168.2.103 from 192.168.1.80) :
1 <1ms <1ms <1ms 192.168.1.1
2 * * * Request timed out
3 * * * Request timed outWhile it should be :
1 <1ms <1ms <1ms 192.168.1.1
2 Xms Xms Xms 192.168.20.1
3 Yms Yms Yms 192.168.10.80Like if the server is not taking in consideration the tunnel to the client subnet LAN2 when routing traffic !
-
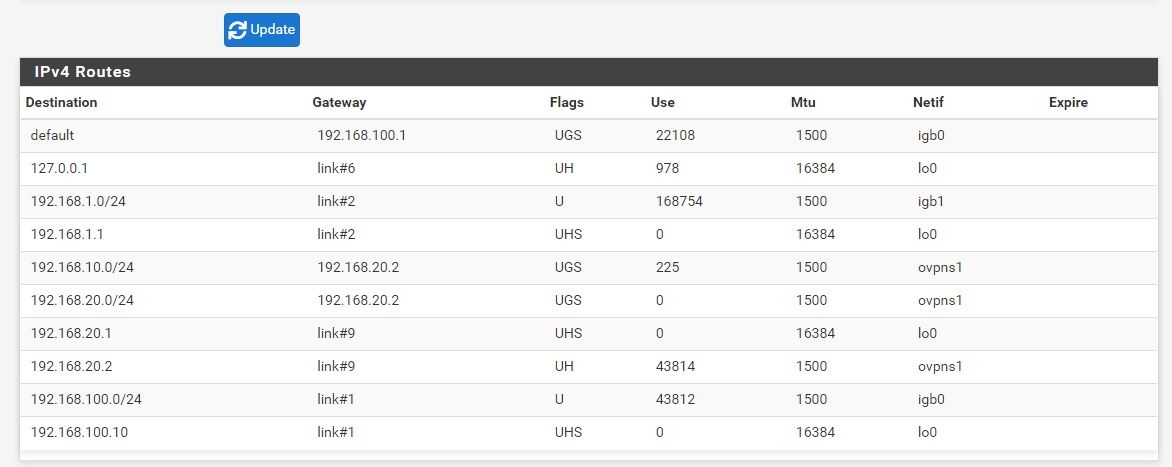
@aziz-1 Check your routes in Diagnostic/Routes
-
@aziz-1
You have to set the tunnel network mask to /30 for a site to site VPN with one server and only one client.If you have a larger tunnel you would need to configure a CSO for the client to route the network behind the client properly.
As well as already mentioned, set the routes in the OpenVPN settings on both sites instead of static ones.
-
-
@viragomann Thanks Viragomann
No static routes configured so far
The problem is no traffic from LAN1 (server side) to LAN2 (client side) => no ping unless routes are there -
@aziz-1 You don't have a route to the 2.0 network.
post an image of the server openvpn config. -
@aziz-1 said in Static route over OpenVPN VPN:
The problem is no traffic from LAN1 (server side) to LAN2 (client side) => no ping unless routes are there
I know, but you should start with properly setting up your VPN connection.
If you can access site A from site B, but not the other way round, it's not a routing issue at all.
It would be rather an issue on site A due either not allowing the access by the router or the LAN devices are blocking access from outside of their subnet. -
@jarhead ahhh sorry, I lately restored a config with 192.168.10.0 instead of 192.168.2.0 (those are the same LAN)
The route to 192.168.10.0 is there in the table -
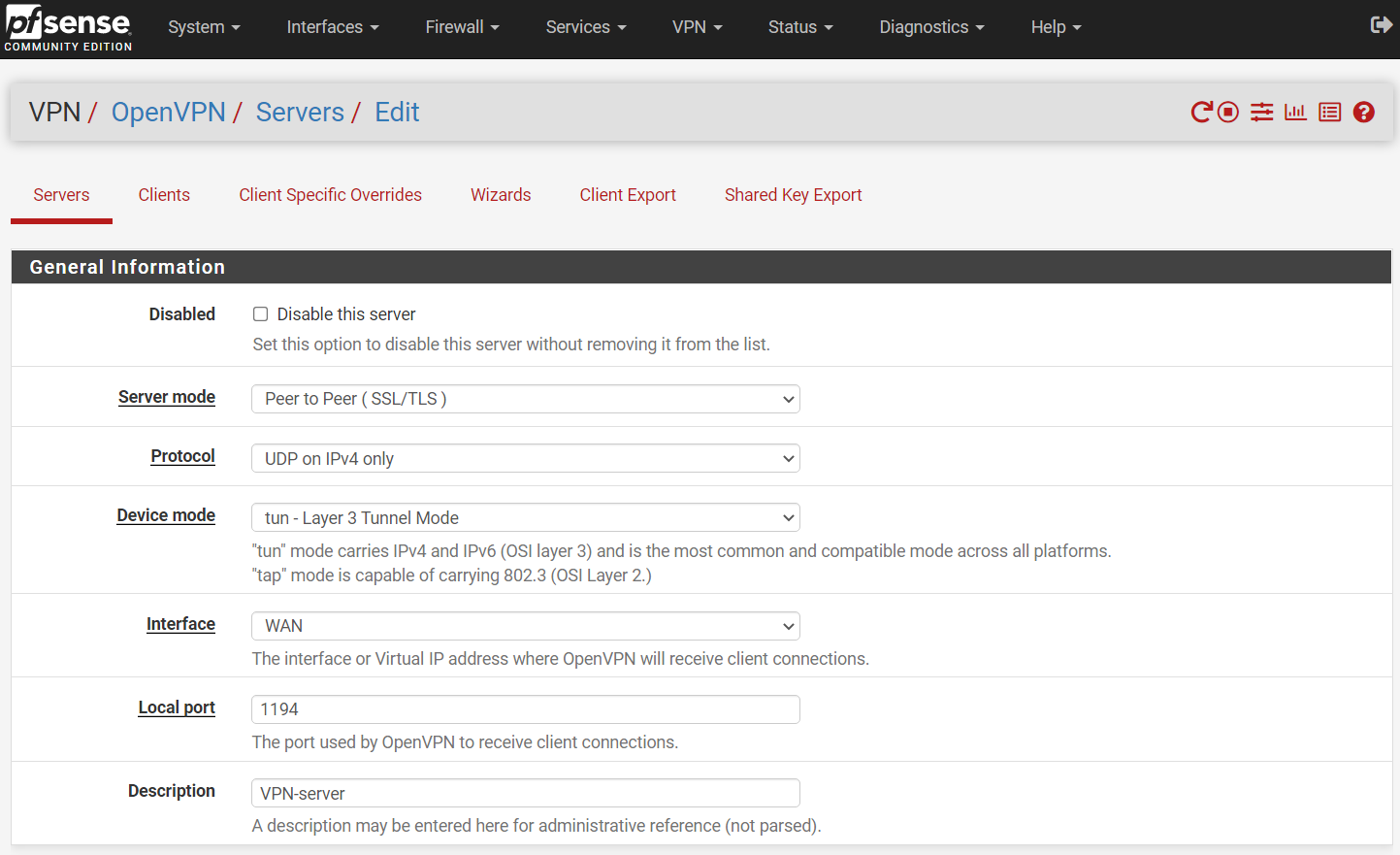
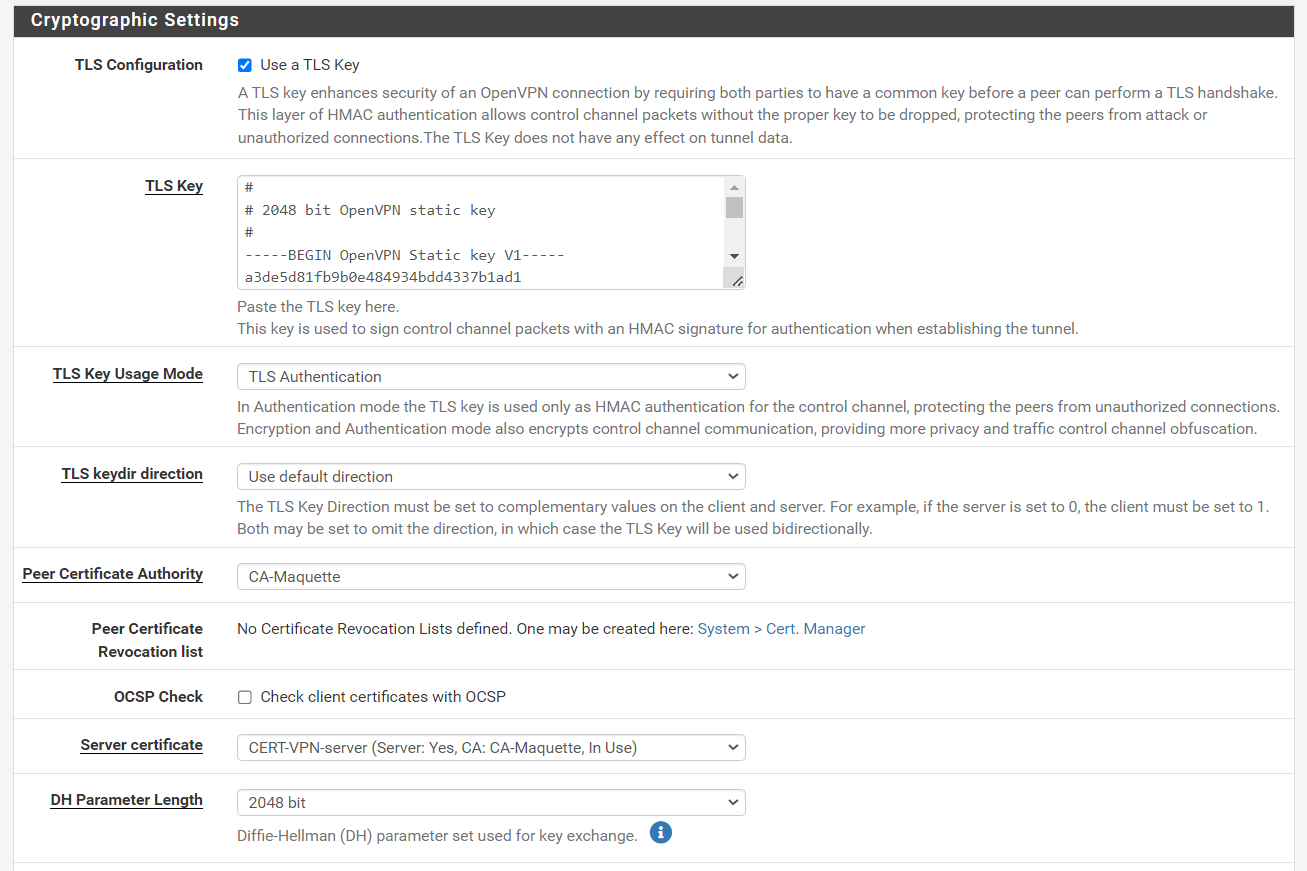
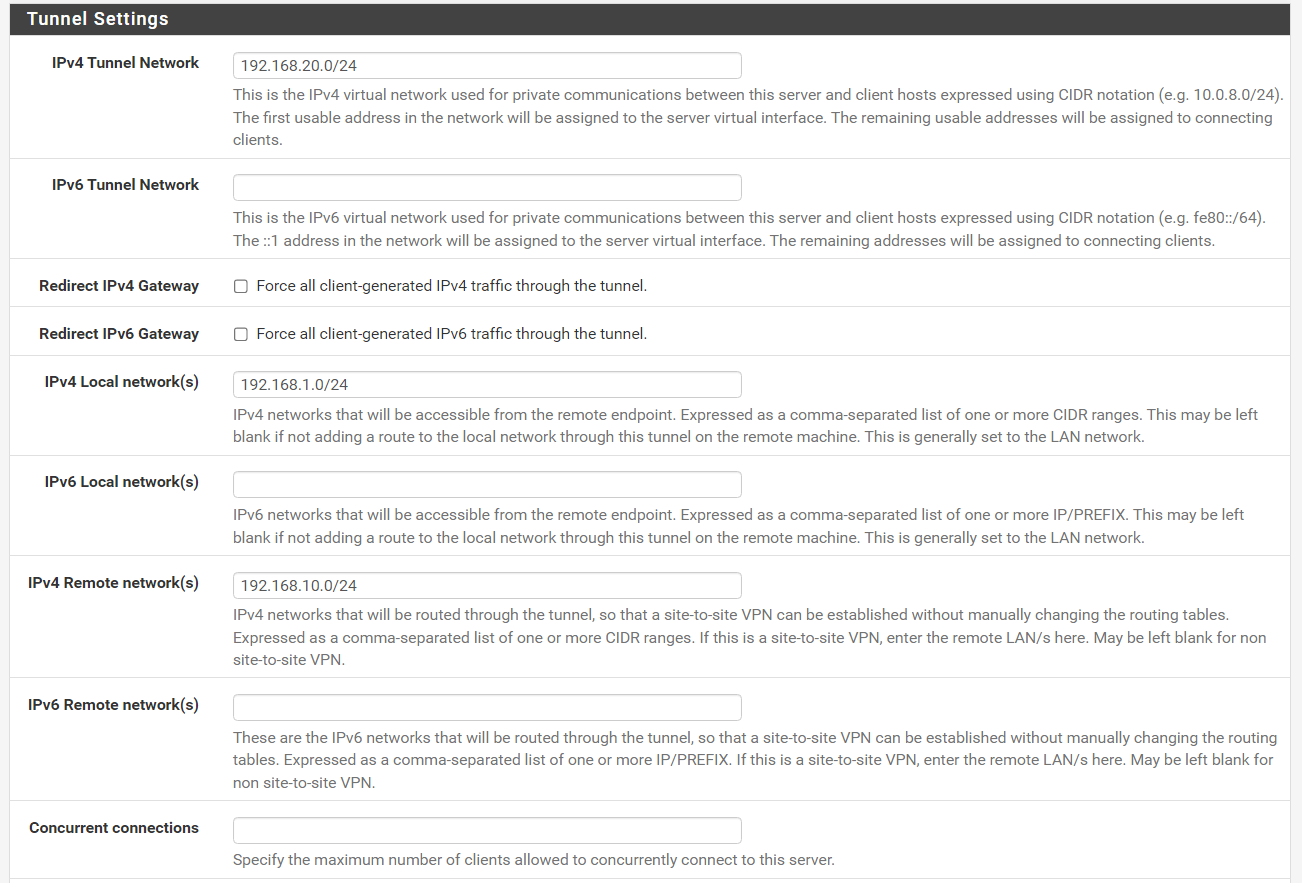
-
@aziz-1 So you changed it to a site to site?
Change the tunnel address to a /30 ( or even better a /31 ) on both sides. -
@viragomann in both test machines : 1.80 and 10.103 (or 2.103 before) I use Wireshark to detect incoming traffic so that the local windows firewall can't be an issue
-
@aziz-1 said in Static route over OpenVPN VPN:
in both test machines : 1.80 and 10.103 (or 2.103 before) I use Wireshark to detect incoming traffic so that the local windows firewall can't be an issueNetwork sniffing with Wireshark or whatever taps the packets in front of the firewall. So seeing the incoming packets says nothing.
Did you also see responses? -
@viragomann I test the ping and the tracert while running wireshark in every test machine so to be sure of having traffic between them
Actually I m in 10.103 remote logged to 1.80
In the other direction : while in 1.80 I can't access 10.1 router GUI nor ping or remote log to 10.103 -
Yes, I got this already from your first post.
However, any connections have packets flow in both directions. There are request packets and responses. And I was asking if you see both on both sites.
Here you can see both:
16:25:16.281216 IP 10.10.81.11 > 10.10.76.53: ICMP echo request, id 1, seq 5, length 40 16:25:16.281454 IP 10.10.76.53 > 10.10.81.11: ICMP echo reply, id 1, seq 5, length 40 16:25:17.288271 IP 10.10.81.11 > 10.10.76.53: ICMP echo request, id 1, seq 6, length 40 16:25:17.288458 IP 10.10.76.53 > 10.10.81.11: ICMP echo reply, id 1, seq 6, length 40 16:25:18.303884 IP 10.10.81.11 > 10.10.76.53: ICMP echo request, id 1, seq 7, length 40 16:25:18.304076 IP 10.10.76.53 > 10.10.81.11: ICMP echo reply, id 1, seq 7, length 40Here we see requests only:
16:30:56.995347 IP 10.10.81.11 > 10.10.76.240: ICMP echo request, id 1, seq 17, length 40 16:30:58.000729 IP 10.10.81.11 > 10.10.76.240: ICMP echo request, id 1, seq 18, length 40 16:30:59.004189 IP 10.10.81.11 > 10.10.76.240: ICMP echo request, id 1, seq 19, length 40In this case the capture was taken on the router and the destination device send its responses to another gateway.
-
@viragomann when pinging from LAN2 to LAN1 we got request and responses,
The other way only requests -
@aziz-1 said in Static route over OpenVPN VPN:
The other way only requests
So that's the point where you should check the firewall on the destination device.
Do you get responses if you ping a LAN2 device from LAN1 pfSense?
To be sure, are both VPN endpoints the default gateway in their local networks?